Today, we are announcing new capabilities in the Microsoft Graph Security API to help our customers simplify integration, speed up response, and improve the effectiveness of their existing security investments. The latest updates include an expanded list of alert providers, new capabilities that enable threat intelligence sharing, streamline the creation of security automation workflows, and enable rich security analytics and reporting. Finally, we’re announcing several new integration partners.
Security Alerts
The Microsoft Graph Security API provides a unified interface and common schema to simplify integration of security alerts from Microsoft products, services, and partners. In addition to the many Microsoft and partner solutions previously available for the Microsoft Graph Security API, you can now access security alerts from Office 365 and Azure Advanced Threat Protection solutions as well as the new Microsoft Azure Sentinel service.
Developers can integrate alerts via a single endpoint, using one authentication key and one SDK. You can query for all alerts pertaining to specific users, devices, files, or command lines when investigating a specific threat or use webhook subscriptions to get notified when any new alert matching your search criteria is created or updated. Learn more about alerts.
Threat Intelligence (preview)
Threat indicators, also referred to as indicators of compromise or IoCs, represent data about known threats, such as malicious files, URLs, domains, and IP addresses. Microsoft amasses a huge volume of indicators each day using trillions of unique insights into cloud, users, and endpoints, which plays a huge role in how we protect Microsoft and our customers. You may also generate indicators through internal threat intelligence gathering or acquire indicators from threat intelligence communities, licensed feeds, and other sources. In addition to the vast threat intelligence built into Microsoft products and services, you can now also leverage your own indicators to enable custom detections in Microsoft solutions. Learn more.
- Connect your threat intelligence platform and communities to automatically share the latest indicators with Microsoft. Use the Microsoft Graph Security API or leverage integrations with leading threat intelligence platforms, including Palo Alto Networks MineMeld and the open source MISP platform. Use with Azure Sentinel today to correlate threat intelligence with log data to alert on malicious activity. Refer to the tiIndicators schema.
- Take immediate action in response to new threat, such as block file, URL, domain, or IP address from within your security tools and workflows. When a security analyst discovers a new threat, protection can be instantly enabled in your Microsoft security solutions. Try it first with Windows Defender ATP (coming soon) to block malicious activity on your Windows endpoints using the properties seen in alerts or identified during investigations. Refer to the SecurityActions schema.
Security Automation
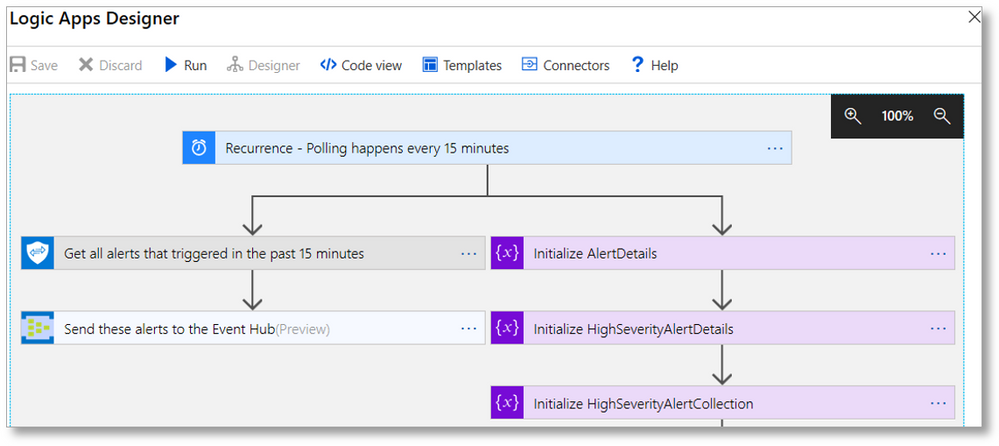
In a world of fast-moving, disruptive attacks and under-resourced security teams, automation of security workflows is essential. However, development of workflows to expedite alert routing, triage, investigation, and remediation can be challenging to create and maintain. We recently announced a set of Microsoft Graph Security API connectors to simplify development of automated security workflows without writing any code.
- Leverage Azure Logic Apps, Microsoft Flow, and PowerApps connectors to quickly build automation workflows using insights from the Microsoft Graph Security API. Mash up the Microsoft Graph Security API connector with over 200 other connectors to build workflows that act on security alerts, such as automatically routing high severity alerts to the on-call analyst – creating a ticket assigned to that user, sending an email or SMS notification, and collecting related alerts to speed their investigation See other example workflows.
Security Analytics + Reporting
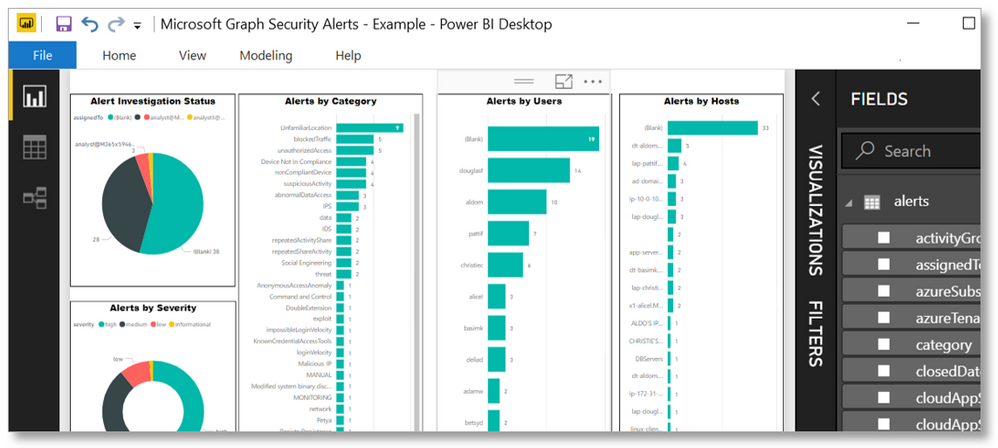
The Microsoft Graph Security API now makes it easier than ever to analyze and visualize data across different security products running in your organization to get deeper security insights. Create reports and dashboards for visibility into active threats and trends. Discover opportunities to learn from the data and train your security models. The Microsoft Graph Security API schema provides multiple properties to pivot on to build rich reports and exploratory datasets using your security data.
- Use the PowerBI connector to create enterprise-wide security dashboards and reports. Get a complete picture of security alerts and secure score across your organization. Mash up security data with data from the other Power BI connectors, like Excel workbooks or other databases, for richer context. Use Power BI and Microsoft Flow to trigger an automated security workflow based on metrics, such as a percent decrease in your secure score. A sample dashboard and template help you get started. Learn more.
- Get deep insights to train security solutions by leveraging the power of Jupyter Notebooks for Microsoft Graph Security API. Use these Notebooks to build your visualizations and training data models with alert properties for users, files, hosts, processes, etc. across multiple security products. Learn more.
Integrated Partner Solutions
The Microsoft Graph Security API offers a wide range of possibilities for partners to build and enhance security solutions. We’ve been building an ecosystem of technology partners and are excited to announce the following new integrations:
- Barracuda Cloud Security Guardian accesses alerts and a secure score from the Microsoft Security Graph API and displays this on a single plane of glass.
- Bay Dynamics Risk Fabric integrates with the Microsoft Graph Security API to gain greater visibility into threats, enabling them to better prioritize remediation activities.
- Citrix Analytics leverages the Microsoft Graph Security API to correlate alerts from the Graph with Citrix products and take security actions. See video.
- DF Labs integrates with the Microsoft Graph Security API to enable its IncMan SOAR solution to orchestrate and automate response to threats from Graph Providers.
- FireEye Helix uses the Microsoft Graph Security API to integrate security insights from Microsoft and partners into its security operations platform.
- JASK uses the Microsoft Graph Security API to ingest data and information related to Microsoft users, applications, and events into its ASOC SIEM platform.
- Swimlane’s SOAR platform integrates with Microsoft Graph Security API to orchestrate and automate incident response across multiple solutions for faster threat response.
Find out more about partner integration opportunities here.
In addition to technology partners, we’re also working closely with a number of managed security services providers who are building solutions leveraging the Security API. Most recently, SWC Technology Partners announced new security solutions that help improve organizations’ security posture. In particular, SWC is using the Microsoft Graph Security API in its Managed Defense Service that helps identify suspicious behavior and allows organizations to quickly surface and remediate threats.
We know that our customers struggle with integrating their diverse security tools, workflows, and systems. The cost, time, and resources necessary to integrate systems, enable correlation of alerts, connect to existing workflows, and provide access to contextual data is extremely high. We’re excited about the potential the Microsoft Graph Security API offers to directly address these challenges.
Get started today
Join us at the Microsoft booth, N6059 in the north expo hall, at RSA Conference 2019 in San Francisco. You’ll get the chance to speak to experts and see how our partners are using the API.
To learn more and get started with using the Microsoft Graph Security API, check out the following resources:
- Visit the Microsoft Graph Security API webpage to learn more
- Read the Microsoft Graph Security documentation
- Download the sample code and contribute
- Join the TechCommunity and follow the discussion on Stack Overflow