Am a keen follower of Microsoft's SharePoint Blog and proud to provide this direct from the Microsoft Tech Community:
Issue :
You are using Google Chrome 80, and when you have ADFS/SAML or FBA configured site, you notice that intermittently, users logging in fails and goes into a login loop.
The following error is received on ADFS :
“An error occured. Contact your administrator for more information”
FBA does not sign you out either.
Cause :
This behavior is because of Chrome’s new security feature :
A cookie associated with a cross-site resource at <URL> was set with the `SameSite` attribute. It has been blocked, as Chrome now only delivers cookies with cross-site requests if they are set with `SameSite=None` and `Secure`. You can review cookies in developer tools under Application>Storage>Cookies.
Ref: https://blog.chromium.org/2020/02/samesite-cookie-changes-in-february.html
Testing/Troubleshooting to understand the behavior :
- First test by passing any load balancer and check if you have the issue
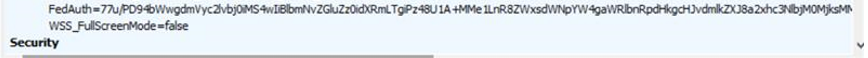
- We need to collect a fiddler trace, and look for the frame in fiddler which is a GET request to the site, and in request header you will see that the ‘Fedauth’ cookie still exists.
- This is the response from the server, a “Set-Cookie” Header, that sets the FedAuth to blank, this is because the user is browsing the site with an expired FedAuth cookie :
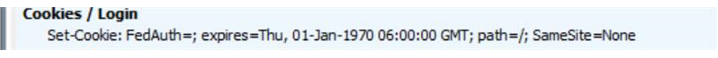
- Even after setting it to blank by SharePoint Server, Chrome does not deliver the blank Fedauth cookie(due to the same changes in it’s cookie handling behavior), and in the next POST to the site it sends the same old expired cookie, you can see it in the request header in next request :
- When we use “Set-Cookie” to set the Fedauth to blank, we also see the ‘SameSite=None’ attribute, but Chrome will deliver the cookie ONLY if it HAS ‘SameSite=None’ alongwith ‘Secure’ attribute
Resolution :
Step 1 — Recommendations by Microsoft
- Reference : https://docs.microsoft.com/en-us/office365/troubleshoot/miscellaneous/chrome-behavior-affects-applications
Step 2 — If you still see issue continues after March 2020 CU update for SharePoint
- If you still see issues with Load Balancer in place, you will have to contact your load balancer vendor for having an iRule created to add the SameSite=None and Secure parameter in the “Set-Cookie” header.
Step 3 — If you do not have a load balancer that distributes load between servers in SharePoint
Note :
Make sure to take a backup of the web.config file from all SharePoint servers before making the below changes
This is only if you are using a SSL web application
- If you do not have a load balancer, you will have to use the URL Rewrite module on all SharePoint servers.
Install the URL Rewrite Module : https://www.iis.net/downloads/microsoft/url-rewrite
- The Rewrite we will be using is an Outbound Rule, follow below steps
-Start by selecting the IIS site pertaining to the ADFS/SAML web app
-Enter into the URL Rewrite module
-Select Add Rule and then Select the “Blank Rule” under “Outbound Rules”, and configure below options
Matching Scope : Server Variable
Variable Name : RESPONSE_Set_Cookie
Pattern : (FedAuth=;)(.*)(SameSite=None)
Action type : Rewrite
Value : {R:1}{R:2}{R:3};Secure
- Test your web application for the same issues now in newer version of Chrome
Related Posts
The above is kindly provided by the Microsoft Tech Community!