I was a guest speaker on a general SharePoint Security Webcast today, which was great fun. On the agenda was security of SharePoint relating to mobile devices. Unfortunately, the session did not manage to get into that topic, and I was so keen to talk about it. To counter, I’ve provided an article written today which talks about how personal devices as part of Consumerization have impacted SharePoint, some features available to mobile users, what implications are there in terms of security and finally a look at what Support needs to address.
Am going to summarise this all and prepare a webcast and talk looking at this topic – in fact, an expanded version will end up in my forthcoming book!
Before starting however, I must stress this is a massive area of concern; and even I am learning more about this topic and the more I do the more fascinating the topic becomes. That said, I think I’ve managed to pen some salient points and helpful suggestions. Even so, when putting this article together I kept coming up against more areas of concern (which I thought – when do I stop?), and am learning how to solve and consider them.
I do hope you enjoy this article – I had great fun putting it together; please contact me if you have any comments!
Striking a Balance
We are now deep in the forest of devices and consumer applications, with employees now using these devices in a now ‘blurred’ landscape of their workplace (cafe, airport, train, etc.). When employees bring their personal mobile devices to work, and use them to share files or data inside and outside of the office, it is difficult for IT to maintain visibility and control. At the same time, there is now an increasing argument that those using such devices are more productive; that the organisation where they work does not need to pay for such devices.
And, with the increasing Social Culture in terms of IT technologies in the workplace this then increases the ability for organisations to allow of ‘bringing your own’ (commonly referred to as BYOD) devices into an enterprise, allowing those devices to connect into a sea of connected systems and platforms, of which SharePoint plays a part. Providing this kind of open offering of connectivity from personal devices has been seen as a major boon for companies, one benefit mooted as helping to retain staff. Certain returns of investment can be seen particularly in increased worker productivity, they are less stressed, increased job satisfaction, increased motivation and for the company an enhanced image – being seen as being proactive in tolerating, encouraging and sponsoring the use of such devices.
In SharePoint, there are more challenges associated with providing a user experience that allows use of smart devices to access SharePoint as if they were accessing SharePoint from a laptop. These challenges are not just technical; there are business security and management issues as well.
How do we deal with the increased level of devices in an organisation?
1: Force users not to allow access using the devices – self-defeating and flies against user adoption.
2: Don’t inform users of any available integration to such devices, or ‘lie’ to them about any enterprise platform having such capabilities.
3: Allow them to use only specific devices, ones not part of the list are either not supported or barred from use.
4: Give in – the IT department has far too many other things to do, and any issue concerning a device is ignored.
5: Embrace change; ensure readiness.
For organisations adopting SharePoint as their collaborative platform, Consumerization needs to be treated with extreme care and caution. For a start, Consumerization requires that providers be a trusted community asset to the company. In other words, apple devices such as IPAD is ‘trusted’, iPhone is ‘trusted’, Blackberry is ‘trusted’, certain other smart devices are trusted; and then the granularity as to exactly what applications and services are available for use on those devices comes into play.
Therefore, to fulfil that goal, company leaders must make key decisions based on the best services offered by these devices in terms of how they fulfil business strategies and meet security requirements, given their financial and workforce resources.
Once achieved, organizations that foster trust with their employees will gain a competitive edge through increased productivity, better employee satisfaction and retention, enhanced customer satisfaction, and a more credible voice, by speaking from a position that supports their employee needs, not just a business needs. In addition, creating these good community relations translates into increased employee giving and volunteerism through the use of social applications and tools that have been integrated.
So defining security for personal devices users wish to use with SharePoint needs to be balanced with the need to provide a user experience which does not prevent or detrimentally impact their productivity.
“Security in human systems we’re told will always, always last. Emotions are the sail, and blind faith is the mast. Without the breath of real freedom we’re getting nowhere fast.” – Gordon Sumner
So what is Consumerization?
Consumerization as a term is well known – one definition of it is as follows: Consumerization is an increasingly accepted term used to describe the growing tendency for new information technology to emerge first in the consumer market and then spread into business and government organizations.
Fundamentally, this means that things like mobile phones, Internet Tablets, which in the past may not have been acceptable in the business is now seen as a key driver in providing staff productivity, particularly for those who work remotely and/or travel (which is on the increase).
Examples of this are where companies now actively allow their staff with certain types of mobiles access to their corporate network. Some have even gone as far to allow any mobile device to be used (with constraints) to access their wireless network.
So, a company set with managing a bank of ‘supplied’ mobile devices to their remotely working staff could be seen as not as cost effective as allowing staff to BYOD (as long as security is in place and security risks are mitigated and understood).
Using personal devices to access not only SharePoint content but other services
When looking at this in a SharePoint environment, the number of challenges rises exponentially from a support and security perspective.
92 million Computers shipped in 2010 but 101 million Smartphones shipped in 2010
The trend in supply of computers is definitely falling as the march to provide more benefits, features and performance to mobile devices increases. Aligned with this is a marked increase in the number of applications available, which will further entice users away from the standalone computer (mobility excepted).
With desktop computing, security has traditionally been more controlled due to the simple fact that it is not mobile, and that data is therefore more secured due to the standard protection devices available to protect data (e.g. hardwired dongles, network protection etc.)
Whilst this is not entirely difficult for laptops, there still is the intangible security issues concerning misappropriation, theft, loss. With smaller devices such as tablets, smartphones security risks increase again. And now that personal devices are being allowed to access corporate data remotely more security challenges.
Therefore, the converged trend of mobile device procurement over desktop will provide SharePoint owners of data security concerns which will impact on the governance of data security.
SharePoint fitting to the mobilized workforce
So, in this now digital world, content becomes more and more important to us. Everything we do is translated digitally. From the perspective of creating a document for a team, to organising an event, to keeping abreast with the latest news, to ideas building in discussion forums, to recording pictures and video, ad-infinitum. We do this not just at work, but also on the move. Be that on the train, airport, cafe, bus. The importance of collaboration is now related to how quickly we can collaborate. Uptime is becoming a very important word in ensuring that the systems we use to collaborate are available. Security whilst of utmost importance needs to be delivered in line with performance requirements and at the same time provide confidence in the monitoring and protection of the data.
Because the nature of the content defines its purpose there could be three types of individuals requiring access to the content – here are typical business high level requirements:
Remote employees will need to be able to access corporate information and electronic resources anywhere, anytime, and any place, without requiring a virtual private network (VPN).
- Travelling sales employees.
- Employees working from home offices or customer sites.
- Geographically dispersed virtual teams.
External partners must be able to participate in business processes and collaborate with employees of your organization.
Internal employees of the organization and partners may be required to view, change, add, and delete content to promote successful results for both companies.
Partners may be required to access the corporate environment through an Extranet, and in so doing security is enhanced:
- Apply appropriate security and user-interface components to isolate partners and segregate internal data.
- Authorize partners to use only sites and data that are necessary for their contributions.
- Restrict partners from viewing other partners’ data.
Customers may need to see branded, targeted content based on a product line or customer profile. Security implications include:
- Segmenting content by implementing separate site collections within a farm.
- Limiting content access and search results based on audience.
This is further impacted by the various options available designed to provide a consistent user experience and provide differing methods of accessing the data by these typical users. So, before describing the security implications related to the use of mobile devices of SharePoint, a quick review on some tools, components and technology where users are able to access SharePoint content. There are others, though I’d like to just cover these for now:
1: Mobile View.
2: SharePoint Workspace.
3: VPN and Direct Access.
4: SharePoint Online (Office 365).
Mobile View
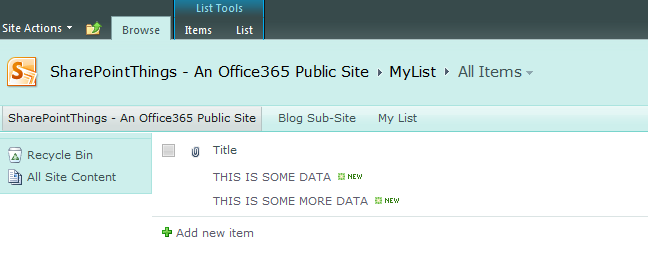
This presents a view of data from a SharePoint repository removing any styling and is available to a site, document library or list. Here is an example of a simple list on an Office365 SharePoint site:
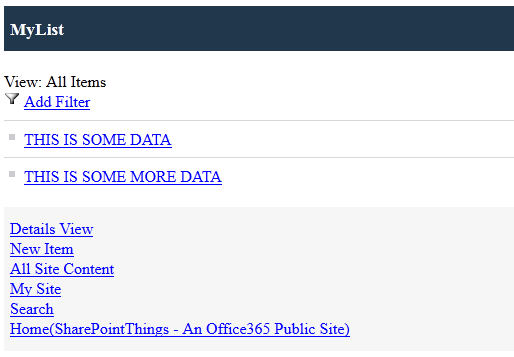
Now, this is how it looks as a mobile view:
Please note, I would have shown you how this looks using a Samsung Galaxy S3, but I could not show the mobile view, only the normal view (in a massively and unreadable mode) – hence the reasoning for mobile view which simply shows the data.
Here are some challenges concerning Security for you to mull over concerning mobile view.
- User authenticates to the site using a method of authentication. User then loses the device or device stolen resulting in a potential security risk; content and security credentials is cached on the device.
- Mobile view not acceptable to the business so the mobile view is customised. This customisation works on a number of browsers; but needs tweaking on others. Some modification relaxes security at code level allowing the user access to browser features that attempt to lock down security.
There are more potential issues but there are solutions; a wonderful article that explains mobile view and how to provide solutions is given here – I urge you to read this:
SharePoint Workspace 2010
In chapter 5 of my book ‘SharePoint 2010 Study Guide (exam 77-886) I describe what SharePoint Workspace 2010 is and how to use it – here’s a quick recap:
Microsoft SharePoint Workspace 2010 is a client application (included with Microsoft Office Professional Plus 2010) for SharePoint 2010. The program provides offline access to SharePoint documents and lists from the desktop and lets you synchronize content on a local computer with content in SharePoint. When you are connected to SharePoint all content updates are automatically synchronized. When you are not connected, changes you make in the workspace are cached locally.
So, the scenario is that a user who has access to a SharePoint site and/or document libraries and lists can request to take a copy of the data for remote working, make changes to the data on the move, and then have that data automatically sync back to the site. No security challenges there? WRONG.
- If the user downloads confidential or restricted data as for SharePoint Workspace then the device onto which that data has been downloaded to becomes a security issue.
- If the user is not supposed to have access to the data in the first place but has the ability to use SharePoint Workspace 2010 they could be compromising data security and acceptable use.
- IRM (Information Rights Management) implementation is client software dependent (may or may not work as intended). Not all types of content can be secured via IRM.
- Synchronization of SharePoint libraries with IRM is not supported by SharePoint Workspace 2010.
- Business rules concerning security need to be applied more rigidly and need more stewardship due to usage of SharePoint Workspace 2010
VPN Access and Direct Access
VPN allows those using a method utilising a user account, password, passkey which then provides access to a suit of applications of which SharePoint would be available within the corporate network.
DirectAccess, introduced in the Windows 7 and Windows Server 2008 R2 operating systems, allows remote users to securely access enterprise shares, web sites, and applications without connecting to a virtual private network (VPN). This connection is further enhanced using Forefront Unified Access Gateway. You should read the below article if you need to learn more:
http://technet.microsoft.com/en-us/network/dd420463.aspx
In either case, the user authenticates and then has access to the data. However, some of the issues are addressed through the use of UAG. One massively important point is indicated as follows:
Information leakage prevention – When users open or edit a document from a SharePoint library via Forefront UAG, no information is left on the client computer; Forefront UAG deletes all cached files, temporary files, and cookies. Even if there’s a sudden power outage, once the computer recovers Forefront UAG will take care of all the leftover data and erase it.
This is very important; erase of cached information on the client computer, which at least takes care of the possibility of the machine being lost / stolen. There are other indicators too, which could be seen as extremely useful – I would urge you to read this article – this is very helpful if you are considering going down the Extranet route for SharePoint, and need authentication and security monitoring solutions:
http://technet.microsoft.com/en-us/library/dd861393.aspx
The challenge though here is not the security; it’s how to provide the same user experience which the user may have using a terminal or laptop to that on a mobile device. Work needs to be done to ensure that the technology driving the security authentication is identical, and that may present challenges concerning look, feel, performance.
SharePoint Online
SharePoint Online is the provision of SharePoint services hosted by Microsoft in the ‘Cloud’. Am not going to talk too much about what it is, or the services it provides as there is a massive amount of content available (and I’ve also written some articles, for example here: https://serviceautomation.online/office365-explanation/ )
You may be aware that there will be those who do not want to, and for their own very good reasons, not to commit to Office365 as part of their provisioned and supported IT. Whilst those reasons (e.g. country regulation, retention, security management, control) are all valid in the eyes of the business requirement, I should stress (and I am not selling MS services here!) that no other company is more committed to cloud data security than Microsoft where this product is concerned; so much so that there is an entire area dedicated to Office365 security.
http://www.microsoft.com/en-us/office365/trust-center.aspx#fbid=VyjAGG3_p6W
However, security is still the responsibility of those owning the data. Irrespective of the security applied at the repository end, all this takes for a breakdown is a user having incorrectly set access, or not understanding the implications of downloading confidential content.
Administrators need to take heed. Administrators of the SharePoint Online site needs to be aware of the nature of the sites provided, since, for example, SharePoint online sites are set to “private” by default. To create a public website, the administrator must change the configuration in the SharePoint Online Admin Center – if done inadvertently without understanding security implications there could be issues.
Authentication is through either a Microsoft Online Services ID or Live ID. Because of this you will need to consider federation that allows single signon using your Live ID through an internal Active Directory account (for example), if you wish to provide a mechanism for partners to access data rolled up from on-premise SharePoint into say a Private SharePoint online provided site.
Points to note:
- For Office 365 for professionals and small business (Plan P1), content and files transferred to and from SharePoint Online are not encrypted in-transit through Secure Socket Layer (SSL) or other mechanisms.
- On public computers, it is strongly recommend that administrators advise users not to click on “Remember My Password” when prompted to sign-in, and to close the browser or log-out of SharePoint each time a site is accessed. Administrators are advised not to use the “Remember My Password” function and should change the default Administrator Password as part of the initial set-up process. If a user does click “Remember My Password.”, the SharePoint site will be accessible to anyone using Windows credentials on that computer until the authentication credentials are removed. For example, in Windows 7, authentication credentials can be removed by deleting cookies.
- User Profile data, including user shared and social updates, may be visible to other users. Social, published updates and shared information settings can be disabled.
Based on the three topics above, it is also important to note the user experience of those using Office365 on their mobile devices (especially smartphones) relevant to screen size – ok, so this is a user adoption comment – but it still refers back to security, since branding methods introduce security concerns. There are a number of third parties which provide authentication methods for iPads for example and methods by which smart phones can access SharePoint content – however, federation is always a key facet here which if done right provides user productivity benefits as well as possible audit and monitoring capabilities (utopia!).
Some Security issues
Because personal devices are flooding the work place, employees are under increased pressure to let them use mobile devices, and of course social networking applications which may be required to integrate with SharePoint. This presents not just a supporting issue but also security challenges.
These challenges are not just solved by adopting the technical solutions as indicated in this article, they are solved with combination of security awareness commonsense, governance and the ability to monitor content use in the environment. Lets take a look at some challenges.
Lost Devices
Even if sufficient security is implemented in wireless virtual private networks (VPNs), if a device is lost or stolen, the entire corporate intranet could be threatened if those devices aren’t protected by password and other user-level security measures.
For example, an individual could access SharePoint by simply opening the browser whose user credentials had been cached on a mobile if steps are not taken to address those and related risks.
Lost IP
Mobile devices use wireless connectivity – therefore, anything that could impact access from that perspective is considered a security issue.
Here’s a scenario explained via an email to Support – user was on an Internet Tablet, got a virus which then disabled the wireless connection:
“My IP address seems to have been lost. It’s currently at 0.0.0.0 I tried to reset the tablet. but it would not connect. I’m running out of ideas, and with a 10 page research paper due tomorrow, I need to figure this out fast. Any help would be appreciated. Thanks”
This issue, whilst it might sound abitary, could cause serious loss of business use. Consider that user was a key worker preparing a business case that required submission to secure funding and had a time limit?
Security Breaches
Because Consumerization continues to become a larger part of daily business operations. The costs related to security will invariably increase, and could cause serious cost and loss of face issues to a company.
Even if the company has security policies, the challenge they face comes in two-parts:
- The security policies need to adapt to a mobile work environment
- Decisions need to be made concerning deciding what kind of technology they need to manage devices and enforce policies.
Indeed, the indirect costs associated with security breaches are often far greater than the direct costs of mitigating damages; beyond costs of data remediation and possible fines for compliance rule violations, security breaches can cost companies their competitive advantage. They can embarrass companies or key people in those companies, creating bad publicity and legal problems. They can cause a loss of customer and partner confidence. Ultimately security breaches can damage a company’s brand and its ability to do business.
Additionally, if there are little monitoring in place to identify the nature of the breach this could further undermine the ability to provide a service. It is therefore important to consider how monitoring tools and auditing can be put in place, and provided in such a way that self-governance in data access from business users can be provided.
Information Leaks
Information Leaks are of a primary concern for mobile devices. The problem is that companies have almost no control over what documents are available on the devices. Mobile devices are a great source of information leakage because they often have inadequate or nonexistent security controls available.
Patching of Mobile Devices
Even under a “corporate” account, mobile devices are updated at the whims of the mobile carrier, who would usually prefer that you buy a new device with the updated OS (and extend your contract as well).
Getting Support Sorted
Time to look at how mobile device use gets supported from a basic perspective.
IT Support (or the company helpdesk) sometimes gets ‘glossed’ over when it comes to Consumerization, simply because sometimes IT Support wrongly perceived that they do not have time to understand what device is connected, and therefore it goes on to say that once the user is successfully connected that unless rigid monitoring is in place they will not be able to adequately provide information about what the user is doing on their personal device (remember that the Acceptable User Policy must extend to mobile device use!).
And, as more devices get connected via an ‘open’ wireless system in a corporate network, its fundamental that IT Support is aware of the various SharePoint and Business challenges faced by the use of mobile devices when planning an approach to securing the device on their networks.
An example of where this can go horrendously wrong is the provision of a wireless connection to an unprotected device which could be compromised without any policies in place from Support to protect the network or even identify the culprit.
Governance of the Mobile Device is the key
Policies should be defined around mobile devices to help protect sensitive SharePoint content. This can include securing the mobile device by using a PIN or lock, and ensuring that you can remotely wipe the data on the mobile device. Be aware that to do this that there is not yet a standards, and that there are programs and features which may vary by mobile device.
You can educate users about how they can help protect their user credentials. This can include signing out of sites when they are done, not enabling any option that keeps them signed in or remembers their password, and frequently deleting cookies in the mobile browser. This can help prevent others from using their user credentials to log on to a SharePoint site if their mobile device is lost or stolen.
Get the Users involved
Users need to be comfortable knowing that the data housed on SharePoint is secure, available and that the platform on which it sits is resilient and performs.
Security of the data is paramount in ensuring there can be a structured and managed SharePoint environment. This rule is applied both to technical and business users alike.
Technical security is covered by authentication, service application scaleability, integration of other data sources and platform connectivity.
For Consumerization, it is crucial that the security issues are not just addressed for the relevant device, but there are policies defined, communicated to the user and enforced on that device. This must be regularly reviewed. And, the reason why you get the user involved in this process is that:
a – you learn what the user wishes to do (what applications will be run on the device to access SharePoint).
b – you learn where the user wants to visit within SharePoint
c – you create more possibilities for guidance and that in turn leads to better governance
d – remember that some company strategies openly advocate the use of personal mobile devices as part of their march to create a more social networking attitude. Do not become prima donnas and attempt to curtail use of devices unless there is a valid security risk high enough to invalidate their use (and the client approves and is aware!). That said, this requires more time resource to investigate issues – there are tools to help.
One Final Thought
As I bring this article to a close, one point has really struck home with me. That even in the face of providing technical solutions to implying security to protect content on SharePoint, that the crucial aspect is user involvement, mentoring and awareness. This is unlike an implementation programme of SharePoint since a core driver is the ability for the benefits of security to be realised and then adopted (through the sites and content managed, for example). Henceforth, security for mobile devices needs to be a shared burden and the answers in terms of security governance needs to be understood and realised by business users.
“Information technology and business are becoming inextricably interwoven. I don’t think anybody can talk meaningfully about one without the talking about the other.” – Bill Gates