
Investigative Tools to Empower Stronger Threat Protection
We launched Office 365 Threat Intelligence to help organization’s become more secure by enhancing admin capabilities which offer greater visibility, deeper insights, and powerful executable actions (check out the recent webinar overviewing the service). Today we’re excited to announce ‘Threat Trackers’ for Office 365 Threat Intelligence, enabling efficient monitoring and management of threat investigations to help admins quickly remediate and respond to threats. The feature can be found under ‘Threat Management’ in the Security and Compliance Center. Table 1 summarizes the four available ‘Threat tracker’ categories.
 Table 1. The different tracker categories available in Office 365 Threat Intelligence Threat Trackers view
Table 1. The different tracker categories available in Office 365 Threat Intelligence Threat Trackers view
Threat Tracker Categories
Noteworthy campaigns are classified, as well known and important global threats. Office 365 Threat Intelligence pre-builds Noteworthy Campaign monitors, enabling admins to quickly review the impact of these threats, assessing both their volume and frequency. This automated monitoring allows admins speedy remediation from these threats. Noteworthy Campaign monitors update hourly, showing the latest impact of these threats to your organization. Click ‘Explore’ if you want to see the detailed events detected by the filter.
The Trending Campaigns view provides dynamic assessments of email threats impacting your organization’s Office 365 environment. This view shows tenant level malware trends, identifying malware families on the rise, flat, or declining, giving admins greater insight into which threats require further attention. New threats not seen recently in your organization will appear at the top of the page (sorted by trend). Trending Campaigns also offers a comparative view on how a threat impacts your organization versus others. If an organization’s targeting percentage is >10%, it indicates that it is being specifically targeted by the attack. Admins can further investigate targeted and trending attacks in Explorer, where actions such as deleting or moving the malware to junk can be taken. Targeted attacks are typically short-lived, so these types of attacks in the Trending Campaigns view may drop out of the view within a few days.
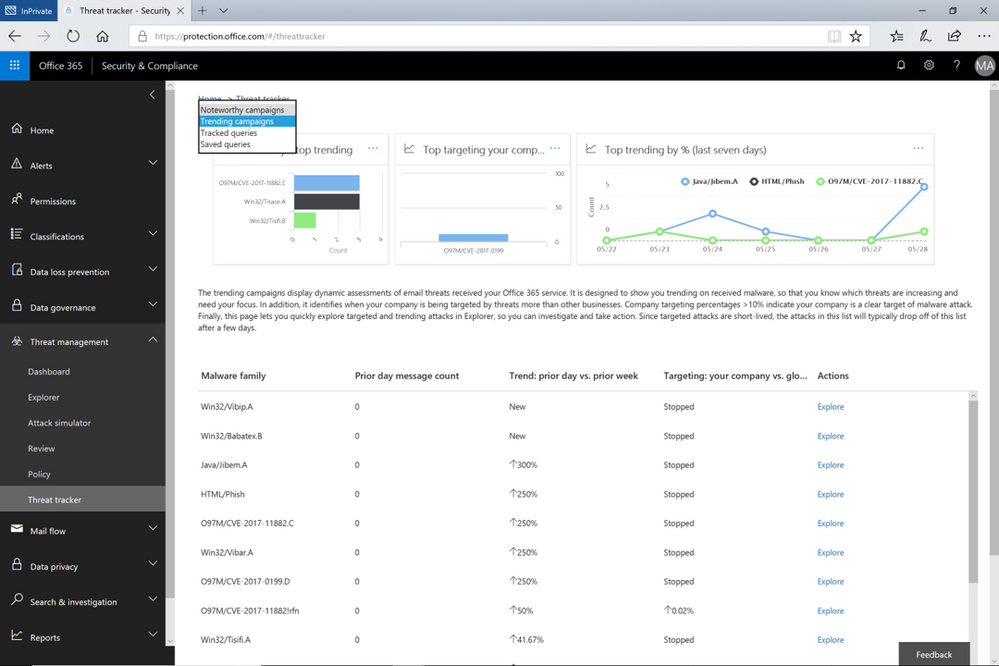 Figure 1. The Trending Campaigns view in Office 365 Threat Intelligence Threat trackers
Figure 1. The Trending Campaigns view in Office 365 Threat Intelligence Threat trackers
While the campaign views enable tracking and quick assessment of threats, queries are powerful investigative views allowing deeper understanding of threats, aiding admins to make data driven security updates. Queries can be accessed from either campaign view by clicking on ‘Explorer’ which displays that tracked threat campaign. Saved Queries provides a view into all Explorer searches saved as queries. Admins can monitor malware and phish events with the scope (number of emails included in an incident) defined and saved from Explorer. Saved queries are useful for checking items frequently. To create more saved queries, go to the Explorer, add filters to view specific sets of events, then select ‘Save query’ (button at top of page).
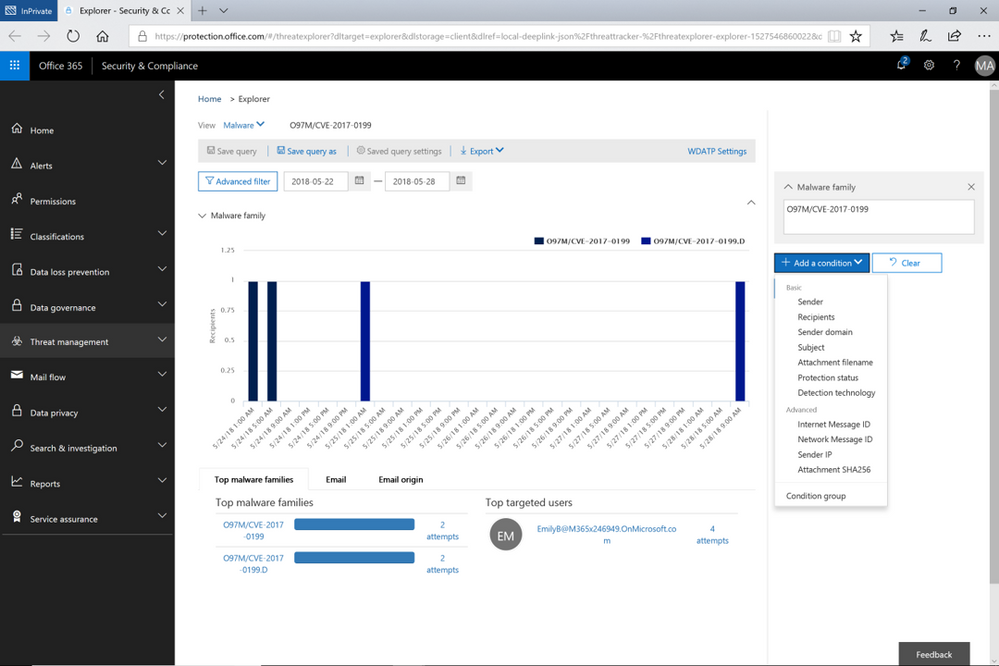 Figure 2. Opened Explorer page on tracked threat campaign. The threat campaign can be saved as query from the Explorer
Figure 2. Opened Explorer page on tracked threat campaign. The threat campaign can be saved as query from the Explorer
Tracked queries provide regular assessments of malware, phish, and other events with the scope defined from Threat Explorer. Tracked queries help monitor items frequently, providing reports, allowing quick and in-depth evaluation of threats or groups. A limited number of tracked queries are available for each organization. Admins can choose to convert saved queries and begin tracking them using the edit option for that query.
These ‘Threat Trackers’ enrich the admin experience, providing a powerful new tool for monitoring and managing, investigations, which ultimately enables quick response to threats. With this added feature, Office 365 Threat Intelligence provides admins to more efficiently and easily secure their organization.
Send Us Your Feedback
Let us know what you think of the new Threat trackers feature by beginning an Office 365 E5 trial today to experience the powerful capabilities of Office 365 Threat Intelligence. Your feedback enables us to make updates and enhancements to provide you with the best protection for Office 365. Please watch our recent webinar on Office 365 Threat Intelligence to learn further details on how the service can help your organization become more secure.

Investigative Tools to Empower Stronger Threat Protection
We launched Office 365 Threat Intelligence to help organization’s become more secure by enhancing admin capabilities which offer greater visibility, deeper insights, and powerful executable actions (check out the recent webinar overviewing the service). Today we’re excited to announce ‘Threat Trackers’ for Office 365 Threat Intelligence, enabling efficient monitoring and management of threat investigations to help admins quickly remediate and respond to threats. The feature can be found under ‘Threat Management’ in the Security and Compliance Center. Table 1 summarizes the four available ‘Threat tracker’ categories.
 Table 1. The different tracker categories available in Office 365 Threat Intelligence Threat Trackers view
Table 1. The different tracker categories available in Office 365 Threat Intelligence Threat Trackers view
Threat Tracker Categories
Noteworthy campaigns are classified, as well known and important global threats. Office 365 Threat Intelligence pre-builds Noteworthy Campaign monitors, enabling admins to quickly review the impact of these threats, assessing both their volume and frequency. This automated monitoring allows admins speedy remediation from these threats. Noteworthy Campaign monitors update hourly, showing the latest impact of these threats to your organization. Click ‘Explore’ if you want to see the detailed events detected by the filter.
The Trending Campaigns view provides dynamic assessments of email threats impacting your organization’s Office 365 environment. This view shows tenant level malware trends, identifying malware families on the rise, flat, or declining, giving admins greater insight into which threats require further attention. New threats not seen recently in your organization will appear at the top of the page (sorted by trend). Trending Campaigns also offers a comparative view on how a threat impacts your organization versus others. If an organization’s targeting percentage is >10%, it indicates that it is being specifically targeted by the attack. Admins can further investigate targeted and trending attacks in Explorer, where actions such as deleting or moving the malware to junk can be taken. Targeted attacks are typically short-lived, so these types of attacks in the Trending Campaigns view may drop out of the view within a few days.
 Figure 1. The Trending Campaigns view in Office 365 Threat Intelligence Threat trackers
Figure 1. The Trending Campaigns view in Office 365 Threat Intelligence Threat trackers
While the campaign views enable tracking and quick assessment of threats, queries are powerful investigative views allowing deeper understanding of threats, aiding admins to make data driven security updates. Queries can be accessed from either campaign view by clicking on ‘Explorer’ which displays that tracked threat campaign. Saved Queries provides a view into all Explorer searches saved as queries. Admins can monitor malware and phish events with the scope (number of emails included in an incident) defined and saved from Explorer. Saved queries are useful for checking items frequently. To create more saved queries, go to the Explorer, add filters to view specific sets of events, then select ‘Save query’ (button at top of page).
 Figure 2. Opened Explorer page on tracked threat campaign. The threat campaign can be saved as query from the Explorer
Figure 2. Opened Explorer page on tracked threat campaign. The threat campaign can be saved as query from the Explorer
Tracked queries provide regular assessments of malware, phish, and other events with the scope defined from Threat Explorer. Tracked queries help monitor items frequently, providing reports, allowing quick and in-depth evaluation of threats or groups. A limited number of tracked queries are available for each organization. Admins can choose to convert saved queries and begin tracking them using the edit option for that query.
These ‘Threat Trackers’ enrich the admin experience, providing a powerful new tool for monitoring and managing, investigations, which ultimately enables quick response to threats. With this added feature, Office 365 Threat Intelligence provides admins to more efficiently and easily secure their organization.
Send Us Your Feedback
Let us know what you think of the new Threat trackers feature by beginning an Office 365 E5 trial today to experience the powerful capabilities of Office 365 Threat Intelligence. Your feedback enables us to make updates and enhancements to provide you with the best protection for Office 365. Please watch our recent webinar on Office 365 Threat Intelligence to learn further details on how the service can help your organization become more secure.

Investigative Tools to Empower Stronger Threat Protection
We launched Office 365 Threat Intelligence to help organization’s become more secure by enhancing admin capabilities which offer greater visibility, deeper insights, and powerful executable actions (check out the recent webinar overviewing the service). Today we’re excited to announce ‘Threat Trackers’ for Office 365 Threat Intelligence, enabling efficient monitoring and management of threat investigations to help admins quickly remediate and respond to threats. The feature can be found under ‘Threat Management’ in the Security and Compliance Center. Table 1 summarizes the four available ‘Threat tracker’ categories.
 Table 1. The different tracker categories available in Office 365 Threat Intelligence Threat Trackers view
Table 1. The different tracker categories available in Office 365 Threat Intelligence Threat Trackers view
Threat Tracker Categories
Noteworthy campaigns are classified, as well known and important global threats. Office 365 Threat Intelligence pre-builds Noteworthy Campaign monitors, enabling admins to quickly review the impact of these threats, assessing both their volume and frequency. This automated monitoring allows admins speedy remediation from these threats. Noteworthy Campaign monitors update hourly, showing the latest impact of these threats to your organization. Click ‘Explore’ if you want to see the detailed events detected by the filter.
The Trending Campaigns view provides dynamic assessments of email threats impacting your organization’s Office 365 environment. This view shows tenant level malware trends, identifying malware families on the rise, flat, or declining, giving admins greater insight into which threats require further attention. New threats not seen recently in your organization will appear at the top of the page (sorted by trend). Trending Campaigns also offers a comparative view on how a threat impacts your organization versus others. If an organization’s targeting percentage is >10%, it indicates that it is being specifically targeted by the attack. Admins can further investigate targeted and trending attacks in Explorer, where actions such as deleting or moving the malware to junk can be taken. Targeted attacks are typically short-lived, so these types of attacks in the Trending Campaigns view may drop out of the view within a few days.
 Figure 1. The Trending Campaigns view in Office 365 Threat Intelligence Threat trackers
Figure 1. The Trending Campaigns view in Office 365 Threat Intelligence Threat trackers
While the campaign views enable tracking and quick assessment of threats, queries are powerful investigative views allowing deeper understanding of threats, aiding admins to make data driven security updates. Queries can be accessed from either campaign view by clicking on ‘Explorer’ which displays that tracked threat campaign. Saved Queries provides a view into all Explorer searches saved as queries. Admins can monitor malware and phish events with the scope (number of emails included in an incident) defined and saved from Explorer. Saved queries are useful for checking items frequently. To create more saved queries, go to the Explorer, add filters to view specific sets of events, then select ‘Save query’ (button at top of page).
 Figure 2. Opened Explorer page on tracked threat campaign. The threat campaign can be saved as query from the Explorer
Figure 2. Opened Explorer page on tracked threat campaign. The threat campaign can be saved as query from the Explorer
Tracked queries provide regular assessments of malware, phish, and other events with the scope defined from Threat Explorer. Tracked queries help monitor items frequently, providing reports, allowing quick and in-depth evaluation of threats or groups. A limited number of tracked queries are available for each organization. Admins can choose to convert saved queries and begin tracking them using the edit option for that query.
These ‘Threat Trackers’ enrich the admin experience, providing a powerful new tool for monitoring and managing, investigations, which ultimately enables quick response to threats. With this added feature, Office 365 Threat Intelligence provides admins to more efficiently and easily secure their organization.
Send Us Your Feedback
Let us know what you think of the new Threat trackers feature by beginning an Office 365 E5 trial today to experience the powerful capabilities of Office 365 Threat Intelligence. Your feedback enables us to make updates and enhancements to provide you with the best protection for Office 365. Please watch our recent webinar on Office 365 Threat Intelligence to learn further details on how the service can help your organization become more secure.

Investigative Tools to Empower Stronger Threat Protection
We launched Office 365 Threat Intelligence to help organization’s become more secure by enhancing admin capabilities which offer greater visibility, deeper insights, and powerful executable actions (check out the recent webinar overviewing the service). Today we’re excited to announce ‘Threat Trackers’ for Office 365 Threat Intelligence, enabling efficient monitoring and management of threat investigations to help admins quickly remediate and respond to threats. The feature can be found under ‘Threat Management’ in the Security and Compliance Center. Table 1 summarizes the four available ‘Threat tracker’ categories.
 Table 1. The different tracker categories available in Office 365 Threat Intelligence Threat Trackers view
Table 1. The different tracker categories available in Office 365 Threat Intelligence Threat Trackers view
Threat Tracker Categories
Noteworthy campaigns are classified, as well known and important global threats. Office 365 Threat Intelligence pre-builds Noteworthy Campaign monitors, enabling admins to quickly review the impact of these threats, assessing both their volume and frequency. This automated monitoring allows admins speedy remediation from these threats. Noteworthy Campaign monitors update hourly, showing the latest impact of these threats to your organization. Click ‘Explore’ if you want to see the detailed events detected by the filter.
The Trending Campaigns view provides dynamic assessments of email threats impacting your organization’s Office 365 environment. This view shows tenant level malware trends, identifying malware families on the rise, flat, or declining, giving admins greater insight into which threats require further attention. New threats not seen recently in your organization will appear at the top of the page (sorted by trend). Trending Campaigns also offers a comparative view on how a threat impacts your organization versus others. If an organization’s targeting percentage is >10%, it indicates that it is being specifically targeted by the attack. Admins can further investigate targeted and trending attacks in Explorer, where actions such as deleting or moving the malware to junk can be taken. Targeted attacks are typically short-lived, so these types of attacks in the Trending Campaigns view may drop out of the view within a few days.
 Figure 1. The Trending Campaigns view in Office 365 Threat Intelligence Threat trackers
Figure 1. The Trending Campaigns view in Office 365 Threat Intelligence Threat trackers
While the campaign views enable tracking and quick assessment of threats, queries are powerful investigative views allowing deeper understanding of threats, aiding admins to make data driven security updates. Queries can be accessed from either campaign view by clicking on ‘Explorer’ which displays that tracked threat campaign. Saved Queries provides a view into all Explorer searches saved as queries. Admins can monitor malware and phish events with the scope (number of emails included in an incident) defined and saved from Explorer. Saved queries are useful for checking items frequently. To create more saved queries, go to the Explorer, add filters to view specific sets of events, then select ‘Save query’ (button at top of page).
 Figure 2. Opened Explorer page on tracked threat campaign. The threat campaign can be saved as query from the Explorer
Figure 2. Opened Explorer page on tracked threat campaign. The threat campaign can be saved as query from the Explorer
Tracked queries provide regular assessments of malware, phish, and other events with the scope defined from Threat Explorer. Tracked queries help monitor items frequently, providing reports, allowing quick and in-depth evaluation of threats or groups. A limited number of tracked queries are available for each organization. Admins can choose to convert saved queries and begin tracking them using the edit option for that query.
These ‘Threat Trackers’ enrich the admin experience, providing a powerful new tool for monitoring and managing, investigations, which ultimately enables quick response to threats. With this added feature, Office 365 Threat Intelligence provides admins to more efficiently and easily secure their organization.
Send Us Your Feedback
Let us know what you think of the new Threat trackers feature by beginning an Office 365 E5 trial today to experience the powerful capabilities of Office 365 Threat Intelligence. Your feedback enables us to make updates and enhancements to provide you with the best protection for Office 365. Please watch our recent webinar on Office 365 Threat Intelligence to learn further details on how the service can help your organization become more secure.
Today is the enforcement date of the EU’s General Data Protection Regulation (GDPR), which establishes an important milestone for individual privacy rights. Microsoft has been a strong supporter of the GDPR since it was first proposed in 2012. The GDPR sets a strong standard for privacy because it puts people in control of their own data.
In this post, we summarize the resources on the Service Trust Portal that can help you with GDPR readiness when using Microsoft Cloud services.
Service Trust Portal – Get in-depth information to help you meet GDPR obligations
The Privacy area on Service Trust Portal provides GDPR resources across Microsoft Cloud services, including Office 365, Azure, Dynamics 365, Windows, and Professional Services. You can find 3 primary topics under the Privacy tab:
- Data Subject Requests (DSRs): get information about how specific Microsoft Cloud services enable you to discover, access, rectify, restrict, delete, and export personal data; connect you to the DSRs tools Microsoft builds to help you respond to DSRs (e.g. Data Log Export for responding to telemetry log DSRs).
- Data breach notification: find information about how Microsoft detects and responds to personal data breaches, and how you can set up your privacy contact to receive breach notifications from Microsoft in the event of personal data breach.
- Data Protection Impact Assessments (DPIAs): learn about Microsoft’s and your responsibilities for DPIA compliance, and get information provided by Microsoft that can support you to create your own DPIAs.
Visit it today at https://aka.ms/GDPRGetStarted and learn more about how to use Service Trust Portal to plan and implement GDPR controls in this video:
Compliance Manager – Assess and improve your GDPR compliance posture
Compliance Manager is a cross-Microsoft-Cloud solution that helps organizations understand and manage the complex compliance landscape with 3 key capabilities:
- Ongoing risk assessment: gain visibility into Microsoft’s internal controls as well as your compliance performance and make better plans with Compliance Score.[1]
- Actionable insights: get guidance on implementing controls to increase your Compliance Score and enhance data protection capabilities.
- Simplified compliance: use the built-in dashboard, control management, and audit-ready reporting functions to assign, track, and record your compliance activities
GDPR assessments are now available in Compliance Manager for Azure, Dynamics 365, Office 365, and Microsoft Professional Services.[2] Check out Compliance Manager today at https://aka.ms/compliancemanager.
Watch this 2-min video, which summarizes the capabilities of Compliance Manager:
More Resources
You can find more resources about Service Trust Portal and Compliance Manager below:
[1] Compliance Manager is a dashboard that provides the Compliance Score and a summary of your data protection and compliance stature as well as recommendations to improve data protection and compliance. This is a recommendation, it is up to you to evaluate and validate the effectiveness of customer controls as per your regulatory environment. Recommendations from Compliance Manager and Compliance Score should not be interpreted as a guarantee of compliance.
[2] Note that Office 365 GCC customers can access Compliance Manager; however, users should evaluate whether to use the document upload feature of Compliance Manager, as the storage for document upload is compliant with Office 365 Tier C only. Compliance Manager is not yet available in sovereign clouds including Office 365 U.S. Government Community High (GCC High), Office 365 Department of Defense (DoD), Office 365 Operated by 21 Vianet, and Office 365 Germany.
Today is the enforcement date of the EU’s General Data Protection Regulation (GDPR), which establishes an important milestone for individual privacy rights. Microsoft has been a strong supporter of the GDPR since it was first proposed in 2012. The GDPR sets a strong standard for privacy because it puts people in control of their own data.
In this post, we summarize the resources on the Service Trust Portal that can help you with GDPR readiness when using Microsoft Cloud services.
Service Trust Portal – Get in-depth information to help you meet GDPR obligations
The Privacy area on Service Trust Portal provides GDPR resources across Microsoft Cloud services, including Office 365, Azure, Dynamics 365, Windows, and Professional Services. You can find 3 primary topics under the Privacy tab:
- Data Subject Requests (DSRs): get information about how specific Microsoft Cloud services enable you to discover, access, rectify, restrict, delete, and export personal data; connect you to the DSRs tools Microsoft builds to help you respond to DSRs (e.g. Data Log Export for responding to telemetry log DSRs).
- Data breach notification: find information about how Microsoft detects and responds to personal data breaches, and how you can set up your privacy contact to receive breach notifications from Microsoft in the event of personal data breach.
- Data Protection Impact Assessments (DPIAs): learn about Microsoft’s and your responsibilities for DPIA compliance, and get information provided by Microsoft that can support you to create your own DPIAs.
Visit it today at https://aka.ms/GDPRGetStarted and learn more about how to use Service Trust Portal to plan and implement GDPR controls in this video:
Compliance Manager – Assess and improve your GDPR compliance posture
Compliance Manager is a cross-Microsoft-Cloud solution that helps organizations understand and manage the complex compliance landscape with 3 key capabilities:
- Ongoing risk assessment: gain visibility into Microsoft’s internal controls as well as your compliance performance and make better plans with Compliance Score.[1]
- Actionable insights: get guidance on implementing controls to increase your Compliance Score and enhance data protection capabilities.
- Simplified compliance: use the built-in dashboard, control management, and audit-ready reporting functions to assign, track, and record your compliance activities
GDPR assessments are now available in Compliance Manager for Azure, Dynamics 365, Office 365, and Microsoft Professional Services.[2] Check out Compliance Manager today at https://aka.ms/compliancemanager.
Watch this 2-min video, which summarizes the capabilities of Compliance Manager:
More Resources
You can find more resources about Service Trust Portal and Compliance Manager below:
[1] Compliance Manager is a dashboard that provides the Compliance Score and a summary of your data protection and compliance stature as well as recommendations to improve data protection and compliance. This is a recommendation, it is up to you to evaluate and validate the effectiveness of customer controls as per your regulatory environment. Recommendations from Compliance Manager and Compliance Score should not be interpreted as a guarantee of compliance.
[2] Note that Office 365 GCC customers can access Compliance Manager; however, users should evaluate whether to use the document upload feature of Compliance Manager, as the storage for document upload is compliant with Office 365 Tier C only. Compliance Manager is not yet available in sovereign clouds including Office 365 U.S. Government Community High (GCC High), Office 365 Department of Defense (DoD), Office 365 Operated by 21 Vianet, and Office 365 Germany.
Today is the enforcement date of the EU’s General Data Protection Regulation (GDPR), which establishes an important milestone for individual privacy rights. Microsoft has been a strong supporter of the GDPR since it was first proposed in 2012. The GDPR sets a strong standard for privacy because it puts people in control of their own data.
In this post, we summarize the resources on the Service Trust Portal that can help you with GDPR readiness when using Microsoft Cloud services.
Service Trust Portal – Get in-depth information to help you meet GDPR obligations
The Privacy area on Service Trust Portal provides GDPR resources across Microsoft Cloud services, including Office 365, Azure, Dynamics 365, Windows, and Professional Services. You can find 3 primary topics under the Privacy tab:
- Data Subject Requests (DSRs): get information about how specific Microsoft Cloud services enable you to discover, access, rectify, restrict, delete, and export personal data; connect you to the DSRs tools Microsoft builds to help you respond to DSRs (e.g. Data Log Export for responding to telemetry log DSRs).
- Data breach notification: find information about how Microsoft detects and responds to personal data breaches, and how you can set up your privacy contact to receive breach notifications from Microsoft in the event of personal data breach.
- Data Protection Impact Assessments (DPIAs): learn about Microsoft’s and your responsibilities for DPIA compliance, and get information provided by Microsoft that can support you to create your own DPIAs.
Visit it today at https://aka.ms/GDPRGetStarted and learn more about how to use Service Trust Portal to plan and implement GDPR controls in this video:
Compliance Manager – Assess and improve your GDPR compliance posture
Compliance Manager is a cross-Microsoft-Cloud solution that helps organizations understand and manage the complex compliance landscape with 3 key capabilities:
- Ongoing risk assessment: gain visibility into Microsoft’s internal controls as well as your compliance performance and make better plans with Compliance Score.[1]
- Actionable insights: get guidance on implementing controls to increase your Compliance Score and enhance data protection capabilities.
- Simplified compliance: use the built-in dashboard, control management, and audit-ready reporting functions to assign, track, and record your compliance activities
GDPR assessments are now available in Compliance Manager for Azure, Dynamics 365, Office 365, and Microsoft Professional Services.[2] Check out Compliance Manager today at https://aka.ms/compliancemanager.
Watch this 2-min video, which summarizes the capabilities of Compliance Manager:
More Resources
You can find more resources about Service Trust Portal and Compliance Manager below:
[1] Compliance Manager is a dashboard that provides the Compliance Score and a summary of your data protection and compliance stature as well as recommendations to improve data protection and compliance. This is a recommendation, it is up to you to evaluate and validate the effectiveness of customer controls as per your regulatory environment. Recommendations from Compliance Manager and Compliance Score should not be interpreted as a guarantee of compliance.
[2] Note that Office 365 GCC customers can access Compliance Manager; however, users should evaluate whether to use the document upload feature of Compliance Manager, as the storage for document upload is compliant with Office 365 Tier C only. Compliance Manager is not yet available in sovereign clouds including Office 365 U.S. Government Community High (GCC High), Office 365 Department of Defense (DoD), Office 365 Operated by 21 Vianet, and Office 365 Germany.
Today is the enforcement date of the EU’s General Data Protection Regulation (GDPR), which establishes an important milestone for individual privacy rights. Microsoft has been a strong supporter of the GDPR since it was first proposed in 2012. The GDPR sets a strong standard for privacy because it puts people in control of their own data.
In this post, we summarize the resources on the Service Trust Portal that can help you with GDPR readiness when using Microsoft Cloud services.
Service Trust Portal – Get in-depth information to help you meet GDPR obligations
The Privacy area on Service Trust Portal provides GDPR resources across Microsoft Cloud services, including Office 365, Azure, Dynamics 365, Windows, and Professional Services. You can find 3 primary topics under the Privacy tab:
- Data Subject Requests (DSRs): get information about how specific Microsoft Cloud services enable you to discover, access, rectify, restrict, delete, and export personal data; connect you to the DSRs tools Microsoft builds to help you respond to DSRs (e.g. Data Log Export for responding to telemetry log DSRs).
- Data breach notification: find information about how Microsoft detects and responds to personal data breaches, and how you can set up your privacy contact to receive breach notifications from Microsoft in the event of personal data breach.
- Data Protection Impact Assessments (DPIAs): learn about Microsoft’s and your responsibilities for DPIA compliance, and get information provided by Microsoft that can support you to create your own DPIAs.
Visit it today at https://aka.ms/GDPRGetStarted and learn more about how to use Service Trust Portal to plan and implement GDPR controls in this video:
Compliance Manager – Assess and improve your GDPR compliance posture
Compliance Manager is a cross-Microsoft-Cloud solution that helps organizations understand and manage the complex compliance landscape with 3 key capabilities:
- Ongoing risk assessment: gain visibility into Microsoft’s internal controls as well as your compliance performance and make better plans with Compliance Score.[1]
- Actionable insights: get guidance on implementing controls to increase your Compliance Score and enhance data protection capabilities.
- Simplified compliance: use the built-in dashboard, control management, and audit-ready reporting functions to assign, track, and record your compliance activities
GDPR assessments are now available in Compliance Manager for Azure, Dynamics 365, Office 365, and Microsoft Professional Services.[2] Check out Compliance Manager today at https://aka.ms/compliancemanager.
Watch this 2-min video, which summarizes the capabilities of Compliance Manager:
More Resources
You can find more resources about Service Trust Portal and Compliance Manager below:
[1] Compliance Manager is a dashboard that provides the Compliance Score and a summary of your data protection and compliance stature as well as recommendations to improve data protection and compliance. This is a recommendation, it is up to you to evaluate and validate the effectiveness of customer controls as per your regulatory environment. Recommendations from Compliance Manager and Compliance Score should not be interpreted as a guarantee of compliance.
[2] Note that Office 365 GCC customers can access Compliance Manager; however, users should evaluate whether to use the document upload feature of Compliance Manager, as the storage for document upload is compliant with Office 365 Tier C only. Compliance Manager is not yet available in sovereign clouds including Office 365 U.S. Government Community High (GCC High), Office 365 Department of Defense (DoD), Office 365 Operated by 21 Vianet, and Office 365 Germany.
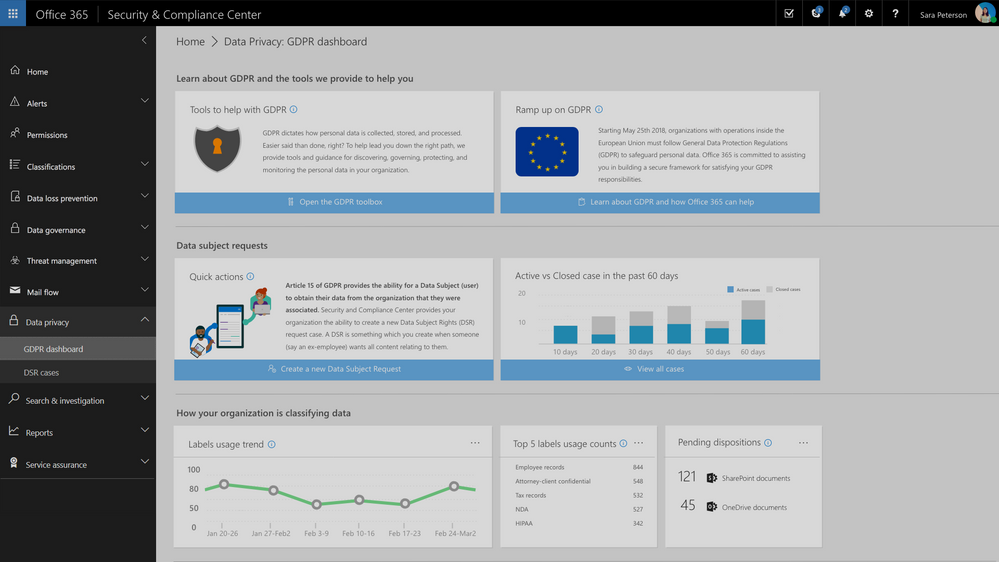
Update: The Data Privacy tab, GDPR dashboard and Data Subject Requests for Office 365 content are now generally available to Office 365 commercial customers in the Security and Compliance center.
One of the core requirements of the GDPR is that organizations have a process to respond to Data Subject Requests from individuals in the EU for access to their data. As part of Microsoft’s commitment to helping customers on their journey to GDPR, today we are announcing preview of the new Data Subject Requests experience is enabled within the Microsoft 365 Security & Compliance Center.
To handle GDPR related tasks for your Office 365 data and content, access to the Data Privacy tab within the Security & Compliance Center is now available in preview. This new Data Privacy tab will provide information to help you on your GDPR journey, and provide the ability to create, manage and complete data subject requests for content in Office 365.
This new experience will help to manage the process and execution of data subject requests for data within the Office 365 core apps and services including Exchange, SharePoint and OneDrive, Office 365 Groups, Skype for Business, and now Teams.

Request creation for each Data Subject Request is completed via a simple module that allows you to identify the request name or unique identifier, identify the related data subject e.g. the person submitting the request, and add that new request to the queue or requests that you may be managing.
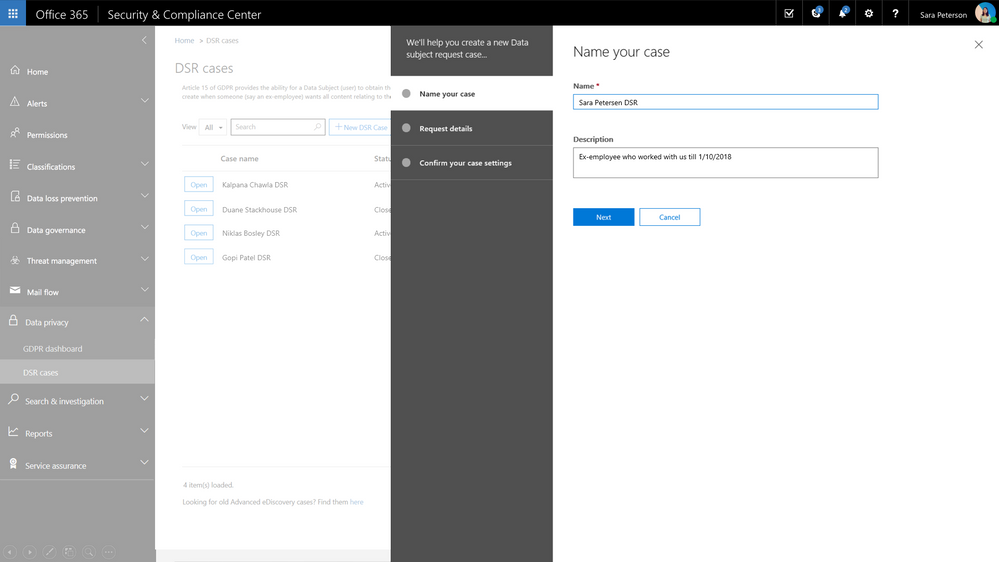
Once the request has been created, search for relevant content within your Office 365 environment. Select locations, specific content types and additional filters to refine your search to return only the content related to your specific request. In many cases, an employee will want to know what personally identifiable information their employer has on them and with content search you can refine your search to just look for PII rather than all data related to the requestor. Once search is complete, you now have option to export the related content for further review, processing or transport to the requestor. We provide several options for export to enable your work flow and processes. Once export is complete, the request status is updated.
Check out the video to see how this will work.

Update: The Data Privacy tab, GDPR dashboard and Data Subject Requests for Office 365 content are now generally available to Office 365 commercial customers in the Security and Compliance center.
One of the core requirements of the GDPR is that organizations have a process to respond to Data Subject Requests from individuals in the EU for access to their data. As part of Microsoft’s commitment to helping customers on their journey to GDPR, today we are announcing preview of the new Data Subject Requests experience is enabled within the Microsoft 365 Security & Compliance Center.
To handle GDPR related tasks for your Office 365 data and content, access to the Data Privacy tab within the Security & Compliance Center is now available in preview. This new Data Privacy tab will provide information to help you on your GDPR journey, and provide the ability to create, manage and complete data subject requests for content in Office 365.
This new experience will help to manage the process and execution of data subject requests for data within the Office 365 core apps and services including Exchange, SharePoint and OneDrive, Office 365 Groups, Skype for Business, and now Teams.

Request creation for each Data Subject Request is completed via a simple module that allows you to identify the request name or unique identifier, identify the related data subject e.g. the person submitting the request, and add that new request to the queue or requests that you may be managing.

Once the request has been created, search for relevant content within your Office 365 environment. Select locations, specific content types and additional filters to refine your search to return only the content related to your specific request. In many cases, an employee will want to know what personally identifiable information their employer has on them and with content search you can refine your search to just look for PII rather than all data related to the requestor. Once search is complete, you now have option to export the related content for further review, processing or transport to the requestor. We provide several options for export to enable your work flow and processes. Once export is complete, the request status is updated.
Check out the video to see how this will work.

Update: The Data Privacy tab, GDPR dashboard and Data Subject Requests for Office 365 content are now generally available to Office 365 commercial customers in the Security and Compliance center.
One of the core requirements of the GDPR is that organizations have a process to respond to Data Subject Requests from individuals in the EU for access to their data. As part of Microsoft’s commitment to helping customers on their journey to GDPR, today we are announcing preview of the new Data Subject Requests experience is enabled within the Microsoft 365 Security & Compliance Center.
To handle GDPR related tasks for your Office 365 data and content, access to the Data Privacy tab within the Security & Compliance Center is now available in preview. This new Data Privacy tab will provide information to help you on your GDPR journey, and provide the ability to create, manage and complete data subject requests for content in Office 365.
This new experience will help to manage the process and execution of data subject requests for data within the Office 365 core apps and services including Exchange, SharePoint and OneDrive, Office 365 Groups, Skype for Business, and now Teams.

Request creation for each Data Subject Request is completed via a simple module that allows you to identify the request name or unique identifier, identify the related data subject e.g. the person submitting the request, and add that new request to the queue or requests that you may be managing.

Once the request has been created, search for relevant content within your Office 365 environment. Select locations, specific content types and additional filters to refine your search to return only the content related to your specific request. In many cases, an employee will want to know what personally identifiable information their employer has on them and with content search you can refine your search to just look for PII rather than all data related to the requestor. Once search is complete, you now have option to export the related content for further review, processing or transport to the requestor. We provide several options for export to enable your work flow and processes. Once export is complete, the request status is updated.
Check out the video to see how this will work.

Update: The Data Privacy tab, GDPR dashboard and Data Subject Requests for Office 365 content are now generally available to Office 365 commercial customers in the Security and Compliance center.
One of the core requirements of the GDPR is that organizations have a process to respond to Data Subject Requests from individuals in the EU for access to their data. As part of Microsoft’s commitment to helping customers on their journey to GDPR, today we are announcing preview of the new Data Subject Requests experience is enabled within the Microsoft 365 Security & Compliance Center.
To handle GDPR related tasks for your Office 365 data and content, access to the Data Privacy tab within the Security & Compliance Center is now available in preview. This new Data Privacy tab will provide information to help you on your GDPR journey, and provide the ability to create, manage and complete data subject requests for content in Office 365.
This new experience will help to manage the process and execution of data subject requests for data within the Office 365 core apps and services including Exchange, SharePoint and OneDrive, Office 365 Groups, Skype for Business, and now Teams.

Request creation for each Data Subject Request is completed via a simple module that allows you to identify the request name or unique identifier, identify the related data subject e.g. the person submitting the request, and add that new request to the queue or requests that you may be managing.

Once the request has been created, search for relevant content within your Office 365 environment. Select locations, specific content types and additional filters to refine your search to return only the content related to your specific request. In many cases, an employee will want to know what personally identifiable information their employer has on them and with content search you can refine your search to just look for PII rather than all data related to the requestor. Once search is complete, you now have option to export the related content for further review, processing or transport to the requestor. We provide several options for export to enable your work flow and processes. Once export is complete, the request status is updated.
Check out the video to see how this will work.
Today we are announcing an upcoming change to Office that blocks activation of Flash, Shockwave and Silverlight controls within Office.
We are taking this step based on the following factors:
- Use of some these controls in exploit campaigns to target end users of Office.
- Low observed use of these controls within Office.
- Upcoming end of support for some these components
- On July 2017, Adobe announced that Flash will no longer be supported after 2020. Major browsers including Edge, Chrome, Safari and Firefox have announced their respective roadmaps for ending support for Flash.
- Silverlight is expected to reach end of support in 2021 with support for several browsers and OS platforms already ended in 2016.
Note: This change only applies to Office 365 subscription clients. It will not apply to Office 2016, Office 2013 or Office 2010.
Customers who wish to enforce this behavior now in Office 365 subscription clients or in Office 2016 perpetual and down level versions can use the guidance published here to block controls targeted by this change.
Furthermore, customers can also take advantage of the recently published Security Baseline for Office 2016 that includes a custom Group Policy that blocks Flash.
What does this update block?
This change blocks the activation of the following controls within the Office process.
|
Control
|
CLSID
|
|
Flash
|
D27CDB6E-AE6D-11CF-96B8-444553540000
D27CDB70-AE6D-11CF-96B8-444553540000
|
|
Shockwave
|
233C1507-6A77-46A4-9443-F871F945D258
|
|
Silverlight
|
DFEAF541-F3E1-4c24-ACAC-99C30715084A
|
Some examples of scenarios that would be impacted by this change are:
- Controls directly embedded in an Office document, for example, Flash video directly embedded within a PowerPoint document using the Insert Object functionality
- Controls invoked by extensibility components within the Office process, for example, Power View add-in that uses Silverlight
Note: this change does not cover scenarios where these controls are activated outside the Office process, for example, a Flash video inserted into a document via the Insert Online Video functionality.
When would this block take effect?
This change only applies to Office 365 subscription clients and is targeted to take effect in the following order
- Controls are blocked in Office 365 Monthly Channel starting in June 2018.
- Controls are blocked in Office 365 Semi Annual Targeted (SAT) Channel starting in September 2018.
- Controls are blocked in Office 365 Semi Annual (SA) Channel starting in January 2019.
Can I unblock these controls if I need to?
Yes. While we are confident that this will not impact most Office users, we do understand there is potential to impact some of our users and we apologize for the inconvenience caused as a result.
Please refer to support guidance published here if you need to unblock controls critical to your workflow.
In closing, we believe this is another step forward in elevating the security of Office. One that protects our users from malicious attacks without disrupting day to day productivity for most of them.
Today we are announcing an upcoming change to Office that blocks activation of Flash, Shockwave and Silverlight controls within Office.
We are taking this step based on the following factors:
- Use of some these controls in exploit campaigns to target end users of Office.
- Low observed use of these controls within Office.
- Upcoming end of support for some these components
- On July 2017, Adobe announced that Flash will no longer be supported after 2020. Major browsers including Edge, Chrome, Safari and Firefox have announced their respective roadmaps for ending support for Flash.
- Silverlight is expected to reach end of support in 2021 with support for several browsers and OS platforms already ended in 2016.
Note: This change only applies to Office 365 subscription clients. It will not apply to Office 2016, Office 2013 or Office 2010.
Customers who wish to enforce this behavior now in Office 365 subscription clients or in Office 2016 perpetual and down level versions can use the guidance published here to block controls targeted by this change.
Furthermore, customers can also take advantage of the recently published Security Baseline for Office 2016 that includes a custom Group Policy that blocks Flash.
What does this update block?
This change blocks the activation of the following controls within the Office process.
|
Control
|
CLSID
|
|
Flash
|
D27CDB6E-AE6D-11CF-96B8-444553540000
D27CDB70-AE6D-11CF-96B8-444553540000
|
|
Shockwave
|
233C1507-6A77-46A4-9443-F871F945D258
|
|
Silverlight
|
DFEAF541-F3E1-4c24-ACAC-99C30715084A
|
Some examples of scenarios that would be impacted by this change are:
- Controls directly embedded in an Office document, for example, Flash video directly embedded within a PowerPoint document using the Insert Object functionality
- Controls invoked by extensibility components within the Office process, for example, Power View add-in that uses Silverlight
Note: this change does not cover scenarios where these controls are activated outside the Office process, for example, a Flash video inserted into a document via the Insert Online Video functionality.
When would this block take effect?
This change only applies to Office 365 subscription clients and is targeted to take effect in the following order
- Controls are blocked in Office 365 Monthly Channel starting in June 2018.
- Controls are blocked in Office 365 Semi Annual Targeted (SAT) Channel starting in September 2018.
- Controls are blocked in Office 365 Semi Annual (SA) Channel starting in January 2019.
Can I unblock these controls if I need to?
Yes. While we are confident that this will not impact most Office users, we do understand there is potential to impact some of our users and we apologize for the inconvenience caused as a result.
Please refer to support guidance published here if you need to unblock controls critical to your workflow.
In closing, we believe this is another step forward in elevating the security of Office. One that protects our users from malicious attacks without disrupting day to day productivity for most of them.
Today we are announcing an upcoming change to Office that blocks activation of Flash, Shockwave and Silverlight controls within Office.
We are taking this step based on the following factors:
- Use of some these controls in exploit campaigns to target end users of Office.
- Low observed use of these controls within Office.
- Upcoming end of support for some these components
- On July 2017, Adobe announced that Flash will no longer be supported after 2020. Major browsers including Edge, Chrome, Safari and Firefox have announced their respective roadmaps for ending support for Flash.
- Silverlight is expected to reach end of support in 2021 with support for several browsers and OS platforms already ended in 2016.
Note: This change only applies to Office 365 subscription clients. It will not apply to Office 2016, Office 2013 or Office 2010.
Customers who wish to enforce this behavior now in Office 365 subscription clients or in Office 2016 perpetual and down level versions can use the guidance published here to block controls targeted by this change.
Furthermore, customers can also take advantage of the recently published Security Baseline for Office 2016 that includes a custom Group Policy that blocks Flash.
What does this update block?
This change blocks the activation of the following controls within the Office process.
|
Control
|
CLSID
|
|
Flash
|
D27CDB6E-AE6D-11CF-96B8-444553540000
D27CDB70-AE6D-11CF-96B8-444553540000
|
|
Shockwave
|
233C1507-6A77-46A4-9443-F871F945D258
|
|
Silverlight
|
DFEAF541-F3E1-4c24-ACAC-99C30715084A
|
Some examples of scenarios that would be impacted by this change are:
- Controls directly embedded in an Office document, for example, Flash video directly embedded within a PowerPoint document using the Insert Object functionality
- Controls invoked by extensibility components within the Office process, for example, Power View add-in that uses Silverlight
Note: this change does not cover scenarios where these controls are activated outside the Office process, for example, a Flash video inserted into a document via the Insert Online Video functionality.
When would this block take effect?
This change only applies to Office 365 subscription clients and is targeted to take effect in the following order
- Controls are blocked in Office 365 Monthly Channel starting in June 2018.
- Controls are blocked in Office 365 Semi Annual Targeted (SAT) Channel starting in September 2018.
- Controls are blocked in Office 365 Semi Annual (SA) Channel starting in January 2019.
Can I unblock these controls if I need to?
Yes. While we are confident that this will not impact most Office users, we do understand there is potential to impact some of our users and we apologize for the inconvenience caused as a result.
Please refer to support guidance published here if you need to unblock controls critical to your workflow.
In closing, we believe this is another step forward in elevating the security of Office. One that protects our users from malicious attacks without disrupting day to day productivity for most of them.
Today we are announcing an upcoming change to Office that blocks activation of Flash, Shockwave and Silverlight controls within Office.
We are taking this step based on the following factors:
- Use of some these controls in exploit campaigns to target end users of Office.
- Low observed use of these controls within Office.
- Upcoming end of support for some these components
- On July 2017, Adobe announced that Flash will no longer be supported after 2020. Major browsers including Edge, Chrome, Safari and Firefox have announced their respective roadmaps for ending support for Flash.
- Silverlight is expected to reach end of support in 2021 with support for several browsers and OS platforms already ended in 2016.
Note: This change only applies to Office 365 subscription clients. It will not apply to Office 2016, Office 2013 or Office 2010.
Customers who wish to enforce this behavior now in Office 365 subscription clients or in Office 2016 perpetual and down level versions can use the guidance published here to block controls targeted by this change.
Furthermore, customers can also take advantage of the recently published Security Baseline for Office 2016 that includes a custom Group Policy that blocks Flash.
What does this update block?
This change blocks the activation of the following controls within the Office process.
|
Control
|
CLSID
|
|
Flash
|
D27CDB6E-AE6D-11CF-96B8-444553540000
D27CDB70-AE6D-11CF-96B8-444553540000
|
|
Shockwave
|
233C1507-6A77-46A4-9443-F871F945D258
|
|
Silverlight
|
DFEAF541-F3E1-4c24-ACAC-99C30715084A
|
Some examples of scenarios that would be impacted by this change are:
- Controls directly embedded in an Office document, for example, Flash video directly embedded within a PowerPoint document using the Insert Object functionality
- Controls invoked by extensibility components within the Office process, for example, Power View add-in that uses Silverlight
Note: this change does not cover scenarios where these controls are activated outside the Office process, for example, a Flash video inserted into a document via the Insert Online Video functionality.
When would this block take effect?
This change only applies to Office 365 subscription clients and is targeted to take effect in the following order
- Controls are blocked in Office 365 Monthly Channel starting in June 2018.
- Controls are blocked in Office 365 Semi Annual Targeted (SAT) Channel starting in September 2018.
- Controls are blocked in Office 365 Semi Annual (SA) Channel starting in January 2019.
Can I unblock these controls if I need to?
Yes. While we are confident that this will not impact most Office users, we do understand there is potential to impact some of our users and we apologize for the inconvenience caused as a result.
Please refer to support guidance published here if you need to unblock controls critical to your workflow.
In closing, we believe this is another step forward in elevating the security of Office. One that protects our users from malicious attacks without disrupting day to day productivity for most of them.
Publishers note: I am posting this on behalf my colleague Jon Nordstrom who is part of the Office 365 customer experience team. Myself and few other engineers thought you would all benefit from his knowledge of the Office 365 management activity API
A common question we get from organizations that move to Office 365 is, how do I get visibility into transactions that effect the information stored in Office 365. The security and compliance center and the Office 365 Management Activity API provide organizations with this visibility though detailed information with regards to user, admin, system, and policy actions and events from Office 365 and Azure Active Directory (Azure AD).
Reviewing the wealth of information available via the API and the audit logs, can be challenging though. Triaging detection results manually and categorizing related activities into groups can be difficult. The amounts of data generated from likely malicious activity can overwhelm investigators with irrelevant results. We know from experience the importance of accurate tooling, Microsoft Online Services processes petabytes of event monitoring data.
When Microsoft Online Services engineering started on the journey to view detection results as graphs we found that it enabled us to:
- evaluate intrusion detection results in context with related activity
- incorporate lower-fidelity indicators without being overwhelmed with benign results
- determine with greater fidelity when datacenter activity is likely to represent an intrusion
In this first post of our two-part series we will to help you understand how you can get the data necessary to perform a security analysis of it. The second post will focus on examples scenarios and using Power BI to visualize the data.
We are going to use Azure Cosmos DB, Azure Function Apps and cloud message queues to retrieve and store information. The data stores can be removed or purged, and the solution can be disabled or removed. Azure Cosmos DB also allows for the concept of TTL to expire content if you continue to synchronize the information. The sample graphs generated in this post were created with the free version of the ZoomCharts add-in for Power BI Desktop. Depending on your need there are several other graph add-ins available such as Network Navigator Chart and Force-Directed Graph. If you already have a method for obtaining data from the Activity API such as Azure Log Analytics , then continue to use that and access the information from Power BI which we briefly discuss in this post and go into more detail in next post.
1. Register an App with Azure Active Directory
Use this as a guide to create and register an application for making calls to the Office 365 Activity API. There are more detailed information about app registrations here. For this environment, the “Configure an X.509 certificate to enable service-to-service calls” is not necessary; it is enough to have an application with the appropriate permissions set. Don’t forget to complete the Administrator consent.
2. Setting up the infrastructure to push the Office 365 activities
The first step is to push the information you need to a store. We’ll use this sample from GitHub https://github.com/OfficeDev/O365-ActivityFeed-AzureFunction that allow you to push the past seven days of Office 365 Activity data to an instance of Azure Cosmos DB. You can limit the number of days and the workloads as needed. The code is created to run in two Azure Functions (PowerShell is currently in preview).
- Azure Function 1 places activity messages in a cloud message queue.
- Azure Function 2 picks up messages from that queue and transmits them to Azure Cosmos DB.
1. Create Function 1. (QueueEvents.ps1)
Remember to register a new Application in Azure Active Directory with adequate permissions before you take these steps.
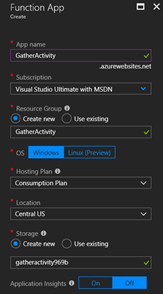
If you don’t already have a Function App start to create one. By default, runtime is limited to 5 minutes for the functions running under the consumption plans, however, you can increase the runtime up to 10 minutes. An alternative is to use the App Consumption plan if you expect longer execution times. The consumption plans typically cover the need for retrieving the event data.

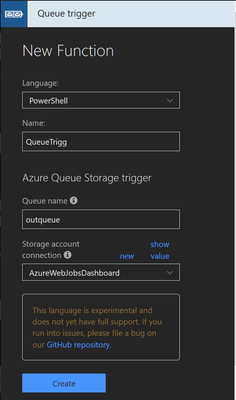
Create a New Function in the Function App
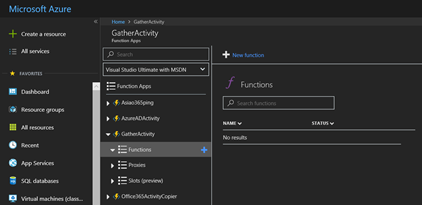
Enable experimental Language support, select Timer trigger and PowerShell.
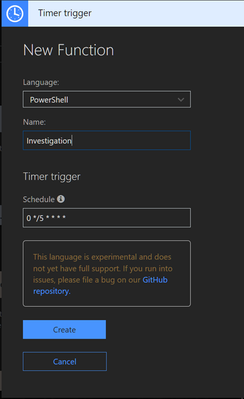
Name the new function, and select the schedule for the trigger, which determines how often the function will pull data. A workload.log file is used to keep track of time to prevent duplicate requests.
Next, paste the code for function 1., QueueEvents.ps1 to the function.
Adjust the variables for sign in based on the AAD application registered. The Tenant GUID can be found under the Endpoints in the app registration. It is listed as part of the endpoints.
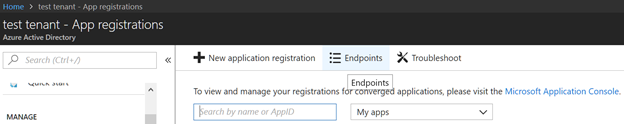
We will come back to adjust the storage variables shortly as part of the integration of the storage queues. Optionally modify the included workloads or message size. Note that reducing message size will increase the number of times Azure Function 2 is run. Making message size too large (for example, > 100) may cause you to exceed the limits of the queue and reduce performance.
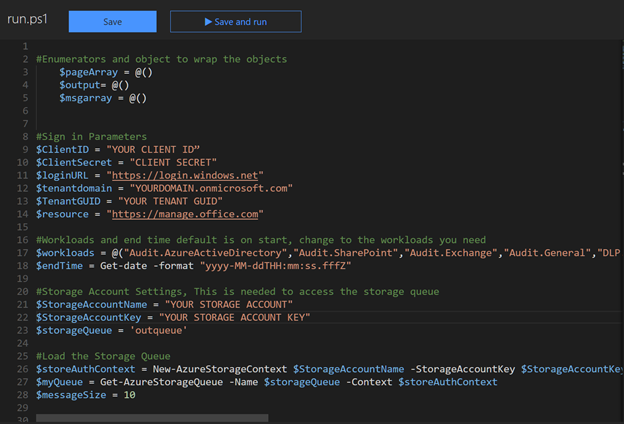
Next, select integrate and add an Azure Queue Storage output. The queue name is specified using the $storageQueue variable use ‘outQueue’with single quotes unless you changed the queue name in the output settings. Click, Show Value on the “Storage account connection” and copy the Account key value to $StorageAccountKey and the AccountName to $StorageAccountName. These steps are required to use cloud queue functionality. A regular storage queue call does not allow for multiple objects.
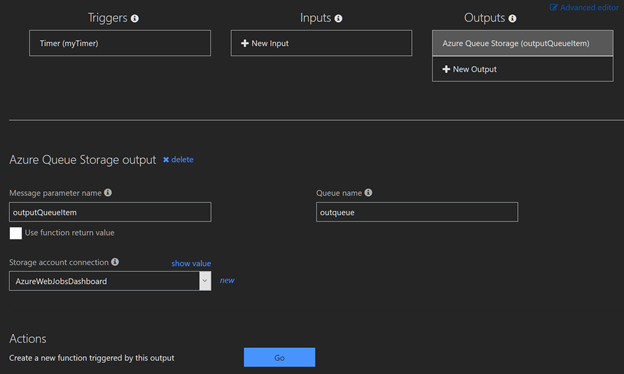
Do verify that the queue was created, there have been some instances in the testing where they weren’t. In that case create a queue manually in the associated storage account.
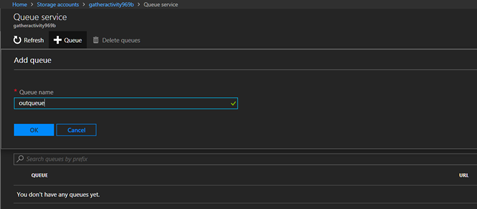
2. Create Function 2. (StoreEvents.ps1)
Follow these steps to create the second function, which is a Queue trigger. Create a new Function in the previously created Function App. Provide a Queue name and the storage account defined in Function 1.
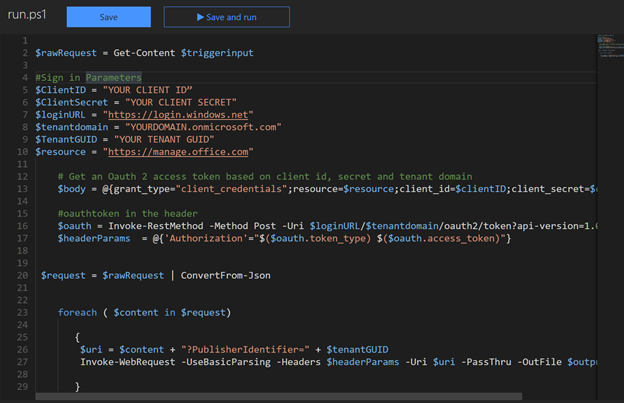
Add the code StoreEvents.ps1 and the information for the auth variables. The $triggerInput variable is the message parameter name.
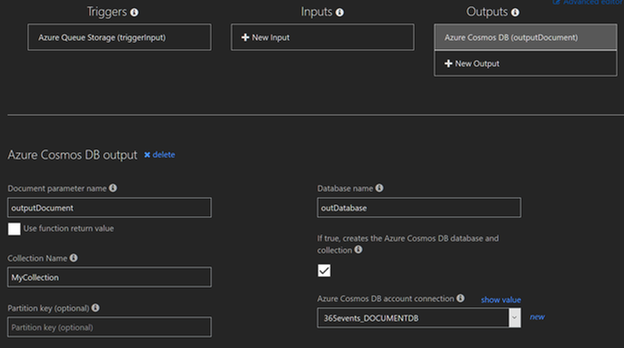
Select Integrate and add a Cosmos DB. The $outputdocument variable is based on the Document parameter name. If you change the name, you must also change the name of the variable. Click Show Value for “Azure Cosmos DB account connection” and store the account key for making requests from Power BI (an alternative is to navigate to the Cosmos DB and use a read-only key).
If you don’t already have an Azure Cosmos DB in place create a new database before creating the output. If you don’t have a Cosmos DB and collection, ensure to set the checkbox to create the Azure Cosmos DB and collection.
3. Start the functions.
If you haven’t enabled the Office 365 Activity API subscriptions that is the first step to take. There is a sample script for how to enable the subscriptions at the GitHub page it can be run from on-premises (Enablesubscription.ps1). Do enable Office 365 audit log search as well.
When configuring a start date for retrieving data, note that the maximum time span is the past 7 days based on Activity API restrictions.
If you change variable $StoredTime = Get-content $Tracker to a date in the format of “yyyy-MM-ddTHH:mm:ss.fffZ” the workloads will use it as the starting point (e.g., $StoredTime = “2018-04-12T01:34:18.702Z”). Either disable the function after it has completed a first run or replace it with Get-content $Tracker as the next scheduled run will process the same data if not adjusted.
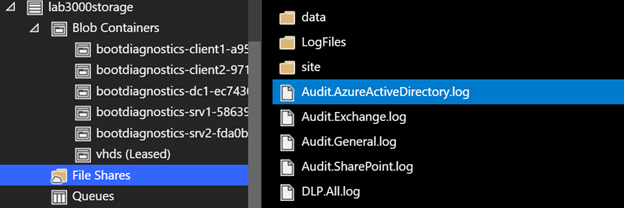
Alternatively, you can use Azure Storage Explorer and add these files with your desired start time to the root of the Azure functions blob store:
- Audit.AzureActiveDirectory.log
- Audit.SharePoint.log
- Audit.Exchange.log
- Audit.General.log
- DLP.All.log
The only thing you need in the file is the date example “2018-03-27T11:34:18.702Z” without the quotation marks. The log files allow for continuous synch excluding content previously synchronized.
When the functions are started, invocation logs will indicate if there are any issues. Use Azure Storage Explorer to view the storage queues.
If the function for some reason breaks the workload.log files will not be updated, and the function will start from the date last stamped in the workload.log file. There may be some overlap, but the analysis tools will identify any duplicates.
Ensure that the data is reaching your Cosmos DB instance by navigating to the Database, as shown below.
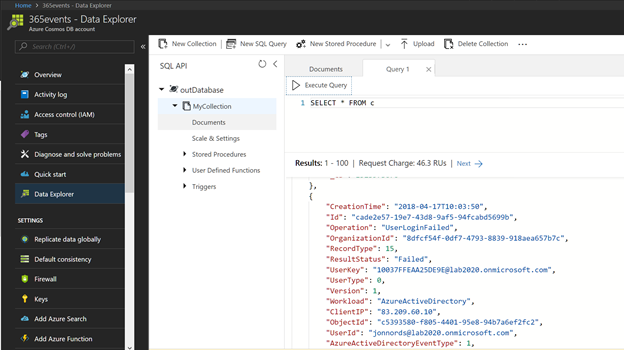
3. Open the data in Power BI
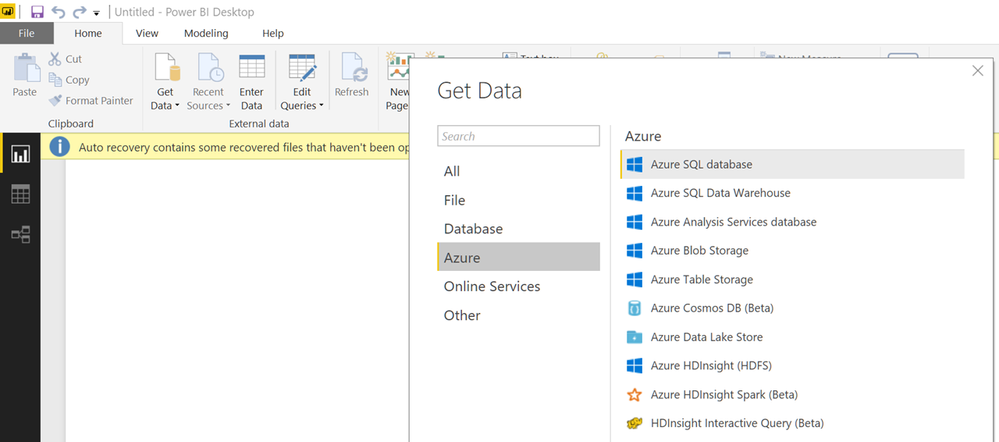
Download the Power BI Desktop client and the ZoomCharts referenced previously. Select to connect to Azure Cosmos DB in the Power BI desktop client.
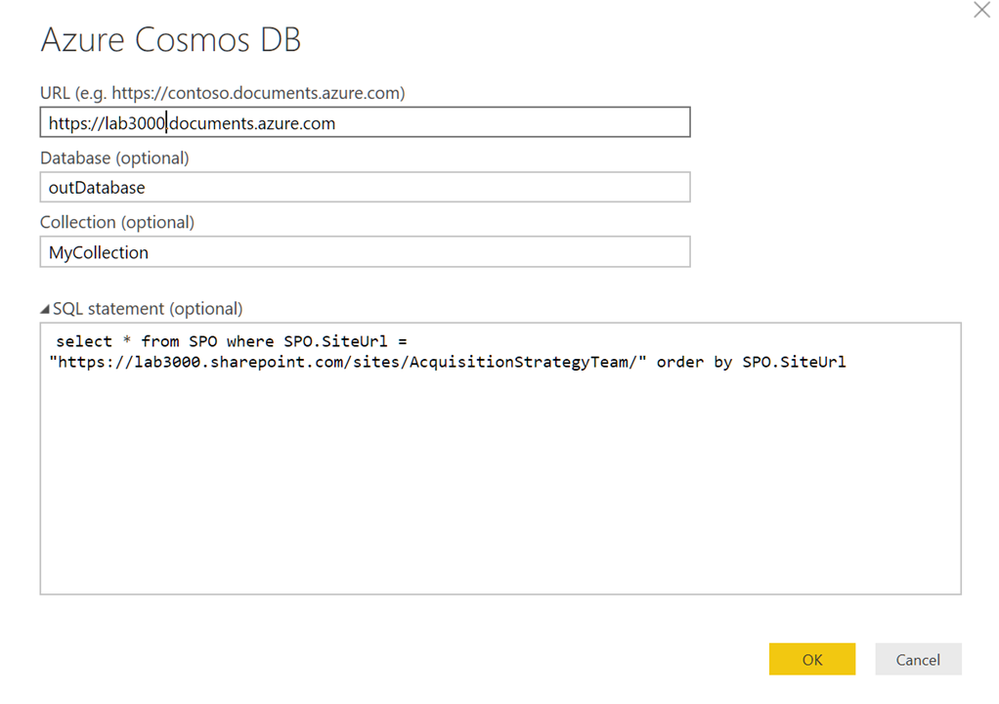
Specify your connection string, etc., and optionally specify a query to limit the scope to the asset you want to investigate. Do remember that everything is case sensitive. In this case I have scoped it down to a specific site. Please see the GitHub page for more query samples. The subsequent step will require the Cosmos DB storage key that you stored as part of setting up the Cosmos DB.
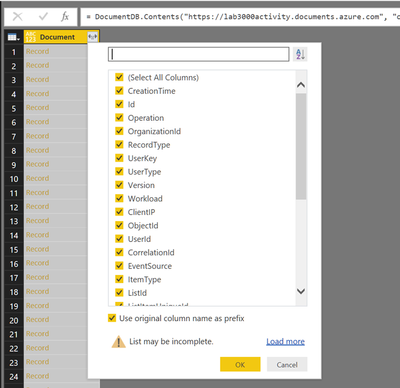
Expand the columns by selecting the expand arrows. When done close and apply.
Import the Zoomchart visual if you haven’t completed that step previously.
Load the Nodes you want to review and the Measure.
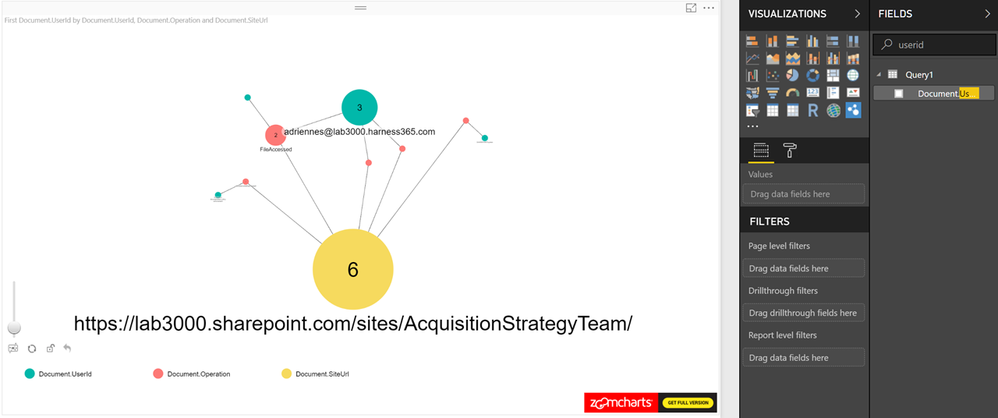
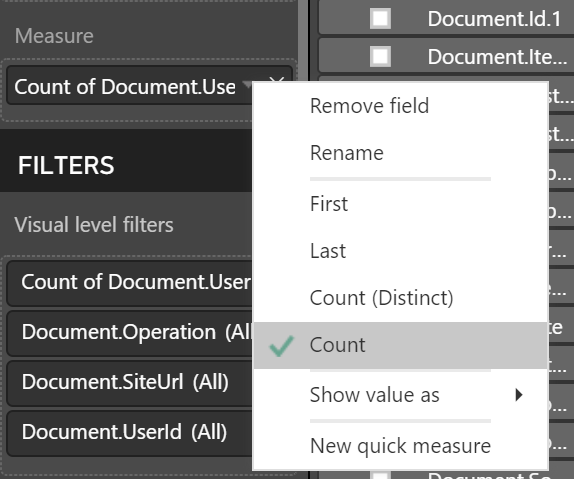
Change the Measure to count to make the node sizes reflect the actual number of occurrences as an example
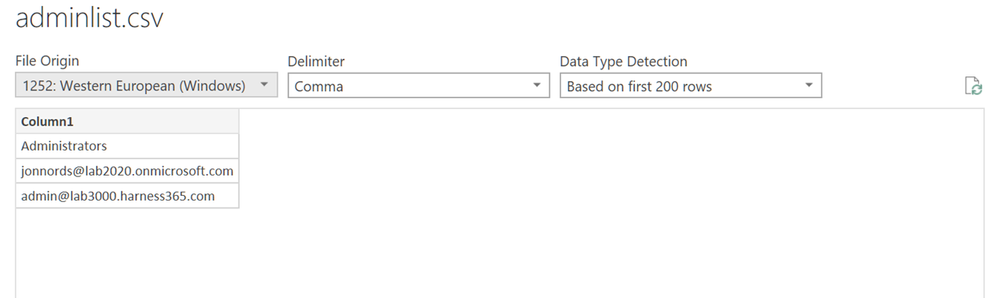
In many cases you can export csv files or directly make relationships to existing data and join it with the activity data. This is an example where we imported a few admin accounts from adminlist.csv. It could just as well be a number of files or ip addresses for which you need more information. We loaded the csv file.
In the next step we went to Relationships and joined the Adminlist with the UserID field to allow us to eliminate all accounts but those we are investigating.
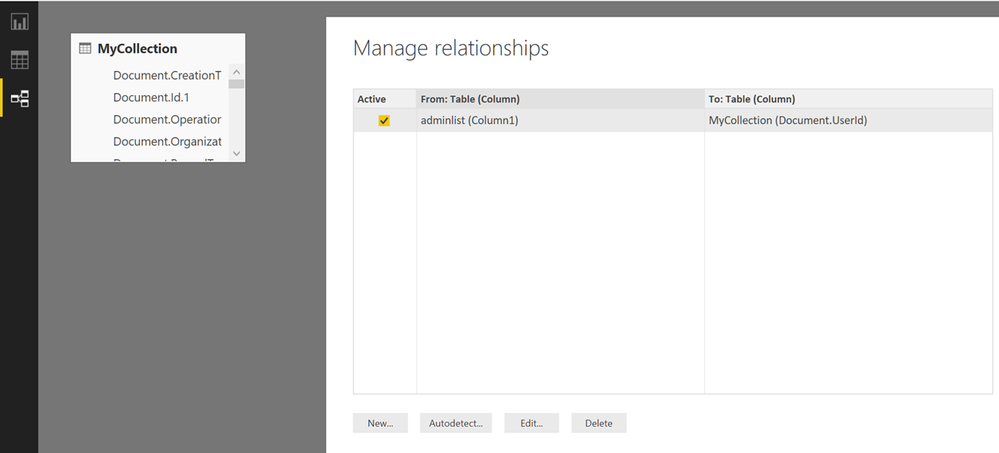
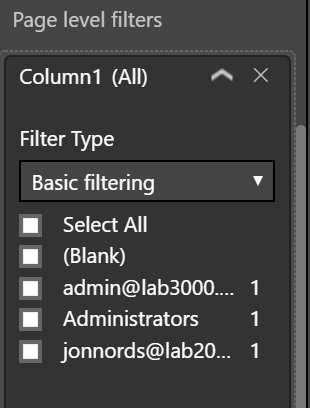
In the visual level filter, we removed any account but those we are investigating
Summary
We have provided you with a starting point for how to analyze Office 365 Data using Power BI. The data can be pivoted and analyzed in many ways. Templates and continuously pulling the Activity Data can be used to quickly load data and draw conclusions from the wealth of information. Other event sources such as on premises Intrusion Detection Systems, Information classification systems or Azure Information Protection may be used to join with the activity data to improve visibility.
Our next post will provide more examples of analyzing information using Graphs.
If you have any feedback please provide it at the GitHub project page or by emailing it to cxprad@microsoft.com.
We look forward to hearing from you!
—Jon Nordstrom, senior program manager, Office 365 customer experience

Publishers note: I am posting this on behalf my colleague Jon Nordstrom who is part of the Office 365 customer experience team. Myself and few other engineers thought you would all benefit from his knowledge of the Office 365 management activity API
A common question we get from organizations that move to Office 365 is, how do I get visibility into transactions that effect the information stored in Office 365. The security and compliance center and the Office 365 Management Activity API provide organizations with this visibility though detailed information with regards to user, admin, system, and policy actions and events from Office 365 and Azure Active Directory (Azure AD).
Reviewing the wealth of information available via the API and the audit logs, can be challenging though. Triaging detection results manually and categorizing related activities into groups can be difficult. The amounts of data generated from likely malicious activity can overwhelm investigators with irrelevant results. We know from experience the importance of accurate tooling, Microsoft Online Services processes petabytes of event monitoring data.
When Microsoft Online Services engineering started on the journey to view detection results as graphs we found that it enabled us to:
- evaluate intrusion detection results in context with related activity
- incorporate lower-fidelity indicators without being overwhelmed with benign results
- determine with greater fidelity when datacenter activity is likely to represent an intrusion
In this first post of our two-part series we will to help you understand how you can get the data necessary to perform a security analysis of it. The second post will focus on examples scenarios and using Power BI to visualize the data.
We are going to use Azure Cosmos DB, Azure Function Apps and cloud message queues to retrieve and store information. The data stores can be removed or purged, and the solution can be disabled or removed. Azure Cosmos DB also allows for the concept of TTL to expire content if you continue to synchronize the information. The sample graphs generated in this post were created with the free version of the ZoomCharts add-in for Power BI Desktop. Depending on your need there are several other graph add-ins available such as Network Navigator Chart and Force-Directed Graph. If you already have a method for obtaining data from the Activity API such as Azure Log Analytics , then continue to use that and access the information from Power BI which we briefly discuss in this post and go into more detail in next post.
1. Register an App with Azure Active Directory
Use this as a guide to create and register an application for making calls to the Office 365 Activity API. There are more detailed information about app registrations here. For this environment, the “Configure an X.509 certificate to enable service-to-service calls” is not necessary; it is enough to have an application with the appropriate permissions set. Don’t forget to complete the Administrator consent.
2. Setting up the infrastructure to push the Office 365 activities
The first step is to push the information you need to a store. We’ll use this sample from GitHub https://github.com/OfficeDev/O365-ActivityFeed-AzureFunction that allow you to push the past seven days of Office 365 Activity data to an instance of Azure Cosmos DB. You can limit the number of days and the workloads as needed. The code is created to run in two Azure Functions (PowerShell is currently in preview).
- Azure Function 1 places activity messages in a cloud message queue.
- Azure Function 2 picks up messages from that queue and transmits them to Azure Cosmos DB.
1. Create Function 1. (QueueEvents.ps1)
Remember to register a new Application in Azure Active Directory with adequate permissions before you take these steps.
If you don’t already have a Function App start to create one. By default, runtime is limited to 5 minutes for the functions running under the consumption plans, however, you can increase the runtime up to 10 minutes. An alternative is to use the App Consumption plan if you expect longer execution times. The consumption plans typically cover the need for retrieving the event data.

Create a New Function in the Function App

Enable experimental Language support, select Timer trigger and PowerShell.

Name the new function, and select the schedule for the trigger, which determines how often the function will pull data. A workload.log file is used to keep track of time to prevent duplicate requests.

Next, paste the code for function 1., QueueEvents.ps1 to the function.
Adjust the variables for sign in based on the AAD application registered. The Tenant GUID can be found under the Endpoints in the app registration. It is listed as part of the endpoints.

We will come back to adjust the storage variables shortly as part of the integration of the storage queues. Optionally modify the included workloads or message size. Note that reducing message size will increase the number of times Azure Function 2 is run. Making message size too large (for example, > 100) may cause you to exceed the limits of the queue and reduce performance.

Next, select integrate and add an Azure Queue Storage output. The queue name is specified using the $storageQueue variable use ‘outQueue’with single quotes unless you changed the queue name in the output settings. Click, Show Value on the “Storage account connection” and copy the Account key value to $StorageAccountKey and the AccountName to $StorageAccountName. These steps are required to use cloud queue functionality. A regular storage queue call does not allow for multiple objects.

Do verify that the queue was created, there have been some instances in the testing where they weren’t. In that case create a queue manually in the associated storage account.

2. Create Function 2. (StoreEvents.ps1)
Follow these steps to create the second function, which is a Queue trigger. Create a new Function in the previously created Function App. Provide a Queue name and the storage account defined in Function 1.

Add the code StoreEvents.ps1 and the information for the auth variables. The $triggerInput variable is the message parameter name.

Select Integrate and add a Cosmos DB. The $outputdocument variable is based on the Document parameter name. If you change the name, you must also change the name of the variable. Click Show Value for “Azure Cosmos DB account connection” and store the account key for making requests from Power BI (an alternative is to navigate to the Cosmos DB and use a read-only key).
If you don’t already have an Azure Cosmos DB in place create a new database before creating the output. If you don’t have a Cosmos DB and collection, ensure to set the checkbox to create the Azure Cosmos DB and collection.

3. Start the functions.
If you haven’t enabled the Office 365 Activity API subscriptions that is the first step to take. There is a sample script for how to enable the subscriptions at the GitHub page it can be run from on-premises (Enablesubscription.ps1). Do enable Office 365 audit log search as well.
When configuring a start date for retrieving data, note that the maximum time span is the past 7 days based on Activity API restrictions.
If you change variable $StoredTime = Get-content $Tracker to a date in the format of “yyyy-MM-ddTHH:mm:ss.fffZ” the workloads will use it as the starting point (e.g., $StoredTime = “2018-04-12T01:34:18.702Z”). Either disable the function after it has completed a first run or replace it with Get-content $Tracker as the next scheduled run will process the same data if not adjusted.
Alternatively, you can use Azure Storage Explorer and add these files with your desired start time to the root of the Azure functions blob store:
- Audit.AzureActiveDirectory.log
- Audit.SharePoint.log
- Audit.Exchange.log
- Audit.General.log
- DLP.All.log
The only thing you need in the file is the date example “2018-03-27T11:34:18.702Z” without the quotation marks. The log files allow for continuous synch excluding content previously synchronized.

When the functions are started, invocation logs will indicate if there are any issues. Use Azure Storage Explorer to view the storage queues.
If the function for some reason breaks the workload.log files will not be updated, and the function will start from the date last stamped in the workload.log file. There may be some overlap, but the analysis tools will identify any duplicates.
Ensure that the data is reaching your Cosmos DB instance by navigating to the Database, as shown below.

3. Open the data in Power BI
Download the Power BI Desktop client and the ZoomCharts referenced previously. Select to connect to Azure Cosmos DB in the Power BI desktop client.

Specify your connection string, etc., and optionally specify a query to limit the scope to the asset you want to investigate. Do remember that everything is case sensitive. In this case I have scoped it down to a specific site. Please see the GitHub page for more query samples. The subsequent step will require the Cosmos DB storage key that you stored as part of setting up the Cosmos DB.

Expand the columns by selecting the expand arrows. When done close and apply.

Import the Zoomchart visual if you haven’t completed that step previously.

Load the Nodes you want to review and the Measure.

Change the Measure to count to make the node sizes reflect the actual number of occurrences as an example

In many cases you can export csv files or directly make relationships to existing data and join it with the activity data. This is an example where we imported a few admin accounts from adminlist.csv. It could just as well be a number of files or ip addresses for which you need more information. We loaded the csv file.

In the next step we went to Relationships and joined the Adminlist with the UserID field to allow us to eliminate all accounts but those we are investigating.

In the visual level filter, we removed any account but those we are investigating

Summary
We have provided you with a starting point for how to analyze Office 365 Data using Power BI. The data can be pivoted and analyzed in many ways. Templates and continuously pulling the Activity Data can be used to quickly load data and draw conclusions from the wealth of information. Other event sources such as on premises Intrusion Detection Systems, Information classification systems or Azure Information Protection may be used to join with the activity data to improve visibility.
Our next post will provide more examples of analyzing information using Graphs.
If you have any feedback please provide it at the GitHub project page or by emailing it to cxprad@microsoft.com.
We look forward to hearing from you!
—Jon Nordstrom, senior program manager, Office 365 customer experience

Publishers note: I am posting this on behalf my colleague Jon Nordstrom who is part of the Office 365 customer experience team. Myself and few other engineers thought you would all benefit from his knowledge of the Office 365 management activity API
A common question we get from organizations that move to Office 365 is, how do I get visibility into transactions that effect the information stored in Office 365. The security and compliance center and the Office 365 Management Activity API provide organizations with this visibility though detailed information with regards to user, admin, system, and policy actions and events from Office 365 and Azure Active Directory (Azure AD).
Reviewing the wealth of information available via the API and the audit logs, can be challenging though. Triaging detection results manually and categorizing related activities into groups can be difficult. The amounts of data generated from likely malicious activity can overwhelm investigators with irrelevant results. We know from experience the importance of accurate tooling, Microsoft Online Services processes petabytes of event monitoring data.
When Microsoft Online Services engineering started on the journey to view detection results as graphs we found that it enabled us to:
- evaluate intrusion detection results in context with related activity
- incorporate lower-fidelity indicators without being overwhelmed with benign results
- determine with greater fidelity when datacenter activity is likely to represent an intrusion
In this first post of our two-part series we will to help you understand how you can get the data necessary to perform a security analysis of it. The second post will focus on examples scenarios and using Power BI to visualize the data.
We are going to use Azure Cosmos DB, Azure Function Apps and cloud message queues to retrieve and store information. The data stores can be removed or purged, and the solution can be disabled or removed. Azure Cosmos DB also allows for the concept of TTL to expire content if you continue to synchronize the information. The sample graphs generated in this post were created with the free version of the ZoomCharts add-in for Power BI Desktop. Depending on your need there are several other graph add-ins available such as Network Navigator Chart and Force-Directed Graph. If you already have a method for obtaining data from the Activity API such as Azure Log Analytics , then continue to use that and access the information from Power BI which we briefly discuss in this post and go into more detail in next post.
1. Register an App with Azure Active Directory
Use this as a guide to create and register an application for making calls to the Office 365 Activity API. There are more detailed information about app registrations here. For this environment, the “Configure an X.509 certificate to enable service-to-service calls” is not necessary; it is enough to have an application with the appropriate permissions set. Don’t forget to complete the Administrator consent.
2. Setting up the infrastructure to push the Office 365 activities
The first step is to push the information you need to a store. We’ll use this sample from GitHub https://github.com/OfficeDev/O365-ActivityFeed-AzureFunction that allow you to push the past seven days of Office 365 Activity data to an instance of Azure Cosmos DB. You can limit the number of days and the workloads as needed. The code is created to run in two Azure Functions (PowerShell is currently in preview).
- Azure Function 1 places activity messages in a cloud message queue.
- Azure Function 2 picks up messages from that queue and transmits them to Azure Cosmos DB.
1. Create Function 1. (QueueEvents.ps1)
Remember to register a new Application in Azure Active Directory with adequate permissions before you take these steps.
If you don’t already have a Function App start to create one. By default, runtime is limited to 5 minutes for the functions running under the consumption plans, however, you can increase the runtime up to 10 minutes. An alternative is to use the App Consumption plan if you expect longer execution times. The consumption plans typically cover the need for retrieving the event data.

Create a New Function in the Function App

Enable experimental Language support, select Timer trigger and PowerShell.

Name the new function, and select the schedule for the trigger, which determines how often the function will pull data. A workload.log file is used to keep track of time to prevent duplicate requests.

Next, paste the code for function 1., QueueEvents.ps1 to the function.
Adjust the variables for sign in based on the AAD application registered. The Tenant GUID can be found under the Endpoints in the app registration. It is listed as part of the endpoints.

We will come back to adjust the storage variables shortly as part of the integration of the storage queues. Optionally modify the included workloads or message size. Note that reducing message size will increase the number of times Azure Function 2 is run. Making message size too large (for example, > 100) may cause you to exceed the limits of the queue and reduce performance.

Next, select integrate and add an Azure Queue Storage output. The queue name is specified using the $storageQueue variable use ‘outQueue’with single quotes unless you changed the queue name in the output settings. Click, Show Value on the “Storage account connection” and copy the Account key value to $StorageAccountKey and the AccountName to $StorageAccountName. These steps are required to use cloud queue functionality. A regular storage queue call does not allow for multiple objects.

Do verify that the queue was created, there have been some instances in the testing where they weren’t. In that case create a queue manually in the associated storage account.

2. Create Function 2. (StoreEvents.ps1)
Follow these steps to create the second function, which is a Queue trigger. Create a new Function in the previously created Function App. Provide a Queue name and the storage account defined in Function 1.

Add the code StoreEvents.ps1 and the information for the auth variables. The $triggerInput variable is the message parameter name.

Select Integrate and add a Cosmos DB. The $outputdocument variable is based on the Document parameter name. If you change the name, you must also change the name of the variable. Click Show Value for “Azure Cosmos DB account connection” and store the account key for making requests from Power BI (an alternative is to navigate to the Cosmos DB and use a read-only key).
If you don’t already have an Azure Cosmos DB in place create a new database before creating the output. If you don’t have a Cosmos DB and collection, ensure to set the checkbox to create the Azure Cosmos DB and collection.

3. Start the functions.
If you haven’t enabled the Office 365 Activity API subscriptions that is the first step to take. There is a sample script for how to enable the subscriptions at the GitHub page it can be run from on-premises (Enablesubscription.ps1). Do enable Office 365 audit log search as well.
When configuring a start date for retrieving data, note that the maximum time span is the past 7 days based on Activity API restrictions.
If you change variable $StoredTime = Get-content $Tracker to a date in the format of “yyyy-MM-ddTHH:mm:ss.fffZ” the workloads will use it as the starting point (e.g., $StoredTime = “2018-04-12T01:34:18.702Z”). Either disable the function after it has completed a first run or replace it with Get-content $Tracker as the next scheduled run will process the same data if not adjusted.
Alternatively, you can use Azure Storage Explorer and add these files with your desired start time to the root of the Azure functions blob store:
- Audit.AzureActiveDirectory.log
- Audit.SharePoint.log
- Audit.Exchange.log
- Audit.General.log
- DLP.All.log
The only thing you need in the file is the date example “2018-03-27T11:34:18.702Z” without the quotation marks. The log files allow for continuous synch excluding content previously synchronized.

When the functions are started, invocation logs will indicate if there are any issues. Use Azure Storage Explorer to view the storage queues.
If the function for some reason breaks the workload.log files will not be updated, and the function will start from the date last stamped in the workload.log file. There may be some overlap, but the analysis tools will identify any duplicates.
Ensure that the data is reaching your Cosmos DB instance by navigating to the Database, as shown below.

3. Open the data in Power BI
Download the Power BI Desktop client and the ZoomCharts referenced previously. Select to connect to Azure Cosmos DB in the Power BI desktop client.

Specify your connection string, etc., and optionally specify a query to limit the scope to the asset you want to investigate. Do remember that everything is case sensitive. In this case I have scoped it down to a specific site. Please see the GitHub page for more query samples. The subsequent step will require the Cosmos DB storage key that you stored as part of setting up the Cosmos DB.

Expand the columns by selecting the expand arrows. When done close and apply.

Import the Zoomchart visual if you haven’t completed that step previously.

Load the Nodes you want to review and the Measure.

Change the Measure to count to make the node sizes reflect the actual number of occurrences as an example

In many cases you can export csv files or directly make relationships to existing data and join it with the activity data. This is an example where we imported a few admin accounts from adminlist.csv. It could just as well be a number of files or ip addresses for which you need more information. We loaded the csv file.

In the next step we went to Relationships and joined the Adminlist with the UserID field to allow us to eliminate all accounts but those we are investigating.

In the visual level filter, we removed any account but those we are investigating

Summary
We have provided you with a starting point for how to analyze Office 365 Data using Power BI. The data can be pivoted and analyzed in many ways. Templates and continuously pulling the Activity Data can be used to quickly load data and draw conclusions from the wealth of information. Other event sources such as on premises Intrusion Detection Systems, Information classification systems or Azure Information Protection may be used to join with the activity data to improve visibility.
Our next post will provide more examples of analyzing information using Graphs.
If you have any feedback please provide it at the GitHub project page or by emailing it to cxprad@microsoft.com.
We look forward to hearing from you!
—Jon Nordstrom, senior program manager, Office 365 customer experience

Publishers note: I am posting this on behalf my colleague Jon Nordstrom who is part of the Office 365 customer experience team. Myself and few other engineers thought you would all benefit from his knowledge of the Office 365 management activity API
A common question we get from organizations that move to Office 365 is, how do I get visibility into transactions that effect the information stored in Office 365. The security and compliance center and the Office 365 Management Activity API provide organizations with this visibility though detailed information with regards to user, admin, system, and policy actions and events from Office 365 and Azure Active Directory (Azure AD).
Reviewing the wealth of information available via the API and the audit logs, can be challenging though. Triaging detection results manually and categorizing related activities into groups can be difficult. The amounts of data generated from likely malicious activity can overwhelm investigators with irrelevant results. We know from experience the importance of accurate tooling, Microsoft Online Services processes petabytes of event monitoring data.
When Microsoft Online Services engineering started on the journey to view detection results as graphs we found that it enabled us to:
- evaluate intrusion detection results in context with related activity
- incorporate lower-fidelity indicators without being overwhelmed with benign results
- determine with greater fidelity when datacenter activity is likely to represent an intrusion
In this first post of our two-part series we will to help you understand how you can get the data necessary to perform a security analysis of it. The second post will focus on examples scenarios and using Power BI to visualize the data.
We are going to use Azure Cosmos DB, Azure Function Apps and cloud message queues to retrieve and store information. The data stores can be removed or purged, and the solution can be disabled or removed. Azure Cosmos DB also allows for the concept of TTL to expire content if you continue to synchronize the information. The sample graphs generated in this post were created with the free version of the ZoomCharts add-in for Power BI Desktop. Depending on your need there are several other graph add-ins available such as Network Navigator Chart and Force-Directed Graph. If you already have a method for obtaining data from the Activity API such as Azure Log Analytics , then continue to use that and access the information from Power BI which we briefly discuss in this post and go into more detail in next post.
1. Register an App with Azure Active Directory
Use this as a guide to create and register an application for making calls to the Office 365 Activity API. There are more detailed information about app registrations here. For this environment, the “Configure an X.509 certificate to enable service-to-service calls” is not necessary; it is enough to have an application with the appropriate permissions set. Don’t forget to complete the Administrator consent.
2. Setting up the infrastructure to push the Office 365 activities
The first step is to push the information you need to a store. We’ll use this sample from GitHub https://github.com/OfficeDev/O365-ActivityFeed-AzureFunction that allow you to push the past seven days of Office 365 Activity data to an instance of Azure Cosmos DB. You can limit the number of days and the workloads as needed. The code is created to run in two Azure Functions (PowerShell is currently in preview).
- Azure Function 1 places activity messages in a cloud message queue.
- Azure Function 2 picks up messages from that queue and transmits them to Azure Cosmos DB.
1. Create Function 1. (QueueEvents.ps1)
Remember to register a new Application in Azure Active Directory with adequate permissions before you take these steps.
If you don’t already have a Function App start to create one. By default, runtime is limited to 5 minutes for the functions running under the consumption plans, however, you can increase the runtime up to 10 minutes. An alternative is to use the App Consumption plan if you expect longer execution times. The consumption plans typically cover the need for retrieving the event data.

Create a New Function in the Function App

Enable experimental Language support, select Timer trigger and PowerShell.

Name the new function, and select the schedule for the trigger, which determines how often the function will pull data. A workload.log file is used to keep track of time to prevent duplicate requests.

Next, paste the code for function 1., QueueEvents.ps1 to the function.
Adjust the variables for sign in based on the AAD application registered. The Tenant GUID can be found under the Endpoints in the app registration. It is listed as part of the endpoints.

We will come back to adjust the storage variables shortly as part of the integration of the storage queues. Optionally modify the included workloads or message size. Note that reducing message size will increase the number of times Azure Function 2 is run. Making message size too large (for example, > 100) may cause you to exceed the limits of the queue and reduce performance.

Next, select integrate and add an Azure Queue Storage output. The queue name is specified using the $storageQueue variable use ‘outQueue’with single quotes unless you changed the queue name in the output settings. Click, Show Value on the “Storage account connection” and copy the Account key value to $StorageAccountKey and the AccountName to $StorageAccountName. These steps are required to use cloud queue functionality. A regular storage queue call does not allow for multiple objects.

Do verify that the queue was created, there have been some instances in the testing where they weren’t. In that case create a queue manually in the associated storage account.

2. Create Function 2. (StoreEvents.ps1)
Follow these steps to create the second function, which is a Queue trigger. Create a new Function in the previously created Function App. Provide a Queue name and the storage account defined in Function 1.

Add the code StoreEvents.ps1 and the information for the auth variables. The $triggerInput variable is the message parameter name.

Select Integrate and add a Cosmos DB. The $outputdocument variable is based on the Document parameter name. If you change the name, you must also change the name of the variable. Click Show Value for “Azure Cosmos DB account connection” and store the account key for making requests from Power BI (an alternative is to navigate to the Cosmos DB and use a read-only key).
If you don’t already have an Azure Cosmos DB in place create a new database before creating the output. If you don’t have a Cosmos DB and collection, ensure to set the checkbox to create the Azure Cosmos DB and collection.

3. Start the functions.
If you haven’t enabled the Office 365 Activity API subscriptions that is the first step to take. There is a sample script for how to enable the subscriptions at the GitHub page it can be run from on-premises (Enablesubscription.ps1). Do enable Office 365 audit log search as well.
When configuring a start date for retrieving data, note that the maximum time span is the past 7 days based on Activity API restrictions.
If you change variable $StoredTime = Get-content $Tracker to a date in the format of “yyyy-MM-ddTHH:mm:ss.fffZ” the workloads will use it as the starting point (e.g., $StoredTime = “2018-04-12T01:34:18.702Z”). Either disable the function after it has completed a first run or replace it with Get-content $Tracker as the next scheduled run will process the same data if not adjusted.
Alternatively, you can use Azure Storage Explorer and add these files with your desired start time to the root of the Azure functions blob store:
- Audit.AzureActiveDirectory.log
- Audit.SharePoint.log
- Audit.Exchange.log
- Audit.General.log
- DLP.All.log
The only thing you need in the file is the date example “2018-03-27T11:34:18.702Z” without the quotation marks. The log files allow for continuous synch excluding content previously synchronized.

When the functions are started, invocation logs will indicate if there are any issues. Use Azure Storage Explorer to view the storage queues.
If the function for some reason breaks the workload.log files will not be updated, and the function will start from the date last stamped in the workload.log file. There may be some overlap, but the analysis tools will identify any duplicates.
Ensure that the data is reaching your Cosmos DB instance by navigating to the Database, as shown below.

3. Open the data in Power BI
Download the Power BI Desktop client and the ZoomCharts referenced previously. Select to connect to Azure Cosmos DB in the Power BI desktop client.

Specify your connection string, etc., and optionally specify a query to limit the scope to the asset you want to investigate. Do remember that everything is case sensitive. In this case I have scoped it down to a specific site. Please see the GitHub page for more query samples. The subsequent step will require the Cosmos DB storage key that you stored as part of setting up the Cosmos DB.

Expand the columns by selecting the expand arrows. When done close and apply.

Import the Zoomchart visual if you haven’t completed that step previously.

Load the Nodes you want to review and the Measure.

Change the Measure to count to make the node sizes reflect the actual number of occurrences as an example

In many cases you can export csv files or directly make relationships to existing data and join it with the activity data. This is an example where we imported a few admin accounts from adminlist.csv. It could just as well be a number of files or ip addresses for which you need more information. We loaded the csv file.

In the next step we went to Relationships and joined the Adminlist with the UserID field to allow us to eliminate all accounts but those we are investigating.

In the visual level filter, we removed any account but those we are investigating

Summary
We have provided you with a starting point for how to analyze Office 365 Data using Power BI. The data can be pivoted and analyzed in many ways. Templates and continuously pulling the Activity Data can be used to quickly load data and draw conclusions from the wealth of information. Other event sources such as on premises Intrusion Detection Systems, Information classification systems or Azure Information Protection may be used to join with the activity data to improve visibility.
Our next post will provide more examples of analyzing information using Graphs.
If you have any feedback please provide it at the GitHub project page or by emailing it to cxprad@microsoft.com.
We look forward to hearing from you!
—Jon Nordstrom, senior program manager, Office 365 customer experience






































