Introduction Microsoft Security Exposure Management (MSEM) provides the Cyber Defense team with a...

Introduction Microsoft Security Exposure Management (MSEM) provides the Cyber Defense team with a...

This week at Microsoft Secure, we announced the next big step forward in agentic security. In addition to Microsoft...
This blog details automating phishing email triage using Azure Logic Apps, Azure Function Apps, and Microsoft Security Copilot. Deployable in under 10 minutes, this solution primarily analyzes email intent without relying on traditional indicators of compromise,...
In this blog, I will walk through how you can build functions based on a Microsoft Sentinel Log Analytics workspace for use in custom KQL-based plugins for Security Copilot. The same approach can be used for Azure Data Explorer and Defender XDR,...
Microsoft’s Security Copilot is a new AI-powered security assistant (launched in April 2024) that integrates with Microsoft Defender, Sentinel, Intune, Entra and Purview to help analysts protect and defend at the speed and scale of AI. As a cutting-edge...
In a time of escalating cyber threats, security teams face relentless pressure to do more with less – more threats, more data, more tools, fewer resources. Microsoft Security Copilot was built to bridge that gap, delivering an AI-driven assistant that...
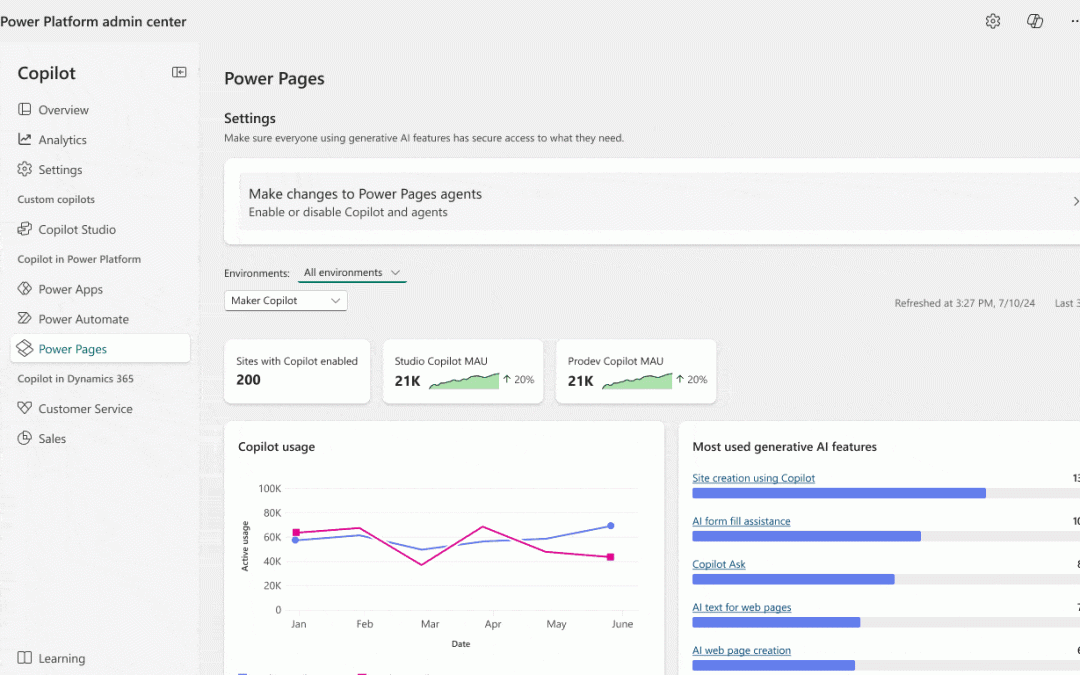
Introduction There are many different approaches when it comes to prioritizing the vulnerabilities which need addressing with urgency. Any information or guidance to help you make better informed decisions can be critical but how can you stay informed?...
There are risks of granting Edit rights broadly. This article underscores the importance of assigning Edit rights selectively and implementing controls such as versioning and approval workflows to safeguard critical documents.
Being a Microsoft Office 365 Partner am keen to follow any news concerning feature changes and updates to Office365. Microsoft announced via this blog, that Office 2013 clients’ connections to commercial Office 365 services will not be supported after October 13,...
Personal data (also referred to as PII – Personal Identifiable Information) identifies an individual. In that personal data, a name by itself is not enough to identify an individual, however, a name including the address would. For example, when you are called by an...
One of the most useful documents in my view in planning implementations of Office365 is understanding data encryption and data backup and the standards applied. Microsoft have provided audit reports covering their cloud stack (Dynamics CRM, Office365, Yammer and...