Often admins with privileged accounts have broad standing access, and therefore, become lucrative targets of repeated attacks as access to admin credentials can lead to deeper access to sensitive data. Due to this risk, regulators are increasingly looking for appropriate limits on privileged access, greater oversight, and audit trails.
To help customers protect and control their sensitive data, and meet their compliance needs, today, we are announcing preview of privileged access management in Office 365.
New privileged access management capabilities in Office 365 provides an approval workflow that’s scoped to your high-risk tasks within Office 365. For example, standing admin privileges enable admins to execute tasks that can provide unfettered access to organizational data, such as a journal rule, which can copy emails to a shadow mailbox and exfiltrate sensitive data undetected.
Privileged access management in Office 365 was designed based on the principle of Zero Standing Access, which is how we run our own data centers at Microsoft through Lockbox and Customer Lockbox. With privileged access management in Office 365, access requests must be approved by an authorized set of approvers. Access is then time-bound for a limited duration — often referred to as “Just-In-Time” (JIT) access. This level of rigor is how we manage administrative access privileges internally for Office 365 today.
Requests for access can be automatically or manually approved. Either way, all the activity is logged and auditable, so that both privileged access requests and approvals can be reviewed and seamlessly provided for internal reviews and auditor requests.
Read below for more details.
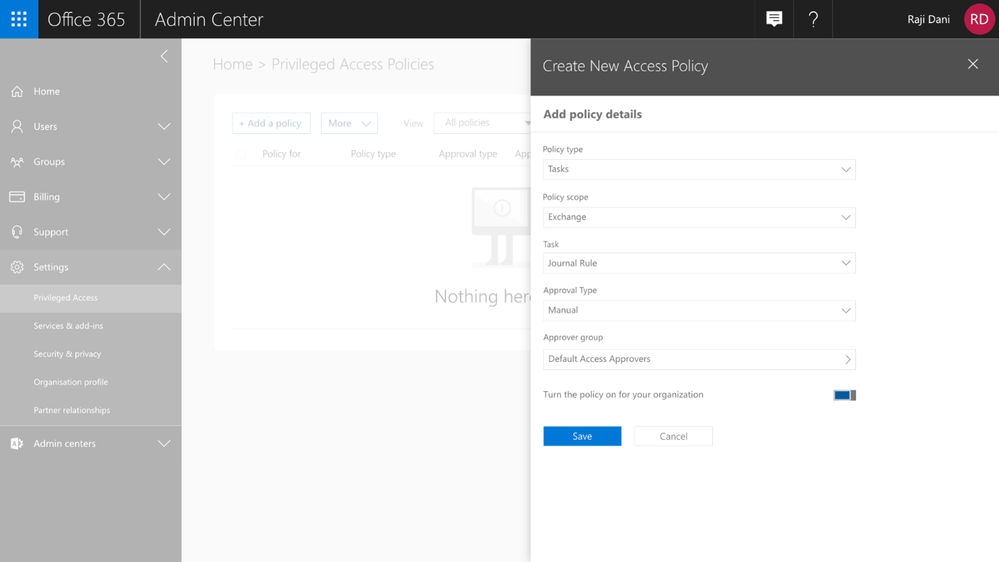
Creating Access Policies
Getting started with privileged access management in Office 365 in your organization is simple. Within the Office 365 Admin Center, you can create access policies at a task level, scope it to an Office 365 workload, and to a specific task within that workload. The policies also allow for flexibility in how requests can be approved – automatically or manually through a set of designated approvers.
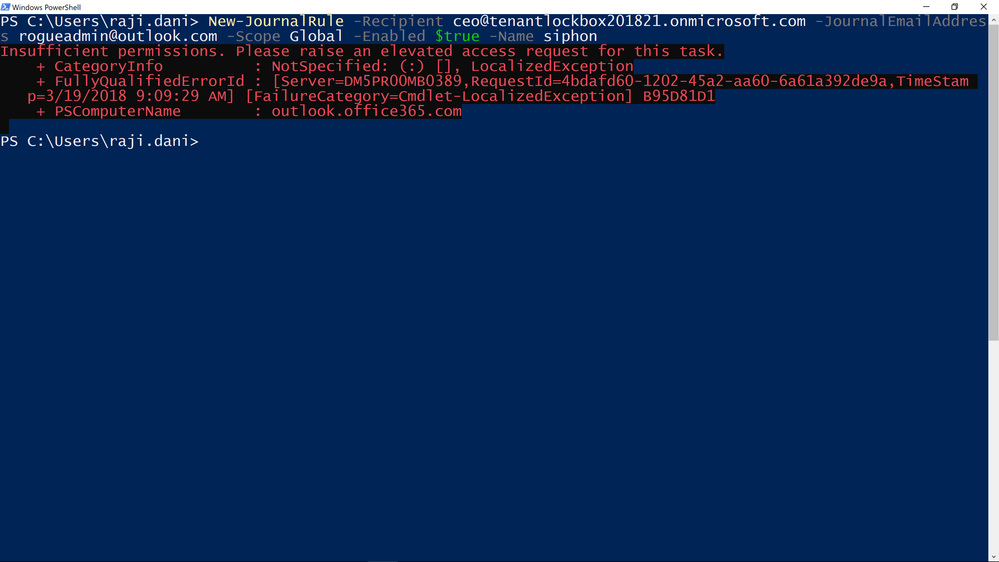
Enforcing an Approval Workflow
Once policies are in place, privileged access management in Office 365 will enforce the approval workflow, and when needed, users can request Just-in-Time access to execute these privileged tasks. Their privileges will endure only for the time requested and approved, vastly reducing the risk to the organization from privileged credential compromise.
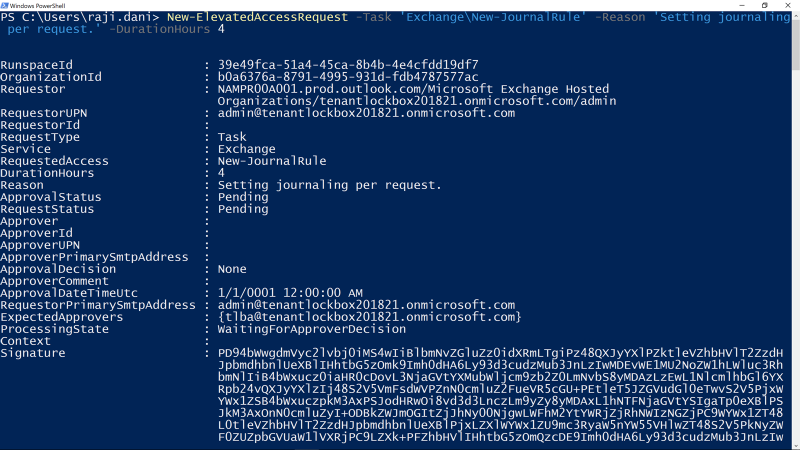
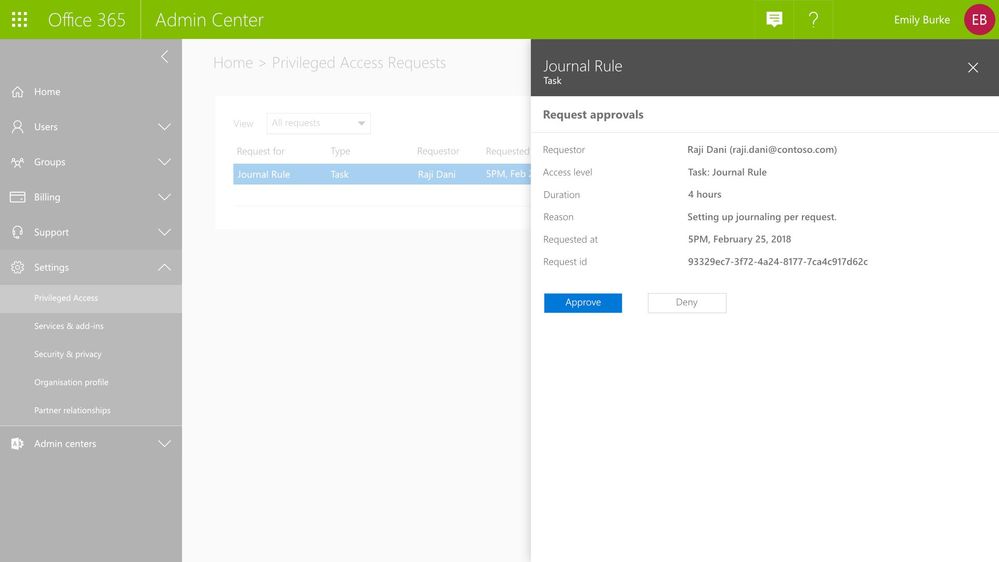
Approving Access
All access requests generated through the privileged access management workflow are available to view in the Office 365 Admin center. Designated approvers can review the details of the request –the requester, requested duration, and specified reason – and can then approve or deny the request.
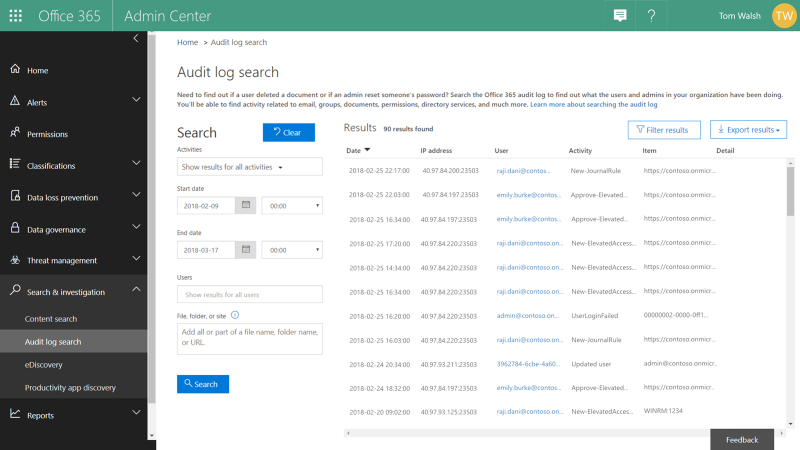
Audit Documentation
All activities – requests, approver actions, and subsequent tasks performed by the requesters – are logged and available for review in the Office 365 Management Activity logs. These audit logs provide a chain of events that also serve as evidence for compliance requirements.
Get Started Today!
Privileged access management in Office 365 is available in preview for our customers with Office 365 E5 and Advanced Compliance SKUs who register for the option. We hope you take that extra step to enable these features for advanced access control capabilities in your Office 365 tenant today. You can get started by:
- Watching the Mechanics Video on privileged access management in Office 365.
- Signing up for the preview at https://previews.office.com, with code PAM044.
- Attending the Ask Me Anything (AMA) – sign up for the event here.
We hope you like what you see – please do sign up for preview so we can get your feedback!
Frequently Asked Questions
Q: What SKUs do I need to use privileged access management in Office 365?
A: We plan to offer this capability in the Office 365 E5 or the Advanced Compliance SKU when we release to general availability.
Q: Which Office 365 services are supported with privileged access management in Office 365?
A: During this preview, privileged access management in Office 365 applies to tasks available in Exchange Online. We are working to expand privileged access management capabilities to other Office 365 workloads.
Q: How is this different from the Azure Active Directory Privileged Identity Management (AAD PIM)?
A: Azure AD Privileged Identity Management (PIM) and privileged access management (PAM) in Office 365 together provide a robust set of controls for protecting privileged access to your corporate data. With Azure AD PIM, customers can secure admin roles to ensure protection across Office 365 and Azure clouds. PAM in Office 365 can provide another granular layer of protection by controlling access to tasks within Office 365.
Q: What permissions do I need to turn this feature on?
A: You need to be a Global or Tenant administrator to be able to turn this feature on. Soon we will enable a new user Role that also will be able to perform these actions.
Q: How is privileged access management in Office 365 related to Customer Lockbox?
A: Customer Lockbox allows a level of access control for organizations around accessed to data by their service provider, i.e. Microsoft. Privileged access management in Office 365, allows granular access control within an organization for all Office 365 privileged tasks.