The following is provided from Microsoft Security and Compliance blogs at TechCommunity:
Our customers spend a lot of time and money on security solutions and very few of them are taking full advantage of the solutions they’ve deployed. Even fewer of them are deploying or maintaining these solutions correctly. Based on this it’s not surprising to see stats like “93% of all breaches could have been avoided if basic cyber hygiene had been in place” (Online Trust Alliance).
From my view the industry and even our customers have been overly focused on finding technological solutions with the hope they’ll will address the people and process issues that are the root cause of so many incidents. Here at Microsoft we recognize that technology alone can’t solve the problem and so we’re increasingly focusing on delivering solutions that provide integrated capabilities on all three fronts.
Microsoft Secure Score is a perfect example of this. With it we can help you take full advantage of the Microsoft 365 security solutions you’ve deployed while at the same time helping you validate that they’ve been configured correctly.
Using Microsoft Secure Score to Amp Your Security Posture for Identity
As you’re probably aware of, when an organization suffers from a cyber-attack one of the first things attacks will target are user identities. By brute forcing passwords and then using lateral movement techniques to move across an organization, attackers can achieve their targeted goals. This is where Azure ATP comes in.
Azure ATP constantly monitors your domain controllers for identity-based threats, attacks and security posture issues by capturing and parsing network traffic and leveraging Windows events. From here it then analyzes the data utilizing profiling, deterministic detection, machine learning and behavioral algorithms that enable it to learn your network, detect anomalies and warn you of suspicious activities.
To maximize Azure ATP’s potential to catch anomalous identity related activities and to lower your time-to-resolve them we need to ensure that Azure ATP is fully configured and to do this you can use Microsoft Secure Score to surface a series of configuration checks.
Top 5 Most Impactful Improvement Actions to Prioritize
To maximize Azure ATP’s impact on your overall identity security posture, here are five improvement actions that many will find they can get done in a single day:
- Install Azure ATP Sensor on all Domain Controllers
- Set a honeytoken account
- Configure VPN integration
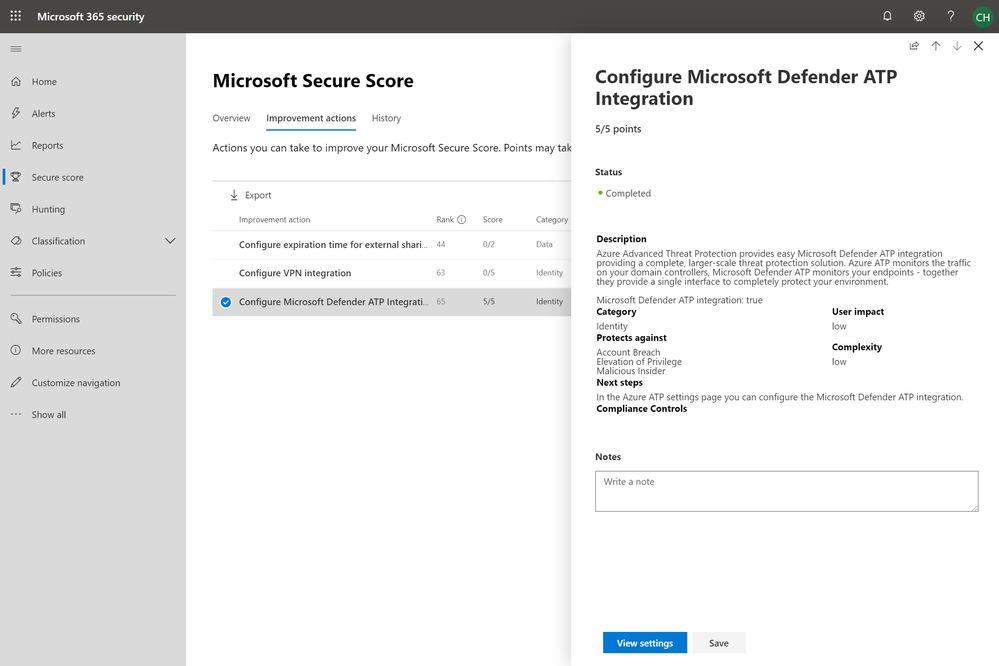
- Configure Microsoft Defender ATP Integration
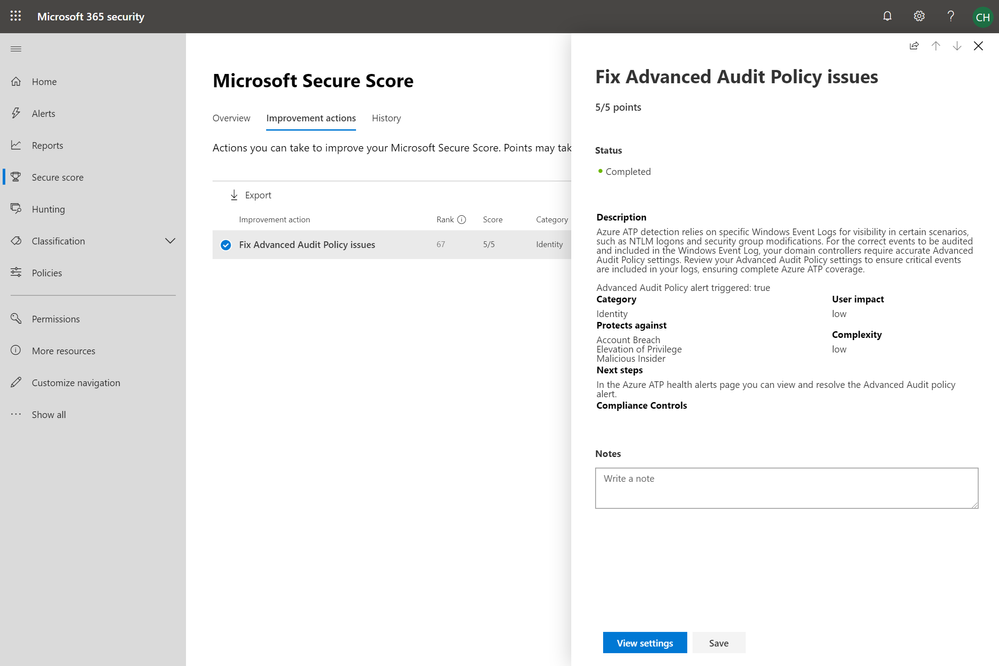
- Fix Advanced Audit Policy issues
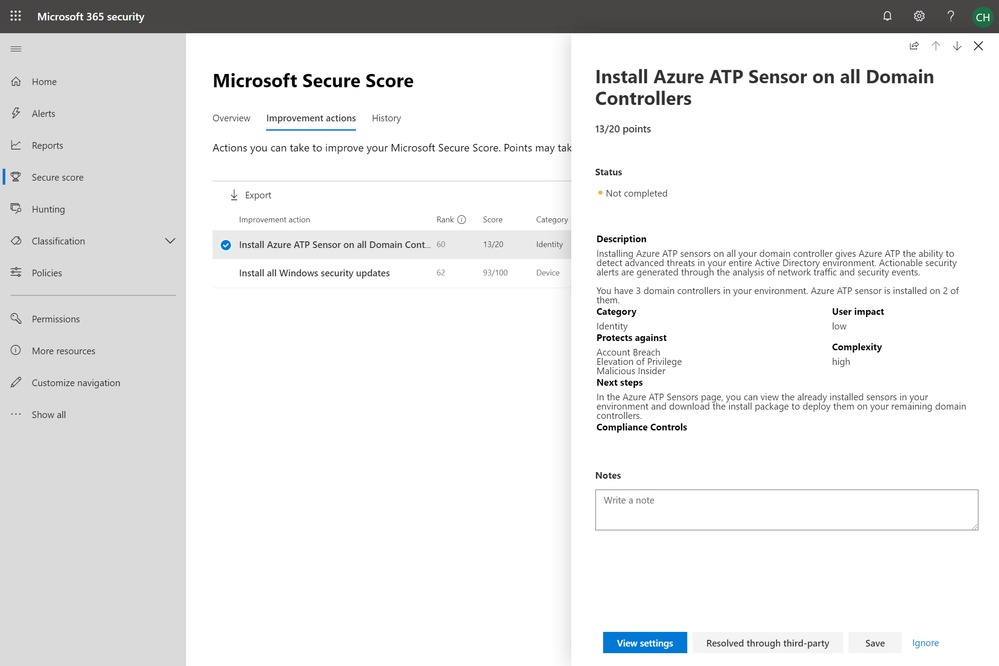
Install Azure ATP Sensor on all Domain Controllers
It may seem trivial, but our telemetry shows that in complex environments IT sometimes struggle to verify that all of their domain controllers are monitored by Azure ATP. This improvement action leverages Azure ATP’s knowledge of your network to pinpoint the domain controllers that you may have missed or were added after Azure ATP’s initial setup. Make this the first Improvement Action to improve your security posture with Azure ATP.
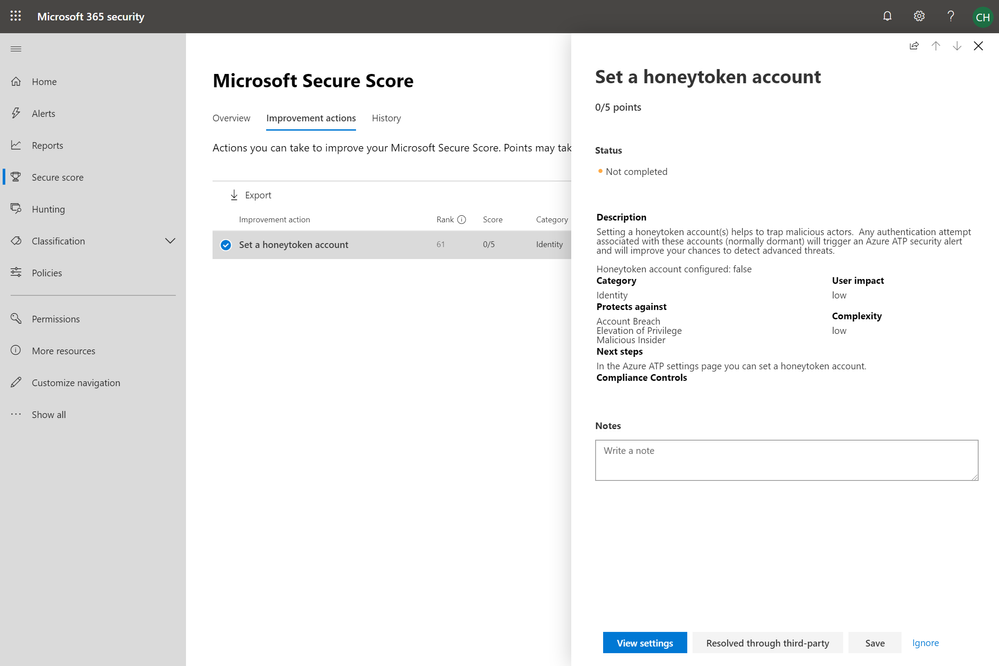
Set a honeytoken account
Setting a honeytoken account(s) is a great way to help expose malicious actors . A honeytoken account, like one temptingly named “SuperAdmin”, is a real account that is used as bait to lure attackers into exposing their presence and activities. Any authentication attempts associated with these accounts will trigger an Azure ATP security alert enabling you to catch attackers in the act.
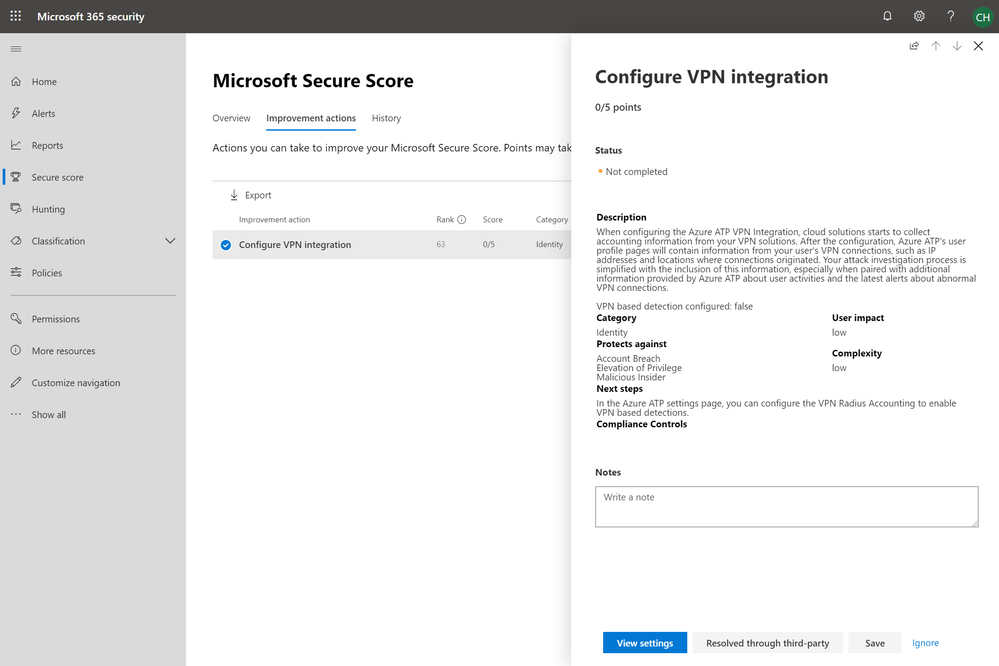
Configure VPN integration
A user’s VPN related activity can prove interesting for investigation purposes and once the “Configure VPN integration” improvement action has been implemented your SecOps team will be armed with information that will help them expedite their incident response activities. Once configured Azure ATP will start collecting VPN connection data (e.g.: IP addresses and locations where connections originated) which will be exposed in user profile pages within the Azure ATP .
Configure Microsoft Defender ATP Integration
Azure ATP easily integrates with Microsoft Defender ATP to help provide a more end to end threat protection solution. Azure ATP monitors the traffic on your domain controllers, Microsoft Defender ATP monitors your endpoints – together they provide an integrated experience to completely protect your . For example, Azure ATP will alert on remote execution of malicious code targeting domain controllers from a compromised device. From here an analyst can pivot to detailed device level information from Microsoft Defender ATP that enables the analyst to determine where it the malicious code came from, how it executed, etc.
Fix Advanced Audit Policy issues
Azure ATP detection relies on specific Windows Event Logs for visibility into a variety of scenarios, such as NTLM logons and security group modifications. To enable Azure ATP to monitor these events on your domain controllers the “success” and “failure” audit event options should be enabled in the Audit Credential Validation and Audit Security Group Management policies. These policies can be found under Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration.
Wrapping It Up
So, there you have it – a quick tour of the top improvement actions for Azure ATP. As you can likely tell from the list, implementing them will have no negative impact on your users and each of them can be quickly enabled. Start using Microsoft Secure Score today to see how you maximize your security posture and squeak each and every ounce of capability out of your Microsoft 365 security solutions. More information on Azure ATP and Microsoft Secure Score can be found at Microsoft Docs (Azure ATP and Microsoft Secure Score).
Related Posts
The above was provided from Microsoft Security and Compliance blogs at TechCommunity