![How to secure your remote workers with Office Cloud Policy Service]()
With more and more users working from home, organizations are facing new security and privacy challenges. One of them might be, that users are working on unmanaged, maybe personal devices accessing corporate data. Classic technologies like Active Directory Group Policy Management do not help in such scenarios, as these do not apply to unmanaged devices.
This blog post will provide guidance on how to leverage the Office cloud policy service (OCPS) to address those scenarios. OCPS allows an admin to target a user with policies which follow them across all devices, regardless of the way the devices are managed (if at all). We will also share some recommended security settings which might be worth considering.
Step 1 – Enable OCPS
The Office cloud policy service (OCPS) is a cloud-based service that enables you to apply policy settings for Microsoft 365 Apps for enterprise (formally known as Office 365 ProPlus) on a user’s device. The policy settings roam to whichever device the user signs into and uses Microsoft 365 Apps for enterprise. This applies whether the device is managed through on-premises domain devices, as a Azure AD registered, Azure AD Joined, or Hybrid Azure AD joined device.
You should start by verifying the requirements:
- Supported version of Microsoft 365 Apps for enterprise deployed
- Licensed for Microsoft 365 Apps for enterprise
- At least one Azure AD group which contains the users you’re targeting.
- An admin user with at least the Office Apps Admin role assigned
Sign in on https://config.office.com and accept the EULA for OCPS. That’s it. No more prep work needed.

Step 2 – Create a policy configuration and assign to users
Now you should create your first policy configuration and assign it to a group of users:
- Expand the Customization node and select Policy Management
- On the Policy configurations page, choose Create and provide a name and a description (optional)
- In assignments, choose whether this policy applies to all users of Microsoft 365 Apps for enterprise, or just to users who anonymously access documents using Office for the web.
- Select the AAD-based security group that is assigned to the policy configuration. Each policy configuration can only be assigned to one group, and each group can only be assigned one policy configuration.

We also have a video ready for you which walks you through these steps.
Step 3 – Set policies
After clicking on Configure policies you can start to search for and configure policies. Please note that most policies are only applicable to Office on Windows, but some are applicable cross-platform as noted in the platform column in the policy list.
As a starting point, you can filter the Recommendation column to view the recommended Microsoft Security baseline policies. Click on each policy name to view the description and decide if you want to keep the baseline’s recommended value or manually configure it. The reviewed items will switch the Status to Configured when applied.

Especially for the scenario of remote workers, here are some policies you might want to have a closer look at:
| Policy Name |
Comment |
| Block signing into Office |
Can be used to prevent users from being signed in with a corporate and personal account at the same time in order to prevent data leakage to e.g. a personal OneDrive. |
| Hide file locations when opening or saving files |
Setting to “Hide local PC” will discourage users from saving corporate data to the maybe non-corporate device. |
| Disable VBA for Office applications |
VBA/macros are powerful tools and can help automate data processing or entry. But it is also used for malicious attacks and might be better prevented to run on non-managed/remote devices. |
| Do not open files from the Internet zone in Protected View |
If set to “Disabled”, Office files downloaded from the internet will always be opened in Protected View first. |
| Set document behavior if file validation fails |
Admins can enforce Protected View for files which failed validation. Those files could e.g. try to exploit Office through malformed documents. |
| Allow the use of connected experiences in Office, et al. |
Admins can control if Office is allowed to leverage cloud services for downloading and analyzing content. Review documentation for available controls. |
| Force Runtime AV Scan |
If enabled, all files opened by Office will be passed to the installed AV engine for scanning. |
| Use Cached Exchange Mode for new and existing Outlook profiles |
You can use this policy to enforce Online Mode for Exchange in order to prevent users from syncing down their inbox content to a maybe insecure device. Note that this setting will apply to all devices the user is signing into. |
| Block all unmanaged add-ins |
This setting allows you to block all add-ins from being loaded by Office. |
Step 4 – Additional considerations
As policies configured through OCPS are following the user across all devices, it is not limited to remote workers or users on un-managed devices. You should consider folding your on-prem policies into OCPS policies and go forward with a single solution for both on-prem as well as off-prem users.
Once you have deployed OCPS policies, you can also enable the Security Policy Advisor to get further insights into high impactful these changes are for your users. Maybe there are opportunities to further tightening it up without impacting users.
Overview of blog post series
This post is part of a series which is covering different stages and phases in the Office lifecycle in remote worker/work from home scenarios. The others are:
We hope this will help you to minimize the impact of deploying, servicing and managing Microsoft 365 Apps for enterprise on your own network and your user’s VPN connections.
FAQ
Q: Am I secure after enabling OCPS and setting the Microsoft recommended policies?
A: “Being secure” is a relative state where you can try to achieve a high bar, but basically never be 100% secure. Using OCPS is one building block in a broader strategy to secure remote workers. In addition make sure to review Azure Multi-Factor Authentication, Azure Conditional Access and the user’s sign-in risk assessment to further protect the user’s identity. For guidance on protecting your corporate data, please review Azure Information Protection.
Q: I’ve got issues with OCPS, how can I troubleshoot the service?
A: We got you covered, please review Troubleshooting OCPS on Windows.
Q: Can I fully secure a device not owned by my organization?
A: There are limits on how secure a device that you don’t own or manage can be. Each employed security technology raises the bar for an attack/exploit on the device/user/data successfully, but unless you fully manage the device there is a risk to your data. Security is sometimes not about secure/not secure, but more about the right level of security for a given scenario. You can use Intune to manage devices that you don’t own.
Q: Can I also secure and control Office on iOS or Android using OCPS?
A: While some policies also apply to Office on Android or iOS, there are more advanced controls available through Intune Application policies. These allow you to e.g. enforce a PIN, local data encryption of cloud-only storage of data for the Office apps on mobile devices.
Q: We’re an Intune shop, can I also use Intune to manage OCPS policies?
A: Sure thing. You can manage the Policies for Office apps from the Intune portal as well.
Q: Can we use OCPS to block syncing OneDrive for Business content on devices which aren’t managed?
A: No. However, we can address this concern by having your Office 365 tenant administrator running Set-SPOTenantSyncClientRestriction cmdlet. This permits adding restrictions on whether users can sync items to non-domain joined machines.
The Authors
This blog post is brought to you by the Microsoft 365 Apps for enterprise Ranger Team at Microsoft. Feel free to share your questions and feedback in the comments below.
![How to secure your remote workers with Office Cloud Policy Service]()
This blog post will address the enterprise IT admin’s challenge on how to deploy Office 365 ProPlus to remote workers without saturating the company’s VPN connections. It will show you how to implement a tactical approach which allows an IT admin to stay in control and quickly relief the pain of VPN congestion by offloading content distribution to the Microsoft Content Delivery Network (CDN). Maybe you are in the process of moving off legacy versions of Office and want to keep the pace with e.g. the Office 2010 end-of-support approaching fast. There are multiple strategic solutions available (e.g. Intune and Windows Autopilot), but for now we focus on a quick fix.
Overview of blog post series
This blog post is part of a three-part series, which is brought to you by the ProPlus Rangers at Microsoft, a group of most senior deployment experts. The series provides guidance on how to offload content distribution to the Microsoft CDN across the lifecycle of an Office 365 ProPlus installation:
We hope this will help you to minimize the impact of deploying, servicing and managing Office 365 ProPlus on your own network and your user’s VPN connections.
The Concept
With the approach described below, we want to achieve two things:
- Keep IT admins in control what happens when by continue using your enterprise management solution like Microsoft Endpoint Configuration Manager (formally known as System Center Configuration Manager (SCCM))
- Offloading the content distribution to Microsoft’s CDN to allow remote user to leverage their local internet connection instead of pulling large source files from your ConfigMgr Distribution Points over VPN connections
We will walk you through the process on how to adjust an existing Office 365 ProPlus deployment package for a hybrid approach, update your sources and ensure that the source file download will bypass your VPN.
Step 1 – Adjust your deployment package
To allow remote users to leverage their local internet connection for source file access, we have to remove the source files from the Configuration Manager application. Navigate to the folder which is holding your software sources, locate the “office” folder and delete it:

In the above example, 11 Language Packs were included in the deployment package, bumping the size up to 6+ gigabytes. Keep the setup.exe as well as any configuration files located in the folder. This reduces the size of your deployment package to less than 10 megabyte. That’s a huge saving on your VPN connections.
In case you don’t have an Office 365 ProPlus installation package yet, you can use the built-in wizard to create one. Maybe you want to adjust the handling of languages, instead of hard-coding those you might want to use MatchOS or MatchPreviousMSI. After that, apply the steps above.
Step 2 – Update the content sources
If your application was already synced to Distribution Points, those still have the larger package cached. Navigate to Software Library > Application Management > Applications, select your application, switch to the Deployment Types Tab, right-click the appropriate entry and click Update Content.

This will re-sync any changes to your Distribution Points, so those will now also have the smaller deployment package ready to sync to devices.
Step 3 – Verify VPN configuration and deploy
Once a client has received the smaller deployment package through ConfigMgr and kicks off the installation, it will download the source files directly from the Microsoft CDN. It is important to ensure that your devices can actually reach out to those endpoints directly and don’t backhaul through the VPN tunnel. We published guidance on how to enable so-called VPN split-tunneling, the endpoints relevant for Office 365 ProPlus source file download are listed at Office 365 URLs and IP address ranges as entry #92.
If you already have an active deployment of the newly-updated package, clients will start receiving it after the Distribution Points have finished syncing the changes. If you want to start with a fresh deployment, just follow the regular guidelines in your organization.
FAQ
Q: We usually controlled which build is installed by embedding the matching source files. How can I control this now?
A: By default, setup will fetch the latest build available for the specified update channel. You can use the version attribute in the configuration file to specify a build. This might be important if your organization is wants to deploy the older SAC feature release.
The Authors
This blog post is brought to you by from the Office 365 ProPlus Ranger Team at Microsoft. Feel free to share your questions and feedback in the comments below.
![How to secure your remote workers with Office Cloud Policy Service]()
Over the past few weeks, Microsoft, and more specifically the Office 365 Network team have seen a large influx of questions from customers around how best to optimize their Office 365 connectivity as they work diligently to plan for a large amount of their userbase suddenly working from home. We’ve also seen similar queries from customers looking for best practice whilst rapidly enabling their Office 365 benefits, Free Teams plans or free 6 month E1 trial recently announced to rapidly roll out Teams to allow their business to continue to function and allow users to collaborate effectively without being in the Office.
The recent COVID-19/Coronavirus outbreak has caused many customers to rapidly enable, or proactively plan for the bulk of their employees working from home. This sudden switch of connectivity model for the majority of users typically has a significant impact on the corporate network infrastructure which may have been scaled and designed before any major cloud service was rolled out and in some cases, not designed for a situation when it is required simultaneously by all users.
Network elements such as VPN concentrators, central network egress equipment such as proxies, DLP etc, central internet bandwidth, backhaul MPLS circuits, NAT capability and so on are suddenly put under enormous strain due to the load of the entire business using them, with the end result being poor performance and productivity coupled with a poor user experience for those users forced to adapt to working from home.
A simple diagram of a traditional network model can be seen below, where remote user’s connectivity is forced in and back out of the corporate network to reach critical resources as well as branch offices using MPLS circuits to reach the services offered at head office. It is an incredibly common network model for businesses around the world, but it was designed to be effective for a pre-cloud world.
 A traditional enterprise network, which does not work well in a cloud first world
A traditional enterprise network, which does not work well in a cloud first world
This model made perfect sense and worked very well when the bulk of applications, data and services resided within the corporate network (the dotted line in the diagram), but as enterprises shift to the cloud, it rapidly becomes a cumbersome environment which doesn’t scale well or provide the organization with any agility to react to situations such as that we face today. Many customers report to Microsoft that they have seen a very rapid shift of network traffic which used to be contained within the corpnet now almost exclusively connecting to some external cloud-based source.
Fortunately, Microsoft has been working closely with customers and the wider industry for many years to provide effective, modern solutions to these problems from within our own services, and also aligned to industry best practice. Solutions that apply very simply and effectively to remote workers as much as they do to branch offices. Microsoft has designed the connectivity requirements for the Office 365 service to work efficiently for remote users whilst still allowing an organization to maintain security and control over their connectivity.
Below we will outline the simple steps an organization can take to drastically reduce the impact Office 365 traffic has on the traditional corporate infrastructure when we have a large percentage of users working remotely all at once. The solution will also have a significant impact on user performance and also provide the benefit of freeing up the corporate resources for elements which still have to rely on it.
Most remote users who are not using a virtualized desktop will use a VPN solution of some sort to route all connectivity back into the corporate environment where it is then routed out to Office 365, often through an on premises security stack which is generally designed for web browsing.
The key to this solution is separating out the critical Office 365 traffic which is both latency sensitive and that which also puts enormous load on the traditional network architecture. We then treat this traffic differently and use the user’s local internet connection to route the connectivity directly to the service. To do this we need to follow a simple set of actions:
1. Identify the endpoints we need to Optimize
Microsoft has already identified these endpoints and marks them very clearly for reference. In the URL/IP list for the service these endpoints are marked as “Optimize”. There are just four URLS which need to be optimized and nineteen IP subnets. In just this small group of endpoints we can account for around 80% of the volume of traffic to the service and it also includes the latency sensitive endpoints such as those for Teams media. Essentially this is the traffic that we need to take special care of and is also the traffic which will put incredible pressure on traditional network paths.
URLs in this category have the following characteristics:
- Are Microsoft owned and managed endpoints hosted on Microsoft infrastructure.
- Have IPs provided
- Low rate of change to URLs/IPs compare to other two categories
- Expected to remain low in number of URLs
- Are High volume and/or latency sensitive
You can also query the REST API Web Service for this information, and a PowerShell example script which does this and outputs the URLs/IPs/Ports for all three endpoint categories can be found using the link above.
|
Endpoint to Optimize
|
Port/s
|
Use
|
|
https://outlook.office365.com
|
TCP 443
|
This is one of the Core URLs Outlook uses to connect to its Exchange Online server and has high volume of bandwidth usage and connection count. Low network latency is required for online features including: Instant search, Other mailbox calendars, Free / busy lookup, manage rules & alerts, Exchange online archive, Emails departing the outbox.
|
|
https://outlook.office.com
|
TCP 443
|
This is use for Outlook Online web access to connect to its Exchange Online server and network latency. Connectivity is particularly required for large file upload and download with SharePoint Online.
|
|
https://<tenant>.sharepoint.com
|
TCP 443
|
This is the primary URL for SharePoint Online and has high volume of bandwidth usage.
|
|
https://<tenant>-my.sharepoint.com
|
TCP 443
|
This is the primary URL for OneDrive for Business and has high volume of bandwidth and possibly high connection count from the OneDrive for Business Sync tool.
|
|
Teams Media IPs (no URL)
|
UDP 3478, 3479, 3480, and 3481
|
Relay Discovery allocation and real time traffic (3478), Audio (3479), Video (3480), and Video Screen Sharing (3481). These are the endpoints used for Skype for Business and Microsoft Teams Media traffic (Calls, meetings etc). Most endpoints are provided when the Microsoft Teams client establishes a call (and are contained within the required IPs listed for the service).
UDP is required for optimal media quality.
|
<tenant> should be replaced with your Office 365 tenant name. For example contoso.onmicrosoft.com would use contoso.sharepoint.com and constoso-my.sharepoint.com
At the time of writing the IP ranges which these endpoints correspond to are as follows. It is strongly advised you use the script referenced previously or the URL/IP page to check for any updates when applying the policy, and do so on a regular basis.
104.146.128.0/17
13.107.128.0/22
13.107.136.0/22
13.107.18.10/31
13.107.6.152/31
13.107.64.0/18
131.253.33.215/32
132.245.0.0/16
150.171.32.0/22
150.171.40.0/22
191.234.140.0/22
204.79.197.215/32
23.103.160.0/20
40.104.0.0/15
40.108.128.0/17
40.96.0.0/13
52.104.0.0/14
52.112.0.0/14
52.96.0.0/14
52.120.0.0/14

- TCP ports 80/443
- UDP ports 3478, 3479, 3480, 3481
IPV6 endpoints can be ignored if not currently required, i.e. the service will currently operate successfully on IPV4 only (but not the other way round). This will likely change in future but IPV4 only is possible for the time being.
2. Optimize access to these endpoints via the VPN
Now that we have identified these critical endpoints, we need to divert them away from the VPN tunnel and allow them to use the user’s internet connection to connect directly to the service. The vast majority of VPN solutions allow split tunnelling, where identified traffic is not sent down the VPN tunnel to the corporate network but rather sent direct out the user’s local internet connection. The VPN client should be configured so that traffic to the above, Optimize marked URLs/IPs/Ports are routed in this way. This allows the traffic to utilize local Microsoft resources such as Office 365 Service Front Doors such as AFD as one example, which deliver Office 365 services & connectivity points as close to your users as possible. This allows us to deliver extremely high performance levels to users wherever they are in the world. There is also Microsoft’s world class global network which is very likely within a small number of milliseconds of your users direct egress, and is designed to take your traffic securely to Microsoft resources wherever they may be in the world, as efficiently as possible.
The solution would look something like that below.
 A client’s VPN connection with split tunneling enabled
A client’s VPN connection with split tunneling enabled
Sounds simple? It is in most cases, but for an enterprise, this shift in connectivity invariably raises questions about security. In the traditional network approach security is often applied inline to network traffic as it egresses to the internet. Proxies and firewalls perform inspection on the traffic to check for data exfiltration, viruses and so on. By bypassing this we are removing this layer of protection we have come to rely on when connecting to the internet. The good news is, for the highlighted endpoints above, Microsoft has numerous features in place which means your security with the modern approach may well be higher than available previously. We will run through some of the common solutions below, not all will be relevant or necessary to all customers, but we will cover the majority of common concerns that come up when implementing modern network connectivity.
3. Common questions when implementing local breakout and split tunnelling for Office 365
It should be noted that the two steps above are all that is necessary to solve the performance/scalability issues if you need to move very quickly given the current situation. The elements below can be added as needed and as time allows or you may have them in place already.
Q1. How do I stop users accessing other tenants I do not trust where they could exfiltrate data?
A: The answer is a feature called tenant restrictions. Authentication traffic is not high volume nor especially latency sensitive so can be sent through the VPN solution to the on-premises proxy where the feature is applied. An allow list of trusted tenants is maintained here and if the client attempts to obtain a token to a tenant which is not trusted, the proxy simply denies the request. If the tenant is trusted, then a token is accessible if the user has the right credentials and rights.
So even though a user can make a TCP/UDP connection to the Optimize marked endpoints above, without a valid token to access the tenant in question, they simply cannot login and access/move any data.
Q2. Does this model allow access to consumer services such as personal OneDrive accounts?
A: No, it does not, the Office 365 endpoints are not the same as the consumer services (Onedrive.live.com as an example) so the split tunnel will not allow a user to directly access consumer services. Traffic to consumer endpoints will continue to use the VPN tunnel and existing policies will continue to apply.
Q3. How do I apply DLP and protect my sensitive data when the traffic no longer flows through my on-premises solution?
A: If required, endpoints can be protected with Office DLP if required and it’s much more efficient to provide this feature in the service itself rather than try and do it in line at the network edge. Azure Information protection can also be used to provide a high level of information protection if required.
Q4. How do I evaluate and maintain control of the user’s authentication when they are connecting directly?
A: In addition to the tenant restrictions feature noted in Q1, conditional access policies can be applied to dynamically assess the risk of an authentication request and react appropriately. Microsoft recommends the Zero Trust model is implemented over time and we can use Azure AD conditional access policies to maintain control in a mobile & cloud first world. Conditional access policies can be used to make a real-time decision on whether an authentication request is successful based on numerous factors such as:
- Device, is the device known/trusted/Domain joined?
- IP – is the authentication request coming from a known corporate IP address? Or from a country we do not trust?
- Application – Is the user authorized to use this application?
We can then trigger policy such as approve, trigger MFA or block authentication based on these policies.
Q5. How do I protect against viruses and malware?
A: Again, Office 365 provides protection for the Optimize marked endpoints in various layers in the service itself, outlined in this document. As noted, it is vastly more efficient to provide these security elements in the service itself rather than try and do it in line with devices which may not fully understand the protocols/traffic.
For the Exchange endpoints listed above, Exchange Online Protection and Office 365 Advanced Threat Protection do an excellent job of providing security of the traffic to the service.
Q6. Can I send more than just the Optimize traffic direct?
A. Priority should be given to the Optimize marked endpoints as these will give maximum benefit for a low level of work. However, if you wish, the Allow marked endpoints are required for the service to work and have IPs provided for the endpoints which can be used if required.
There are also various vendors who offer cloud based proxy/security solutions called secure web gateways which provide central security, control and corporate policy application for general web browsing. These solutions can work well in a cloud first world, if highly available, performant, and provisioned close to your users by allowing secure internet access to be delivered from a cloud based location close to the user. This removes the need for a hairpin through the VPN/corporate network for general browsing traffic, whilst still allowing central security control.
Even with these solutions in place however, Microsoft still strongly recommends the Optimize marked Office 365 traffic is sent direct to the service.
Q7. Why is port 80 required? Is traffic sent in the clear?
A. Port 80 is only used for things like redirect to a port 443 session, no customer data is sent or is accessible over port 80. This article outlines encryption for data in transit, and at rest for Office 365 and this article outlines how we use SRTP to protect Teams media traffic.
Q8. Does this advice apply to users in China using a worldwide instance of Office 365?
A. No it does not. The one caveat to the above advice is users in the PRC who are connecting to a worldwide instance of Office 365. Due to the common occurrence of cross border network congestion in the region, direct internet egress performance can be variable. Most customers in the region operate using a VPN to bring the traffic into the corporate network and utilize their authorized MPLS circuit or similar to egress outside the country via an optimized path. This is outlined further in this article https://docs.microsoft.com/en-us/office365/enterprise/office-365-networking-china
Finally, please ask any questions you may have in the comments section below and we will do our best to answer as quickly as possible.
4. Further reading
General best practice for Office 365 connectivity:
http://aka.ms/pnc
https://docs.microsoft.com/en-us/archive/blogs/onthewire/__guidance
Recorded Ignite sessions
https://myignite.techcommunity.microsoft.com/sessions/81561?source=sessions
https://myignite.techcommunity.microsoft.com/videos/64276
https://myignite.techcommunity.microsoft.com/videos/64275
Office 365 Partner Program
https://resources.techcommunity.microsoft.com/networking/
Current partners are Citrix, Netfoundry, NTT, SilverPeak and Zscaler
Network Connectivity performance testing
https://connectivity.office.com/
This tool runs some tests against Office 365 endpoints including the Optimize marked ones and give you some clear feedback around how connectivity looks for those endpoints and anything you can do to improve the connectivity.
Bandwidth planning
https://aka.ms/bandwidth/
This tool is one mechanism you can use to monitor user’s Office 365 network traffic volumes to get a clear figure for bandwidth requirements for the wider business.
![How to secure your remote workers with Office Cloud Policy Service]()
Due to the dynamic situation with COVID-19 many IT pros are being challenged to assess ways to configure Office 365 Client to update directly from Microsoft CDN. Today, the majority of customers I engage with manage updates using Configuration Manager (ConfigMgr), predominately on-premises. The objective of this posting is how to minimize internet egress through customer VPN network for Office updates.
Network considerations
There are an infinite number of ways customers configure network access, no two customers are identical in configuration. Speaking generally, the VPN client needs to support split tunneling or be configured so network traffic destined for Office 365 are directed to internet and are not required to pass through VPN Server. Microsoft provides a list of all Office 365 URLs and IP address ranges in the following document. Some customers have VPN clients dynamically aware of Office 365 Services using Microsoft Graph API, some support URLs and others only support IP exclusions. You’ll notice item(s) 90 and 92 which provide specific URLs used by the Office 365 Client to perform updates.
|
90
|
Default
Required
|
mrodevicemgr.officeapps.live.com (Description: Device Management Service (DMS) is used to advertise the C2R builds to the machines which are non-admin managed based on the meta data passed by the machine.)
|
TCP: 443
|
|
92
|
Default
Required
|
officecdn.microsoft.com, officecdn.microsoft.com.edgesuite.net (Description: Office CDN where content is downloaded)
|
TCP: 443, 80
|
Tip: Please review blog posting How to quickly optimize Office 365 traffic for remote staff & reduce the load on your infrastructure
Tip: Please review blog posting Managing remote machines with cloud management gateway in Microsoft Endpoint Configuration Manager
Background on how Office 365 Client works by default
Office 365 ProPlus is designed by default to update from CDN. A scheduled task called “Office Automatic Updates 2.0” uses a trigger to routinely check for updates as advertised by DMS service. The Office client will always move to the latest versionbuild available by assigned channel documented here. Documentation around what to expect from a user experience when updates are delivered from CDN can be found here. If ConfigMgr Office 365 Client Management integration is enabled by Configuration.xml during initial installation, ConfigMgr Client settings, or Domain Policy, the scheduled task will continue to execute but will only perform software updates from ConfigMgr.
Options available to update from CDN
Option 1: Cloud managed
Steps:
- Disable OfficeMgmtCOM (required if previously ConfigMgr managed)
- On the next restart of Microsoft Office Click-to-Run Service, Office COM application will de-registered. Allows Office Client to do its thing and get updates from the CDN.
- This can be done by changing client settings in ConfigMgr or by Group Policy.
- Set UpdatesEnabled GPO to True (optional)
- Allows the client to resume normal update checks from the CDN
- UpdateDeadline GPO as an integer (optional) in days (ex. 12) to ensure the client is updated to ensure compliance. Using an integer value allows the admin to not have to continually change the date to a future date/time for every update.
Option 2: SCCM managed but offload content distribution
Use normal deploy software updates wizard within ConfigMgr console selecting deploy option. When completing deployment package screen, it is important to select option “No deployment package”. In this way, clients will download content directly from CDN but keep existing controls and user experience during software update workflow.
Steps:


FAQ:
How can I verify ConfigMgr integration is disabled?
Start -> Run ->dcomcnfg.exe and look for presence of OfficeC2Rcom application.


Where in the Office logs can I confirm Office updates are coming from CDN?
Use http://aka.ms/office365logcollector to collect Office logs or search for files in C:windowstemp which have your NetBIOS name like MININT-314VFT4-20200318-0857.log. (There will be a bunch of them). Use your favorite text editor to search for strings like ‘officecdn.microsoft.com’ or the build number you deployed.
Starting with version 1902, ‘Prefer cloud based sources over on-premise sources’ allows IT Pro to prioritize Cloud content. Does this feature extendsupport Office 365 Client updates?
No, this appear to be a bug which is under investigation. Workaround is to ensure Distribution Points used by VPN clients do not host Office 365 Client updates resulting in error 404. If the software deployment has selection ‘If software updates are not available on distribution point in current, neighbor or site boundary groups, download content from Microsoft Updates’, this should allow new location of CDN fallback to be used. I will update this item with updates when available.
The Authors
This blog post is brought to you by Dave Guenthner and Martin Nothnagel, two ProPlus Rangers at Microsoft. We’re looking forward to your questions and feedback in the comments below.
![How to secure your remote workers with Office Cloud Policy Service]()
When installing Office 365 ProPlus using the Office Deployment Tool (ODT), the standard configuration includes the entire suite of applications by default. In some cases, IT Pros need to exclude one or more of the apps or add back previously excluded ones. The article will go over the various scenarios and provide guidance on how to implement them. These scenarios include:
- Exclude apps during initial install
- Remove specific apps after initial install
- Re-including apps that were previously removed
- Adding Visio and/or Project after initial ProPlus installation
So, let’s look at each of these scenarios:
Exclude apps during initial install
There are two main ways how admins can control which apps are excluded at the initial install of Office 365 ProPlus. First, using the Office Customization Tool (OCT) at https://config.office.com, admins can simply toggle the buttons for the apps they wish to exclude from the initial install:

This will craft the configuration file with the necessary exclusions for you. You can either export and save the file locally or to the cloud and reference this file during setup.
A second way that admins can control which apps are installed at the initial install of Office 365 ProPlus is to leverage the <ExcludeApp ID=”APPNAME” /> attribute in the ODT configuration file directly. The names of all the app values are as follows:
- ID=”Access”
- ID=”Excel”
- ID=”Groove” (This is the old sync client for on-Premises SharePoint)
- ID=”Lync” (Skype for Business)
- ID=”OneDrive”
- ID=”OneNote” (OneNote 2016, Win32 app. NOT the UWP Windows 10 app)
- ID=”Outlook”
- ID=”PowerPoint”
- ID=”Publisher”
- ID=”Teams”
- ID=”Word”
A sample configuration file with Groove and OneNote excluded from the install would look like this:
<Configuration>
<Add OfficeClientEdition=”64″ Channel=”Monthly”>
<Product ID=”0365ProPlusRetail”>
<Language ID=”MatchOS” />
<ExcludeApp ID=”Groove” />
<ExcludeApp ID=”OneNote” />
</Product>
</Add>
</Configuration>
With either method at install time, Office 365 ProPlus will be installed with the selected apps excluded. You can verify by looking at this registry key:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftOfficeClickToRunConfiguration
O365ProPlusRetail.ExcludedApps
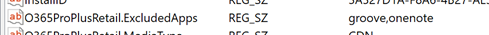
Or simply by checking the start menu and noticing those applications are not present.
Remove specific apps after initial install
If Office 365 ProPlus is already installed on a device or devices and you need to remove one or more of the apps, you can use the same method as above. However, there are a couple things to keep in mind.
- You can use Version=”MatchInstalled” to eliminate the need to keep track of the Architecture and Servicing Channel as this attribute will read the existing values and honor them. This can cut down on the number of configuration files needed in environments with multiple Office 365 ProPlus configurations.
- Setup.exe and the configuration file will need access to the Office source files. Either from the Microsoft CDN (Recommended) or internally by including them in a Configuration Manager application. Click-to-Run Office does not cache source files like the MSI version did in the MSOCache location.

If you had previously excluded an app or apps at initial install time, and wish to keep them excluded, you must continue to exclude them via the <ExcludeApp…/> section of the new configuration file you create along with whichever app or apps you now also want to exclude. Failure to do so will result in those applications being present and usable by your users.
The below example configuration file, leveraging “MatchInstalled” would remove Access from the device after initial install:
<Configuration>
<Add Version=”MatchInstalled”>
<Product ID=”O365ProPlusRetail”>
<Language ID=”MatchOS” />
<ExcludeApp ID=”Access” />
</Product>
</Add>
</Configuration>
Like the warning pointed out, running the above configuration will result in Access excluded and ONLY ACCESS EXCLUDED. If you had previously excluded apps such as Groove or OneNote 2016 from your initial install and now wish to exclude Access while keeping Groove and OneNote 2016 also excluded, you must have all three applications called out like in this example:
<Configuration>
<Add Version=”MatchInstalled”>
<Product ID=”O365ProPlusRetail”>
<Language ID=”MatchOS” />
<ExcludeApp ID=”Access” />
<ExcludeApp ID=”Groove” />
<ExcludeApp ID=”OneNote” />
</Product>
</Add>
</Configuration>
Re-including apps that were previously removed
This is very similar to the above scenario. Since Office 365 ProPlus does not include or exclude applications in the traditional sense, but rather asks “what do you want the suite to look like after this configuration?” So therefore If you excluded an app at initial install or post install and now wish to add it back in, you will use a similar configuration to the above example leaving any other apps still excluded you want to remain that way.
Consider this scenario: The IT Pro excluded Access, Groove and OneNote 2016 at initial install and now wishes to add OneNote 2016 back into the suite but leave Access and Groove still excluded. The example configurations would look like this:
Initial install Configuration:
<Configuration>
<Add OfficeClientEdition=”64″ Channel=”Monthly”>
<Product ID=”O365ProPlusRetail”>
<Language ID=”MatchOS” />
<ExcludeApp ID=”Access” />
<ExcludeApp ID=”Groove” />
<ExcludeApp ID=”OneNote” />
</Product>
</Add>
</Configuration>
Second install Configuration:
<Configuration>
<Add Version=”MatchInstalled”>
<Product ID=”O365ProPlusRetail”>
<Language ID=”MatchOS” />
<ExcludeApp ID=”Access” />
<ExcludeApp ID=”Groove” />
</Product>
</Add>
</Configuration>
Adding Visio and/or Project after initial ProPlus installation
Visio and Project operate in a different manner as they are different Product ID’s. These products cannot be added or excluded with the <ExcludeApp/> attribute. They can be added after the initial install by using a configuration file with Visio and/or Project as the <add Product ID> value. You must match the servicing channel and version of Click to Run architecture (64/32-bit) to prevent making unwanted changes. Better yet, you can leverage the power of the CDN and the new <MatchInstalled> attribute to do the heavy lifting here. Deploying Visio and/or Project from the Microsoft CDN after installing Office 365 ProPlus is very bandwidth friendly as most of the shared files are already installed.
Here is an example configuration of adding Visio and Project to device after Office 365 ProPlus has already been deployed:
<Configuration>
<Add Version=”MatchInstalled”>
<Product ID=”ProjectProRetaill”>
<Language ID=”MatchOS” />
<ExcludeApp ID=”Groove” />
</Product>
<Product ID=”VisioProRetaill”>
<Language ID=”MatchOS” />
<ExcludeApp ID=”Groove” />
</Product>
</Add>
</Configuration>

Notice in the above example I have excluded Groove from both Product sections. Groove, OneDrive and Teams operate slightly different at install time and if not excluded from each product they will get installed along with Office 365 ProPlus, Visio and Project Click-to-Run.
The Author
This blog post is brought to you by Eric Wayne, a Sr. Office Deployment expert and ProPlus Ranger at Microsoft. Feel free to share your questions and feedback in the comments below.
![How to secure your remote workers with Office Cloud Policy Service]()
I’d like to give you an early heads up on a visual design update that is coming to the Office 365 sign-in experience. These are the screens used to sign in to Microsoft’s apps and services, including Office 365, Azure and Dynamics.
We’re updating the default background image on our sign-in screens to something that’s fresher and more performant. The new image is just 1% the size of the previous one, which reduces bandwidth requirements and improves perceived page load times, especially on slower networks.
 Sign-in screen with old vs new background images
Sign-in screen with old vs new background images
This is solely a visual user interface (UI) change with no changes to functionality. There is no change to your users if you have configured a custom background image in Company Branding for your tenant. This change will only affect screens where the default background image (screenshot on the left above) shows up today.
We plan on rolling this out globally in early-April. If this change affects your users, we recommend updating any documentation that contains screenshots and to give your help desk a heads up.
Writing code for calendaring features is hard. Some of you might say writing any kind of code is hard, and you might have a point, but calendaring is particularly tricky. Why’s that? Well, consider time zones for a start – a meeting you set up isn’t necessarily in the same time as it is for me, and then you also invited people, from a whole bunch of other time zones (did you know some time zones are 30 mins off, not a full hour?), and then you made the meeting recurring, not every week, but every third Monday, except for next month, when it’s on Tuesday… and so on and so forth. But you got a meeting set up, all good.
And then one of the attendees happens to live in a country that decided to implement Daylight Saving Time (DST) and change the local time by an hour. Just in that country.
And we have an good example, as Brazil changed their DST rules in 2019 to eliminate DST and those changes are coming up very soon and they might impact users even with the latest OS updates applied. Users may see various issues with “off by an hour” calendar items when using the Brasilia time zone.
Sometimes we get caught out by a DST change made by a country, or a particular change needs us to code something new to account for it, and for the most part we make it so you don’t notice. But despite our best efforts sometimes users notice meetings are off by an hour. Then the users call you, their IT Pro to complain.
What do you do? There are a number of things we recommend, and so we wanted to share some simple advice on what to do, if it happens.
The “off by one hour” issue can vary widely in terms of scope and symptom, although it is typically limited to recurring appointments and meetings. For example, a user might report:
- Every single recurring meeting is off by an hour, but only in Outlook on the Web (OWA). The meetings render correctly in Outlook for Windows.
- Only a few meetings are off by an hour, but they show incorrectly in both OWA and in Outlook for Windows.
- Only exceptions to a recurring meeting are off by an hour, and only for attendees, not for the organizer.
- Only existing meetings that were created BEFORE the Windows Operating System DST patches were applied are off by an hour.
- Some other possible variation of meeting creation, attendee vs organizer, all vs some, OWA or Outlook desktop, etc.
The #1 best thing you can do to avoid seeing these issues in the first place is to keep your client software and operating system up to date. Sorry if that’s obvious to you, but the OS is the master time source for the client (in OWA’s case that means Exchange Online), and sometimes these DST patches require an update to Windows/Mac/Linux – so keep them patched. Sometimes we need to patch Outlook for Windows, Mac, iOS or Android, and so keeping the client up to date can prevent these issues from showing up. There’s a strong case to be made here for switching to Office 365 ProPlus and having updates regularly applied.
These DST issues can also require server-side changes. Exchange Online does all that for you, of course. In an on-premises world you need to update your servers, so make sure you keep up to date on Cumulative Updates (CU’s) for Exchange and OS updates.
Assuming you’ve done all that, your clients and servers/services are up to date – what then?
You need to figure out how large the scope of this issue is for your users. Is it every user? Is it Outlook for Windows only? What about OWA, does that work? Because the easiest thing might be to have the user switch to another client app until you figure it out.
If it’s only a subset of users (as you only have a small number of users in that geography where DST changed the time) perhaps you decide to manually ‘fix’ the meetings. If so, here’s what we suggest;
- Make sure the DST patches/updates are in place.
- Make sure you note any existing meeting exceptions that might exist if the problem meeting is recurring.
- Have the organizer cancel the meeting that is problematic.
- Have the organizer create and send a new meeting so that the start time correctly takes into account the new DST rules.
- Recreate the needed exceptional instances.
We also see cases where users ‘fixed’ their meetings ahead of a patch/update by just dragging them to the ‘correct’ start time, which then results in them breaking again when updates are installed (and their automatic changes come into effect) – that’s confusing but it’s all the same issue.
We realize re-creating the meeting series is a bit inconvenient, but that’s because time zone rule information is stored on the meeting itself and re-creating it on a patched machine will ensure the correct rules are being used for that series. And it’s often the quickest solution. But what if the impact is too large to handle that way, and you’ve made sure your clients are patched – then you should call into support and get some advice.
On multiple occasions we have made service side changes in Exchange Online to ‘fix’ it there. Those changes do make it to on-prem, but not until the next CU typically.
We give you a lot of flexibility in how you can create meetings (and we are not done improving meetings by a long shot) but it sometimes feels like it’s something of a minor miracle any of us ever get to meet and talk to each other at all, it really is. We celebrate people meeting every day, and we work really hard on this stuff, all the time, to make sure changes such as DST are accounted for.
We’re working on the Brazilian DST issue very hard right now, but we want to call it out so admins with users in that timezone are aware, and have a chance to make sure patches are applied, users are aware and so on. We’ll get things patched and fixed in time, no doubt, but we thought this a good time to broadly discuss DST, what it means, what you can do, and why writing code for calendaring can sometimes be a bit hard.
The Office 365 Calendaring Team
On January 22, 2020 we announced in advance that the Microsoft Search in Bing browser extension would be made available through Office 365 ProPlus on Windows devices starting at the end of February. Since then, we’ve heard from many customers who are excited about the value Microsoft Search provides through Bing and the simplicity of deploying that value through Office 365 ProPlus. With Microsoft Search integrated, Bing becomes a single search engine for users to find what they need – both from inside their organization and the public web.
But we’ve also heard concerns about the way we were planning to roll this value out. Most importantly, we heard that customers don’t want Office 365 ProPlus to change search defaults without an opt-in, and they need a way to govern these changes on unmanaged devices.
Based on your feedback, we are making a few changes to our plan:
- The Microsoft Search in Bing browser extension will not be automatically deployed with Office 365 ProPlus.
- Through a new toggle in Microsoft 365 admin center, administrators will be able to opt in to deploy the browser extension to their organization through Office 365 ProPlus.
- In the near term, Office 365 ProPlus will only deploy the browser extension to AD-joined devices, even within organizations that have opted in. In the future we will add specific settings to govern the deployment of the extension to unmanaged devices.
- We will continue to provide end users who receive the extension with control over their search engine preference.
Due to these changes, the Microsoft Search in Bing extension will not ship with Version 2002 of Office 365 ProPlus. We will provide an updated timeline for this rollout over the next few weeks. For more detailed information about deploying Microsoft Search in Bing through Office 365 ProPlus, please refer to this support article. Learn more about rolling out Microsoft Search in Bing to your organization by reading this user adoption guide.
Thank you for your ongoing feedback. Please continue to share with us through UserVoice.
![How to secure your remote workers with Office Cloud Policy Service]()
Office.com is the URL for an experience that we’ve been building for a couple of years. We designed it to be your work hub experience and help you quickly get to the apps, tools, documents, and content you use on a daily basis. We’ve also brought intelligence into the experience that customizes the experience based on your activities.
 Figure 1 – Office.com home page
Figure 1 – Office.com home page
Office.com includes the Office 365 app launcher, which opens when you click the app launcher icon . The app launcher, which in addition to Office.com is also available across the suite, is a menu of your Office 365 apps and services that makes opening and switching between apps easy.
 Figure 2 – Office 365 app launcher
Figure 2 – Office 365 app launcher
We’re rolling out some changes to the way pinned applications work on Office.com and in the app launcher:
- We’ve provided admin controls in the Azure Active Directory portal that enable admins with the Cloud application administrator, Application administrator or Global administrator role to pin up to three apps to Office.com and the app launcher. Any app added by an admin can be unpinned by the user at any time. Office.com and the app launcher are now one experience and will show the same set of apps.
- There’s no need to manually pin apps to the app launcher because the system now automatically pins apps for you based on usage. Any app added automatically can be unpinned at any time.
- In the previous experience, apps were removed after they were unused for a certain period of time. In the updated experience, apps will remain until manually unpinned.
 Figure 3 – Office 365 gallery
Figure 3 – Office 365 gallery
We’re also rolling out a change that provides admins through the Azure Active Directory portal with the ability to group apps and customize the view of the Office 365 gallery. The Office 365 gallery enables you to explore and learn about available applications. This customization can be done via the “collections” blade in the Azure Active Directory admin portal. For more information, see Help your workforce discover and connect to all their apps with the My Apps portal refresh.
Customers will see these changes rolled out soon. We welcome your comments and feedback so be sure to let us know what you think of these changes.
–The Office.com and app launcher team
![How to secure your remote workers with Office Cloud Policy Service]()
The Office cloud policy service (OCPS) is a cloud-based service that enables you to apply policy settings for Office 365 ProPlus on a user’s device. The policy settings roam to whichever device the user signs into and uses Office 365 ProPlus. As end users become increasingly mobile, IT Pros need a single approach to secure Office 365 ProPlus for traditional on-premises domain devices, Azure AD registered devices, Azure AD Joined, and Hybrid Azure AD joined devices. OCPS applies to all scenarios above without the need to download and replicate any content such as Administrative Template files (ADMX/ADML) on-premises. The goal of this blog is to provide some transparency of how the service works to help IT Pros during their validation phase and to encourage transition from classic domain-based policy to OCPS service for Office 365 ProPlus.
Requirements of OCPS
1. At least Version 1808 (August 2018) of Office 365 ProPlus
2. User accounts created in or synchronized to Azure Active Directory (AAD). The user must be signed into Office 365 ProPlus with an AAD based account.
3. Security groups created in or synchronized to Azure Active Directory (AAD), with the appropriate users added to those groups.
4. To create a policy configuration, you must be assigned one of the following roles in Azure Active Directory (AAD): Global Administrator, Security Administrator, or Office Apps Admin.
5. Connectivity to addresses below. Microsoft recommends proxy bypasswhitelist for these URLs
*.manage.microsoft.com, *.officeconfig.msocdn.com, config.office.com over 443
Steps to perform proof of concept and validation
1. Create a test user, ours will be “Kasper Graf”, kgraf@contoso.com.
2. Create security group “OCPS Service Validation” and add user to group within Active Directory Users and Computers.
3. Allow AAD Connect to synchronize user and group to Azure AD. (lunch break 🙂 or force synchronization via commands below)
(optional) From AAD Connect Server and elevated PowerShell, run the following commands:
PS C:WINDOWSsystem32>import-module adsync
PS C:WINDOWSsystem32>Set-ADSyncScheduler -NextSyncCyclePolicyType Delta
PS C:WINDOWSsystem32>Start-ADSyncSyncCycle
Browse Azure AD portal and explore Users – All Users, select Kasper Graf and then Groups. Verify that group “OCPS Service Validation” has been assigned and source says, “Windows Server AD”. This confirms user and group were synced into Azure AD successfully and we can proceed to next steps.
4. Create your first OCPS policy and select “Create” button:

5. Complete input fields, when selecting assigned security group input “OCPS” and service should filter results to “OCPS Service Validation” group. Next, define a policy. For the demo, I chose policy “VBA Macro Notification Settings”, “Enabled” where VBA Macro Notification Settings are set to “Disable all with notification”. Once selections have been made “Create” or “Save”.


6. From Policy Management, we can now see our policy exists.

So, we’ve got a policy, we’ve assigned it to a security group containing our test user, our next step is to validate. My test machine happens to be classic on-premises domain joined machine. My user, Kasper Graf, is signed in with his normal Active Directory credentials which is displayed in upper right hand corner of Word.

Traditional Group Policy uses Client-Side Extensions in Windows to apply policy every 90 minutes. IT Pros can force policy by using command line “gpupdate /force” and inspectverify registry as well as application behavior prior to broad deployment. OCPS checks for policy upon initial Office application launch, calls into cloud service endpoints listed above, determines policy applicability based on group membership and priority assignment and registry keys are populated.
Specifically, there are two locations of interest in registry.
1. HKEY_CURRENT_USERSoftwareMicrosoftOffice16.0CommonCloudPolicy
This will contain information about FetchInterval, 90 minutes is default, as well as record of Last Fetch Time and Last Payload Hash.
2. HKEY_CURRENT_USERSoftwarePoliciesMicrosoftCloud. This key will contain path to registry keys representing the policy assignment. For example, ours will be HKEY_CURRENT_USERSoftwarePoliciesMicrosoftCloudOffice16.0wordsecurity
Vbawarnings = 2 (DWORD)
IT Pros can achieve the same behavior of gpupdate by simply deleting the key HKEY_CURRENT_USERSoftwareMicrosoftOffice16.0CommonCloudPolicy, close Office application and relaunch to fetch policy. I typically use tools like Process Monitor to help trustverify operations of this type with filters such as “Path” contains “CloudPolicy” or where Operation is “RegSetValue” etc. Opening a Word document containing a Macro displaying warning with notification as expected.

FAQ:
How does conflict resolution work if the same policy is set via traditional domain-based policy as well as OCPS?
OCPS takes priority if there are any conflicts with traditional domain-based policies.
Currently policies are limited to user settings. Are there plans on adding machine settings?
Yes. This has been accepted and currently is in our backlog. We hope to have this available next year.
Group Policy provides a view of all policies on the device or for the specified user. Does OCPS support this?
Currently OCPS does not provide a list of all Office policies applied to a specific user or device. This is on our backlog and we hope to have this available next year.
Will OCPS support other platforms such as MacOS, Android and iOS?
Yes, OCPS in the future will also support additional platforms such as MacOS, Android and iOS. We will create additional blog postings per platform once features are generally available.
Are there any environments where OCPS is not available?
The Office cloud policy service isn’t available to customers who have the following plans: Office 365 operated by 21Vianet, Office 365 Germany, Office 365 GCC, or Office 365 GCC High and DoD.
The Author
This blog post is brought to you by Dave Guenthner, a Senior Premier Field Engineer and “ProPlus Ranger” at Microsoft. Feel free to share your questions and feedback in the comments below.
![How to secure your remote workers with Office Cloud Policy Service]()
Customers tell us they want easier ways to manage their environments while delivering more productivity value to their employees. This includes helping people quickly find the information they need, a potentially frustrating prospect given the sheer and constantly growing volume of content within an organization. To help IT solve this — and to do so in a way that is easy for you to manage — we are offering the Microsoft Search in Bing extension to Office 365 ProPlus customers starting at the end of February.1,2 To help you prepare, we want to share guidance on how you can configure Office 365 ProPlus updates to best meet your organization’s search needs.
Microsoft Search in Bing
Bing is a gateway to Microsoft Search, a unified enterprise search solution that provides contextual work-related information using data sources in Office 365 including SharePoint, Microsoft OneDrive for Business, and Exchange. Microsoft Search delivers personalized results surfaced by the Microsoft Graph to make search in your organization more effective, increase productivity, and save everyone time.
Employees can search for colleagues by typing the title, team name, or even office location into the address bar. They can also search for office location and get answers that show floor plans for directions. They can even get definitions for company acronyms.
As part of Microsoft 365, Microsoft Search is on by default for all Microsoft apps that support it. This update is designed to enable an accessible and familiar entry point for your users: a search engine.
Deploy Microsoft Search through Office 365 ProPlus
You have told us that you want a single tool to deploy all desktop components of Office 365. To simplify the process of deploying Microsoft Search, we’re making the Microsoft Search in Bing extension available through Office 365 ProPlus with version 2002, alongside Word, Excel, PowerPoint, Outlook, OneDrive, and Teams. This extension will be installed with new installations of Office 365 ProPlus and when existing installations are updated. If Bing is already the default search engine, the extension will not get installed.
If you don’t want to deploy the extension to your users, you can exclude it by using the Office Deployment Tool or Group Policy. There are also ways to exclude it if you’re using Microsoft Endpoint Configuration Manager (current branch) or Microsoft Intune. For more information about how to manage the extension, read this article.
Honor your users’ search preferences
Even if you deploy the Microsoft Search in Bing extension with Office 365 ProPlus, users will still have an opportunity to choose their search engine. The first time your users open Google Chrome after the extension for Microsoft Search in Bing is installed, they will have an option to change back their search preferences by taking a few simple steps.
 Mockup of the search toggle in Chrome browsers (subject to change).
Mockup of the search toggle in Chrome browsers (subject to change).
Learn more about the user benefits of this change by downloading the Microsoft Search in Bing Adoption Kit (zip file) and this user adoption guide. As always, please visit our Tech Community page to learn more about Office 365 ProPlus, and share your feedback and insights.
Footnotes
- This change is enabled for new and existing Office 365 ProPlus installations in Australia, Canada, France, Germany, India, the United Kingdom, and the United States. As we add locations, we will notify admins through the Message Center.
- The extension will be released to the Monthly Channel in late February 2020. Release for the Semi-Annual Channel (Targeted) and Semi-Annual Channel are coming soon.
As more and more Office 365 customers adopt Microsoft Teams, we’ve heard from many of you that you want to deploy and manage Teams the same way you deploy and manage other Office 365 apps. To streamline that process, we made Teams available through Office 365 ProPlus alongside Word, Excel, PowerPoint, Outlook, and OneDrive. We first provided this option to customers on the monthly channel several months ago. Starting on January 14, 2020, customers on the semi-annual channel will start to receive Teams through Office 365 ProPlus as well. With that date approaching, we want to remind you how to configure Office 365 ProPlus and Teams updates to meet the needs of your organization.
Deploy and manage Teams through Office 365 ProPlus
If you are an existing Office 365 ProPlus (or Office 365 Business) customer on the semi-annual channel, Teams will be included in your organization’s next update starting on January 14, 2020, as a part of the normal update process.
If you’re ready for Teams to be deployed on your users’ machines, you don’t need to take any action. You can learn more how to adopt Teams in this article. If Teams is already installed on a user’s machine, there will be no impact when the semi-annual update rolls out.
Learn more about how Teams updates, after it is installed.
Customize Teams deployment as a part of Office 365 ProPlus
While the number of customers using Teams continues to grow, we recognize that not all customers are ready for Teams to be automatically deployed on their users’ machines. You can manage your preferences and configure each Office 365 ProPlus app using the Group Policy or the Office Deployment Tool. Learn more about how to deploy and manage or exclude Teams in your Office 365 ProPlus updates in this article: Deploy Microsoft Teams with Office 365 ProPlus.
Send us your feedback
Every innovation we make with Microsoft 365, the world’s productivity cloud, is designed to help you and your organization unlock new forms of productivity to achieve more. Thank you for being our customers and we look forward to your feedback and insights.
Visit our Tech Community page to learn more about Office 365 ProPlus.
![How to secure your remote workers with Office Cloud Policy Service]()
The Office cloud policy service (OCPS) is a cloud-based service that enables you to apply policy settings for Office 365 ProPlus on a user’s device. The policy settings roam to whichever device the user signs into and uses Office 365 ProPlus. As end users become increasingly mobile, IT Pros need a single approach to secure Office 365 ProPlus for traditional on-premises domain devices, Azure AD registered devices, Azure AD Joined, and Hybrid Azure AD joined devices. OCPS applies to all scenarios above without the need to download and replicate any content such as Administrative Template files (ADMX/ADML) on-premises. The goal of this blog is to provide some transparency of how the service works to help IT Pros during their validation phase and to encourage transition from classic domain-based policy to OCPS service for Office 365 ProPlus.
Requirements of OCPS
1. At least Version 1808 (August 2018) of Office 365 ProPlus
2. User accounts created in or synchronized to Azure Active Directory (AAD). The user must be signed into Office 365 ProPlus with an AAD based account.
3. Security groups created in or synchronized to Azure Active Directory (AAD), with the appropriate users added to those groups.
4. To create a policy configuration, you must be assigned one of the following roles in Azure Active Directory (AAD): Global Administrator, Security Administrator, or Office Apps Admin.
5. Connectivity to addresses below. Microsoft recommends proxy bypasswhitelist for these URLs
*.manage.microsoft.com, *.officeconfig.msocdn.com, config.office.com over 443
Steps to perform proof of concept and validation
1. Create a test user, ours will be “Gottlieb Daimler”, gdaimler@contoso.com.
2. Create security group “OCPS Service Validation” and add user to group within Active Directory Users and Computers.
3. Allow AAD Connect to synchronize user and group to Azure AD. (lunch break 🙂 or force synchronization via commands below)
(optional) From AAD Connect Server and elevated PowerShell, run the following commands:
PS C:WINDOWSsystem32>import-module adsync
PS C:WINDOWSsystem32>Set-ADSyncScheduler -NextSyncCyclePolicyType Delta
PS C:WINDOWSsystem32>Start-ADSyncSyncCycle
Browse Azure AD portal and explore Users – All Users, select Gottlieb Daimler and then Groups. Verify that group “OCPS Service Validation” has been assigned and source says, “Windows Server AD”. This confirms user and group were synced into Azure AD successfully and we can proceed to next steps.
4. Create your first OCPS policy and select “Create” button:

5. Complete input fields, when selecting assigned security group input “OCPS” and service should filter results to “OCPS Service Validation” group. Next, define a policy. For the demo, I chose policy “VBA Macro Notification Settings”, “Enabled” where VBA Macro Notification Settings are set to “Disable all with notification”. Once selections have been made “Create” or “Save”.


6. From Policy Management, we can now see our policy exists.

So, we’ve got a policy, we’ve assigned it to a security group containing our test user, our next step is to validate. My test machine happens to be classic on-premises domain joined machine. My user, Gottlieb Daimler, is signed in with his normal Active Directory credentials which is displayed in upper right hand corner of Word.

Traditional Group Policy uses Client-Side Extensions in Windows to apply policy every 90 minutes. IT Pros can force policy by using command line “gpupdate /force” and inspectverify registry as well as application behavior prior to broad deployment. OCPS checks for policy upon initial Office application launch, calls into cloud service endpoints listed above, determines policy applicability based on group membership and priority assignment and registry keys are populated.
Specifically, there are two locations of interest in registry.
1. HKEY_CURRENT_USERSoftwareMicrosoftOffice16.0CommonCloudPolicy
This will contain information about FetchInterval, 90 minutes is default, as well as record of Last Fetch Time and Last Payload Hash.
2. HKEY_CURRENT_USERSoftwarePoliciesMicrosoftCloud. This key will contain path to registry keys representing the policy assignment. For example, ours will be HKEY_CURRENT_USERSoftwarePoliciesMicrosoftCloudOffice16.0wordsecurity
Vbawarnings = 2 (DWORD)
IT Pros can achieve the same behavior of gpupdate by simply deleting the key HKEY_CURRENT_USERSoftwareMicrosoftOffice16.0CommonCloudPolicy, close Office application and relaunch to fetch policy. I typically use tools like Process Monitor to help trustverify operations of this type with filters such as “Path” contains “CloudPolicy” or where Operation is “RegSetValue” etc. Opening a Word document containing a Macro displaying warning with notification as expected.

FAQ:
How does conflict resolution work if the same policy is set via traditional domain-based policy as well as OCPS?
OCPS takes priority if there are any conflicts with traditional domain-based policies.
Currently policies are limited to user settings. Are there plans on adding machine settings?
Yes. This has been accepted and currently is in our backlog. We hope to have this available next year.
Group Policy provides a view of all policies on the device or for the specified user. Does OCPS support this?
Currently OCPS does not provide a list of all Office policies applied to a specific user or device. This is on our backlog and we hope to have this available next year.
Will OCPS support other platforms such as MacOS, Android and iOS?
Yes, OCPS in the future will also support additional platforms such as MacOS, Android and iOS. We will create additional blog postings per platform once features are generally available.
The Author
This blog post is brought to you by Dave Guenthner, a Senior Premier Field Engineer and “ProPlus Ranger” at Microsoft. Feel free to share your questions and feedback in the comments below.

As an admin, you might have been tasked with the deployment of Office 365 ProPlus to your organization. But such a deployment is more than just Office. After the initial migration to ProPlus, you might have to provide ways for your users to acquire automated installs of additional Language Packs, Proofing Tools, products like Visio and Project or other components.
This blog post will walk your through a concept of building dynamic, lean & universal packages for Office 365 ProPlus, greatly reducing long-term maintenance costs and effort needed in managed environments.
Grab a coffee, it’s a long post. Let’s roll.
The challenge
When you plan your upgrade to Office 365 ProPlus, the actual upgrade from a legacy version to the always-current Office 365 ProPlus is front and center. But looking beyond the initial deployment, there are other scenarios you’ll need to cover as an admin. After you upgraded your users, they might need one of the following components going forward:
- Additional Language Packs
- Proofing Tools
- Visio
- Project
So in managed environments each of the above would require a dedicated installation package in order to allow an automated and controlled way to e.g. install additional languages for a user. Usually, for each of the above components, an admin would combine the necessary source files (~2.5 gigabyte), a copy of the Office Deployment Tool (ODT) together with a configuration file into a package.
But, especially in larger organizations, you often do not run a single installation of Office 365 ProPlus. You might have a mix of update channels (often SAC and SAC-T) and maybe you are currently transitioning from 32 bit to 64 bit, and for quite some time you will have to support both architectures.
So at the end, we would not have one package per component, but rather four, covering each possible permutation of SAC/SAC-T and x86/x64.
The end result would be:
- High number of packages, the four listed components would result in 16 or more packages.
- High bandwidth consumption, as a client might get the full 2.5 GB package pushed down before install
- High maintenance costs to keep embedded source files current.
- High user impact, if you haven’t kept the source files current and installing a component will perform a downgrade, just to perform an update to the current version soon after.
- Low user satisfaction when having to pick the matching package out of a bunch of options.
While the initial upgrade to Office 365 ProPlus is a one-time activity, the above scenarios will be applicable over a longer period as users might need additional components days, weeks or even years after the initial deployment.
So, how do we build packages which are less costly to maintain over a long time frame and avoid the above downsides?
The solution: Dynamic, lean and universal packages
Good news: There is a way to resolve all of the above issues by implementing self-adjusting, small and universal package. I will give you the “meat and potatoes” of the concept before we dive into sample scenarios:
Build
dynamic packages where you don’t hard-code anything. Leverage features of the
Office Deployment Tool (ODT) to allow the packages to self-adjust to the requirements:
- Use Version=MatchInstalled to prevent unexpected updates and stay in control of the version installed on a client. No hard-coding of a build number (which gets outdated quickly) required.
- Use Language=MatchInstalled to instruct e.g. Visio or Project to install with the very same languages which are already installed for Office. No need to list them or build a script which injects the required languages.
Build lean packages by removing the source files from the packages. This has multiple benefits:
- Package size is much smaller, from 2.5 GB down to less than 10 megabytes for the ODT and its configuration file.
- Instead of pushing a 2.5 GB install package to clients, we allow clients to pull what it needs on demand from Office CDN which saves bandwidth:
- When adding Project to an existing Office 365 ProPlus install, we need to download less than 50 megabytes as Office shared components are already installed.
- Visio installs are typically between 100-200 megabytes, based and the number of languages as the templates/stencils are a substantial part of the download.
- Installing Proofing Tools is typically between 30-50 megabytes versus a full Language Pack is somewhere between 200 to 300 megabyte.
- A 2nd install scenario is often less frequent, which lowers the burden on the internet traffic ultimately reducing the impact.
- You don’t have to update the source files every time when Microsoft releases new features, security and quality fixes.
Build universal packages by not hard-coding things like the architecture or update channel. ODT will dynamically match the existing install ; so your packages work across all update channels and architectures. Instead of having e.g. four packages to install Visio, you will have a single, universal package which will work across all permutations of update channels and architectures.
- Leaving out OfficeClientEdition makes your package universal for mixed x86/x64 environments.
- Leaving out Channel makes your package universal across update channels, even ones you don’t support
 .
.
How to and benefit of building dynamic, lean & universal packages
The idea behind this concept is to not hard-coding everything in the configuration file, but rather leverage the cleverness of the Office Deployment Tool (ODT) as much as possible. Let’s have a look at a “classic” package, built to add Project to an existing install of Office 365 ProPlus. We have the source files (~2.5 gigabyte in size) and a configuration file which explicitly states what we want to achieve:
<Configuration>
<Add OfficeClientEdition=”64″ Channel=”Broad”>
<Product ID=”ProjectProRetail”>
<Language ID=”en-us” />
</Product>
</Add>
<Display Level=”None” />
</Configuration>
When applying the concepts of dynamic, lean, universal packages, the result would look like this:

<Configuration>
<Add Version=”MatchInstalled”>
<Product ID=”ProjectProRetail”>
<Language ID=”MatchInstalled” TargetProduct=”O365ProPlusRetail” />
</Product>
</Add>
<Display Level=”None” />
</Configuration>
So what have we changed and what are the benefits of doing so?
- Removed OfficeClientEdition-attribute, as the ODT will automatically match the installed version.
- Benefit: Configuration file now work for both x86 and x64 scenarios.
- Remove Channel, same reason, ODT will automatically match the already assigned update channel.
- Benefit I: Package works for all update channels (Monthly, Semi-Annual, SAC-T, you name it)
- Benefit II: It will also work for update channels you don’t offer as central IT. Some users are running Monthly, some are on Insider builds? Don’t worry, it just works!
- Added Version=MatchInstalled which will ensure that ODT will install the exact same version which is already installed.
- Benefit: You are in control of versions deployed, no unexpected updates.
- Added Language ID=”MatchInstalled” and TargetProduct designed to match the currently installed language(s), replacing a hard-coded list of languages to install.
- Benefit I: User will have the same languages in Project as already installed for Office.
- Benefit II: No need to re-request Language Pack installs.
- Benefit III: Will also work for rarely used languages which you as central IT admin don’t offer, leading to happier users.
- Removed the source files, the ODT will fetch the correct set of source files from the Office CDN just-in-time.
- Benefit I: Package never gets old. No maintenance of source files needed.
- Benefit II: Download is ~50 megabyte instead of pushing 2.5 GB around.
Another example: Adding Language Packs and Proofing Tools the dynamic, lean & universal way
Let’s have a brief look at other scenarios as well, like adding Language Packs and Proofing Tools. The classic configuration file to install the German Language Pack might look like this:
<Configuration>
<Add OfficeClientEdition=”64″ Channel=”Broad”>
<Product ID=”LanguagePack”>
<Language ID=”de-de” />
</Product>
</Add>
<Display Level=”None” />
</Configuration>
If you’re running SAC as well as SAC-T and have a x86/x64 mixed environment, you would need three additional files to cover the remaining permutations of configurations. Or you just go the dynamic, lean and universal way:
<Configuration>
<Add Version=”MatchInstalled”>
<Product ID=”LanguagePack”>
<Language ID=”de-de” />
</Product>
</Add>
<Display Level=”None” />
</Configuration>
This single configuration file will work across x86/x64 and all update channels (Insider Fast, Monthly Targeted, Monthly, SAC-T, SAC, and so on). So if you want to offer 5 additional languages in your environment, just build 5 of these “config file + ODT” packages and you’re good to go. For Proofing Tools you just change the ProductID to “ProofingTools”.
Prerequisites
I hope this new concept helps you to build dynamic, lean and universal packages and reduce the overall effort of managing Office 365 client Apps.
There are some prerequisites you must meet to make this concept work in your environment:
- Use Office Deployment Tool 16.0.11615.33602 or newer to enable Version=MatchInstalled to work.
- The ODT must be able to locate the matching source files on the Office CDN.
- Ensure that the context your using for running the install can traverse the proxy. Check out our Office 365 ProPlus Deployment and Proxy Server Guidance for a deep-dive on this.
- Make sure, that the account (user or SYSTEM) used to install the apps is able to connect to the internet.
The Author
This blog post is brought to you by , a ProPlus Ranger and senior ProPlus deployment expert at Microsoft. Feel free to share your questions and feedback in the comments below.

**12/5/2019 We’ve updated this guidance and published it as an article on docs.microsoft.com: Change the Office 365 ProPlus update channel for devices in your organization. We recommend that you follow the steps in that article to change channels.”
Microsoft recommends enterprise customers include validation as a part of their Office 365 ProPlus deployment processes. Microsoft provides “channels” which control the rate of change in terms of features and quality fixes. For most customer deployments this means a minimum of two channels such as Semi-Annual Channel and Semi-Annual Channel (Targeted). Many IT Pros broadly deploy a single channel (usually Semi-Annual Channel) and leverage group policy to assign validation computers to faster channel such as Semi-Annual Channel (Targeted). In this way, IT Pros can preview what’s coming four months prior to production release.
The goal of the blog is to provide clarification around the mechanics on how Office 365 ProPlus processes channel change requests.
 Tip: New Semi-Annual Channel versions are released in JanuaryJuly and Semi-Annual Channel (Targeted) versions are released in MarchSeptember. All channels will receive a minimum of one build per month which contain security and critical customer escalated fixes. (The latter has very high bar)
Tip: New Semi-Annual Channel versions are released in JanuaryJuly and Semi-Annual Channel (Targeted) versions are released in MarchSeptember. All channels will receive a minimum of one build per month which contain security and critical customer escalated fixes. (The latter has very high bar)
To read more about Channels please see Overview of update channels for Office 365 ProPlus
Ideally, minimizing the number of Office 365 ProPlus packages reduces overall cost of ownership. Therefore, the next step is to develop a process where machines receive standard package placing them on Semi-Annual Channel but dynamically move validation machines to faster channel such as Semi-Annual Channel (Targeted).
Step 1: Deploy your standard Office 365 ProPlus package based on Semi-Annual Channel
Step 2: Assign GPO to validation machine(s) or add policy registry key specifying Semi-Annual Channel (Targeted)
Using Office ADMX files, use Update Channel GPO to set Semi-Annual Channel (Targeted)

* Group Policy refreshes in the background every 90 minutes by default. Use gpupdate /force to expedite. Alternatively, add registry key manually to policy key
HKLMSOFTWAREPoliciesMicrosoftoffice16.0commonofficeupdate “updatebranch”=”FirstReleaseDeferred”
Step 3: Allow MicrosoftOfficeOffice Automatic Updates 2.0 scheduled task to run
Group Policy will set registry keys, that’s all. Office 365 ProPlus uniquely leverages a scheduled task named Office Automatic Updates to maintain product configuration including channel management. The name itself “Automatic Updates” can cause confusion for IT Pros in enterprise environments where System Center Configuration (SCCM) is used to deploy updates. When OfficeMgmtCom (COM) is enabled, updates will be delivered only from SCCM. The Office Automatic Updates scheduled task will fire based on default set of triggers, regardless if COM is enabled or not, or by manually running task you can compress time frame to validate change.
 Microsoft recommends Automatic Updates remain Enabled (default configuration) in all update scenarios. This task does more than name implies. By disabling task, you may observe diminished experience in terms of channel management and disable feature to apply updates when SYSTEM is IDLE.
Microsoft recommends Automatic Updates remain Enabled (default configuration) in all update scenarios. This task does more than name implies. By disabling task, you may observe diminished experience in terms of channel management and disable feature to apply updates when SYSTEM is IDLE.
See 2:00 in Managing Office with SCCM (2019) video for more information, applicable for CDN update workflow.
 Tip: List of Channels and respective URL identifiers
Tip: List of Channels and respective URL identifiers
CDNBaseUrl represents the channel where product was installed. If no channel was defined in unattend, Semi-Annual Channel is default selection.
Monthly Channel
(formerly Current Channel):
CDNBaseUrl = http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60
Semi-Annual Channel
(formerly Deferred Channel):
CDNBaseUrl = http://officecdn.microsoft.com/pr/7ffbc6bf-bc32-4f92-8982-f9dd17fd3114
Monthly Channel (Targeted)
(formerly First Release for Current Channel):
CDNBaseUrl = http://officecdn.microsoft.com/pr/64256afe-f5d9-4f86-8936-8840a6a4f5be
Semi-Annual Channel (Targeted)
(formerly First Release for Deferred Channel):
CDNBaseUrl = http://officecdn.microsoft.com/pr/b8f9b850-328d-4355-9145-c59439a0c4cf
 Tip: IT Pros can monitor several registry keys to validate change has occurred after scheduled task has completed. Registry keys of interest when monitoring can be found under the following key: HKLMSOFTWAREMicrosoftOfficeClickToRunConfiguration. Editing key(s) should not be done directly and can lead to unintended consequences. Rather, monitor keys for desired outcome.
Tip: IT Pros can monitor several registry keys to validate change has occurred after scheduled task has completed. Registry keys of interest when monitoring can be found under the following key: HKLMSOFTWAREMicrosoftOfficeClickToRunConfiguration. Editing key(s) should not be done directly and can lead to unintended consequences. Rather, monitor keys for desired outcome.
UpdateChannel: This is the channel configuration “winner”. This is dynamically managed by the Automatic Updates scheduled task and should not be edited directly.
In our example where we are using GPO to move Office 365 ProPlus to Semi-Annual Channel (Targeted), Office Automatic Updates scheduled task will discover policy key and then will flip UpdateChannel to new value, in this case from http://officecdn.microsoft.com/pr/7ffbc6bf-bc32-4f92-8982-f9dd17fd3114 (SAC) to http://officecdn.microsoft.com/pr/b8f9b850-328d-4355-9145-c59439a0c4cf (SAC-T). Additionally, UpdateChannelChanged will be set to True. Upon next successful Office 365 Client update, UpdateChannelChanged will reset to False. The product can only accept one channel change request at a time with successful update as a prerequisite prior to accepting another change.
If you have completed steps above and channel change is still not being reflected, you may be blocked by temporary “Discovery Period.” Generally, updates will not happen within the Discovery Period which can last up to 24 hours after initial installation. IT Pros may encounter this scenario during compressed time validation in lab scenarios.
After UpdateChannel has successfully changed, Office 365 Clients pointing to CDN will download latest build from faster channel. Office 365 Clients which have COM enabled for SCCM integration will download newer build next time Software Updates Deployment Evaluation cycle runs based on configuration of Software Deployment within SCCM. IT Pros can expedite testing channel migration by deploying desired build to validation collection (should be a build from Semi-Annual Channel (Targeted), use the Configuration Manager applet from control panel to perform Machine Policy Retrieval followed by Software Updates Deployment Evaluation Cycle.

 Tip: Office 365 ProPlus behavior – slow to fast vs fast to slow
Tip: Office 365 ProPlus behavior – slow to fast vs fast to slow
Slower -> Faster (Example: Semi-Annual Channel to Semi-Annual Channel Targeted)
- Client will always gracefully move forward when now available build number is higher. For example, a client on June 2019 Semi-Annual Channel with build version 1808 (Build 10730.20348) will move to Semi-Annual Channel Targeted with build Version 1902 (Build 11328.20318). No other Administrative intervention is required, normal update processworkflow applies the change.
Faster -> Slower (Example: SAC-T to SAC)
- In SCCM managed environment where COM is enabled, Office will not auto downgrade when channel is changed. It will only move forward once build advertised is greater than what’s currently installed. For example, Office ProPlus client on Semi-Annual Targeted build June 2019 Version 1902 (Build 11328.20318) will have to wait until Semi-Annual Channel build number is greater to move forward such as July 2019 Version 1902 (Build 11328.20368). Supported downgrade method is to re-run Office Deployment Tool (ODT) with desired build and channel. Keep in mind during waiting period, Office 365 Client will not receive any updates including security.
- In non COM managed environment such as default configuration CDN, we will downgrade your new version to match the Group Policy assigned.
*Since we can’t do binary delta compression (BDC) the download will be larger. As a result, network considerations should be considered when downgrading from CDN.
FAQ:
How does channel management work when Office 2019 is installed and GPO “Upgrade Office 2019 to Office 365 ProPlus” is enabled?
Some customers may have a need to have one factory image of Windows which includes Office 2019 and later upgrade a subset of machines to Office 365 ProPlus. The steps outlined above still apply in terms of mechanics and how channel chnages are processed. The only difference is Office 2019 will initially have CDNBaseURL and UpdateChannel will reflect http://officecdn.microsoft.com/pr/f2e724c1-748f-4b47-8fb8-8e0d210e9208. First, the GPO above will set policy key. Second, The Office Automatic Updates 2.0 scheduled task will flip the UpdateChannel to Semi-Annual Channel (3114) by default and dynamically convert the product to Semi-Annual Channel. In short, Office 2019 is just an older version of Office 365 ProPlus, so differences in content between the two products will download from CDN or from SCCM Distribution Point depending on your configuration. (Size will be significant for one-time conversion). For CDN, this process is automatic. For SCCM, IT Pro only needs to deploy latest Semi-Annual Channel build software update to collection, just like any monthly “Patch Tuesday” process. SCCM will find build applicable and upgrade like any other Office update. LicensingActivation will switch from volume activation (KMS) to subscription based (Office Licensing Service).
Why does this guidance differ from SCCM page Change the update channel after you enable Office 365 clients to receive updates from Configuration Manager?
Microsoft recommends customers leverage Group Policy to change Office 365 ProPlus channels because its easier for IT Pros. Group Policy sets registry key under policy hive and Office Automatic Updates scheduled task to processes channel change. The link above references CDNBaseURL. Notice from the list below this is the 4th item evaluated for priority by the scheduled task. As a result, if the first three priorities listed are not configured and CDNBaseURL doesn’t match UpdateChannel, scheduled task will align them resulting in channel change. This blog posting leads with Group Policy where link above requires a direct registry change through Group Policy Preferences or Compliance Item in SCCM.
1st Priority : GPO "UpdatePath" - HKLMsoftwarepoliciesmicrosoftoffice16.0commonofficeupdate!updatepath
2nd Priority : GPO "UpdateChannel" - HKLMsoftwarepoliciesmicrosoftoffice16.0commonofficeupdate!updatebranch
3rd Priority : "UpdateURL" or UpdatePath="ServerShare" HKLMSOFTWAREMicrosoftOfficeClickToRunConfiguration
4th Priority : CDNBaseURL - HKLMSOFTWAREMicrosoftOfficeClickToRunConfigurationCDNBaseUrl
I hope this blog post helps provide additional context for how Office ProPlus Channel Management works “under the hood”.
This blog post is brought to you by Dave Guenthner, a Senior Premier Field Engineer and “ProPlus Ranger” at Microsoft. Feel free to share your questions and feedback in the comments below.
![How to secure your remote workers with Office Cloud Policy Service]()
Office 365 Groups is the membership service that drives teamwork and powers collaboration across Microsoft 365. With Office 365 Groups, a group of people can access and share a collection of collaboration resources, such as a shared Outlook inbox, calendar, SharePoint document library, a Planner, a Team, and more.
Recently, at Microsoft Ignite 2019 in Orlando, FL, the Office 365 Groups team delivered several session that included announcements of enhancements and new innovations for Office 365 Groups, such as new user activity-based expiration policy for Office 365 Groups, and the Groups Admin role, and best practices, such as creating a governance plan, enabling self-service, and leveraging analytics to understand usage.
The Office 365 Groups breakout sessions highlighted innovations across Outlook Mobile, Outlook Desktop, Outlook on the Web, Microsoft Teams, Microsoft 365 admin center, SharePoint Site URL Rename, Identity Governance, Yammer, and more. In case you missed it, you can view the Office 365 Groups sessions on-demand, and download the slide decks, as well.
| Session Code |
Description |
| ADM20 |
Addressing top management issues with users and groups |
| BRK2052 |
What’s new and what’s next: SharePoint and OneDrive administration |
| BRK2056 |
Embrace Office 365 Groups: What’s new and what’s next |
| BRK2058 |
Deploy Office 365 groups at scale to power Microsoft Teams, Outlook, Yammer, and SharePoint |
| BRK2210 |
Finding your collaboration sweet spot with Office 365 Groups, SharePoint, Teams, and Yammer |
| BRK2233 |
The future of Yammer: Share knowledge, engage leaders, and build communities in Microsoft 365 |
| BRK3264 |
Transform collaboration and fight shadow IT with Office 365 groups |
| THR2091 |
Master sharing and permissions of Office 365 in 20 minutes |
| THR2251 |
How Microsoft empowers employees through self-service collaboration while still protecting the company in Office 365 |
| THR3043 |
Microsoft Teams and Office 365 Groups PowerShell MasterClass |
| THR3083 |
Office 365 Groups: Ask us anything |
We’re also taking the learning path session for Office 365 Groups (Embrace Office 365 Groups: What’s new and what’s next) on the Microsoft Ignite The Tour, so if you would like to see it live, and interact with Office 365 Groups experts, register now for a city near you.

–The Office 365 Groups Team

At Microsoft, we’re committed to protecting your data and helping your organization stay current and secure in today’s fast-moving, complex technology environment. And we’ve designed new innovations for Office 365 ProPlus to do just that. As announced at Microsoft Ignite 2019 last week, we introduced:
- An update to the Office cloud policy service.
- Deeper integration for managing Office 365 for Mac using Jamf Pro.
- New tools for Configuration Manager to better plan Office deployment projects.
- New security features for the Office client.
- New Group Policy setting to enable users to install Insider builds.
Together, these new functionalities help you more efficiently adopt, deploy, and manage Office 365 ProPlus—regardless of the size of your organization and the platform you choose.
Cross-platform support* for the Office cloud policy service
The Office cloud policy service—initially announced for Windows earlier this year—is a cloud-based service that enables IT admins to enforce policy settings for Office 365 ProPlus users. The settings are enforced across devices, whether domain-joined, Azure Active Directory (AAD)-joined, or completely unmanaged. In short, the policy settings roam with the user.
Today, we’re introducing an update to add cross-platform support for Office on the web, Android, Mac*, and iOS* devices, giving administrators the ability to manage Office policies from a single portal for all their Office users. To learn more, read this article.
Easier Office 365 for Mac management using Jamf Pro
Today, we’re announcing deeper integration for managing Office 365 using Jamf Pro. Our integration with the new Application and Custom Settings experience, which was demonstrated at the Jamf Nation User Conference (JNUC), allows IT admins to easily set Office 365 policies using a familiar forms-based interface. Mac administrators can centrally configure security, privacy, and update policies to deliver the very best Office 365 experience to their users, including:
- Enabling friction-free sign-on to Office 365
- Controlling privacy and telemetry options
- Reducing the attack surface for sensitive devices
- Increasing compliance levels through feature enablement
- Lowering support costs by implementing desired update workflows
Pilot health and inventory tools to deploy faster
We’ve brought a pair of updates to the Microsoft System Center Configuration Manager—you probably know it as Config Manager—to help IT admins streamline parts of the device upgrade process. The first of these shows the health of pilot devices as it relates to a forthcoming upgrade. Pilots are a subset of devices you’ve selected to validate before deploying. With this update, that subset will also show the upgraded health of selected devices, including which are ready to upgrade right now. For those not ready, you can see what issues are blocking the upgrade and remediate those for faster deployment.
The second update, which enhances your existing inventory tools, leverages device telemetry to determine which devices running Office 365 ProPlus are ready to update to newer release. This update also provides insight into issues that are blocking an immediate upgrade, giving you the information needed to remediate problem areas.
Pilot health and enhanced inventory tools are just the beginning. With 80% of Office 365 ProPlus admins using Config Manager, we’re continuing to prioritize upgrades for the Config Manager console—including features like recommended configurations.
Safe Documents and Application Guard for enhanced file protection
On Tuesday, we shared Safe Documents, a new capability that brings the power of Microsoft Defender Advanced Threat Protection (ATP) to Office 365 ProPlus. When a user has a document in Protected View and wants to consider that document “trusted”, the field will be automatically checked against the ATP threat cloud before release. Admins will have advanced visibility and response capabilities, including alerts, logs, and visibility into similar threats across the enterprise.
We also showed an early, live demo of Application Guard capabilities integrated with Office 365 ProPlus. When available in mid-2020, Microsoft 365 customers will be able to open an untrusted Word, Excel, or PowerPoint file in a virtualized container instead of Protected View. From there, users will be able to view, print, edit, and save changes to untrusted Office documents—all while benefiting from hardware-level security. If the untrusted file is malicious, the attack is confined to the isolated container and the host machine is untouched. Users will be able to leverage Safe Documents to “trust” a document securely, and full reporting and audit trails will be available through ATP.
Group Policy to allow users to experience Office Insider builds
Enabling your users to self-select into the Office Insiders program is as simple as delivering a policy. This can be done by using the Office Cloud Policy service which is available in config.office.com and via group policy. This policy makes it easy for you to enable which users can self-select their device to receive the Office Insider builds as they become available in order to try new features. Read more in this article.
Microsoft Teams deployed with Office 365 ProPlus
As a quick reminder, when you update to Version 1908 of Office 365 ProPlus in January, Microsoft Teams will be rolled out to existing installations on the Semi-Annual Channel. Learn more about deploying Teams as part of Office 365 ProPlus in this article.
Office 2010 End of Support
Finally, support for Office 2010 is ending in October 2020—but with Office 365 ProPlus, you can continue to stay current with the latest Office tools and security features, like the ones we described above. Read more in this blog.
Catch up on all other Office 365 ProPlus deployment content recorded at Ignite by following this guide. As always, learn what’s new in Office 365 ProPlus, watch our YouTube Deployment Insider channel, and join Office Insider Program.
You may also find the following additional resources useful:
*Office cloud policy service support for Mac and iOS devices is expected to roll out soon.
From your flashes of inspiration at 2:00 AM to the list of funny things your children say, or that brilliant idea you had in the conference room, and your ever-growing list of household chores — OneNote holds the notes to your life to track all the things you need to keep in mind, but simply don’t have room for in your overworked brain.
We enjoy the privilege of serving millions of customers like you, who each have unique needs and who use OneNote in unique ways. Over the past year, we’ve been listening to your passionate feedback and are humbled by your consistent love for OneNote. We hear you loud and clear — you want to keep your notes your way!
With that in mind, we’re pleased to announce that we are continuing mainstream support for OneNote 2016 beyond October 2020, so that you can continue using the version of OneNote that works best for you. New support dates for OneNote 2016 now align with Office 2019 (October 10, 2023 for mainstream support and October 14, 2025 for extended support). We also want to make deployment and installation easier for organizations and individuals, so for Windows users, starting in March 2020, when you deploy or install Office 365 subscriptions that include the Office desktop apps or Office 2019, the OneNote desktop app will be installed by default alongside Word, Excel, and PowerPoint. If you’d like to install OneNote 2016 earlier, you can get it here: aka.ms/InstallOneNote.
And, of course, OneNote should look the way you want it to. That’s why this week we are rolling out Dark Mode for OneNote 2016. This will be available for Office 365 subscribers and non-volume licensing Office 2019 customers. Dark Mode changes the app’s interface elements from light to dark. Using OneNote in this mode can improve readability in low light environments, increase legibility of the user interface as well as your notes, provide better contrast, and reduce eye strain. You might also use OneNote in Dark Mode simply as a personal preference. The choice is yours!
We’re excited about today’s announcements and we’ll keep listening to your feedback to make your OneNote better and better! Please continue requesting features and telling us what you think via the in-app feedback.
For more information check out our OneNote FAQ!
![How to secure your remote workers with Office Cloud Policy Service]()
Update: This feature has new updates. Please see the blog for details.
—
O365 Groups power collaboration across Office 365
Collaboration is a key ingredient for the success of any organization. Office 365 groups, of the most used collaboration features in Microsoft 365 today, power the collaboration features across apps, including Outlook, Teams, Yammer, and SharePoint. Employees can create groups quickly and start collaborating with co-workers by sharing group documents, emails, and calendars.
The twin problems of Groups Life cycle Management
As the number of Office 365 groups increases, an organization needs to strike a balance between cleaning up unused groups and ensuring any valuable groups do not get deleted unintentionally, causing data loss. Many of you have shared feedback about these challenges in groups lifecycle management.
You say, we listen and act
We heard your feedback, and we’ve made some changes! We are excited to announce the new version of expiration policy which ensures any group being actively used continues to be available, circumventing expiration. This feature makes life easier for users, including admins, group owners and members, by automating the expiration and renewal process by tracking groups for user activity across different apps, like Teams, SharePoint, Outlook, tied to the group.
The new expiration policy puts group life cycle management on autopilot
The current Expiration policy allows you to set an expiration time frame for selected or all Office 365 groups . After the defined group lifetime, owners are asked to renew them if they are still needed. With this newly added intelligence, groups which are being actively used will be automagically renewed. This preempts the need for any manual action on the part of the group owners. This is based on user activity in groups across Office 365 apps like Outlook, SharePoint, Teams, Yammer, and others.
Example: At Contoso, the administrator has configured the Group lifetime to be 180 days. Megan is the owner of the Contoso Marketing O365 Group, with Enrico and Alex as its members. Her group is set to expire in 45 days. If an owner or a member performs actions like uploading a document in SharePoint, visiting Teams channel or sending an email to the group in Outlook, the group is automatically renewed for another 180 days, and she does not get any expiry notifications.

Manual Controls: Group owners will continue to have the manual “delete”, “renew” option for granular control.
Soft Delete: Like before, groups which aren’t renewed (either automatically based on activity or manually) will be soft deleted. Groups in “Soft-delete” state can still be restored within 30 days, after which the content is deleted permanently.

User actions for group auto-renewal: The following user actions will lead to automatic renewal of groups
- SharePoint – View, Edit, Download, Move, Share, Upload Files
- Outlook – Join group, Read/write group message from group space, Like a message (OWA)
- Teams – Visit a Teams channels
We will continue to update this list to fine tune group auto-renewal experience.
Auditing and reporting: Administrators can get a list of auto-renewed groups from audit logs on the azure portal.

Here are some quick steps to get you started.
Getting started
Office 365 groups expiration policy can be configured from the Azure Active Directory portal, as well as programmatically via Azure Active Directory PowerShell. Please note you need an Azure AD Premium license. Below is a quick tutorial on how to get started with the functionality in the new Azure portal experience.
1. Create Expiration Policy: Sign into the Azure portal, select Azure Active Directory, go to the Groups tab and select Expiration under Settings. (More details here) .
2. Set Group Life cycle: Specify the group lifetime in days and select which groups you want the expiration settings to apply to.
Group owners will receive a renewal notification 30 days before the expiration date, and from that notification they can renew their group with a single click!
If there is no user activity in the group (and the owners don’t manually renew their group) within the required time frame, their group will expire. Upon expiry it will stay in a “soft deleted” state for 30 days. Owners of deleted groups will receive a notification letting them know their group has been deleted and giving them the opportunity to restore their group within 30 days after its deletion date. The Group will be permanently deleted after 30 days.
3. Auto-renewal based on user activity: No explicit action is required to enable activity-based auto-renewal. If an the expiration policy is set for Office 365 groups, auto-renewal will be enabled by default.
Learn more about how you can restore you group to recover all its content, including SharePoint, Planner, and Outlook – how to restore deleted Office 365 groups.
Note: The new version of Office 365 groups expiration feature is available in private preview today for select Azure AD Premium customers. Please reach out to your TAMs/CSMs regarding enrollment in private preview.
Let us know what you think!
We would love to hear your feedback! If you have any suggestions for us, questions, or issues to report, please leave a comment below. We’re always looking for ways to improve.
User Voice: Add security groups to Office 365 groups
Support & feedback: groupsarfeedback@microsoft.com
Best regards,
Salil Kakkar Yuan Karppanen
Program Manager Program Manager
Office 365 Groups Azure Active Directory
 @salil_kakkar
@salil_kakkar
![How to secure your remote workers with Office Cloud Policy Service]()
O365 Groups power collaboration across Office 365
Collaboration is a key ingredient for the success of any organization. Office 365 groups, of the most used collaboration features in Microsoft 365 today, power the collaboration features across apps, including Outlook, Teams, Yammer, and SharePoint. Employees can create groups quickly and start collaborating with co-workers by sharing group documents, emails, and calendars.
The twin problems of Groups Life cycle Management
As the number of Office 365 groups increases, an organization needs to strike a balance between cleaning up unused groups and ensuring any valuable groups do not get deleted unintentionally, causing data loss. Many of you have shared feedback about these challenges in groups lifecycle management.
You say, we listen and act
We heard your feedback, and we’ve made some changes! We are excited to announce the new version of expiration policy which ensures any group being actively used continues to be available, circumventing expiration. This feature makes life easier for users, including admins, group owners and members, by automating the expiration and renewal process by tracking groups for user activity across different apps, like Teams, SharePoint, Outlook, tied to the group.
The new expiration policy puts group life cycle management on autopilot
The current Expiration policy allows you to set an expiration time frame for selected or all Office 365 groups . After the defined group lifetime, owners are asked to renew them if they are still needed. With this newly added intelligence, groups which are being actively used will be automagically renewed. This preempts the need for any manual action on the part of the group owners. This is based on user activity in groups across Office 365 apps like Outlook, SharePoint, Teams, Yammer, and others.
Example: At Contoso, the administrator has configured the Group lifetime to be 180 days. Megan is the owner of the Contoso Marketing O365 Group, with Enrico and Alex as its members. Her group is set to expire in 45 days. If an owner or a member performs actions like uploading a document in SharePoint, visiting Teams channel or sending an email to the group in Outlook, the group is automatically renewed for another 180 days, and she does not get any expiry notifications.

Manual Controls: Group owners will continue to have the manual “delete”, “renew” option for granular control.
Soft Delete: Like before, groups which aren’t renewed (either automatically based on activity or manually) will be soft deleted. Groups in “Soft-delete” state can still be restored within 30 days, after which the content is deleted permanently.

User actions for group auto-renewal: The following user actions will lead to automatic renewal of groups
- SharePoint – View, Edit, Download, Move, Share, Upload Files
- Outlook – Join group, Read/write group message from group space, Like a message (OWA)
- Teams – Visit a Teams channels
We will continue to update this list to fine tune group auto-renewal experience.
Auditing and reporting: Administrators can get a list of auto-renewed groups from audit logs on the azure portal.

Here are some quick steps to get you started.
Getting started
Office 365 groups expiration policy can be configured from the Azure Active Directory portal, as well as programmatically via Azure Active Directory PowerShell. Please note you need an Azure AD Premium license. Below is a quick tutorial on how to get started with the functionality in the new Azure portal experience.
1. Create Expiration Policy: Sign into the Azure portal, select Azure Active Directory, go to the Groups tab and select Expiration under Settings. (More details here) .
2. Set Group Life cycle: Specify the group lifetime in days and select which groups you want the expiration settings to apply to.
Group owners will receive a renewal notification 30 days before the expiration date, and from that notification they can renew their group with a single click!
If there is no user activity in the group (and the owners don’t manually renew their group) within the required time frame, their group will expire. Upon expiry it will stay in a “soft deleted” state for 30 days. Owners of deleted groups will receive a notification letting them know their group has been deleted and giving them the opportunity to restore their group within 30 days after its deletion date. The Group will be permanently deleted after 30 days.
3. Auto-renewal based on user activity: No explicit action is required to enable activity-based auto-renewal. If an the expiration policy is set for Office 365 groups, auto-renewal will be enabled by default.
Learn more about how you can restore you group to recover all its content, including SharePoint, Planner, and Outlook – how to restore deleted Office 365 groups.
Note: The new version of Office 365 groups expiration feature is available in private preview today for select Azure AD Premium customers. Please reach out to your TAMs/CSMs regarding enrollment in private preview.
Let us know what you think!
We would love to hear your feedback! If you have any suggestions for us, questions, or issues to report, please leave a comment below. We’re always looking for ways to improve.
User Voice: Add security groups to Office 365 groups
Support & feedback: groupsarfeedback@microsoft.com
Best regards,
Salil Kakkar Yuan Karppanen
Program Manager Program Manager
Office 365 Groups Azure Active Directory
 @salil_kakkar
@salil_kakkar
















