Data privacy continues to be top-of-mind for businesses. For example, nearly one-third of global enterprises view compliance with new privacy laws, like the EU General Data Protection Regulation (GDPR), as one of the biggest IT hurdles that their organizations face1.
The arrival of the California Consumer Privacy Act (CCPA) will impact many large businesses with customers who reside in California. With more than 39 million individuals residing in California2 and transacting with businesses worldwide, the scope of the CCPA is significant. Businesses around the world need to start formulating a compliance strategy now so they are well prepared when enforcement begins in January 2020.
Today, we want to share five tips that can help your organization to get ready for new privacy regulations such as CCPA with Microsoft 365:
Tip 1: Leverage the GDPR assessment in Compliance Manager
With many commonalities between GDPR and CCPA, such as data subject rights of access, erasure, and portability, organizations can leverage their GDPR program to start tackling CCPA compliance now.
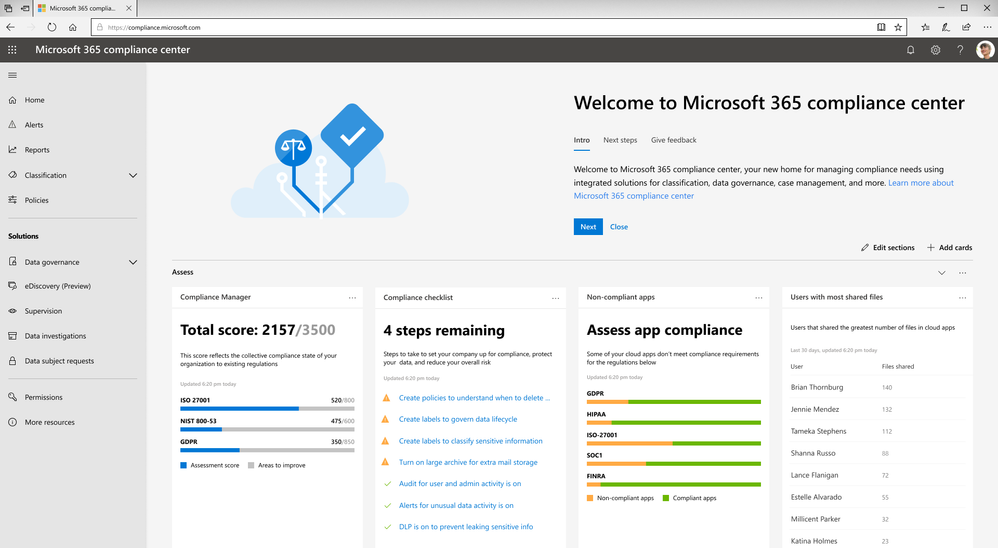
To help businesses assess Microsoft cloud services and find applicable technology solutions to implement GDPR controls, we released Compliance Manager in 2018. Compliance Manager is a cloud-based tool that gives you step-by-step guidance to help you implement, track and record your data-protection controls. You can get started by using the GDPR assessment in Compliance Manager today.
Tip 2: Establish a process to efficiently respond to Data Subject Requests
According to a blog post by Julie Brill, U.S consumers are highly aware of their privacy rights with the highest engagement of approximately 2 million users signing into the Microsoft privacy dashboard to manage their information in 4 months since GDPR came into effect. With that in mind, we encourage you to start building out your data subject access requests process today, because CCPA requires a 12-month look-back period.
To get ready to respond to this high demand of data access requests, we encourage you to start using the Data Subject Requests (DSRs) tool in the new Microsoft 365 compliance center, which allows your privacy and compliance teams to respond more efficiently to DSRs in a timely manner.

Tip 3: Discover, classify & label, and protect sensitive data
The CCPA will impose penalties for data breaches of consumers’ personal information. As organizations live in a world with a tsunami of data across their digital estate, understanding where their most sensitive data is and how to protect it is critical to reduce compliance risks.
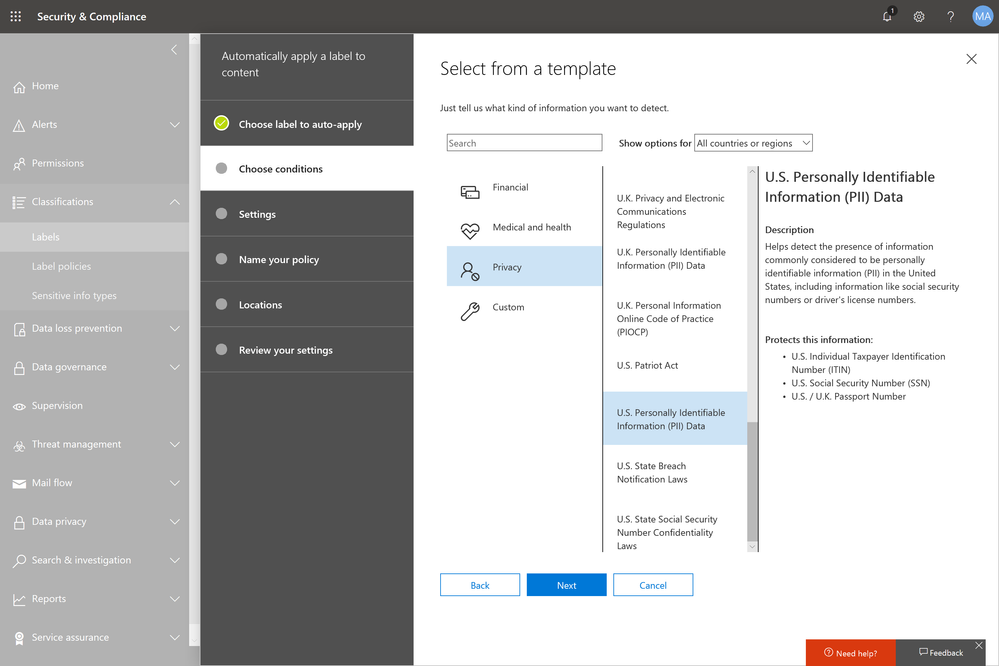
Microsoft Information Protection harnesses an integrated and intelligent approach to target the 80 percent of corporate data that is estimated to be “dark” or un-classified and unprotected3. You can start to make use of the U.S. PII sensitive data types to automatically discover, classify, and protect personal data to help you with CCPA compliance.
Tip 4: Use encryption to protect and control your sensitive emails
Regulations like GDPR and CCPA see encryption as an effective method to protect personal information from unauthorized parties in the event of a data breach.
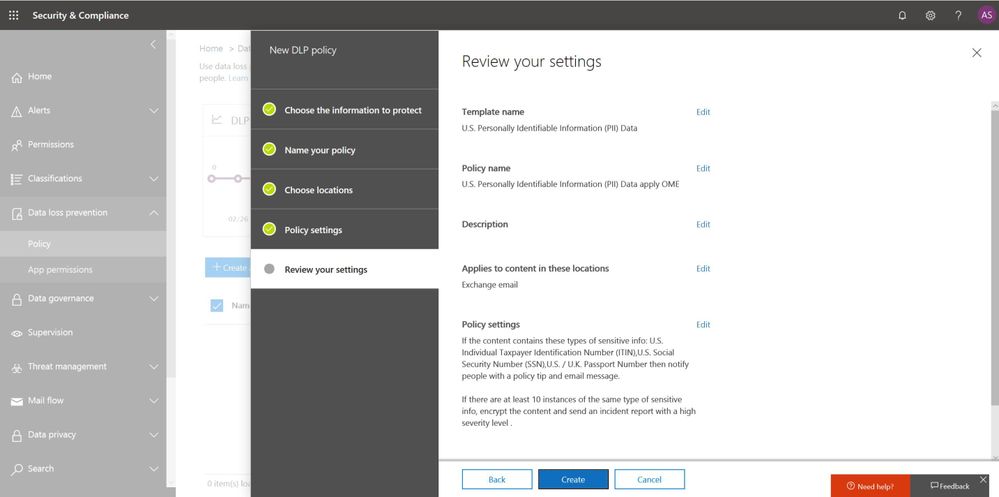
Office 365 Message Encryption enables users to protect sensitive emails shared with anyone inside and outside of your organization. If your tenant is eligible, Office 365 Message Encryption will be on by default. You can get started by setting up a Data Loss Prevention policy that applies Office 365 Message Encryption to U.S. PII sensitive data types.
Also start educating your end users to apply protection such as “do not forward” or “encrypt-only” directly from Outlook (either desktop or web version). Watch this video to learn more.
Tip 5: Champion consumer privacy rights to build a sustainable business
While the CCPA brings prominent challenges to many businesses who were not subject to GDPR, we encourage those organizations to view CCPA and other privacy laws as an opportunity to enhance their privacy programs and embrace privacy as a corporate value to build trust with customers.
Check out the “Championing privacy rights to drive differentiation” webcast with Microsoft CIO Kurt DelBene, CISO Bret Arsenault, and a featured speaker, Enza Iannopollo of Forrester, who discuss the new era of privacy expectations and how to invest in privacy as a business driver.
Learn more about the Microsoft cloud
At Microsoft, we are committed to partnering with you to keep advancing our solutions to help you protect your digital estate in a more compliant manner. Here are some additional resources to help you in your ongoing compliance journey:
- Download our e-book to learn more about how to protect digital privacy.
- Experience first-hand how Microsoft solutions can help solve your business challenges by registering for an upcoming hands-on online experience (US only). Click here for free Microsoft 365 Compliance product training outside the US.
- Learn more about the new Information Protection and Compliance offering in Microsoft 365
1 Forrester. “Global Business Technographics Security Survey, 2018.” August 2018. www.forrester.com/Global+Business+Technographics+Security+Survey+2018/-/E-sus4551.
2 Public Policy Institute of California. “Just the Facts: California’s Population.” www.ppic.org/publication/californias-population/.
3 Andrew Trice. “The Future of Cognitive Computing.” IBM blog. November 2015. www.ibm.com/blogs/bluemix/2015/11/future-of-cognitive-computing/.

Data privacy continues to be top-of-mind for businesses. For example, nearly one-third of global enterprises view compliance with new privacy laws, like the EU General Data Protection Regulation (GDPR), as one of the biggest IT hurdles that their organizations face1.
The arrival of the California Consumer Privacy Act (CCPA) will impact many large businesses with customers who reside in California. With more than 39 million individuals residing in California2 and transacting with businesses worldwide, the scope of the CCPA is significant. Businesses around the world need to start formulating a compliance strategy now so they are well prepared when enforcement begins in January 2020.
Today, we want to share five tips that can help your organization to get ready for new privacy regulations such as CCPA with Microsoft 365:
Tip 1: Leverage the GDPR assessment in Compliance Manager
With many commonalities between GDPR and CCPA, such as data subject rights of access, erasure, and portability, organizations can leverage their GDPR program to start tackling CCPA compliance now.
To help businesses assess Microsoft cloud services and find applicable technology solutions to implement GDPR controls, we released Compliance Manager in 2018. Compliance Manager is a cloud-based tool that gives you step-by-step guidance to help you implement, track and record your data-protection controls. You can get started by using the GDPR assessment in Compliance Manager today.
Tip 2: Establish a process to efficiently respond to Data Subject Requests
According to a blog post by Julie Brill, U.S consumers are highly aware of their privacy rights with the highest engagement of approximately 2 million users signing into the Microsoft privacy dashboard to manage their information in 4 months since GDPR came into effect. With that in mind, we encourage you to start building out your data subject access requests process today, because CCPA requires a 12-month look-back period.
To get ready to respond to this high demand of data access requests, we encourage you to start using the Data Subject Requests (DSRs) tool in the new Microsoft 365 compliance center, which allows your privacy and compliance teams to respond more efficiently to DSRs in a timely manner.

Tip 3: Discover, classify & label, and protect sensitive data
The CCPA will impose penalties for data breaches of consumers’ personal information. As organizations live in a world with a tsunami of data across their digital estate, understanding where their most sensitive data is and how to protect it is critical to reduce compliance risks.
Microsoft Information Protection harnesses an integrated and intelligent approach to target the 80 percent of corporate data that is estimated to be “dark” or un-classified and unprotected3. You can start to make use of the U.S. PII sensitive data types to automatically discover, classify, and protect personal data to help you with CCPA compliance.

Tip 4: Use encryption to protect and control your sensitive emails
Regulations like GDPR and CCPA see encryption as an effective method to protect personal information from unauthorized parties in the event of a data breach.
Office 365 Message Encryption enables users to protect sensitive emails shared with anyone inside and outside of your organization. If your tenant is eligible, Office 365 Message Encryption will be on by default. You can get started by setting up a Data Loss Prevention policy that applies Office 365 Message Encryption to U.S. PII sensitive data types.

Also start educating your end users to apply protection such as “do not forward” or “encrypt-only” directly from Outlook (either desktop or web version). Watch this video to learn more.
Tip 5: Champion consumer privacy rights to build a sustainable business
While the CCPA brings prominent challenges to many businesses who were not subject to GDPR, we encourage those organizations to view CCPA and other privacy laws as an opportunity to enhance their privacy programs and embrace privacy as a corporate value to build trust with customers.
Check out the “Championing privacy rights to drive differentiation” webcast with Microsoft CIO Kurt DelBene, CISO Bret Arsenault, and a featured speaker, Enza Iannopollo of Forrester, who discuss the new era of privacy expectations and how to invest in privacy as a business driver.
Learn more about the Microsoft cloud
At Microsoft, we are committed to partnering with you to keep advancing our solutions to help you protect your digital estate in a more compliant manner. Here are some additional resources to help you in your ongoing compliance journey:
- Download our e-book to learn more about how to protect digital privacy.
- Experience first-hand how Microsoft solutions can help solve your business challenges by registering for an upcoming hands-on online experience (US only). Click here for free Microsoft 365 Compliance product training outside the US.
- Learn more about the new Information Protection and Compliance offering in Microsoft 365
1 Forrester. “Global Business Technographics Security Survey, 2018.” August 2018. www.forrester.com/Global+Business+Technographics+Security+Survey+2018/-/E-sus4551.
2 Public Policy Institute of California. “Just the Facts: California’s Population.” www.ppic.org/publication/californias-population/.
3 Andrew Trice. “The Future of Cognitive Computing.” IBM blog. November 2015. www.ibm.com/blogs/bluemix/2015/11/future-of-cognitive-computing/.

Data privacy continues to be top-of-mind for businesses. For example, nearly one-third of global enterprises view compliance with new privacy laws, like the EU General Data Protection Regulation (GDPR), as one of the biggest IT hurdles that their organizations face1.
The arrival of the California Consumer Privacy Act (CCPA) will impact many large businesses with customers who reside in California. With more than 39 million individuals residing in California2 and transacting with businesses worldwide, the scope of the CCPA is significant. Businesses around the world need to start formulating a compliance strategy now so they are well prepared when enforcement begins in January 2020.
Today, we want to share five tips that can help your organization to get ready for new privacy regulations such as CCPA with Microsoft 365:
Tip 1: Leverage the GDPR assessment in Compliance Manager
With many commonalities between GDPR and CCPA, such as data subject rights of access, erasure, and portability, organizations can leverage their GDPR program to start tackling CCPA compliance now.
To help businesses assess Microsoft cloud services and find applicable technology solutions to implement GDPR controls, we released Compliance Manager in 2018. Compliance Manager is a cloud-based tool that gives you step-by-step guidance to help you implement, track and record your data-protection controls. You can get started by using the GDPR assessment in Compliance Manager today.
Tip 2: Establish a process to efficiently respond to Data Subject Requests
According to a blog post by Julie Brill, U.S consumers are highly aware of their privacy rights with the highest engagement of approximately 2 million users signing into the Microsoft privacy dashboard to manage their information in 4 months since GDPR came into effect. With that in mind, we encourage you to start building out your data subject access requests process today, because CCPA requires a 12-month look-back period.
To get ready to respond to this high demand of data access requests, we encourage you to start using the Data Subject Requests (DSRs) tool in the new Microsoft 365 compliance center, which allows your privacy and compliance teams to respond more efficiently to DSRs in a timely manner.

Tip 3: Discover, classify & label, and protect sensitive data
The CCPA will impose penalties for data breaches of consumers’ personal information. As organizations live in a world with a tsunami of data across their digital estate, understanding where their most sensitive data is and how to protect it is critical to reduce compliance risks.
Microsoft Information Protection harnesses an integrated and intelligent approach to target the 80 percent of corporate data that is estimated to be “dark” or un-classified and unprotected3. You can start to make use of the U.S. PII sensitive data types to automatically discover, classify, and protect personal data to help you with CCPA compliance.

Tip 4: Use encryption to protect and control your sensitive emails
Regulations like GDPR and CCPA see encryption as an effective method to protect personal information from unauthorized parties in the event of a data breach.
Office 365 Message Encryption enables users to protect sensitive emails shared with anyone inside and outside of your organization. If your tenant is eligible, Office 365 Message Encryption will be on by default. You can get started by setting up a Data Loss Prevention policy that applies Office 365 Message Encryption to U.S. PII sensitive data types.

Also start educating your end users to apply protection such as “do not forward” or “encrypt-only” directly from Outlook (either desktop or web version). Watch this video to learn more.
Tip 5: Champion consumer privacy rights to build a sustainable business
While the CCPA brings prominent challenges to many businesses who were not subject to GDPR, we encourage those organizations to view CCPA and other privacy laws as an opportunity to enhance their privacy programs and embrace privacy as a corporate value to build trust with customers.
Check out the “Championing privacy rights to drive differentiation” webcast with Microsoft CIO Kurt DelBene, CISO Bret Arsenault, and a featured speaker, Enza Iannopollo of Forrester, who discuss the new era of privacy expectations and how to invest in privacy as a business driver.
Learn more about the Microsoft cloud
At Microsoft, we are committed to partnering with you to keep advancing our solutions to help you protect your digital estate in a more compliant manner. Here are some additional resources to help you in your ongoing compliance journey:
- Download our e-book to learn more about how to protect digital privacy.
- Experience first-hand how Microsoft solutions can help solve your business challenges by registering for an upcoming hands-on online experience (US only). Click here for free Microsoft 365 Compliance product training outside the US.
- Learn more about the new Information Protection and Compliance offering in Microsoft 365
1 Forrester. “Global Business Technographics Security Survey, 2018.” August 2018. www.forrester.com/Global+Business+Technographics+Security+Survey+2018/-/E-sus4551.
2 Public Policy Institute of California. “Just the Facts: California’s Population.” www.ppic.org/publication/californias-population/.
3 Andrew Trice. “The Future of Cognitive Computing.” IBM blog. November 2015. www.ibm.com/blogs/bluemix/2015/11/future-of-cognitive-computing/.
Today, we are announcing new capabilities in the Microsoft Graph Security API to help our customers simplify integration, speed up response, and improve the effectiveness of their existing security investments. The latest updates include an expanded list of alert providers, new capabilities that enable threat intelligence sharing, streamline the creation of security automation workflows, and enable rich security analytics and reporting. Finally, we’re announcing several new integration partners.
Security Alerts
The Microsoft Graph Security API provides a unified interface and common schema to simplify integration of security alerts from Microsoft products, services, and partners. In addition to the many Microsoft and partner solutions previously available for the Microsoft Graph Security API, you can now access security alerts from Office 365 and Azure Advanced Threat Protection solutions as well as the new Microsoft Azure Sentinel service.
Developers can integrate alerts via a single endpoint, using one authentication key and one SDK. You can query for all alerts pertaining to specific users, devices, files, or command lines when investigating a specific threat or use webhook subscriptions to get notified when any new alert matching your search criteria is created or updated. Learn more about alerts.
Threat Intelligence (preview)
Threat indicators, also referred to as indicators of compromise or IoCs, represent data about known threats, such as malicious files, URLs, domains, and IP addresses. Microsoft amasses a huge volume of indicators each day using trillions of unique insights into cloud, users, and endpoints, which plays a huge role in how we protect Microsoft and our customers. You may also generate indicators through internal threat intelligence gathering or acquire indicators from threat intelligence communities, licensed feeds, and other sources. In addition to the vast threat intelligence built into Microsoft products and services, you can now also leverage your own indicators to enable custom detections in Microsoft solutions. Learn more.
- Connect your threat intelligence platform and communities to automatically share the latest indicators with Microsoft. Use the Microsoft Graph Security API or leverage integrations with leading threat intelligence platforms, including Palo Alto Networks MineMeld and the open source MISP platform. Use with Azure Sentinel today to correlate threat intelligence with log data to alert on malicious activity. Refer to the tiIndicators schema.
- Take immediate action in response to new threat, such as block file, URL, domain, or IP address from within your security tools and workflows. When a security analyst discovers a new threat, protection can be instantly enabled in your Microsoft security solutions. Try it first with Windows Defender ATP (coming soon) to block malicious activity on your Windows endpoints using the properties seen in alerts or identified during investigations. Refer to the SecurityActions schema.
Security Automation
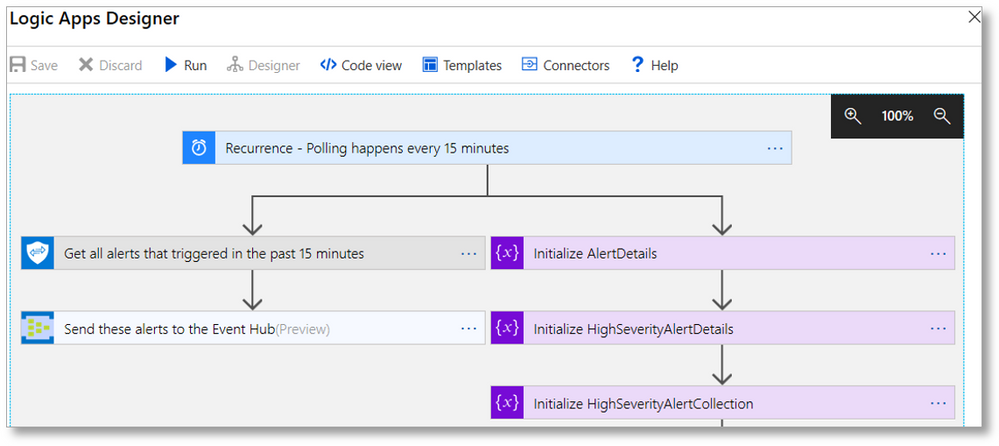
In a world of fast-moving, disruptive attacks and under-resourced security teams, automation of security workflows is essential. However, development of workflows to expedite alert routing, triage, investigation, and remediation can be challenging to create and maintain. We recently announced a set of Microsoft Graph Security API connectors to simplify development of automated security workflows without writing any code.
- Leverage Azure Logic Apps, Microsoft Flow, and PowerApps connectors to quickly build automation workflows using insights from the Microsoft Graph Security API. Mash up the Microsoft Graph Security API connector with over 200 other connectors to build workflows that act on security alerts, such as automatically routing high severity alerts to the on-call analyst – creating a ticket assigned to that user, sending an email or SMS notification, and collecting related alerts to speed their investigation See other example workflows.

Security Analytics + Reporting
The Microsoft Graph Security API now makes it easier than ever to analyze and visualize data across different security products running in your organization to get deeper security insights. Create reports and dashboards for visibility into active threats and trends. Discover opportunities to learn from the data and train your security models. The Microsoft Graph Security API schema provides multiple properties to pivot on to build rich reports and exploratory datasets using your security data.
- Use the PowerBI connector to create enterprise-wide security dashboards and reports. Get a complete picture of security alerts and secure score across your organization. Mash up security data with data from the other Power BI connectors, like Excel workbooks or other databases, for richer context. Use Power BI and Microsoft Flow to trigger an automated security workflow based on metrics, such as a percent decrease in your secure score. A sample dashboard and template help you get started. Learn more.
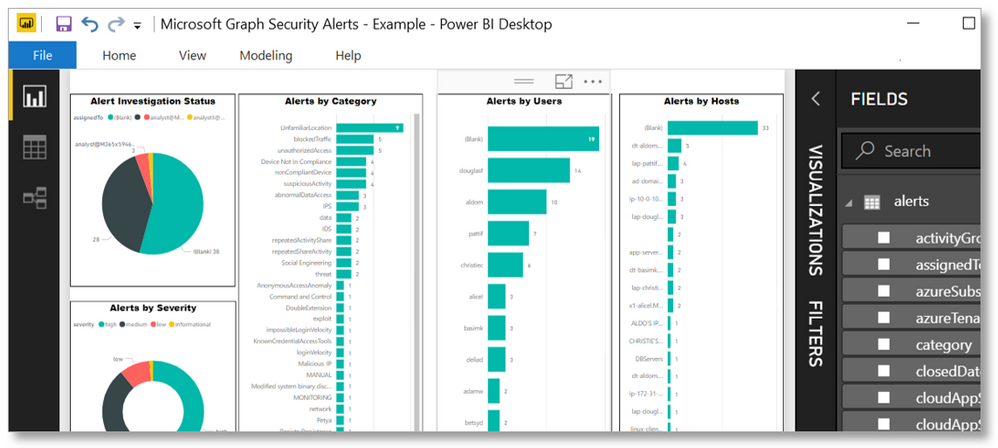
- Get deep insights to train security solutions by leveraging the power of Jupyter Notebooks for Microsoft Graph Security API. Use these Notebooks to build your visualizations and training data models with alert properties for users, files, hosts, processes, etc. across multiple security products. Learn more.
Integrated Partner Solutions
The Microsoft Graph Security API offers a wide range of possibilities for partners to build and enhance security solutions. We’ve been building an ecosystem of technology partners and are excited to announce the following new integrations:
- Barracuda Cloud Security Guardian accesses alerts and a secure score from the Microsoft Security Graph API and displays this on a single plane of glass.
- Bay Dynamics Risk Fabric integrates with the Microsoft Graph Security API to gain greater visibility into threats, enabling them to better prioritize remediation activities.
- Citrix Analytics leverages the Microsoft Graph Security API to correlate alerts from the Graph with Citrix products and take security actions. See video.
- DF Labs integrates with the Microsoft Graph Security API to enable its IncMan SOAR solution to orchestrate and automate response to threats from Graph Providers.
- FireEye Helix uses the Microsoft Graph Security API to integrate security insights from Microsoft and partners into its security operations platform.
- JASK uses the Microsoft Graph Security API to ingest data and information related to Microsoft users, applications, and events into its ASOC SIEM platform.
- Swimlane’s SOAR platform integrates with Microsoft Graph Security API to orchestrate and automate incident response across multiple solutions for faster threat response.
Find out more about partner integration opportunities here.
In addition to technology partners, we’re also working closely with a number of managed security services providers who are building solutions leveraging the Security API. Most recently, SWC Technology Partners announced new security solutions that help improve organizations’ security posture. In particular, SWC is using the Microsoft Graph Security API in its Managed Defense Service that helps identify suspicious behavior and allows organizations to quickly surface and remediate threats.
We know that our customers struggle with integrating their diverse security tools, workflows, and systems. The cost, time, and resources necessary to integrate systems, enable correlation of alerts, connect to existing workflows, and provide access to contextual data is extremely high. We’re excited about the potential the Microsoft Graph Security API offers to directly address these challenges.
Get started today
Join us at the Microsoft booth, N6059 in the north expo hall, at RSA Conference 2019 in San Francisco. You’ll get the chance to speak to experts and see how our partners are using the API.
To learn more and get started with using the Microsoft Graph Security API, check out the following resources:

Today, we are announcing new capabilities in the Microsoft Graph Security API to help our customers simplify integration, speed up response, and improve the effectiveness of their existing security investments. The latest updates include an expanded list of alert providers, new capabilities that enable threat intelligence sharing, streamline the creation of security automation workflows, and enable rich security analytics and reporting. Finally, we’re announcing several new integration partners.
Security Alerts
The Microsoft Graph Security API provides a unified interface and common schema to simplify integration of security alerts from Microsoft products, services, and partners. In addition to the many Microsoft and partner solutions previously available for the Microsoft Graph Security API, you can now access security alerts from Office 365 and Azure Advanced Threat Protection solutions as well as the new Microsoft Azure Sentinel service.
Developers can integrate alerts via a single endpoint, using one authentication key and one SDK. You can query for all alerts pertaining to specific users, devices, files, or command lines when investigating a specific threat or use webhook subscriptions to get notified when any new alert matching your search criteria is created or updated. Learn more about alerts.
Threat Intelligence (preview)
Threat indicators, also referred to as indicators of compromise or IoCs, represent data about known threats, such as malicious files, URLs, domains, and IP addresses. Microsoft amasses a huge volume of indicators each day using trillions of unique insights into cloud, users, and endpoints, which plays a huge role in how we protect Microsoft and our customers. You may also generate indicators through internal threat intelligence gathering or acquire indicators from threat intelligence communities, licensed feeds, and other sources. In addition to the vast threat intelligence built into Microsoft products and services, you can now also leverage your own indicators to enable custom detections in Microsoft solutions. Learn more.
- Connect your threat intelligence platform and communities to automatically share the latest indicators with Microsoft. Use the Microsoft Graph Security API or leverage integrations with leading threat intelligence platforms, including Palo Alto Networks MineMeld and the open source MISP platform. Use with Azure Sentinel today to correlate threat intelligence with log data to alert on malicious activity. Refer to the tiIndicators schema.
- Take immediate action in response to new threat, such as block file, URL, domain, or IP address from within your security tools and workflows. When a security analyst discovers a new threat, protection can be instantly enabled in your Microsoft security solutions. Try it first with Windows Defender ATP (coming soon) to block malicious activity on your Windows endpoints using the properties seen in alerts or identified during investigations. Refer to the SecurityActions schema.
Security Automation
In a world of fast-moving, disruptive attacks and under-resourced security teams, automation of security workflows is essential. However, development of workflows to expedite alert routing, triage, investigation, and remediation can be challenging to create and maintain. We recently announced a set of Microsoft Graph Security API connectors to simplify development of automated security workflows without writing any code.
- Leverage Azure Logic Apps, Microsoft Flow, and PowerApps connectors to quickly build automation workflows using insights from the Microsoft Graph Security API. Mash up the Microsoft Graph Security API connector with over 200 other connectors to build workflows that act on security alerts, such as automatically routing high severity alerts to the on-call analyst – creating a ticket assigned to that user, sending an email or SMS notification, and collecting related alerts to speed their investigation See other example workflows.

Security Analytics + Reporting
The Microsoft Graph Security API now makes it easier than ever to analyze and visualize data across different security products running in your organization to get deeper security insights. Create reports and dashboards for visibility into active threats and trends. Discover opportunities to learn from the data and train your security models. The Microsoft Graph Security API schema provides multiple properties to pivot on to build rich reports and exploratory datasets using your security data.
- Use the PowerBI connector to create enterprise-wide security dashboards and reports. Get a complete picture of security alerts and secure score across your organization. Mash up security data with data from the other Power BI connectors, like Excel workbooks or other databases, for richer context. Use Power BI and Microsoft Flow to trigger an automated security workflow based on metrics, such as a percent decrease in your secure score. A sample dashboard and template help you get started. Learn more.

- Get deep insights to train security solutions by leveraging the power of Jupyter Notebooks for Microsoft Graph Security API. Use these Notebooks to build your visualizations and training data models with alert properties for users, files, hosts, processes, etc. across multiple security products. Learn more.
Integrated Partner Solutions
The Microsoft Graph Security API offers a wide range of possibilities for partners to build and enhance security solutions. We’ve been building an ecosystem of technology partners and are excited to announce the following new integrations:
- Barracuda Cloud Security Guardian accesses alerts and a secure score from the Microsoft Security Graph API and displays this on a single plane of glass.
- Bay Dynamics Risk Fabric integrates with the Microsoft Graph Security API to gain greater visibility into threats, enabling them to better prioritize remediation activities.
- Citrix Analytics leverages the Microsoft Graph Security API to correlate alerts from the Graph with Citrix products and take security actions. See video.
- DF Labs integrates with the Microsoft Graph Security API to enable its IncMan SOAR solution to orchestrate and automate response to threats from Graph Providers.
- FireEye Helix uses the Microsoft Graph Security API to integrate security insights from Microsoft and partners into its security operations platform.
- JASK uses the Microsoft Graph Security API to ingest data and information related to Microsoft users, applications, and events into its ASOC SIEM platform.
- Swimlane’s SOAR platform integrates with Microsoft Graph Security API to orchestrate and automate incident response across multiple solutions for faster threat response.
Find out more about partner integration opportunities here.
In addition to technology partners, we’re also working closely with a number of managed security services providers who are building solutions leveraging the Security API. Most recently, SWC Technology Partners announced new security solutions that help improve organizations’ security posture. In particular, SWC is using the Microsoft Graph Security API in its Managed Defense Service that helps identify suspicious behavior and allows organizations to quickly surface and remediate threats.
We know that our customers struggle with integrating their diverse security tools, workflows, and systems. The cost, time, and resources necessary to integrate systems, enable correlation of alerts, connect to existing workflows, and provide access to contextual data is extremely high. We’re excited about the potential the Microsoft Graph Security API offers to directly address these challenges.
Get started today
Join us at the Microsoft booth, N6059 in the north expo hall, at RSA Conference 2019 in San Francisco. You’ll get the chance to speak to experts and see how our partners are using the API.
To learn more and get started with using the Microsoft Graph Security API, check out the following resources:

Today, we are announcing new capabilities in the Microsoft Graph Security API to help our customers simplify integration, speed up response, and improve the effectiveness of their existing security investments. The latest updates include an expanded list of alert providers, new capabilities that enable threat intelligence sharing, streamline the creation of security automation workflows, and enable rich security analytics and reporting. Finally, we’re announcing several new integration partners.
Security Alerts
The Microsoft Graph Security API provides a unified interface and common schema to simplify integration of security alerts from Microsoft products, services, and partners. In addition to the many Microsoft and partner solutions previously available for the Microsoft Graph Security API, you can now access security alerts from Office 365 and Azure Advanced Threat Protection solutions as well as the new Microsoft Azure Sentinel service.
Developers can integrate alerts via a single endpoint, using one authentication key and one SDK. You can query for all alerts pertaining to specific users, devices, files, or command lines when investigating a specific threat or use webhook subscriptions to get notified when any new alert matching your search criteria is created or updated. Learn more about alerts.
Threat Intelligence (preview)
Threat indicators, also referred to as indicators of compromise or IoCs, represent data about known threats, such as malicious files, URLs, domains, and IP addresses. Microsoft amasses a huge volume of indicators each day using trillions of unique insights into cloud, users, and endpoints, which plays a huge role in how we protect Microsoft and our customers. You may also generate indicators through internal threat intelligence gathering or acquire indicators from threat intelligence communities, licensed feeds, and other sources. In addition to the vast threat intelligence built into Microsoft products and services, you can now also leverage your own indicators to enable custom detections in Microsoft solutions. Learn more.
- Connect your threat intelligence platform and communities to automatically share the latest indicators with Microsoft. Use the Microsoft Graph Security API or leverage integrations with leading threat intelligence platforms, including Palo Alto Networks MineMeld and the open source MISP platform. Use with Azure Sentinel today to correlate threat intelligence with log data to alert on malicious activity. Refer to the tiIndicators schema.
- Take immediate action in response to new threat, such as block file, URL, domain, or IP address from within your security tools and workflows. When a security analyst discovers a new threat, protection can be instantly enabled in your Microsoft security solutions. Try it first with Windows Defender ATP (coming soon) to block malicious activity on your Windows endpoints using the properties seen in alerts or identified during investigations. Refer to the SecurityActions schema.
Security Automation
In a world of fast-moving, disruptive attacks and under-resourced security teams, automation of security workflows is essential. However, development of workflows to expedite alert routing, triage, investigation, and remediation can be challenging to create and maintain. We recently announced a set of Microsoft Graph Security API connectors to simplify development of automated security workflows without writing any code.
- Leverage Azure Logic Apps, Microsoft Flow, and PowerApps connectors to quickly build automation workflows using insights from the Microsoft Graph Security API. Mash up the Microsoft Graph Security API connector with over 200 other connectors to build workflows that act on security alerts, such as automatically routing high severity alerts to the on-call analyst – creating a ticket assigned to that user, sending an email or SMS notification, and collecting related alerts to speed their investigation See other example workflows.

Security Analytics + Reporting
The Microsoft Graph Security API now makes it easier than ever to analyze and visualize data across different security products running in your organization to get deeper security insights. Create reports and dashboards for visibility into active threats and trends. Discover opportunities to learn from the data and train your security models. The Microsoft Graph Security API schema provides multiple properties to pivot on to build rich reports and exploratory datasets using your security data.
- Use the PowerBI connector to create enterprise-wide security dashboards and reports. Get a complete picture of security alerts and secure score across your organization. Mash up security data with data from the other Power BI connectors, like Excel workbooks or other databases, for richer context. Use Power BI and Microsoft Flow to trigger an automated security workflow based on metrics, such as a percent decrease in your secure score. A sample dashboard and template help you get started. Learn more.

- Get deep insights to train security solutions by leveraging the power of Jupyter Notebooks for Microsoft Graph Security API. Use these Notebooks to build your visualizations and training data models with alert properties for users, files, hosts, processes, etc. across multiple security products. Learn more.
Integrated Partner Solutions
The Microsoft Graph Security API offers a wide range of possibilities for partners to build and enhance security solutions. We’ve been building an ecosystem of technology partners and are excited to announce the following new integrations:
- Barracuda Cloud Security Guardian accesses alerts and a secure score from the Microsoft Security Graph API and displays this on a single plane of glass.
- Bay Dynamics Risk Fabric integrates with the Microsoft Graph Security API to gain greater visibility into threats, enabling them to better prioritize remediation activities.
- Citrix Analytics leverages the Microsoft Graph Security API to correlate alerts from the Graph with Citrix products and take security actions. See video.
- DF Labs integrates with the Microsoft Graph Security API to enable its IncMan SOAR solution to orchestrate and automate response to threats from Graph Providers.
- FireEye Helix uses the Microsoft Graph Security API to integrate security insights from Microsoft and partners into its security operations platform.
- JASK uses the Microsoft Graph Security API to ingest data and information related to Microsoft users, applications, and events into its ASOC SIEM platform.
- Swimlane’s SOAR platform integrates with Microsoft Graph Security API to orchestrate and automate incident response across multiple solutions for faster threat response.
Find out more about partner integration opportunities here.
In addition to technology partners, we’re also working closely with a number of managed security services providers who are building solutions leveraging the Security API. Most recently, SWC Technology Partners announced new security solutions that help improve organizations’ security posture. In particular, SWC is using the Microsoft Graph Security API in its Managed Defense Service that helps identify suspicious behavior and allows organizations to quickly surface and remediate threats.
We know that our customers struggle with integrating their diverse security tools, workflows, and systems. The cost, time, and resources necessary to integrate systems, enable correlation of alerts, connect to existing workflows, and provide access to contextual data is extremely high. We’re excited about the potential the Microsoft Graph Security API offers to directly address these challenges.
Get started today
Join us at the Microsoft booth, N6059 in the north expo hall, at RSA Conference 2019 in San Francisco. You’ll get the chance to speak to experts and see how our partners are using the API.
To learn more and get started with using the Microsoft Graph Security API, check out the following resources:

Today, we are announcing new capabilities in the Microsoft Graph Security API to help our customers simplify integration, speed up response, and improve the effectiveness of their existing security investments. The latest updates include an expanded list of alert providers, new capabilities that enable threat intelligence sharing, streamline the creation of security automation workflows, and enable rich security analytics and reporting. Finally, we’re announcing several new integration partners.
Security Alerts
The Microsoft Graph Security API provides a unified interface and common schema to simplify integration of security alerts from Microsoft products, services, and partners. In addition to the many Microsoft and partner solutions previously available for the Microsoft Graph Security API, you can now access security alerts from Office 365 and Azure Advanced Threat Protection solutions as well as the new Microsoft Azure Sentinel service.
Developers can integrate alerts via a single endpoint, using one authentication key and one SDK. You can query for all alerts pertaining to specific users, devices, files, or command lines when investigating a specific threat or use webhook subscriptions to get notified when any new alert matching your search criteria is created or updated. Learn more about alerts.
Threat Intelligence (preview)
Threat indicators, also referred to as indicators of compromise or IoCs, represent data about known threats, such as malicious files, URLs, domains, and IP addresses. Microsoft amasses a huge volume of indicators each day using trillions of unique insights into cloud, users, and endpoints, which plays a huge role in how we protect Microsoft and our customers. You may also generate indicators through internal threat intelligence gathering or acquire indicators from threat intelligence communities, licensed feeds, and other sources. In addition to the vast threat intelligence built into Microsoft products and services, you can now also leverage your own indicators to enable custom detections in Microsoft solutions. Learn more.
- Connect your threat intelligence platform and communities to automatically share the latest indicators with Microsoft. Use the Microsoft Graph Security API or leverage integrations with leading threat intelligence platforms, including Palo Alto Networks MineMeld and the open source MISP platform. Use with Azure Sentinel today to correlate threat intelligence with log data to alert on malicious activity. Refer to the tiIndicators schema.
- Take immediate action in response to new threat, such as block file, URL, domain, or IP address from within your security tools and workflows. When a security analyst discovers a new threat, protection can be instantly enabled in your Microsoft security solutions. Try it first with Windows Defender ATP (coming soon) to block malicious activity on your Windows endpoints using the properties seen in alerts or identified during investigations. Refer to the SecurityActions schema.
Security Automation
In a world of fast-moving, disruptive attacks and under-resourced security teams, automation of security workflows is essential. However, development of workflows to expedite alert routing, triage, investigation, and remediation can be challenging to create and maintain. We recently announced a set of Microsoft Graph Security API connectors to simplify development of automated security workflows without writing any code.
- Leverage Azure Logic Apps, Microsoft Flow, and PowerApps connectors to quickly build automation workflows using insights from the Microsoft Graph Security API. Mash up the Microsoft Graph Security API connector with over 200 other connectors to build workflows that act on security alerts, such as automatically routing high severity alerts to the on-call analyst – creating a ticket assigned to that user, sending an email or SMS notification, and collecting related alerts to speed their investigation See other example workflows.

Security Analytics + Reporting
The Microsoft Graph Security API now makes it easier than ever to analyze and visualize data across different security products running in your organization to get deeper security insights. Create reports and dashboards for visibility into active threats and trends. Discover opportunities to learn from the data and train your security models. The Microsoft Graph Security API schema provides multiple properties to pivot on to build rich reports and exploratory datasets using your security data.
- Use the PowerBI connector to create enterprise-wide security dashboards and reports. Get a complete picture of security alerts and secure score across your organization. Mash up security data with data from the other Power BI connectors, like Excel workbooks or other databases, for richer context. Use Power BI and Microsoft Flow to trigger an automated security workflow based on metrics, such as a percent decrease in your secure score. A sample dashboard and template help you get started. Learn more.

- Get deep insights to train security solutions by leveraging the power of Jupyter Notebooks for Microsoft Graph Security API. Use these Notebooks to build your visualizations and training data models with alert properties for users, files, hosts, processes, etc. across multiple security products. Learn more.
Integrated Partner Solutions
The Microsoft Graph Security API offers a wide range of possibilities for partners to build and enhance security solutions. We’ve been building an ecosystem of technology partners and are excited to announce the following new integrations:
- Barracuda Cloud Security Guardian accesses alerts and a secure score from the Microsoft Security Graph API and displays this on a single plane of glass.
- Bay Dynamics Risk Fabric integrates with the Microsoft Graph Security API to gain greater visibility into threats, enabling them to better prioritize remediation activities.
- Citrix Analytics leverages the Microsoft Graph Security API to correlate alerts from the Graph with Citrix products and take security actions. See video.
- DF Labs integrates with the Microsoft Graph Security API to enable its IncMan SOAR solution to orchestrate and automate response to threats from Graph Providers.
- FireEye Helix uses the Microsoft Graph Security API to integrate security insights from Microsoft and partners into its security operations platform.
- JASK uses the Microsoft Graph Security API to ingest data and information related to Microsoft users, applications, and events into its ASOC SIEM platform.
- Swimlane’s SOAR platform integrates with Microsoft Graph Security API to orchestrate and automate incident response across multiple solutions for faster threat response.
Find out more about partner integration opportunities here.
In addition to technology partners, we’re also working closely with a number of managed security services providers who are building solutions leveraging the Security API. Most recently, SWC Technology Partners announced new security solutions that help improve organizations’ security posture. In particular, SWC is using the Microsoft Graph Security API in its Managed Defense Service that helps identify suspicious behavior and allows organizations to quickly surface and remediate threats.
We know that our customers struggle with integrating their diverse security tools, workflows, and systems. The cost, time, and resources necessary to integrate systems, enable correlation of alerts, connect to existing workflows, and provide access to contextual data is extremely high. We’re excited about the potential the Microsoft Graph Security API offers to directly address these challenges.
Get started today
Join us at the Microsoft booth, N6059 in the north expo hall, at RSA Conference 2019 in San Francisco. You’ll get the chance to speak to experts and see how our partners are using the API.
To learn more and get started with using the Microsoft Graph Security API, check out the following resources:
Across Microsoft Information Protection solutions, our goal is to provide a comprehensive set of capabilities to help you protect your sensitive data throughout its entire lifecycle – across devices, apps, cloud services and on-premises. With the exponential growth of data and increasing data mobility, it’s critical to implement an information protection strategy that not only enables you to meet your internal security objectives, but also address new and emerging compliance and privacy requirements. We’ve recently released several new capabilities to help you discover, classify & label, protect and monitor your sensitive information – here’s a quick roundup of the latest news.
You can also check out this video to see some of the highlights in action:
A unified approach to data classification and label management
In order to effectively apply policy-based protection and controls to your sensitive data, you need to be able to inspect and reason over documents and emails. We provide a unified approach to data classification across our information protection and data governance solutions. There are over 90 out-of-the-box sensitive information types that you can use to detect common types of data, such as financial data, PII or health-care related information. You can also create and customize your sensitive information types (such as detecting employee ID numbers that are unique to your organization). Our classification engine is leveraged across services – including Azure Information Protection, Microsoft Cloud App Security, Advanced Data Governance and Office 365 Data Loss Prevention – enabling consistent classification outcomes for the purpose of applying labels, protecting information and enforcing data policies.
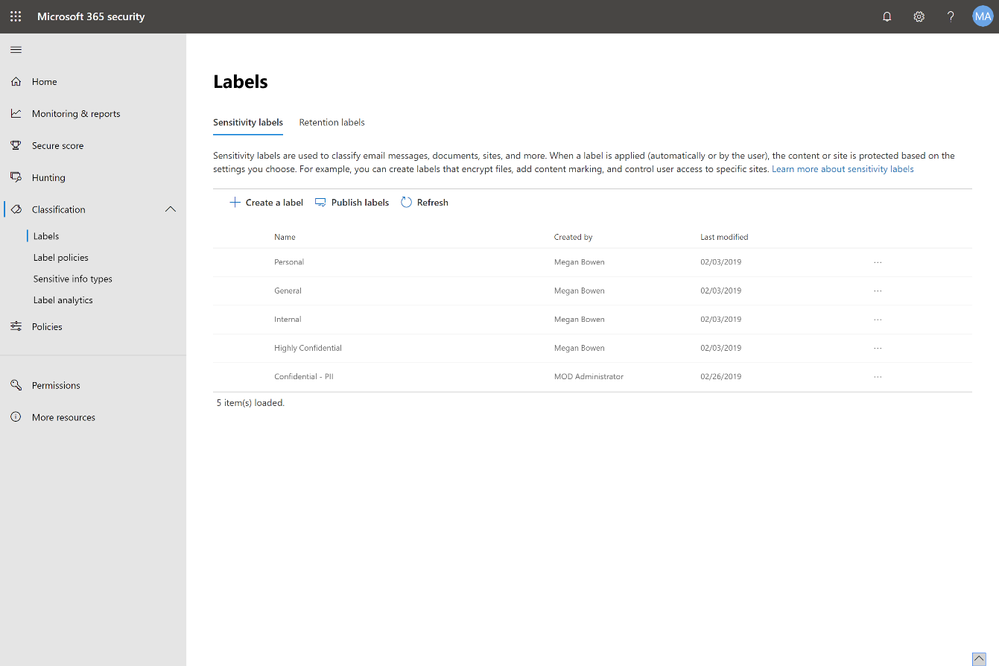
In addition to a consistent approach to data classification, we also provide a unified experience for configuring and managing labels – both sensitivity labels for the purpose of apply protection policies and retention labels for the purpose of applying data governance policies. In late 2018 we released a unified label management experience in the Office 365 Security & Compliance Center. Customers have been using this to create and configure their sensitivity labels and retention labels, set label policies and migrate existing labels from the Azure portal (for Azure Information Protection customers). The recently released Microsoft 365 security center and compliance center gives admins an enhanced experience and a dedicated workspace to manage Microsoft 365 security and compliance solutions, including sensitivity labels and retention labels.
 The new Microsoft 365 security center and compliance center (rolling out now) provides a centralized workspace to manage your Microsoft 365 security and compliance solutions, including management of your sensitivity labels and retention labels.
The new Microsoft 365 security center and compliance center (rolling out now) provides a centralized workspace to manage your Microsoft 365 security and compliance solutions, including management of your sensitivity labels and retention labels.
We’ve also recently announced two new retention capabilities, including the general availability of file plan manager, which helps you migrate complex retention hierarchies into Office 365, and a new assessment of Office 365’s ability to meet SEC 17a-4 requirements around immutability.
New sensitivity labeling capabilities built into Office apps – across platforms
We want to make it easy for end-users to apply sensitivity labels to their documents and emails – without interrupting their workflow or productivity. We recently announced the availability of end-user driven labeling capabilities built natively into Office apps on Mac, iOS and Android. This enables users to assign the appropriate sensitivity label while creating or editing documents and emails – such as “Highly Confidential” when the file contains company secrets. Based on the policies defined by your company, sensitivity labels can result in several actions, such as encryption, rights restrictions or adding visual markings stamped to the document. The experience is consistent and familiar across Office applications.
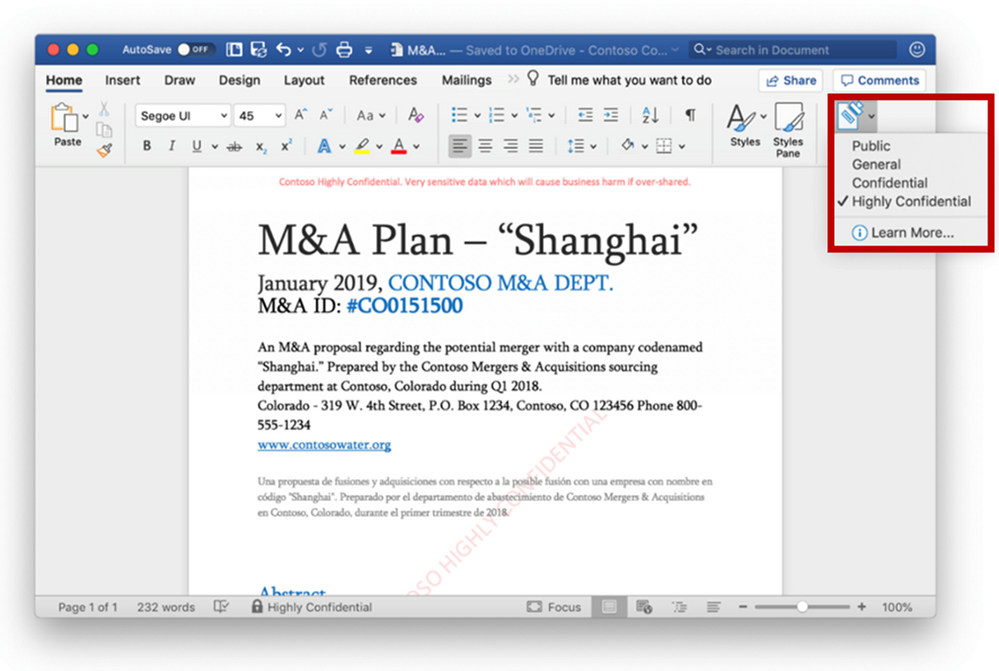 Apply sensitivity labels in Office apps on Mac – encryption, rights restrictions and visual markings can be applied, based on your label policy
Apply sensitivity labels in Office apps on Mac – encryption, rights restrictions and visual markings can be applied, based on your label policy
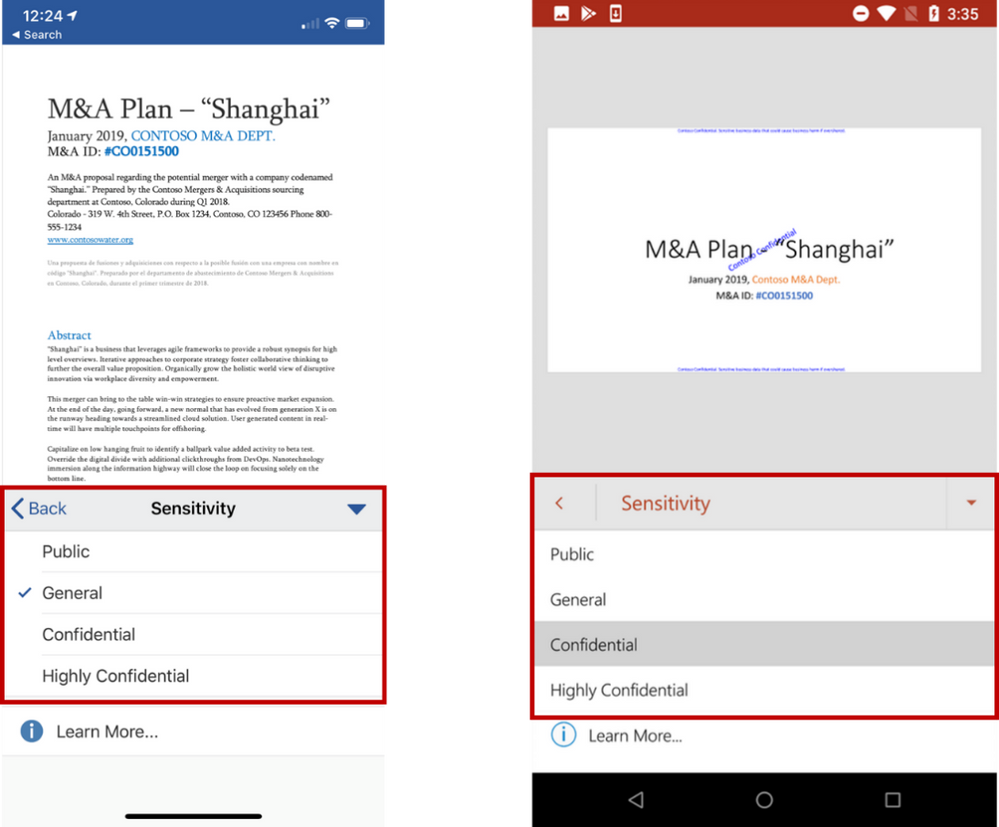 Easily apply the same sensitivity labels in Office mobile apps on iOS and Android
Easily apply the same sensitivity labels in Office mobile apps on iOS and Android
Learn more about the native labeling experience in our blog.
We’re also announcing an updated public preview of the Azure Information Protection client that supports unified labeling. The Azure Information Protection unified labeling client gets it sensitivity labels and policy settings from the Security & Compliance Center or the Microsoft 365 security center (as mentioned earlier). This is particularly useful for existing Azure Information Protection customers who want to evaluate and test the unified labeling and protection capabilities in Office apps on Windows (Word, PowerPoint, Excel and Outlook). The original public preview of the Azure Information Protection unified labeling client supported several features, such as end-user driven manual labeling, and the new updated public preview version now includes recommended labeling, automatic labeling and other customization options. Learn more about the supported features or read our product documentation.
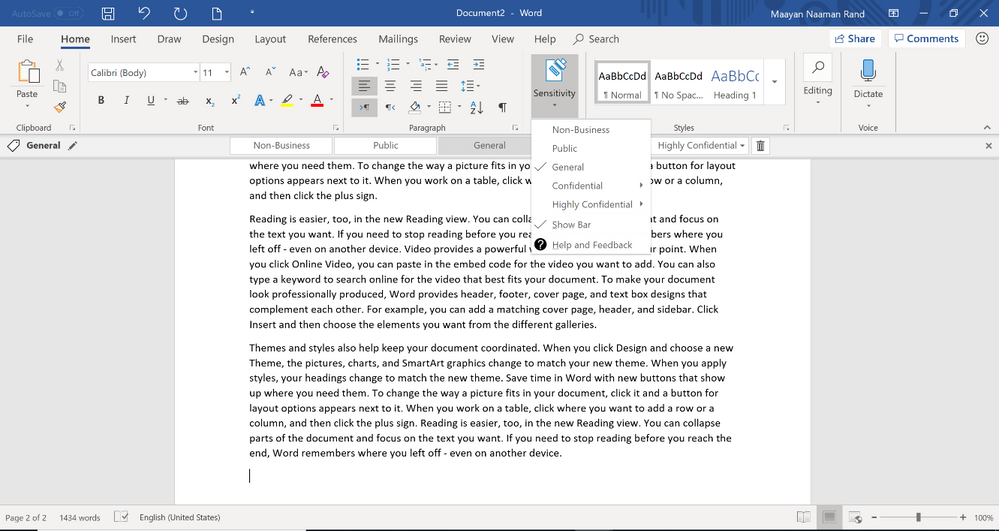 Apply sensitivity labels to Office apps on Windows using the Azure Information Protection unified labeling client (in preview)
Apply sensitivity labels to Office apps on Windows using the Azure Information Protection unified labeling client (in preview)
Enhanced data discovery and protection across your on-premises repositories
The Azure Information Protection scanner is used by customers all over the world to discover, classify, label and protect sensitive information that resides in their on-premises file servers. Based on customer feedback to provide additional capabilities to make it easier and more efficient to deploy and manage the Azure Information Protection scanner at scale, we recently released a new management and operational UI.
The management UI (currently in public preview) helps you manage scanner configuration and scanned repositories – all in one central place within the Azure portal. You can configure sensitive information types that you want to discover, set file types to be scanned, set default label settings along with other configuration options.
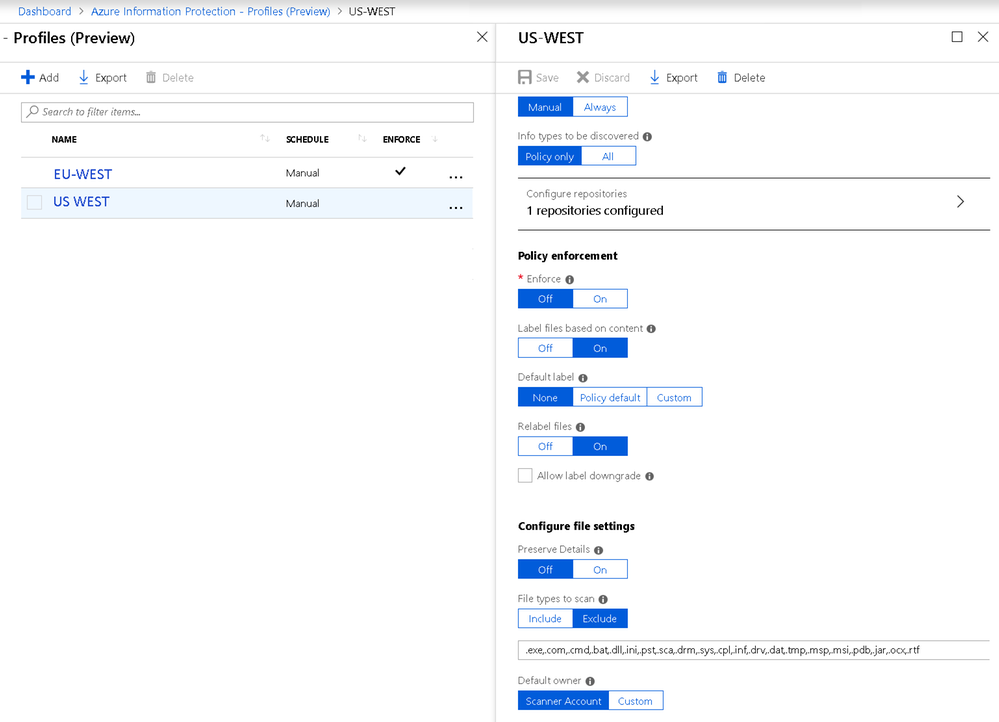 Azure Information Protection scanner profiles management page enables admins to set scanner configuration options
Azure Information Protection scanner profiles management page enables admins to set scanner configuration options
We also recently announced the general availability of a new operational UI which makes it easier to stay on top of Azure Information Protection scanner operations, such as monitoring the status of all scanner nodes, get the latest scanning statistics, initiate on-demand incremental scans or run full rescans. Learn more about the latest Azure Information Protection scanner UI experience in our blog or review the product documentation.
New classification methods to automatically detect sensitive credential information in documents
While we provide over 90 out-of-the-box sensitive information types that you can use to detect common types of data, a frequent customer request has been the ability to automatically detect passwords and other credential types that users have recorded or pasted in unprotected files. For example, sometimes users and admins use Word or Excel to store a list of usernames and passwords they use for applications and services. We’re announcing the public preview of the first group of credential types that we can automatically detect – focusing on Azure secrets and SQL credentials. These new sensitive information types are coming first to Azure Information Protection and will be coming soon to Office 365. Similar to other sensitive information types, you can configure your policy to recommend a sensitivity label to the user or automatically apply a label and protection settings. Read more about the credential types supported in our blog.
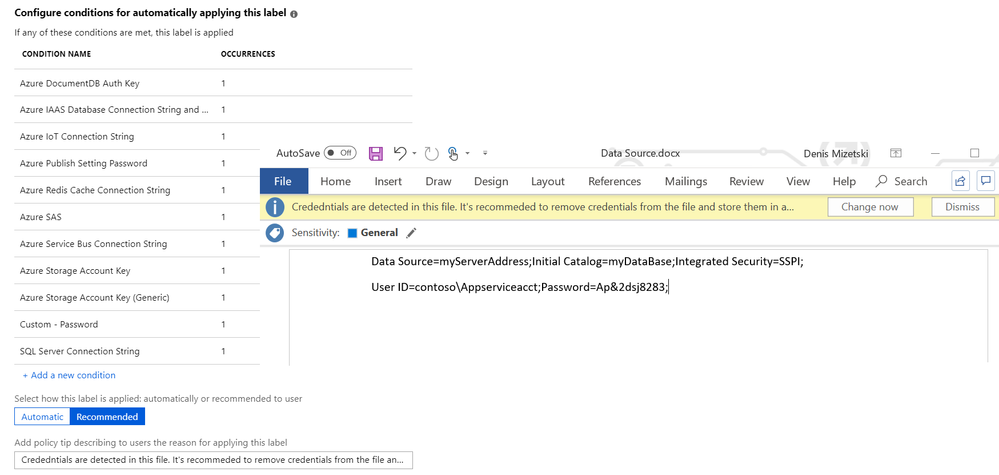 Credential information in a document is automatically detected; sensitivity label is recommended or automatically applied
Credential information in a document is automatically detected; sensitivity label is recommended or automatically applied
Deeper visibility into the sensitive data landscape across your organization
The information protection lifecycle wouldn’t be complete without the ability to understand your sensitive data landscape. Within the new Microsoft 365 security center (and compliance center), the new Label analytics page (currently in preview), provides the starting point for you to better understand label usage across your organization. You can quickly see the overall activity of sensitivity labeling during the past 30 days, the distribution of labels used (such as how many “Highly Confidential” labels were applied), along with the location where labels were applied (such as Word, Excel, PowerPoint, File Explorer).
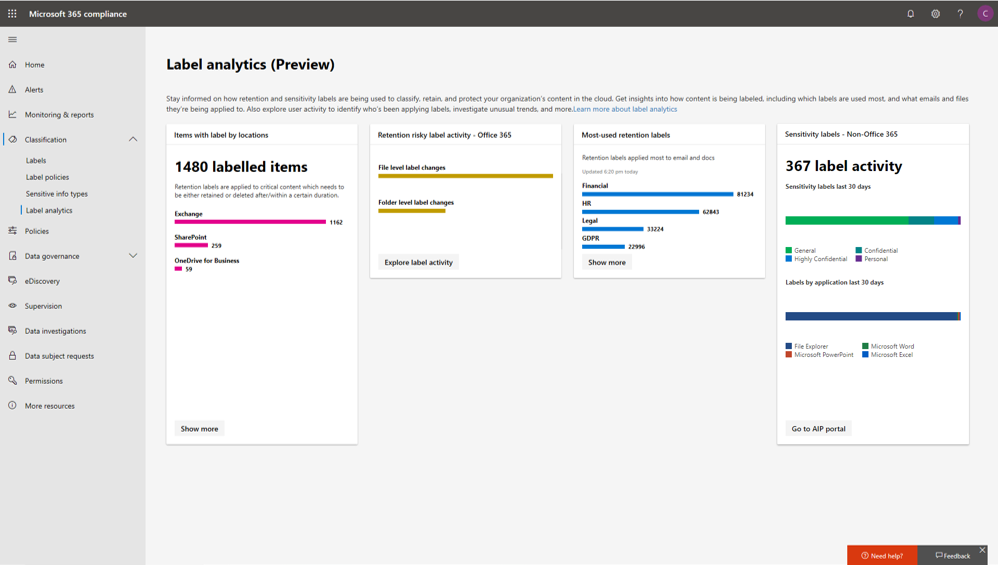 Label analytics (preview) in the Microsoft 365 compliance center gives you an overview of labeled documents and emails – for both retention labels and sensitivity labels
Label analytics (preview) in the Microsoft 365 compliance center gives you an overview of labeled documents and emails – for both retention labels and sensitivity labels
For a deeper view into sensitivity label activity, you can go the Azure Information Protection portal. In late 2018 we announced the public preview of Azure Information Protection analytics, which gives you insights into classified, labeled and protected documents across your organization. There have been several updates to the preview experience over the past couple of months. Information from Windows computers running Windows Defender ATP is now included. Additional activity information is also included, such as which users have accessed a specific labeled document and whether a document label has been upgraded or downgraded by a user. You can learn more in the product documentation. We are targeting general availability in early Q2 CY19, so stay tuned.
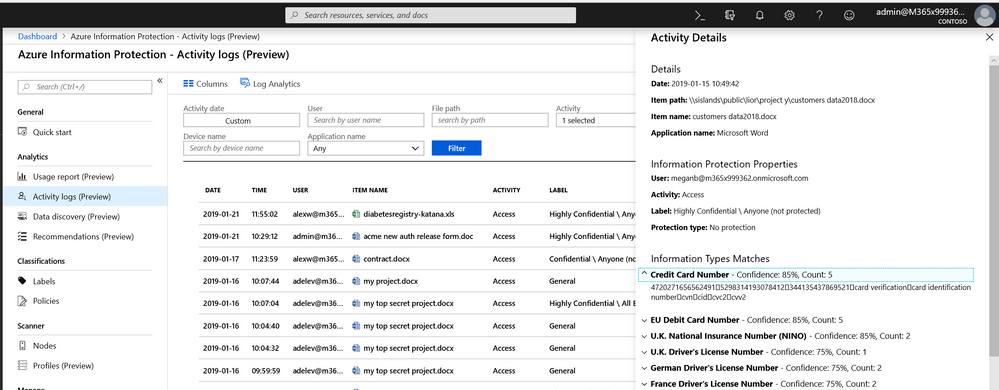
Extend visibility into sensitive information in Windows endpoints
While more and more data lives in cloud services, a significant amount of important data also resides on end-users’ devices. Endpoints represent a key control point for your information protection strategy – especially since devices are often the entry point for sophisticated attacks and data breaches. Windows Defender Advanced Threat Protection (Windows Defender ATP), Microsoft’s endpoint protection platform, can now understand Microsoft Information Protection sensitivity labels – providing visibility into sensitive data on endpoints, protect data based on its content and help you respond to post-breach malicious activity that involves sensitive data.
This integration enables Azure Information Protection analytics to show information on labeled data on Windows devices (as reported by Windows Defender ATP). This help gives admins better visibility into sensitive information residing on a given endpoint and investigates and mitigate security threats on potentially compromised machines.
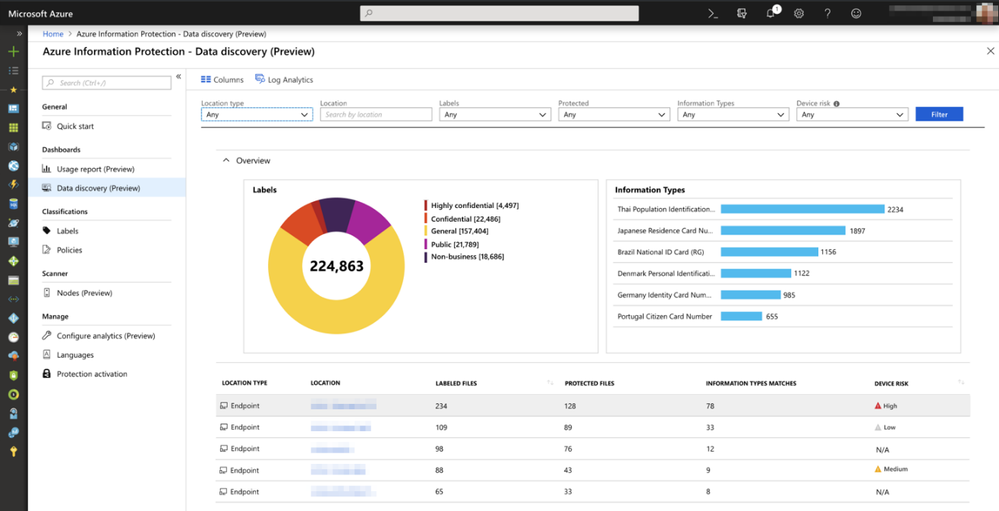 The Azure Information Protection Data discovery dashboard shows labeled files discovered on endpoints by Windows Defender ATP; along with a device risk calculation to help direct further investigation
The Azure Information Protection Data discovery dashboard shows labeled files discovered on endpoints by Windows Defender ATP; along with a device risk calculation to help direct further investigation
Learn more about the latest integration between Windows Defender ATP and Microsoft Information Protection in our blog.
Partners are extending Microsoft Information Protection experiences to their own apps and services
At the RSA Conference in 2018 we announced the public preview of the Microsoft Information Protection SDK, which became generally available in September 2018. Since then, we’ve made several updates, and our partners are developing a diverse set of integrations – ranging from endpoint DLP solutions, classifying and labeling, to reporting on data that has been labeled and protected. With the Microsoft Information Protection SDK, we now have a comprehensive cross-platform SDK that covers Windows, Linux, macOS, iOS and Android. More details on partner integrations are available here. Download the Microsoft Information SDK and get started!
Getting started and looking ahead
We encourage you to start evaluating and deploying these new capabilities. Start using the unified labeling experience to configure and deploy your sensitivity labels. Use the native labeling experience in the Office apps on Mac, iOS and Android to empower users to label and protect their documents and emails. Enable Windows users to do the same by using the Azure Information Protection unified labeling client (preview). Configure Windows Information Protection and Windows Defender ATP to help protect sensitive data on Windows endpoints. Gain visibility into sensitive data across your environment using the Label analytics preview in the Microsoft 365 security center and go deeper with Azure Information Protection analytics.
You can also engage with us and the community on Yammer or Twitter and provide additional feedback on UserVoice.

Across Microsoft Information Protection solutions, our goal is to provide a comprehensive set of capabilities to help you protect your sensitive data throughout its entire lifecycle – across devices, apps, cloud services and on-premises. With the exponential growth of data and increasing data mobility, it’s critical to implement an information protection strategy that not only enables you to meet your internal security objectives, but also address new and emerging compliance and privacy requirements. We’ve recently released several new capabilities to help you discover, classify & label, protect and monitor your sensitive information – here’s a quick roundup of the latest news.
You can also check out this video to see some of the highlights in action:
A unified approach to data classification and label management
In order to effectively apply policy-based protection and controls to your sensitive data, you need to be able to inspect and reason over documents and emails. We provide a unified approach to data classification across our information protection and data governance solutions. There are over 90 out-of-the-box sensitive information types that you can use to detect common types of data, such as financial data, PII or health-care related information. You can also create and customize your sensitive information types (such as detecting employee ID numbers that are unique to your organization). Our classification engine is leveraged across services – including Azure Information Protection, Microsoft Cloud App Security, Advanced Data Governance and Office 365 Data Loss Prevention – enabling consistent classification outcomes for the purpose of applying labels, protecting information and enforcing data policies.
In addition to a consistent approach to data classification, we also provide a unified experience for configuring and managing labels – both sensitivity labels for the purpose of apply protection policies and retention labels for the purpose of applying data governance policies. In late 2018 we released a unified label management experience in the Office 365 Security & Compliance Center. Customers have been using this to create and configure their sensitivity labels and retention labels, set label policies and migrate existing labels from the Azure portal (for Azure Information Protection customers). The recently released Microsoft 365 security center and compliance center gives admins an enhanced experience and a dedicated workspace to manage Microsoft 365 security and compliance solutions, including sensitivity labels and retention labels.
 The new Microsoft 365 security center and compliance center (rolling out now) provides a centralized workspace to manage your Microsoft 365 security and compliance solutions, including management of your sensitivity labels and retention labels.
The new Microsoft 365 security center and compliance center (rolling out now) provides a centralized workspace to manage your Microsoft 365 security and compliance solutions, including management of your sensitivity labels and retention labels.
We’ve also recently announced two new retention capabilities, including the general availability of file plan manager, which helps you migrate complex retention hierarchies into Office 365, and a new assessment of Office 365’s ability to meet SEC 17a-4 requirements around immutability.
New sensitivity labeling capabilities built into Office apps – across platforms
We want to make it easy for end-users to apply sensitivity labels to their documents and emails – without interrupting their workflow or productivity. We recently announced the availability of end-user driven labeling capabilities built natively into Office apps on Mac, iOS and Android. This enables users to assign the appropriate sensitivity label while creating or editing documents and emails – such as “Highly Confidential” when the file contains company secrets. Based on the policies defined by your company, sensitivity labels can result in several actions, such as encryption, rights restrictions or adding visual markings stamped to the document. The experience is consistent and familiar across Office applications.
 Apply sensitivity labels in Office apps on Mac – encryption, rights restrictions and visual markings can be applied, based on your label policy
Apply sensitivity labels in Office apps on Mac – encryption, rights restrictions and visual markings can be applied, based on your label policy
 Easily apply the same sensitivity labels in Office mobile apps on iOS and Android
Easily apply the same sensitivity labels in Office mobile apps on iOS and Android
Learn more about the native labeling experience in our blog.
We’re also announcing an updated public preview of the Azure Information Protection client that supports unified labeling. The Azure Information Protection unified labeling client gets it sensitivity labels and policy settings from the Security & Compliance Center or the Microsoft 365 security center (as mentioned earlier). This is particularly useful for existing Azure Information Protection customers who want to evaluate and test the unified labeling and protection capabilities in Office apps on Windows (Word, PowerPoint, Excel and Outlook). The original public preview of the Azure Information Protection unified labeling client supported several features, such as end-user driven manual labeling, and the new updated public preview version now includes recommended labeling, automatic labeling and other customization options. Learn more about the supported features or read our product documentation.
 Apply sensitivity labels to Office apps on Windows using the Azure Information Protection unified labeling client (in preview)
Apply sensitivity labels to Office apps on Windows using the Azure Information Protection unified labeling client (in preview)
Enhanced data discovery and protection across your on-premises repositories
The Azure Information Protection scanner is used by customers all over the world to discover, classify, label and protect sensitive information that resides in their on-premises file servers. Based on customer feedback to provide additional capabilities to make it easier and more efficient to deploy and manage the Azure Information Protection scanner at scale, we recently released a new management and operational UI.
The management UI (currently in public preview) helps you manage scanner configuration and scanned repositories – all in one central place within the Azure portal. You can configure sensitive information types that you want to discover, set file types to be scanned, set default label settings along with other configuration options.
 Azure Information Protection scanner profiles management page enables admins to set scanner configuration options
Azure Information Protection scanner profiles management page enables admins to set scanner configuration options
We also recently announced the general availability of a new operational UI which makes it easier to stay on top of Azure Information Protection scanner operations, such as monitoring the status of all scanner nodes, get the latest scanning statistics, initiate on-demand incremental scans or run full rescans. Learn more about the latest Azure Information Protection scanner UI experience in our blog or review the product documentation.
New classification methods to automatically detect sensitive credential information in documents
While we provide over 90 out-of-the-box sensitive information types that you can use to detect common types of data, a frequent customer request has been the ability to automatically detect passwords and other credential types that users have recorded or pasted in unprotected files. For example, sometimes users and admins use Word or Excel to store a list of usernames and passwords they use for applications and services. We’re announcing the public preview of the first group of credential types that we can automatically detect – focusing on Azure secrets and SQL credentials. These new sensitive information types are coming first to Azure Information Protection and will be coming soon to Office 365. Similar to other sensitive information types, you can configure your policy to recommend a sensitivity label to the user or automatically apply a label and protection settings. Read more about the credential types supported in our blog.
 Credential information in a document is automatically detected; sensitivity label is recommended or automatically applied
Credential information in a document is automatically detected; sensitivity label is recommended or automatically applied
Deeper visibility into the sensitive data landscape across your organization
The information protection lifecycle wouldn’t be complete without the ability to understand your sensitive data landscape. Within the new Microsoft 365 security center (and compliance center), the new Label analytics page (currently in preview), provides the starting point for you to better understand label usage across your organization. You can quickly see the overall activity of sensitivity labeling during the past 30 days, the distribution of labels used (such as how many “Highly Confidential” labels were applied), along with the location where labels were applied (such as Word, Excel, PowerPoint, File Explorer).
 Label analytics (preview) in the Microsoft 365 compliance center gives you an overview of labeled documents and emails – for both retention labels and sensitivity labels
Label analytics (preview) in the Microsoft 365 compliance center gives you an overview of labeled documents and emails – for both retention labels and sensitivity labels
For a deeper view into sensitivity label activity, you can go the Azure Information Protection portal. In late 2018 we announced the public preview of Azure Information Protection analytics, which gives you insights into classified, labeled and protected documents across your organization. There have been several updates to the preview experience over the past couple of months. Information from Windows computers running Windows Defender ATP is now included. Additional activity information is also included, such as which users have accessed a specific labeled document and whether a document label has been upgraded or downgraded by a user. You can learn more in the product documentation. We are targeting general availability in early Q2 CY19, so stay tuned.

Extend visibility into sensitive information in Windows endpoints
While more and more data lives in cloud services, a significant amount of important data also resides on end-users’ devices. Endpoints represent a key control point for your information protection strategy – especially since devices are often the entry point for sophisticated attacks and data breaches. Windows Defender Advanced Threat Protection (Windows Defender ATP), Microsoft’s endpoint protection platform, can now understand Microsoft Information Protection sensitivity labels – providing visibility into sensitive data on endpoints, protect data based on its content and help you respond to post-breach malicious activity that involves sensitive data.
This integration enables Azure Information Protection analytics to show information on labeled data on Windows devices (as reported by Windows Defender ATP). This help gives admins better visibility into sensitive information residing on a given endpoint and investigates and mitigate security threats on potentially compromised machines.
 The Azure Information Protection Data discovery dashboard shows labeled files discovered on endpoints by Windows Defender ATP; along with a device risk calculation to help direct further investigation
The Azure Information Protection Data discovery dashboard shows labeled files discovered on endpoints by Windows Defender ATP; along with a device risk calculation to help direct further investigation
Learn more about the latest integration between Windows Defender ATP and Microsoft Information Protection in our blog.
Partners are extending Microsoft Information Protection experiences to their own apps and services
At the RSA Conference in 2018 we announced the public preview of the Microsoft Information Protection SDK, which became generally available in September 2018. Since then, we’ve made several updates, and our partners are developing a diverse set of integrations – ranging from endpoint DLP solutions, classifying and labeling, to reporting on data that has been labeled and protected. With the Microsoft Information Protection SDK, we now have a comprehensive cross-platform SDK that covers Windows, Linux, macOS, iOS and Android. More details on partner integrations are available here. Download the Microsoft Information SDK and get started!
Getting started and looking ahead
We encourage you to start evaluating and deploying these new capabilities. Start using the unified labeling experience to configure and deploy your sensitivity labels. Use the native labeling experience in the Office apps on Mac, iOS and Android to empower users to label and protect their documents and emails. Enable Windows users to do the same by using the Azure Information Protection unified labeling client (preview). Configure Windows Information Protection and Windows Defender ATP to help protect sensitive data on Windows endpoints. Gain visibility into sensitive data across your environment using the Label analytics preview in the Microsoft 365 security center and go deeper with Azure Information Protection analytics.
You can also engage with us and the community on Yammer or Twitter and provide additional feedback on UserVoice.

Across Microsoft Information Protection solutions, our goal is to provide a comprehensive set of capabilities to help you protect your sensitive data throughout its entire lifecycle – across devices, apps, cloud services and on-premises. With the exponential growth of data and increasing data mobility, it’s critical to implement an information protection strategy that not only enables you to meet your internal security objectives, but also address new and emerging compliance and privacy requirements. We’ve recently released several new capabilities to help you discover, classify & label, protect and monitor your sensitive information – here’s a quick roundup of the latest news.
You can also check out this video to see some of the highlights in action:
A unified approach to data classification and label management
In order to effectively apply policy-based protection and controls to your sensitive data, you need to be able to inspect and reason over documents and emails. We provide a unified approach to data classification across our information protection and data governance solutions. There are over 90 out-of-the-box sensitive information types that you can use to detect common types of data, such as financial data, PII or health-care related information. You can also create and customize your sensitive information types (such as detecting employee ID numbers that are unique to your organization). Our classification engine is leveraged across services – including Azure Information Protection, Microsoft Cloud App Security, Advanced Data Governance and Office 365 Data Loss Prevention – enabling consistent classification outcomes for the purpose of applying labels, protecting information and enforcing data policies.
In addition to a consistent approach to data classification, we also provide a unified experience for configuring and managing labels – both sensitivity labels for the purpose of apply protection policies and retention labels for the purpose of applying data governance policies. In late 2018 we released a unified label management experience in the Office 365 Security & Compliance Center. Customers have been using this to create and configure their sensitivity labels and retention labels, set label policies and migrate existing labels from the Azure portal (for Azure Information Protection customers). The recently released Microsoft 365 security center and compliance center gives admins an enhanced experience and a dedicated workspace to manage Microsoft 365 security and compliance solutions, including sensitivity labels and retention labels.
 The new Microsoft 365 security center and compliance center (rolling out now) provides a centralized workspace to manage your Microsoft 365 security and compliance solutions, including management of your sensitivity labels and retention labels.
The new Microsoft 365 security center and compliance center (rolling out now) provides a centralized workspace to manage your Microsoft 365 security and compliance solutions, including management of your sensitivity labels and retention labels.
We’ve also recently announced two new retention capabilities, including the general availability of file plan manager, which helps you migrate complex retention hierarchies into Office 365, and a new assessment of Office 365’s ability to meet SEC 17a-4 requirements around immutability.
New sensitivity labeling capabilities built into Office apps – across platforms
We want to make it easy for end-users to apply sensitivity labels to their documents and emails – without interrupting their workflow or productivity. We recently announced the availability of end-user driven labeling capabilities built natively into Office apps on Mac, iOS and Android. This enables users to assign the appropriate sensitivity label while creating or editing documents and emails – such as “Highly Confidential” when the file contains company secrets. Based on the policies defined by your company, sensitivity labels can result in several actions, such as encryption, rights restrictions or adding visual markings stamped to the document. The experience is consistent and familiar across Office applications.
 Apply sensitivity labels in Office apps on Mac – encryption, rights restrictions and visual markings can be applied, based on your label policy
Apply sensitivity labels in Office apps on Mac – encryption, rights restrictions and visual markings can be applied, based on your label policy
 Easily apply the same sensitivity labels in Office mobile apps on iOS and Android
Easily apply the same sensitivity labels in Office mobile apps on iOS and Android
Learn more about the native labeling experience in our blog.
We’re also announcing an updated public preview of the Azure Information Protection client that supports unified labeling. The Azure Information Protection unified labeling client gets it sensitivity labels and policy settings from the Security & Compliance Center or the Microsoft 365 security center (as mentioned earlier). This is particularly useful for existing Azure Information Protection customers who want to evaluate and test the unified labeling and protection capabilities in Office apps on Windows (Word, PowerPoint, Excel and Outlook). The original public preview of the Azure Information Protection unified labeling client supported several features, such as end-user driven manual labeling, and the new updated public preview version now includes recommended labeling, automatic labeling and other customization options. Learn more about the supported features or read our product documentation.
 Apply sensitivity labels to Office apps on Windows using the Azure Information Protection unified labeling client (in preview)
Apply sensitivity labels to Office apps on Windows using the Azure Information Protection unified labeling client (in preview)
Enhanced data discovery and protection across your on-premises repositories
The Azure Information Protection scanner is used by customers all over the world to discover, classify, label and protect sensitive information that resides in their on-premises file servers. Based on customer feedback to provide additional capabilities to make it easier and more efficient to deploy and manage the Azure Information Protection scanner at scale, we recently released a new management and operational UI.
The management UI (currently in public preview) helps you manage scanner configuration and scanned repositories – all in one central place within the Azure portal. You can configure sensitive information types that you want to discover, set file types to be scanned, set default label settings along with other configuration options.
 Azure Information Protection scanner profiles management page enables admins to set scanner configuration options
Azure Information Protection scanner profiles management page enables admins to set scanner configuration options
We also recently announced the general availability of a new operational UI which makes it easier to stay on top of Azure Information Protection scanner operations, such as monitoring the status of all scanner nodes, get the latest scanning statistics, initiate on-demand incremental scans or run full rescans. Learn more about the latest Azure Information Protection scanner UI experience in our blog or review the product documentation.
New classification methods to automatically detect sensitive credential information in documents
While we provide over 90 out-of-the-box sensitive information types that you can use to detect common types of data, a frequent customer request has been the ability to automatically detect passwords and other credential types that users have recorded or pasted in unprotected files. For example, sometimes users and admins use Word or Excel to store a list of usernames and passwords they use for applications and services. We’re announcing the public preview of the first group of credential types that we can automatically detect – focusing on Azure secrets and SQL credentials. These new sensitive information types are coming first to Azure Information Protection and will be coming soon to Office 365. Similar to other sensitive information types, you can configure your policy to recommend a sensitivity label to the user or automatically apply a label and protection settings. Read more about the credential types supported in our blog.
 Credential information in a document is automatically detected; sensitivity label is recommended or automatically applied
Credential information in a document is automatically detected; sensitivity label is recommended or automatically applied
Deeper visibility into the sensitive data landscape across your organization
The information protection lifecycle wouldn’t be complete without the ability to understand your sensitive data landscape. Within the new Microsoft 365 security center (and compliance center), the new Label analytics page (currently in preview), provides the starting point for you to better understand label usage across your organization. You can quickly see the overall activity of sensitivity labeling during the past 30 days, the distribution of labels used (such as how many “Highly Confidential” labels were applied), along with the location where labels were applied (such as Word, Excel, PowerPoint, File Explorer).
 Label analytics (preview) in the Microsoft 365 compliance center gives you an overview of labeled documents and emails – for both retention labels and sensitivity labels
Label analytics (preview) in the Microsoft 365 compliance center gives you an overview of labeled documents and emails – for both retention labels and sensitivity labels
For a deeper view into sensitivity label activity, you can go the Azure Information Protection portal. In late 2018 we announced the public preview of Azure Information Protection analytics, which gives you insights into classified, labeled and protected documents across your organization. There have been several updates to the preview experience over the past couple of months. Information from Windows computers running Windows Defender ATP is now included. Additional activity information is also included, such as which users have accessed a specific labeled document and whether a document label has been upgraded or downgraded by a user. You can learn more in the product documentation. We are targeting general availability in early Q2 CY19, so stay tuned.

Extend visibility into sensitive information in Windows endpoints
While more and more data lives in cloud services, a significant amount of important data also resides on end-users’ devices. Endpoints represent a key control point for your information protection strategy – especially since devices are often the entry point for sophisticated attacks and data breaches. Windows Defender Advanced Threat Protection (Windows Defender ATP), Microsoft’s endpoint protection platform, can now understand Microsoft Information Protection sensitivity labels – providing visibility into sensitive data on endpoints, protect data based on its content and help you respond to post-breach malicious activity that involves sensitive data.
This integration enables Azure Information Protection analytics to show information on labeled data on Windows devices (as reported by Windows Defender ATP). This help gives admins better visibility into sensitive information residing on a given endpoint and investigates and mitigate security threats on potentially compromised machines.
 The Azure Information Protection Data discovery dashboard shows labeled files discovered on endpoints by Windows Defender ATP; along with a device risk calculation to help direct further investigation
The Azure Information Protection Data discovery dashboard shows labeled files discovered on endpoints by Windows Defender ATP; along with a device risk calculation to help direct further investigation
Learn more about the latest integration between Windows Defender ATP and Microsoft Information Protection in our blog.
Partners are extending Microsoft Information Protection experiences to their own apps and services
At the RSA Conference in 2018 we announced the public preview of the Microsoft Information Protection SDK, which became generally available in September 2018. Since then, we’ve made several updates, and our partners are developing a diverse set of integrations – ranging from endpoint DLP solutions, classifying and labeling, to reporting on data that has been labeled and protected. With the Microsoft Information Protection SDK, we now have a comprehensive cross-platform SDK that covers Windows, Linux, macOS, iOS and Android. More details on partner integrations are available here. Download the Microsoft Information SDK and get started!
Getting started and looking ahead
We encourage you to start evaluating and deploying these new capabilities. Start using the unified labeling experience to configure and deploy your sensitivity labels. Use the native labeling experience in the Office apps on Mac, iOS and Android to empower users to label and protect their documents and emails. Enable Windows users to do the same by using the Azure Information Protection unified labeling client (preview). Configure Windows Information Protection and Windows Defender ATP to help protect sensitive data on Windows endpoints. Gain visibility into sensitive data across your environment using the Label analytics preview in the Microsoft 365 security center and go deeper with Azure Information Protection analytics.
You can also engage with us and the community on Yammer or Twitter and provide additional feedback on UserVoice.
























