https://www.youtube.com/watch?v=kxubopY1oFk
General Blogs Articles
#2 – Bash command for File Navigation
https://www.youtube.com/watch?v=Tzm9uzaM6zs
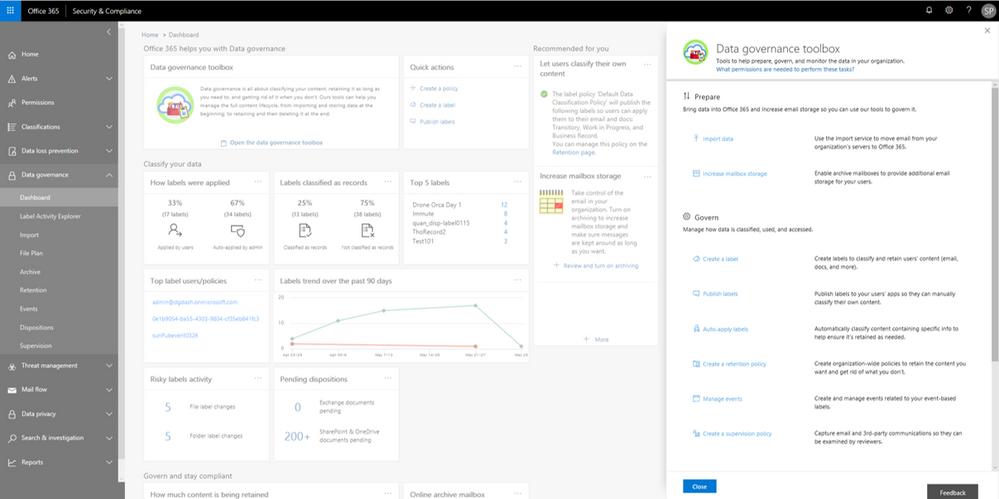
Now available! Validate data classification in your organization with the Label Activity Explorer
The new Label Activity Explorer helps you easily validate how data has been labeled and investigate risky or abnormal label activity in your organization. As data grows in your organization, so does the need to classify and govern it to ensure business continuity and...
Now available! Validate data classification in your organization with the Label Activity Explorer
The new Label Activity Explorer helps you easily validate how data has been labeled and investigate risky or abnormal label activity in your organization. As data grows in your organization, so does the need to classify and govern it to ensure business continuity and...
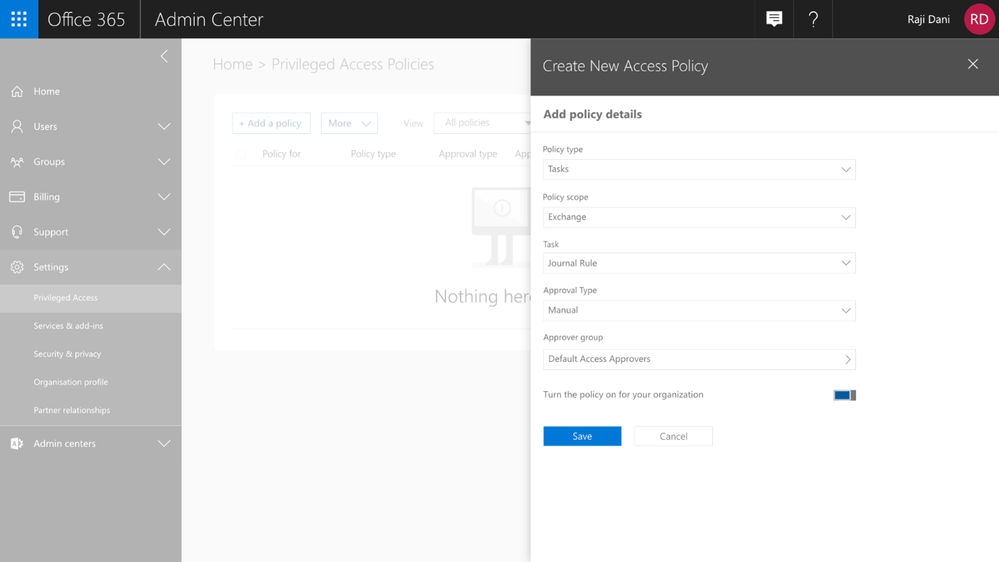
Announcing preview of privileged access management in Office 365
Often admins with privileged accounts have broad standing access, and therefore, become lucrative targets of repeated attacks as access to admin credentials can lead to deeper access to sensitive data. Due to this risk, regulators are increasingly looking for...
Announcing preview of privileged access management in Office 365
Often admins with privileged accounts have broad standing access, and therefore, become lucrative targets of repeated attacks as access to admin credentials can lead to deeper access to sensitive data. Due to this risk, regulators are increasingly looking for...
Announcing preview of privileged access management in Office 365
Often admins with privileged accounts have broad standing access, and therefore, become lucrative targets of repeated attacks as access to admin credentials can lead to deeper access to sensitive data. Due to this risk, regulators are increasingly looking for...
Announcing preview of privileged access management in Office 365
Often admins with privileged accounts have broad standing access, and therefore, become lucrative targets of repeated attacks as access to admin credentials can lead to deeper access to sensitive data. Due to this risk, regulators are increasingly looking for...
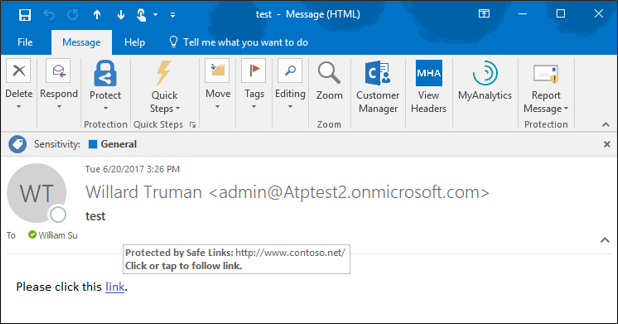
Enhanced User Experience for Office 365 Advanced Threat Protection
With the kickoff of InfoSec Europe, we shared an update of our recent enhancements to Office 365 threat protection services. Today, we discuss the significant enrichment to the end user experience in Office 365. By empowering end users to make better...
Enhanced User Experience for Office 365 Advanced Threat Protection
With the kickoff of InfoSec Europe, we shared an update of our recent enhancements to Office 365 threat protection services. Today, we discuss the significant enrichment to the end user experience in Office 365. By empowering end users to make better...
Enhanced User Experience for Office 365 Advanced Threat Protection
With the kickoff of InfoSec Europe, we shared an update of our recent enhancements to Office 365 threat protection services. Today, we discuss the significant enrichment to the end user experience in Office 365. By empowering end users to make better...