The following is provided from Microsoft Security and Compliance blogs at TechCommunity:
Hello everyone,
Today we are pleased to announce the general availability of Security Policy Advisor, a new service that can help enterprises improve the security of Office 365 ProPlus clients in their organization.
Security Policy Advisor has been in preview for the past few months and we wanted to first thank all our previewers who have evaluated this service and provided us with feedback that has helped us improve the service.
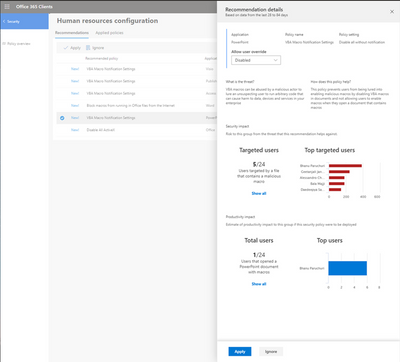
Security Policy Advisor enables IT admins who have deployed Office 365 ProPlus to manage the security of their Office applications with confidence by providing the following capabilities:
- Tailored recommendations for specific security policies that can provide a high value in helping raise the overall security posture of an enterprise and protect against contemporary attacks.
- Rich data insights about the security and productivity impact of applying a policy recommendation. These insights can help admins weigh the benefits and costs of applying a policy and make a data-informed decision.
- One-click deployment of policies to end users through the recently released Office cloud policy service that enables admins to enforce Office policies for Office 365 ProPlus clients directly from the cloud. No on-premises infrastructure or MDM services are required.
- Monitoring and reporting on policy impact, which allows an admin to have visibility into how a security policy is affecting users without having to wait to hear from them.
This service is now generally available and supported for customers with Office 365 ProPlus.
Get started today by visiting and signing into the Office client management portal, turning on Security Policy Advisor, and creating Office cloud policy configurations. For each policy configuration you create and assign to a group of users, Security Policy Advisor will generate recommendations with supporting data that you can review and deploy to users as a policy. Once you have applied a policy, you can continue to monitor its ongoing impact on users through the management portal.
For additional documentation on how to use this new policy service and its capabilities, see Security Policy Advisor for Office 365 ProPlus.
This service is just one of many new services which the Office team will be releasing over the next 12+ months. These services, which shape the foundation of the Office serviceability SDK, are designed to work with 1st and 3rd party management solutions to help administrators simplify and streamline Office deployment and management.
As always, please provide feedback using the feedback button to help us improve the service. We look forward to hearing from you and continue improving this service.
Thank you!
FAQ:
Note: Please refer to our documentation for the most up to date information.
What are the prerequisites to start using Security Policy Advisor?
For prerequisites, see Requirements for using Security Policy Advisor.
How does this relate to a security baseline?
Security baselines are a great starting point for enterprises to configure their applications for security. A new draft of the security baseline for Office 365 ProPlus applications is available here.
A security baseline is generic best practice guidance that ultimately needs to be consumed and customized for your enterprise to balance your security and productivity goals. You can use Office cloud policy service to apply the user level policies recommended in the Office security baseline. Security Policy Advisor complements a security baseline by providing custom recommendations for specific policies that are tailored to your enterprise, helping you to choose a security policy that has the least impact on productivity for your organization.
How are the recommendations, productivity and security impact insights generated?
Security Policy Advisor uses the following data to generate recommendations and associated data insights on productivity and security impact:
- To create the recommendations and productivity insights, Security Policy Advisor relies on required service data from Office 365 ProPlus . For more information, see Required service data for Office.
- If your organization has Office 365 Advanced Threat Protection Plan 2, then Security Policy Advisor can use data from this service to provide insights on recommended policies. These insights will be based on threats that have been detected and stopped by Advanced Threat Protection. For more details on Office 365 Advanced Threat Protection, see Office 365 threat investigation and response.
For more details, see How Security Policy Advisor creates recommendations.
What happens when I turn off Security Policy Advisor?
When you turn off Security Policy Advisor, usage and threat data from your organization are no longer analyzed and no recommendations or insights will be generated.
Admins can control the data collected from their clients using the new privacy controls supported by Office apps. More details are available at Overview of privacy controls for Office 365 ProPlus.
What happens if I do not have Office 365 Threat Investigation and Response (via ATP Plan 2)?
If your organization has Office Threat Investigation and Response (via ATP Plan 2), Security Policy Advisor can use data from this service to provide you with information on threats detected and stopped by ATP that the recommended policy can help protect against. This can be great to quantify the actual risk to your organization when you consider applying a recommendation.
If your organization does not have ATP Plan 2, Security Policy Advisor will still show you information on the productivity impact that is helpful in assessing and monitoring impact to end users when applying recommendations.
Which admin roles can view recommendations and configure policies?
Only the Global Admin, Security Admin or Desktop Analytics Admin roles are allowed access to create or view policy configurations.
Related Posts
The above was provided from Microsoft Security and Compliance blogs at TechCommunity