We are happy to announce Microsoft Graph Security connectors for Azure Logic Apps, Microsoft Flow, and PowerApps, which greatly simplify the development of automated security workflows. By building playbooks that use the Microsoft Graph Security connector, you can automate common security tasks across multiple security solutions. This reduces the time and resources required to triage, investigate, and remediate security alerts, without the cost and complexity of building and maintaining multiple integrations. For further details on integrating with the Microsoft Graph Security API, learn about the API and access the schema.
Getting Started
Use these connectors now in your existing workflows or create new workflows. The steps are similar for Azure Logic Apps, Flow, and PowerApps. We’ll use Azure Logic Apps as an example here. Refer to the documentation and connector reference for further details.
- Your Azure Active Directory (AD) tenant administrator must first grant consent for the connector; follow the steps in the connector documentation.
- Sign in to the Azure portal, and open a new or an existing Logic App in Logic App Designer.
- For a blank Logic App, first start with a trigger, such as the Recurrence trigger. For existing Logic Apps, add an action to the end of a workflow by clicking ‘+ Next Step’ or between steps by clicking the (+) sign and selecting ‘Add an action’.
- Search for “Microsoft graph security” and select an action from the list.
- Provide the necessary details for your selected action and continue building your Logic App workflow.
Supported Actions
The Microsoft Graph Security connectors enable the following actions:
- Get alerts – Use this action to get a list of alerts filtered on one or more alert properties. For example, get a list of alerts with Provider equals Azure Security Center or Palo Alto Networks.
- Get alert by ID – Use this action to get a specific alert by alert id property.
- Update alert – Update a specific alert by specifying the alert id property. Refer to the list of the editable properties of alerts to ensure required and editable properties are passed in your request. For example, you can update alert assigned to property to assign the alert to a security analyst for investigations.
- Create subscriptions – Use this action to create a Graph webhook subscription that notifies you of any changes, filtered to certain types of alerts you are interested in. For example, you can create a subscription that notifies you of high severity alerts.
- Get active subscriptions – Use this action to get a list of unexpired subscriptions to manage the list of subscriptions
- Update subscription – Update your subscription by specifying the subscription id. For example, you can update the expirationDateTime property of the subscription to extend the subscription.
- Delete subscription – Delete your subscription by specifying the subscription id.
User Scenarios
You can mash up the Microsoft Graph Security connector with the 200+ Microsoft and non-Microsoft connectors available for Azure Logic Apps, Flow and PowerApps to build end-to-end scenarios based on your requirements. We have provided a few examples of scenarios that can be enabled using the Microsoft Graph Security and other connectors.
Automating Security Monitoring and Management
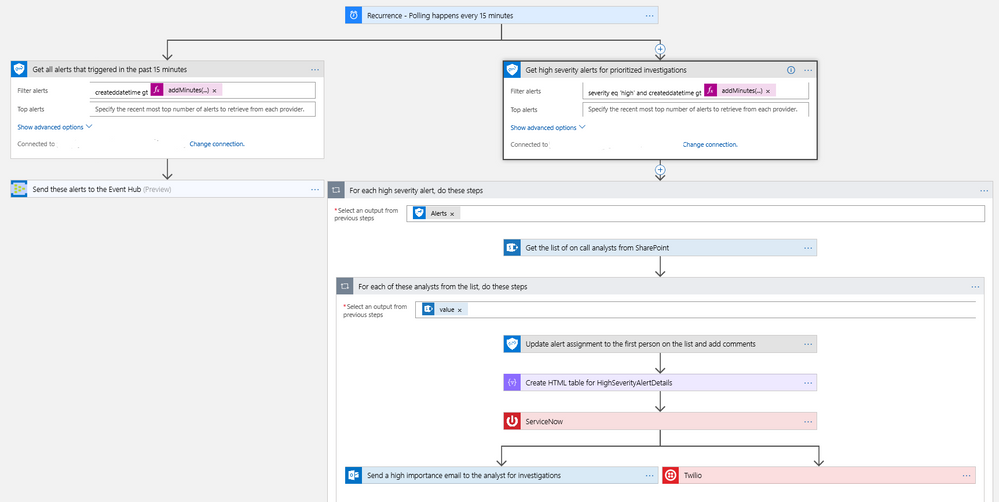
It’s always been a challenge to get notified of critical alerts that needs immediate action in an automated manner. At the same time, not all alerts are of equal priority and needs to be handled differently for optimal security management. You can now use the Microsoft Graph Security connector to get your high severity alerts across various security products like Azure Security Center, Windows Defender ATP, Palo Alto Networks, etc. and route those for immediate action. This example workflow below segregates alerts based on severity and routes high severity alerts for investigations.
- This workflow starts with a Recurrence trigger set for polling every 15 minutes. Two workflows kick off in parallel.
- Refer to the left branch.
- Get new alerts every 15 minutes using the Microsoft Graph Security connector.
- Push these to the event hub using the Event Hub connector.
- Refer to the right branch.
- Get new high severity alerts every 15 minutes using the Graph Security connector.
- Get the list of on-call security analysts using the SharePoint connector.
- Update the alert to assign it to the first analyst using the Graph Security connector. Add comments to the alert as well.
- Create a record for tracking this alert investigation using ServiceNow connector.
- Format and send an email to the analyst on point for investigations using the Outlook connector. At the same time, notify the analyst via SMS using Twilio connector.
Automating Security Response Handling
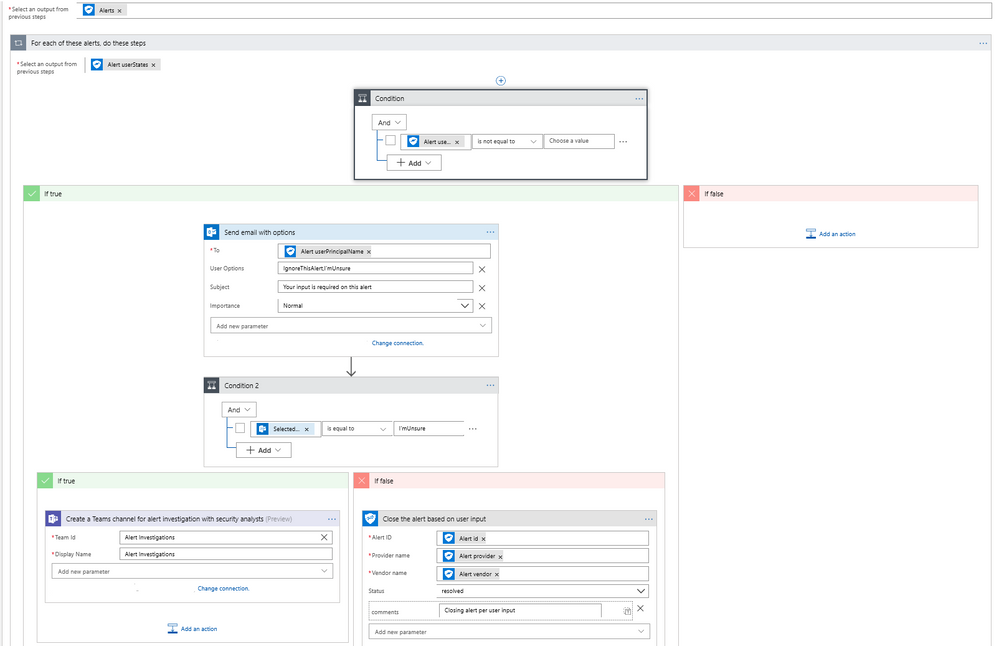
To reduce the workload of security analysts, alerts about suspicious user actions, such as logging in from unusual locations or atypical data access, can be investigated further and in some cases automatically resolved with input from the user in question. An example workflow for this using the Microsoft Graph Security Connector is as follows.
- The workflow starts with a Recurrence trigger like the previous examples.
- For each new alert, check for a user principal name. If present, use the Outlook connector to email the user asking them to provide feedback about the alert, such as IgnoreThisAlert if the activity was legitimate or I’mUnsure if it’s not known.
- If the user responds as I’mUnsure, further investigation of the alert is needed; initiate a Teams channel with the security analysts for further investigations using the Microsoft Teams connector. This can be supplemented by SMS, etc. as well as covered in the earlier example.
- If the user responds as IgnoreThisAlert, update the alert status to closed using the Microsoft Graph Security connector and add comments to track resolution based on user input.
Automating Security Investigations
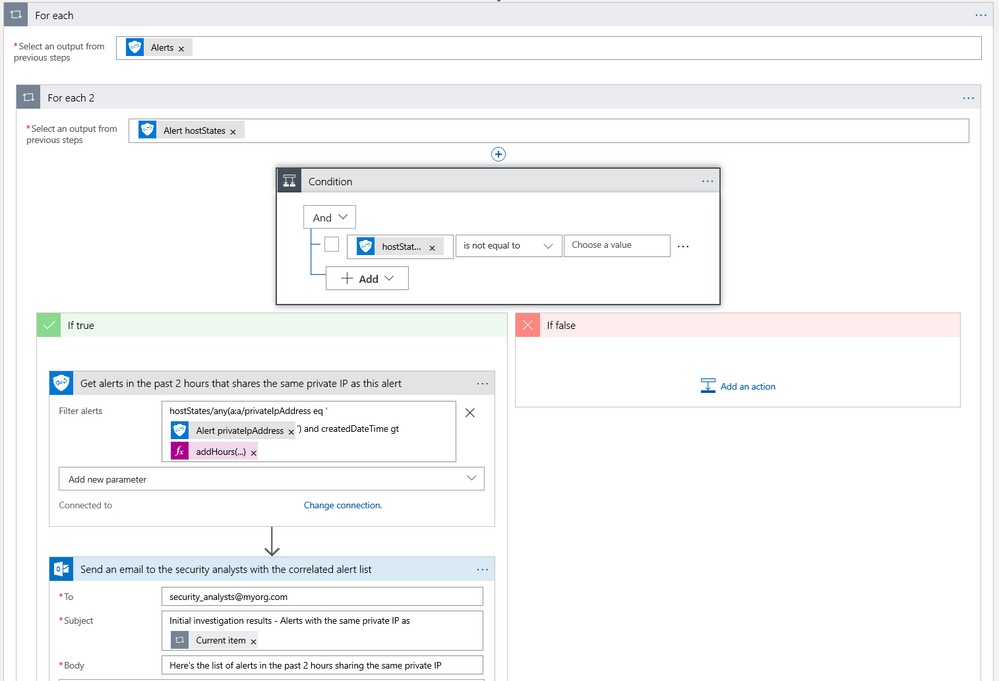
The often-manual process of correlating related alerts during an investigation can be automated using the Microsoft Graph Security connector. In this example workflow, all recent alerts for the host IP being investigated are automatically collected. This same example can be leveraged to find alerts for a specific file, user, or process user under investigation or other alert properties.
- The workflow starts with a Recurrence trigger like the previous examples.
- For each high severity alert, check for a host private IP address. If available, compare the address with that of all alerts generated in the past 2 hours using the Microsoft Graph Security connector.
- Email a list of related alerts to the security analyst team for investigation using the Outlook connector.
What’s Next?
We are working on templates for the Microsoft Graph Security connector to simplify the process of building your security playbooks. Fill out the feedback form to help us design templates for the workflows you need most.
Try the Microsoft Graph Security connector and please share your feedback by filing a GitHub issue or by engaging on the Microsoft Security Graph API tech community or StackOverflow.