The new Label Activity Explorer helps you easily validate how data has been labeled and investigate risky or abnormal label activity in your organization. As data grows in your organization, so does the need to classify and govern it to ensure business continuity and readiness for regulations such as the GDPR. To help meet these goals, you can create Office 365 labels and either publish them to users’ apps (so they can manually classify their own content) or automatically apply them to content containing sensitive information.
Data Governance dashboard refresh
In addition to the Label Activity Explorer, we have also refreshed the Data Governance dashboard to include new features, such as the Data Governance toolbox and label insights widgets. Let’s take a closer look.
Data Governance toolbox
The new Data Governance toolbox is your one-stop-shop for guidance and links to common data governance tasks. These tools can help you manage the full content lifecycle, including how to:
- Import data into Office 365 and increase email storage so you can use Office 365 features to govern it
- Manage how data is classified, retained, accessed, and disposed of
- Track label usage, monitor alerts, and respond to disposition reviews
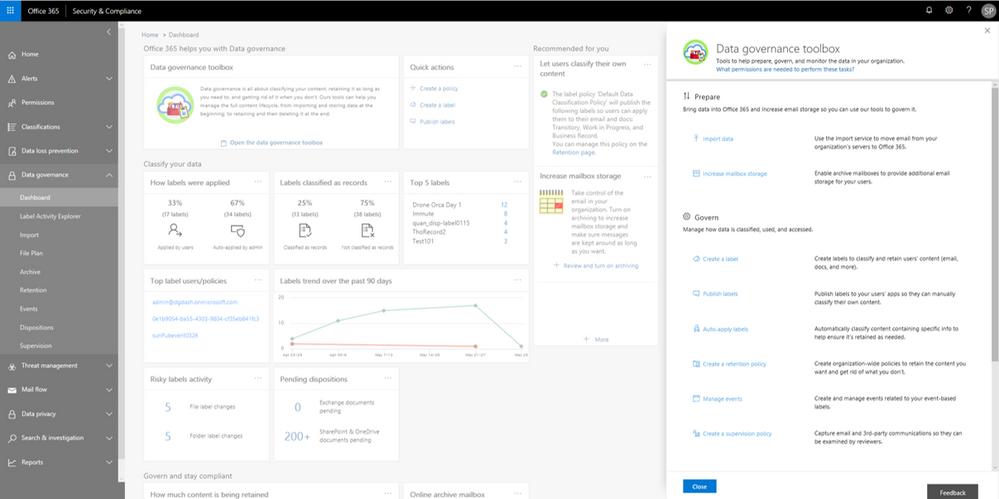
 Data Governance toolbox provides guidance on getting started with Data Governance in Office 365.
Data Governance toolbox provides guidance on getting started with Data Governance in Office 365.
Label insights widgets and supporting reports
Label insights widgets provide you with a quick view into the classification of data in your organization, including how labels were applied, labels that have been classified as records, top labels, top users of labels, label trends, and risky label activities. Click on the label insights widgets to open a more detailed report so you can drill down further.
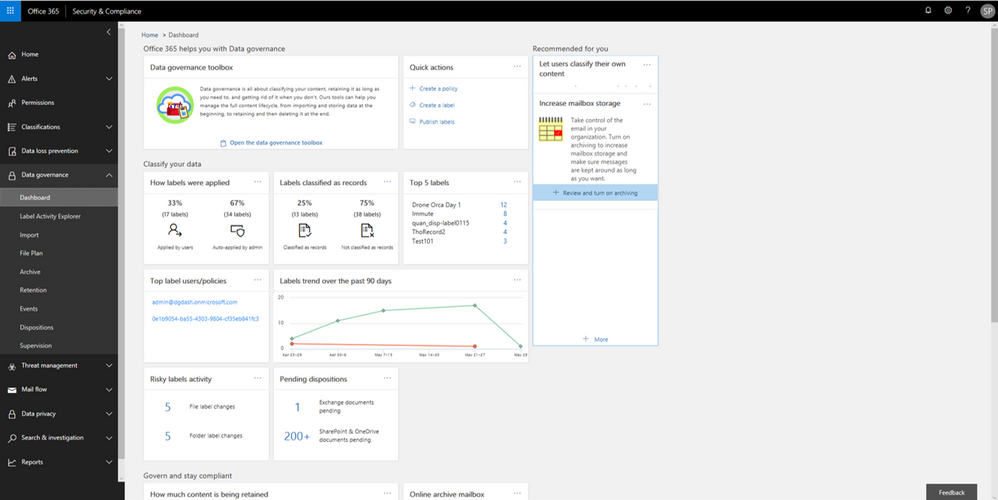 Labels insights widgets provide information about labels usage in your organization.
Labels insights widgets provide information about labels usage in your organization.
Label Activity Explorer
The Label Activity Explorer that was previewed in April is now generally available. This new experience provides real-time data that lets you investigate risky label activity and verify that labels are being applied to content as you intended. Use this information to increase confidence that your sensitive data has been detected, classified, and retained according to your organization’s policies.
Filter on labels applied at either the file or folder level to learn more about activities and changes. Once you find the label and file or folder of interest, you can investigate further by reviewing details such as the user who applied the label, file name, and parent site. If you have the right permissions, you can even access the in-place content directly. Learn more about the label activity explorer.
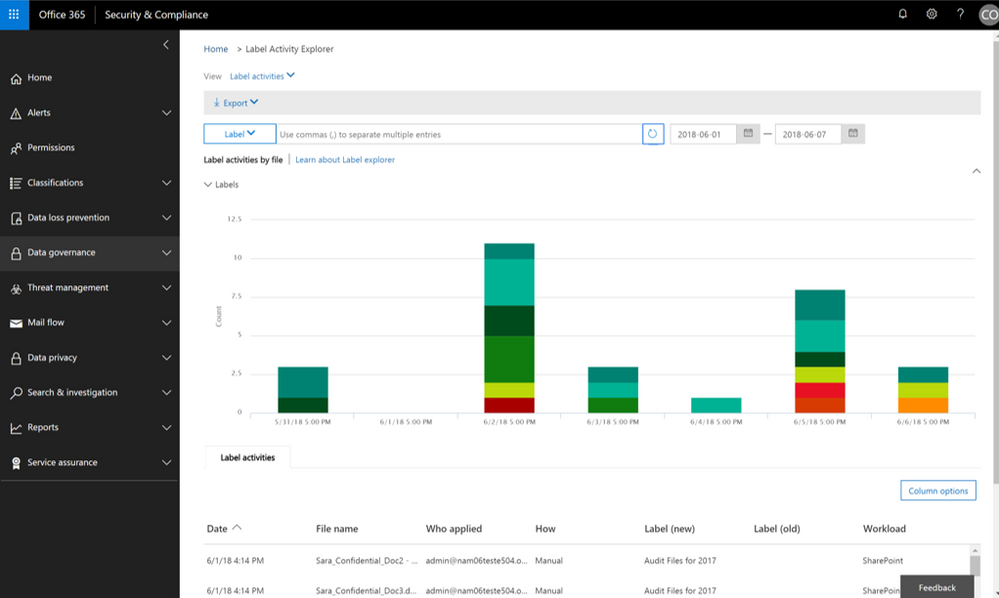 Validate or investigate label activity in your organization.
Validate or investigate label activity in your organization.
Auto-label items as Records
The ability to auto-apply labels to content with sensitive data or based on custom keyword or query has been enabling organizations to classify and retain vast amounts of data, and now you can use that same technology to auto-label a document as a record.
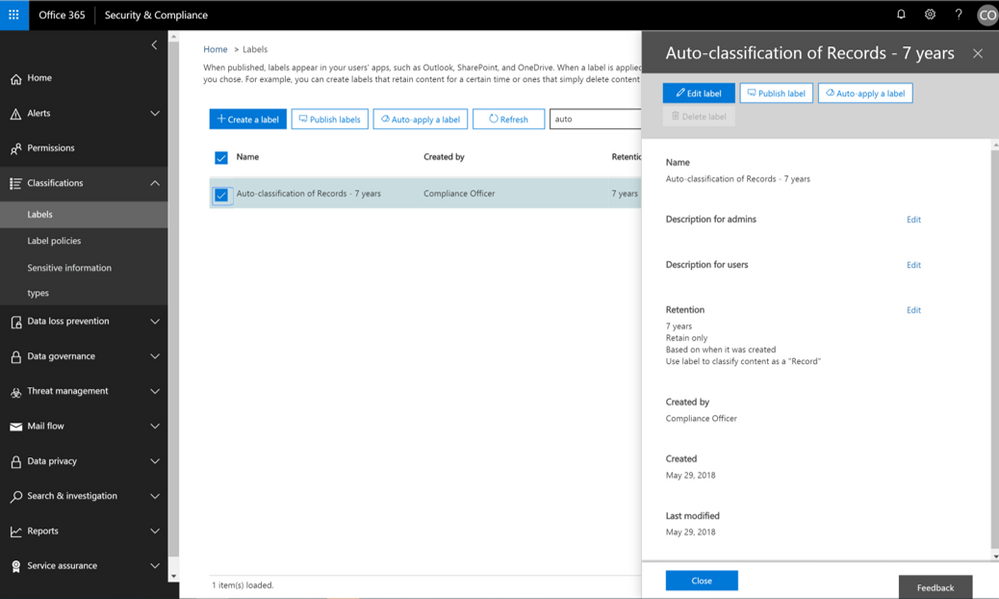 Now auto-apply a label marked as a record.
Now auto-apply a label marked as a record.
In addition, we have also recently provided updates to the user experience of items that have been identified as records. Once an item has been tagged as a record, the SharePoint user experience will show a small lock icon to denote that this item has been classified as a record.
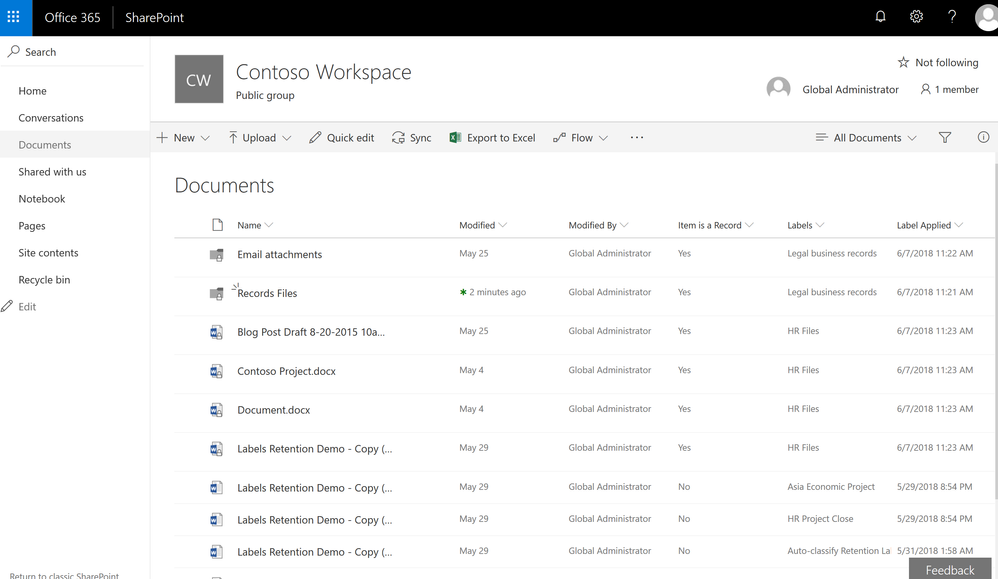 Items labeled as records will now show the small padlock icon to indicate they are records.
Items labeled as records will now show the small padlock icon to indicate they are records.
Event-based Retention
In case you missed it, Events Based Retention is now generally available in Advanced Data Governance, make sure to read the blog post and watch the video showing how this works. For further information read the supporting documentation here.
To learn more about Data Governance in Office 365 read more here.

The new Label Activity Explorer helps you easily validate how data has been labeled and investigate risky or abnormal label activity in your organization. As data grows in your organization, so does the need to classify and govern it to ensure business continuity and readiness for regulations such as the GDPR. To help meet these goals, you can create Office 365 labels and either publish them to users’ apps (so they can manually classify their own content) or automatically apply them to content containing sensitive information.
Data Governance dashboard refresh
In addition to the Label Activity Explorer, we have also refreshed the Data Governance dashboard to include new features, such as the Data Governance toolbox and label insights widgets. Let’s take a closer look.
Data Governance toolbox
The new Data Governance toolbox is your one-stop-shop for guidance and links to common data governance tasks. These tools can help you manage the full content lifecycle, including how to:
- Import data into Office 365 and increase email storage so you can use Office 365 features to govern it
- Manage how data is classified, retained, accessed, and disposed of
- Track label usage, monitor alerts, and respond to disposition reviews
 Data Governance toolbox provides guidance on getting started with Data Governance in Office 365.
Data Governance toolbox provides guidance on getting started with Data Governance in Office 365.
Label insights widgets and supporting reports
Label insights widgets provide you with a quick view into the classification of data in your organization, including how labels were applied, labels that have been classified as records, top labels, top users of labels, label trends, and risky label activities. Click on the label insights widgets to open a more detailed report so you can drill down further.
 Labels insights widgets provide information about labels usage in your organization.
Labels insights widgets provide information about labels usage in your organization.
Label Activity Explorer
The Label Activity Explorer that was previewed in April is now generally available. This new experience provides real-time data that lets you investigate risky label activity and verify that labels are being applied to content as you intended. Use this information to increase confidence that your sensitive data has been detected, classified, and retained according to your organization’s policies.
Filter on labels applied at either the file or folder level to learn more about activities and changes. Once you find the label and file or folder of interest, you can investigate further by reviewing details such as the user who applied the label, file name, and parent site. If you have the right permissions, you can even access the in-place content directly. Learn more about the label activity explorer.
 Validate or investigate label activity in your organization.
Validate or investigate label activity in your organization.
Auto-label items as Records
The ability to auto-apply labels to content with sensitive data or based on custom keyword or query has been enabling organizations to classify and retain vast amounts of data, and now you can use that same technology to auto-label a document as a record.
 Now auto-apply a label marked as a record.
Now auto-apply a label marked as a record.
In addition, we have also recently provided updates to the user experience of items that have been identified as records. Once an item has been tagged as a record, the SharePoint user experience will show a small lock icon to denote that this item has been classified as a record.
 Items labeled as records will now show the small padlock icon to indicate they are records.
Items labeled as records will now show the small padlock icon to indicate they are records.
Event-based Retention
In case you missed it, Events Based Retention is now generally available in Advanced Data Governance, make sure to read the blog post and watch the video showing how this works. For further information read the supporting documentation here.
To learn more about Data Governance in Office 365 read more here.

The new Label Activity Explorer helps you easily validate how data has been labeled and investigate risky or abnormal label activity in your organization. As data grows in your organization, so does the need to classify and govern it to ensure business continuity and readiness for regulations such as the GDPR. To help meet these goals, you can create Office 365 labels and either publish them to users’ apps (so they can manually classify their own content) or automatically apply them to content containing sensitive information.
Data Governance dashboard refresh
In addition to the Label Activity Explorer, we have also refreshed the Data Governance dashboard to include new features, such as the Data Governance toolbox and label insights widgets. Let’s take a closer look.
Data Governance toolbox
The new Data Governance toolbox is your one-stop-shop for guidance and links to common data governance tasks. These tools can help you manage the full content lifecycle, including how to:
- Import data into Office 365 and increase email storage so you can use Office 365 features to govern it
- Manage how data is classified, retained, accessed, and disposed of
- Track label usage, monitor alerts, and respond to disposition reviews
 Data Governance toolbox provides guidance on getting started with Data Governance in Office 365.
Data Governance toolbox provides guidance on getting started with Data Governance in Office 365.
Label insights widgets and supporting reports
Label insights widgets provide you with a quick view into the classification of data in your organization, including how labels were applied, labels that have been classified as records, top labels, top users of labels, label trends, and risky label activities. Click on the label insights widgets to open a more detailed report so you can drill down further.
 Labels insights widgets provide information about labels usage in your organization.
Labels insights widgets provide information about labels usage in your organization.
Label Activity Explorer
The Label Activity Explorer that was previewed in April is now generally available. This new experience provides real-time data that lets you investigate risky label activity and verify that labels are being applied to content as you intended. Use this information to increase confidence that your sensitive data has been detected, classified, and retained according to your organization’s policies.
Filter on labels applied at either the file or folder level to learn more about activities and changes. Once you find the label and file or folder of interest, you can investigate further by reviewing details such as the user who applied the label, file name, and parent site. If you have the right permissions, you can even access the in-place content directly. Learn more about the label activity explorer.
 Validate or investigate label activity in your organization.
Validate or investigate label activity in your organization.
Auto-label items as Records
The ability to auto-apply labels to content with sensitive data or based on custom keyword or query has been enabling organizations to classify and retain vast amounts of data, and now you can use that same technology to auto-label a document as a record.
 Now auto-apply a label marked as a record.
Now auto-apply a label marked as a record.
In addition, we have also recently provided updates to the user experience of items that have been identified as records. Once an item has been tagged as a record, the SharePoint user experience will show a small lock icon to denote that this item has been classified as a record.
 Items labeled as records will now show the small padlock icon to indicate they are records.
Items labeled as records will now show the small padlock icon to indicate they are records.
Event-based Retention
In case you missed it, Events Based Retention is now generally available in Advanced Data Governance, make sure to read the blog post and watch the video showing how this works. For further information read the supporting documentation here.
To learn more about Data Governance in Office 365 read more here.

The new Label Activity Explorer helps you easily validate how data has been labeled and investigate risky or abnormal label activity in your organization. As data grows in your organization, so does the need to classify and govern it to ensure business continuity and readiness for regulations such as the GDPR. To help meet these goals, you can create Office 365 labels and either publish them to users’ apps (so they can manually classify their own content) or automatically apply them to content containing sensitive information.
Data Governance dashboard refresh
In addition to the Label Activity Explorer, we have also refreshed the Data Governance dashboard to include new features, such as the Data Governance toolbox and label insights widgets. Let’s take a closer look.
Data Governance toolbox
The new Data Governance toolbox is your one-stop-shop for guidance and links to common data governance tasks. These tools can help you manage the full content lifecycle, including how to:
- Import data into Office 365 and increase email storage so you can use Office 365 features to govern it
- Manage how data is classified, retained, accessed, and disposed of
- Track label usage, monitor alerts, and respond to disposition reviews
 Data Governance toolbox provides guidance on getting started with Data Governance in Office 365.
Data Governance toolbox provides guidance on getting started with Data Governance in Office 365.
Label insights widgets and supporting reports
Label insights widgets provide you with a quick view into the classification of data in your organization, including how labels were applied, labels that have been classified as records, top labels, top users of labels, label trends, and risky label activities. Click on the label insights widgets to open a more detailed report so you can drill down further.
 Labels insights widgets provide information about labels usage in your organization.
Labels insights widgets provide information about labels usage in your organization.
Label Activity Explorer
The Label Activity Explorer that was previewed in April is now generally available. This new experience provides real-time data that lets you investigate risky label activity and verify that labels are being applied to content as you intended. Use this information to increase confidence that your sensitive data has been detected, classified, and retained according to your organization’s policies.
Filter on labels applied at either the file or folder level to learn more about activities and changes. Once you find the label and file or folder of interest, you can investigate further by reviewing details such as the user who applied the label, file name, and parent site. If you have the right permissions, you can even access the in-place content directly. Learn more about the label activity explorer.
 Validate or investigate label activity in your organization.
Validate or investigate label activity in your organization.
Auto-label items as Records
The ability to auto-apply labels to content with sensitive data or based on custom keyword or query has been enabling organizations to classify and retain vast amounts of data, and now you can use that same technology to auto-label a document as a record.
 Now auto-apply a label marked as a record.
Now auto-apply a label marked as a record.
In addition, we have also recently provided updates to the user experience of items that have been identified as records. Once an item has been tagged as a record, the SharePoint user experience will show a small lock icon to denote that this item has been classified as a record.
 Items labeled as records will now show the small padlock icon to indicate they are records.
Items labeled as records will now show the small padlock icon to indicate they are records.
Event-based Retention
In case you missed it, Events Based Retention is now generally available in Advanced Data Governance, make sure to read the blog post and watch the video showing how this works. For further information read the supporting documentation here.
To learn more about Data Governance in Office 365 read more here.
Often admins with privileged accounts have broad standing access, and therefore, become lucrative targets of repeated attacks as access to admin credentials can lead to deeper access to sensitive data. Due to this risk, regulators are increasingly looking for appropriate limits on privileged access, greater oversight, and audit trails.
To help customers protect and control their sensitive data, and meet their compliance needs, today, we are announcing preview of privileged access management in Office 365.
New privileged access management capabilities in Office 365 provides an approval workflow that’s scoped to your high-risk tasks within Office 365. For example, standing admin privileges enable admins to execute tasks that can provide unfettered access to organizational data, such as a journal rule, which can copy emails to a shadow mailbox and exfiltrate sensitive data undetected.
Privileged access management in Office 365 was designed based on the principle of Zero Standing Access, which is how we run our own data centers at Microsoft through Lockbox and Customer Lockbox. With privileged access management in Office 365, access requests must be approved by an authorized set of approvers. Access is then time-bound for a limited duration — often referred to as “Just-In-Time” (JIT) access. This level of rigor is how we manage administrative access privileges internally for Office 365 today.
Requests for access can be automatically or manually approved. Either way, all the activity is logged and auditable, so that both privileged access requests and approvals can be reviewed and seamlessly provided for internal reviews and auditor requests.
Read below for more details.
Creating Access Policies
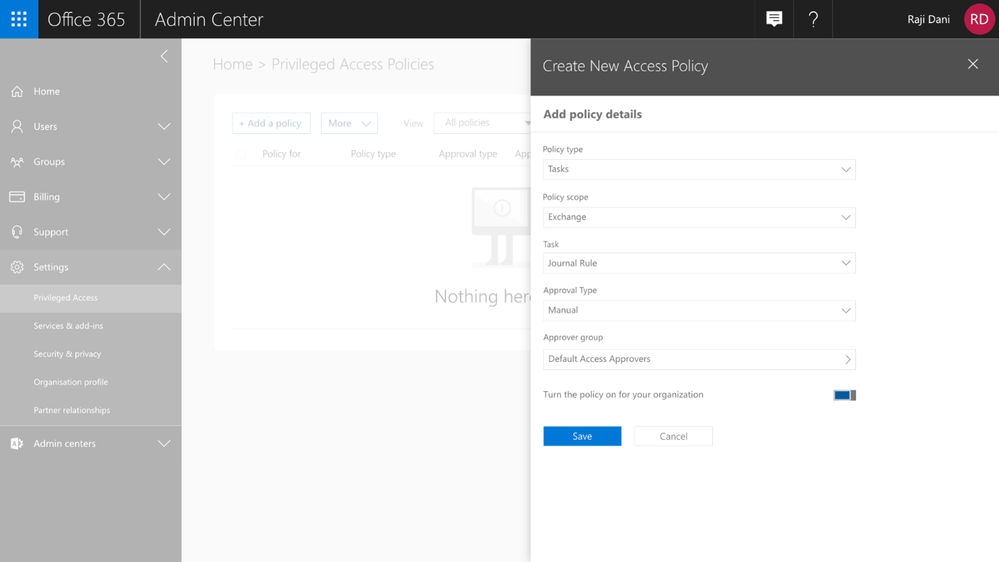
Getting started with privileged access management in Office 365 in your organization is simple. Within the Office 365 Admin Center, you can create access policies at a task level, scope it to an Office 365 workload, and to a specific task within that workload. The policies also allow for flexibility in how requests can be approved – automatically or manually through a set of designated approvers.
 Graphic: Configuring a new access policy in the Office 365 Admin Center.
Graphic: Configuring a new access policy in the Office 365 Admin Center.
Enforcing an Approval Workflow
Once policies are in place, privileged access management in Office 365 will enforce the approval workflow, and when needed, users can request Just-in-Time access to execute these privileged tasks. Their privileges will endure only for the time requested and approved, vastly reducing the risk to the organization from privileged credential compromise.
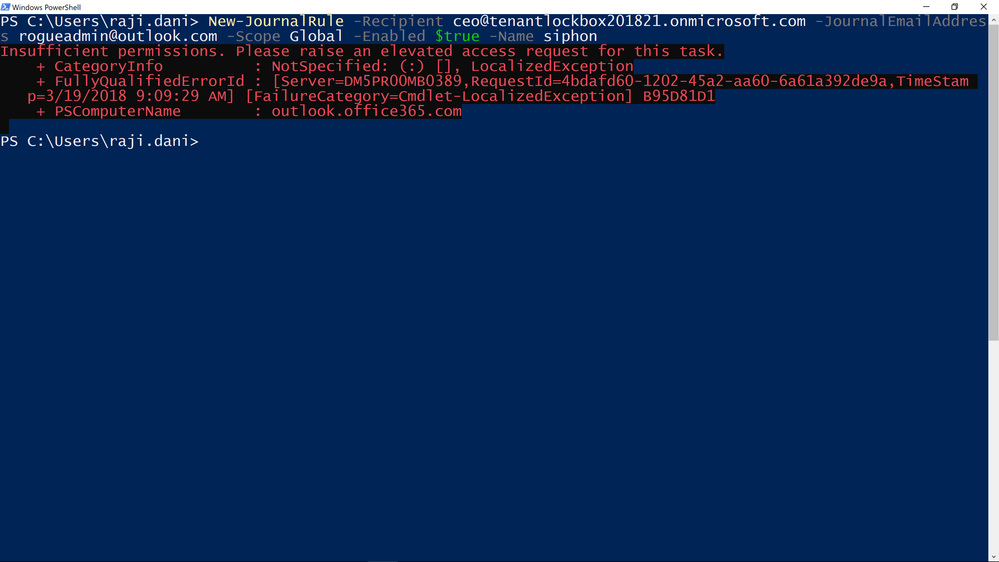 Graphic: Cmdlet fails with an error and asks to raise an elevation request to get access.
Graphic: Cmdlet fails with an error and asks to raise an elevation request to get access.
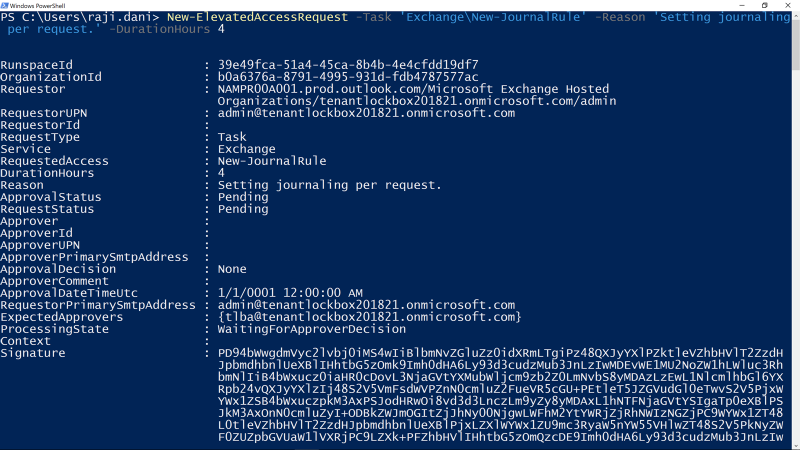 Graphic: Request access using New-Elevated Access Request cmdlet, request is scoped to New-JournalRule with a limited duration of 4 hours.
Graphic: Request access using New-Elevated Access Request cmdlet, request is scoped to New-JournalRule with a limited duration of 4 hours.
Approving Access
All access requests generated through the privileged access management workflow are available to view in the Office 365 Admin center. Designated approvers can review the details of the request –the requester, requested duration, and specified reason – and can then approve or deny the request.
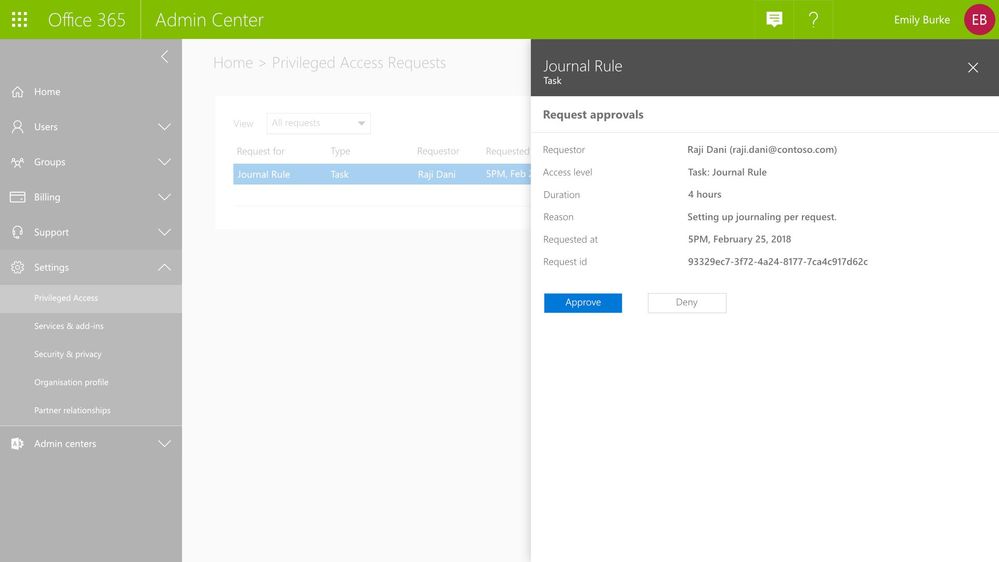 Graphic: As the approver, you can see the pending request with option to approve or deny request.
Graphic: As the approver, you can see the pending request with option to approve or deny request.
Audit Documentation
All activities – requests, approver actions, and subsequent tasks performed by the requesters – are logged and available for review in the Office 365 Management Activity logs. These audit logs provide a chain of events that also serve as evidence for compliance requirements.
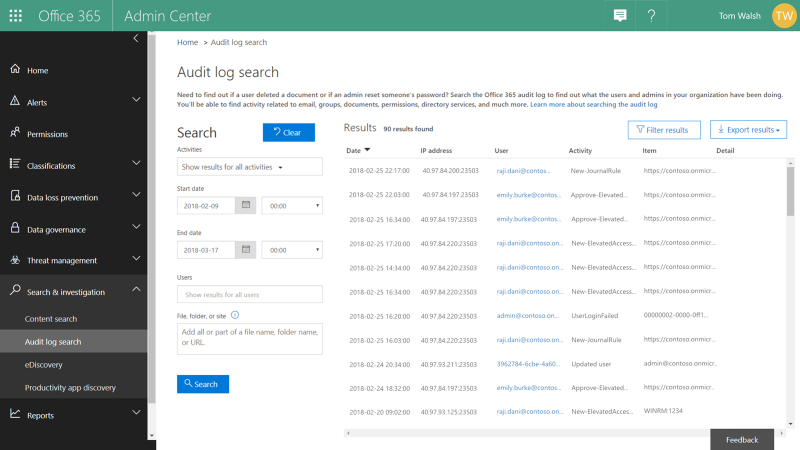 Graphic: Review audit logs for all privileged access management activity.
Graphic: Review audit logs for all privileged access management activity.
Get Started Today!
Privileged access management in Office 365 is available in preview for our customers with Office 365 E5 and Advanced Compliance SKUs who register for the option. We hope you take that extra step to enable these features for advanced access control capabilities in your Office 365 tenant today. You can get started by:
- Watching the Mechanics Video on privileged access management in Office 365.
- Signing up for the preview at https://previews.office.com, with code PAM044.
- Attending the Ask Me Anything (AMA) – sign up for the event here.
We hope you like what you see – please do sign up for preview so we can get your feedback!
Frequently Asked Questions
Q: What SKUs do I need to use privileged access management in Office 365?
A: We plan to offer this capability in the Office 365 E5 or the Advanced Compliance SKU when we release to general availability.
Q: Which Office 365 services are supported with privileged access management in Office 365?
A: During this preview, privileged access management in Office 365 applies to tasks available in Exchange Online. We are working to expand privileged access management capabilities to other Office 365 workloads.
Q: How is this different from the Azure Active Directory Privileged Identity Management (AAD PIM)?
A: Azure AD Privileged Identity Management (PIM) and privileged access management (PAM) in Office 365 together provide a robust set of controls for protecting privileged access to your corporate data. With Azure AD PIM, customers can secure admin roles to ensure protection across Office 365 and Azure clouds. PAM in Office 365 can provide another granular layer of protection by controlling access to tasks within Office 365.
Q: What permissions do I need to turn this feature on?
A: You need to be a Global or Tenant administrator to be able to turn this feature on. Soon we will enable a new user Role that also will be able to perform these actions.
Q: How is privileged access management in Office 365 related to Customer Lockbox?
A: Customer Lockbox allows a level of access control for organizations around accessed to data by their service provider, i.e. Microsoft. Privileged access management in Office 365, allows granular access control within an organization for all Office 365 privileged tasks.

Often admins with privileged accounts have broad standing access, and therefore, become lucrative targets of repeated attacks as access to admin credentials can lead to deeper access to sensitive data. Due to this risk, regulators are increasingly looking for appropriate limits on privileged access, greater oversight, and audit trails.
To help customers protect and control their sensitive data, and meet their compliance needs, today, we are announcing preview of privileged access management in Office 365.
New privileged access management capabilities in Office 365 provides an approval workflow that’s scoped to your high-risk tasks within Office 365. For example, standing admin privileges enable admins to execute tasks that can provide unfettered access to organizational data, such as a journal rule, which can copy emails to a shadow mailbox and exfiltrate sensitive data undetected.
Privileged access management in Office 365 was designed based on the principle of Zero Standing Access, which is how we run our own data centers at Microsoft through Lockbox and Customer Lockbox. With privileged access management in Office 365, access requests must be approved by an authorized set of approvers. Access is then time-bound for a limited duration — often referred to as “Just-In-Time” (JIT) access. This level of rigor is how we manage administrative access privileges internally for Office 365 today.
Requests for access can be automatically or manually approved. Either way, all the activity is logged and auditable, so that both privileged access requests and approvals can be reviewed and seamlessly provided for internal reviews and auditor requests.
Read below for more details.
Creating Access Policies
Getting started with privileged access management in Office 365 in your organization is simple. Within the Office 365 Admin Center, you can create access policies at a task level, scope it to an Office 365 workload, and to a specific task within that workload. The policies also allow for flexibility in how requests can be approved – automatically or manually through a set of designated approvers.
 Graphic: Configuring a new access policy in the Office 365 Admin Center.
Graphic: Configuring a new access policy in the Office 365 Admin Center.
Enforcing an Approval Workflow
Once policies are in place, privileged access management in Office 365 will enforce the approval workflow, and when needed, users can request Just-in-Time access to execute these privileged tasks. Their privileges will endure only for the time requested and approved, vastly reducing the risk to the organization from privileged credential compromise.
 Graphic: Cmdlet fails with an error and asks to raise an elevation request to get access.
Graphic: Cmdlet fails with an error and asks to raise an elevation request to get access.
 Graphic: Request access using New-Elevated Access Request cmdlet, request is scoped to New-JournalRule with a limited duration of 4 hours.
Graphic: Request access using New-Elevated Access Request cmdlet, request is scoped to New-JournalRule with a limited duration of 4 hours.
Approving Access
All access requests generated through the privileged access management workflow are available to view in the Office 365 Admin center. Designated approvers can review the details of the request –the requester, requested duration, and specified reason – and can then approve or deny the request.
 Graphic: As the approver, you can see the pending request with option to approve or deny request.
Graphic: As the approver, you can see the pending request with option to approve or deny request.
Audit Documentation
All activities – requests, approver actions, and subsequent tasks performed by the requesters – are logged and available for review in the Office 365 Management Activity logs. These audit logs provide a chain of events that also serve as evidence for compliance requirements.
 Graphic: Review audit logs for all privileged access management activity.
Graphic: Review audit logs for all privileged access management activity.
Get Started Today!
Privileged access management in Office 365 is available in preview for our customers with Office 365 E5 and Advanced Compliance SKUs who register for the option. We hope you take that extra step to enable these features for advanced access control capabilities in your Office 365 tenant today. You can get started by:
- Watching the Mechanics Video on privileged access management in Office 365.
- Signing up for the preview at https://previews.office.com, with code PAM044.
- Attending the Ask Me Anything (AMA) – sign up for the event here.
We hope you like what you see – please do sign up for preview so we can get your feedback!
Frequently Asked Questions
Q: What SKUs do I need to use privileged access management in Office 365?
A: We plan to offer this capability in the Office 365 E5 or the Advanced Compliance SKU when we release to general availability.
Q: Which Office 365 services are supported with privileged access management in Office 365?
A: During this preview, privileged access management in Office 365 applies to tasks available in Exchange Online. We are working to expand privileged access management capabilities to other Office 365 workloads.
Q: How is this different from the Azure Active Directory Privileged Identity Management (AAD PIM)?
A: Azure AD Privileged Identity Management (PIM) and privileged access management (PAM) in Office 365 together provide a robust set of controls for protecting privileged access to your corporate data. With Azure AD PIM, customers can secure admin roles to ensure protection across Office 365 and Azure clouds. PAM in Office 365 can provide another granular layer of protection by controlling access to tasks within Office 365.
Q: What permissions do I need to turn this feature on?
A: You need to be a Global or Tenant administrator to be able to turn this feature on. Soon we will enable a new user Role that also will be able to perform these actions.
Q: How is privileged access management in Office 365 related to Customer Lockbox?
A: Customer Lockbox allows a level of access control for organizations around accessed to data by their service provider, i.e. Microsoft. Privileged access management in Office 365, allows granular access control within an organization for all Office 365 privileged tasks.

Often admins with privileged accounts have broad standing access, and therefore, become lucrative targets of repeated attacks as access to admin credentials can lead to deeper access to sensitive data. Due to this risk, regulators are increasingly looking for appropriate limits on privileged access, greater oversight, and audit trails.
To help customers protect and control their sensitive data, and meet their compliance needs, today, we are announcing preview of privileged access management in Office 365.
New privileged access management capabilities in Office 365 provides an approval workflow that’s scoped to your high-risk tasks within Office 365. For example, standing admin privileges enable admins to execute tasks that can provide unfettered access to organizational data, such as a journal rule, which can copy emails to a shadow mailbox and exfiltrate sensitive data undetected.
Privileged access management in Office 365 was designed based on the principle of Zero Standing Access, which is how we run our own data centers at Microsoft through Lockbox and Customer Lockbox. With privileged access management in Office 365, access requests must be approved by an authorized set of approvers. Access is then time-bound for a limited duration — often referred to as “Just-In-Time” (JIT) access. This level of rigor is how we manage administrative access privileges internally for Office 365 today.
Requests for access can be automatically or manually approved. Either way, all the activity is logged and auditable, so that both privileged access requests and approvals can be reviewed and seamlessly provided for internal reviews and auditor requests.
Read below for more details.
Creating Access Policies
Getting started with privileged access management in Office 365 in your organization is simple. Within the Office 365 Admin Center, you can create access policies at a task level, scope it to an Office 365 workload, and to a specific task within that workload. The policies also allow for flexibility in how requests can be approved – automatically or manually through a set of designated approvers.
 Graphic: Configuring a new access policy in the Office 365 Admin Center.
Graphic: Configuring a new access policy in the Office 365 Admin Center.
Enforcing an Approval Workflow
Once policies are in place, privileged access management in Office 365 will enforce the approval workflow, and when needed, users can request Just-in-Time access to execute these privileged tasks. Their privileges will endure only for the time requested and approved, vastly reducing the risk to the organization from privileged credential compromise.
 Graphic: Cmdlet fails with an error and asks to raise an elevation request to get access.
Graphic: Cmdlet fails with an error and asks to raise an elevation request to get access.
 Graphic: Request access using New-Elevated Access Request cmdlet, request is scoped to New-JournalRule with a limited duration of 4 hours.
Graphic: Request access using New-Elevated Access Request cmdlet, request is scoped to New-JournalRule with a limited duration of 4 hours.
Approving Access
All access requests generated through the privileged access management workflow are available to view in the Office 365 Admin center. Designated approvers can review the details of the request –the requester, requested duration, and specified reason – and can then approve or deny the request.
 Graphic: As the approver, you can see the pending request with option to approve or deny request.
Graphic: As the approver, you can see the pending request with option to approve or deny request.
Audit Documentation
All activities – requests, approver actions, and subsequent tasks performed by the requesters – are logged and available for review in the Office 365 Management Activity logs. These audit logs provide a chain of events that also serve as evidence for compliance requirements.
 Graphic: Review audit logs for all privileged access management activity.
Graphic: Review audit logs for all privileged access management activity.
Get Started Today!
Privileged access management in Office 365 is available in preview for our customers with Office 365 E5 and Advanced Compliance SKUs who register for the option. We hope you take that extra step to enable these features for advanced access control capabilities in your Office 365 tenant today. You can get started by:
- Watching the Mechanics Video on privileged access management in Office 365.
- Signing up for the preview at https://previews.office.com, with code PAM044.
- Attending the Ask Me Anything (AMA) – sign up for the event here.
We hope you like what you see – please do sign up for preview so we can get your feedback!
Frequently Asked Questions
Q: What SKUs do I need to use privileged access management in Office 365?
A: We plan to offer this capability in the Office 365 E5 or the Advanced Compliance SKU when we release to general availability.
Q: Which Office 365 services are supported with privileged access management in Office 365?
A: During this preview, privileged access management in Office 365 applies to tasks available in Exchange Online. We are working to expand privileged access management capabilities to other Office 365 workloads.
Q: How is this different from the Azure Active Directory Privileged Identity Management (AAD PIM)?
A: Azure AD Privileged Identity Management (PIM) and privileged access management (PAM) in Office 365 together provide a robust set of controls for protecting privileged access to your corporate data. With Azure AD PIM, customers can secure admin roles to ensure protection across Office 365 and Azure clouds. PAM in Office 365 can provide another granular layer of protection by controlling access to tasks within Office 365.
Q: What permissions do I need to turn this feature on?
A: You need to be a Global or Tenant administrator to be able to turn this feature on. Soon we will enable a new user Role that also will be able to perform these actions.
Q: How is privileged access management in Office 365 related to Customer Lockbox?
A: Customer Lockbox allows a level of access control for organizations around accessed to data by their service provider, i.e. Microsoft. Privileged access management in Office 365, allows granular access control within an organization for all Office 365 privileged tasks.

Often admins with privileged accounts have broad standing access, and therefore, become lucrative targets of repeated attacks as access to admin credentials can lead to deeper access to sensitive data. Due to this risk, regulators are increasingly looking for appropriate limits on privileged access, greater oversight, and audit trails.
To help customers protect and control their sensitive data, and meet their compliance needs, today, we are announcing preview of privileged access management in Office 365.
New privileged access management capabilities in Office 365 provides an approval workflow that’s scoped to your high-risk tasks within Office 365. For example, standing admin privileges enable admins to execute tasks that can provide unfettered access to organizational data, such as a journal rule, which can copy emails to a shadow mailbox and exfiltrate sensitive data undetected.
Privileged access management in Office 365 was designed based on the principle of Zero Standing Access, which is how we run our own data centers at Microsoft through Lockbox and Customer Lockbox. With privileged access management in Office 365, access requests must be approved by an authorized set of approvers. Access is then time-bound for a limited duration — often referred to as “Just-In-Time” (JIT) access. This level of rigor is how we manage administrative access privileges internally for Office 365 today.
Requests for access can be automatically or manually approved. Either way, all the activity is logged and auditable, so that both privileged access requests and approvals can be reviewed and seamlessly provided for internal reviews and auditor requests.
Read below for more details.
Creating Access Policies
Getting started with privileged access management in Office 365 in your organization is simple. Within the Office 365 Admin Center, you can create access policies at a task level, scope it to an Office 365 workload, and to a specific task within that workload. The policies also allow for flexibility in how requests can be approved – automatically or manually through a set of designated approvers.
 Graphic: Configuring a new access policy in the Office 365 Admin Center.
Graphic: Configuring a new access policy in the Office 365 Admin Center.
Enforcing an Approval Workflow
Once policies are in place, privileged access management in Office 365 will enforce the approval workflow, and when needed, users can request Just-in-Time access to execute these privileged tasks. Their privileges will endure only for the time requested and approved, vastly reducing the risk to the organization from privileged credential compromise.
 Graphic: Cmdlet fails with an error and asks to raise an elevation request to get access.
Graphic: Cmdlet fails with an error and asks to raise an elevation request to get access.
 Graphic: Request access using New-Elevated Access Request cmdlet, request is scoped to New-JournalRule with a limited duration of 4 hours.
Graphic: Request access using New-Elevated Access Request cmdlet, request is scoped to New-JournalRule with a limited duration of 4 hours.
Approving Access
All access requests generated through the privileged access management workflow are available to view in the Office 365 Admin center. Designated approvers can review the details of the request –the requester, requested duration, and specified reason – and can then approve or deny the request.
 Graphic: As the approver, you can see the pending request with option to approve or deny request.
Graphic: As the approver, you can see the pending request with option to approve or deny request.
Audit Documentation
All activities – requests, approver actions, and subsequent tasks performed by the requesters – are logged and available for review in the Office 365 Management Activity logs. These audit logs provide a chain of events that also serve as evidence for compliance requirements.
 Graphic: Review audit logs for all privileged access management activity.
Graphic: Review audit logs for all privileged access management activity.
Get Started Today!
Privileged access management in Office 365 is available in preview for our customers with Office 365 E5 and Advanced Compliance SKUs who register for the option. We hope you take that extra step to enable these features for advanced access control capabilities in your Office 365 tenant today. You can get started by:
- Watching the Mechanics Video on privileged access management in Office 365.
- Signing up for the preview at https://previews.office.com, with code PAM044.
- Attending the Ask Me Anything (AMA) – sign up for the event here.
We hope you like what you see – please do sign up for preview so we can get your feedback!
Frequently Asked Questions
Q: What SKUs do I need to use privileged access management in Office 365?
A: We plan to offer this capability in the Office 365 E5 or the Advanced Compliance SKU when we release to general availability.
Q: Which Office 365 services are supported with privileged access management in Office 365?
A: During this preview, privileged access management in Office 365 applies to tasks available in Exchange Online. We are working to expand privileged access management capabilities to other Office 365 workloads.
Q: How is this different from the Azure Active Directory Privileged Identity Management (AAD PIM)?
A: Azure AD Privileged Identity Management (PIM) and privileged access management (PAM) in Office 365 together provide a robust set of controls for protecting privileged access to your corporate data. With Azure AD PIM, customers can secure admin roles to ensure protection across Office 365 and Azure clouds. PAM in Office 365 can provide another granular layer of protection by controlling access to tasks within Office 365.
Q: What permissions do I need to turn this feature on?
A: You need to be a Global or Tenant administrator to be able to turn this feature on. Soon we will enable a new user Role that also will be able to perform these actions.
Q: How is privileged access management in Office 365 related to Customer Lockbox?
A: Customer Lockbox allows a level of access control for organizations around accessed to data by their service provider, i.e. Microsoft. Privileged access management in Office 365, allows granular access control within an organization for all Office 365 privileged tasks.
With the kickoff of InfoSec Europe, we shared an update of our recent enhancements to Office 365 threat protection services. Today, we discuss the significant enrichment to the end user experience in Office 365. By empowering end users to make better decisions which help drive proactive protection, we offer an unique, powerful, and potentially best in class solution. The features we showcase today provide end users greater information, enabling better decision making and ultimately greater security.
Introducing Native Link Rendering
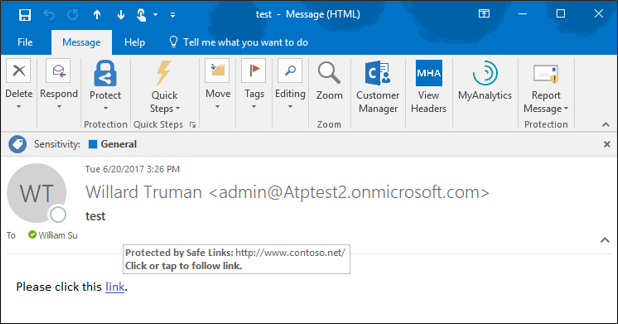
‘Native Link Rendering’ is now available for customers using Office Web Application (OWA). Soon the feature will also be available for the Outlook client. ‘Native Link Rendering’ exposes the native link for a user to view, though we still wrap the link in the back end for analysis. Importantly, no other advanced security solution can provide this powerful and crucial feature. Native Link Rendering has been a top request from customers because it supports end user education by providing visibility to the original view of an URL. Office 365 ATP’s Safe Links ‘time-of-click-protection’ protects users from clicking through to a malicious site. To do so, Safe Links wraps the link at the time of click, obfuscating the native URL which reduces users’ ability to learn what a potentially malicious URL may look like. Customers educating end users on indicators of a malicious link, require the display of native links since wrapped links prevent the ability to train users. ‘Native Link Rendering’ lets users see the original link. It is an unique and critical feature serving to empower our customer’s users to become more aware, sophisticated, and proactive at preventing themselves from being compromised by malicious links. Microsoft believes education and awareness is a foundational element for holistic security and Native Link Rendering serves to both educate and raise user awareness on cyberthreats.
 Figure 1. Native Link Rendering Feature showing the original URL in the hover window
Figure 1. Native Link Rendering Feature showing the original URL in the hover window
Enhanced Safe Links Warning Pages
The end user experience is further enhanced with new Safe Links warning pages. The new warning pages provide granular details on why a warning is generated. The pages range from notifying the user that a link is still being scanned, to a generic error warning.
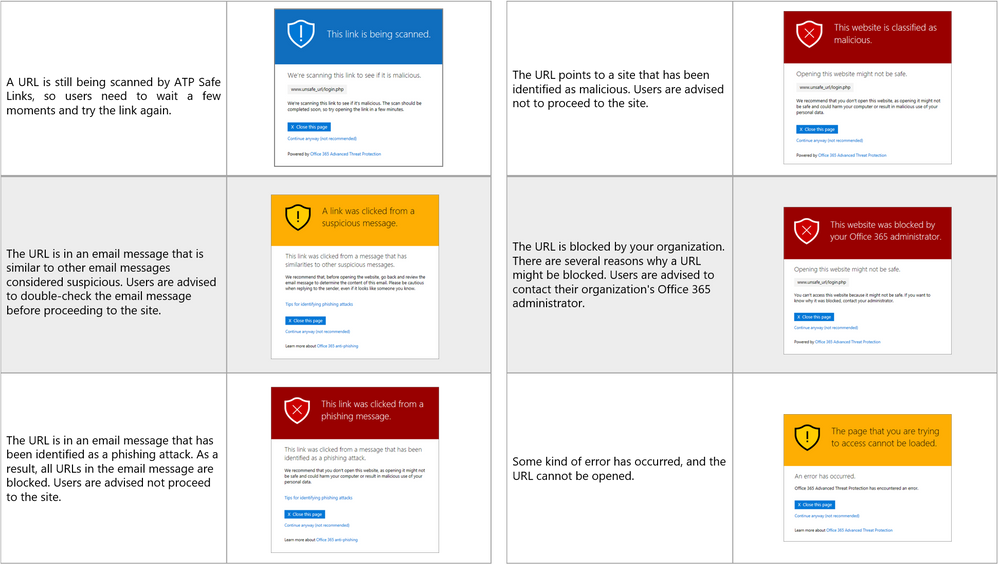 Figure 2. Summary of New Safe Links Warning Pages
Figure 2. Summary of New Safe Links Warning Pages
With this greater detail, users have better information on why a link was flagged, facilitating user understanding of when and why threats are blocked. Ultimately, a more informed user base can make better decisions and can better protect themselves from threats. We are excited to help your end users heighten their awareness and improve on their knowledge of potential threats.
Send Us Your Feedback
Your valuable feedback enables us to continue improving and adding features that support the goal of making Office 365 more secure. We encourage you to begin a free Office 365 E5 trial today and begin further enhancing your security for Office 365 today.

With the kickoff of InfoSec Europe, we shared an update of our recent enhancements to Office 365 threat protection services. Today, we discuss the significant enrichment to the end user experience in Office 365. By empowering end users to make better decisions which help drive proactive protection, we offer an unique, powerful, and potentially best in class solution. The features we showcase today provide end users greater information, enabling better decision making and ultimately greater security.
Introducing Native Link Rendering
‘Native Link Rendering’ is now available for customers using Office Web Application (OWA). Soon the feature will also be available for the Outlook client. ‘Native Link Rendering’ exposes the native link for a user to view, though we still wrap the link in the back end for analysis. Importantly, no other advanced security solution can provide this powerful and crucial feature. Native Link Rendering has been a top request from customers because it supports end user education by providing visibility to the original view of an URL. Office 365 ATP’s Safe Links ‘time-of-click-protection’ protects users from clicking through to a malicious site. To do so, Safe Links wraps the link at the time of click, obfuscating the native URL which reduces users’ ability to learn what a potentially malicious URL may look like. Customers educating end users on indicators of a malicious link, require the display of native links since wrapped links prevent the ability to train users. ‘Native Link Rendering’ lets users see the original link. It is an unique and critical feature serving to empower our customer’s users to become more aware, sophisticated, and proactive at preventing themselves from being compromised by malicious links. Microsoft believes education and awareness is a foundational element for holistic security and Native Link Rendering serves to both educate and raise user awareness on cyberthreats.
 Figure 1. Native Link Rendering Feature showing the original URL in the hover window
Figure 1. Native Link Rendering Feature showing the original URL in the hover window
Enhanced Safe Links Warning Pages
The end user experience is further enhanced with new Safe Links warning pages. The new warning pages provide granular details on why a warning is generated. The pages range from notifying the user that a link is still being scanned, to a generic error warning.
 Figure 2. Summary of New Safe Links Warning Pages
Figure 2. Summary of New Safe Links Warning Pages
With this greater detail, users have better information on why a link was flagged, facilitating user understanding of when and why threats are blocked. Ultimately, a more informed user base can make better decisions and can better protect themselves from threats. We are excited to help your end users heighten their awareness and improve on their knowledge of potential threats.
Send Us Your Feedback
Your valuable feedback enables us to continue improving and adding features that support the goal of making Office 365 more secure. We encourage you to begin a free Office 365 E5 trial today and begin further enhancing your security for Office 365 today.

With the kickoff of InfoSec Europe, we shared an update of our recent enhancements to Office 365 threat protection services. Today, we discuss the significant enrichment to the end user experience in Office 365. By empowering end users to make better decisions which help drive proactive protection, we offer an unique, powerful, and potentially best in class solution. The features we showcase today provide end users greater information, enabling better decision making and ultimately greater security.
Introducing Native Link Rendering
‘Native Link Rendering’ is now available for customers using Office Web Application (OWA). Soon the feature will also be available for the Outlook client. ‘Native Link Rendering’ exposes the native link for a user to view, though we still wrap the link in the back end for analysis. Importantly, no other advanced security solution can provide this powerful and crucial feature. Native Link Rendering has been a top request from customers because it supports end user education by providing visibility to the original view of an URL. Office 365 ATP’s Safe Links ‘time-of-click-protection’ protects users from clicking through to a malicious site. To do so, Safe Links wraps the link at the time of click, obfuscating the native URL which reduces users’ ability to learn what a potentially malicious URL may look like. Customers educating end users on indicators of a malicious link, require the display of native links since wrapped links prevent the ability to train users. ‘Native Link Rendering’ lets users see the original link. It is an unique and critical feature serving to empower our customer’s users to become more aware, sophisticated, and proactive at preventing themselves from being compromised by malicious links. Microsoft believes education and awareness is a foundational element for holistic security and Native Link Rendering serves to both educate and raise user awareness on cyberthreats.
 Figure 1. Native Link Rendering Feature showing the original URL in the hover window
Figure 1. Native Link Rendering Feature showing the original URL in the hover window
Enhanced Safe Links Warning Pages
The end user experience is further enhanced with new Safe Links warning pages. The new warning pages provide granular details on why a warning is generated. The pages range from notifying the user that a link is still being scanned, to a generic error warning.
 Figure 2. Summary of New Safe Links Warning Pages
Figure 2. Summary of New Safe Links Warning Pages
With this greater detail, users have better information on why a link was flagged, facilitating user understanding of when and why threats are blocked. Ultimately, a more informed user base can make better decisions and can better protect themselves from threats. We are excited to help your end users heighten their awareness and improve on their knowledge of potential threats.
Send Us Your Feedback
Your valuable feedback enables us to continue improving and adding features that support the goal of making Office 365 more secure. We encourage you to begin a free Office 365 E5 trial today and begin further enhancing your security for Office 365 today.

With the kickoff of InfoSec Europe, we shared an update of our recent enhancements to Office 365 threat protection services. Today, we discuss the significant enrichment to the end user experience in Office 365. By empowering end users to make better decisions which help drive proactive protection, we offer an unique, powerful, and potentially best in class solution. The features we showcase today provide end users greater information, enabling better decision making and ultimately greater security.
Introducing Native Link Rendering
‘Native Link Rendering’ is now available for customers using Office Web Application (OWA). Soon the feature will also be available for the Outlook client. ‘Native Link Rendering’ exposes the native link for a user to view, though we still wrap the link in the back end for analysis. Importantly, no other advanced security solution can provide this powerful and crucial feature. Native Link Rendering has been a top request from customers because it supports end user education by providing visibility to the original view of an URL. Office 365 ATP’s Safe Links ‘time-of-click-protection’ protects users from clicking through to a malicious site. To do so, Safe Links wraps the link at the time of click, obfuscating the native URL which reduces users’ ability to learn what a potentially malicious URL may look like. Customers educating end users on indicators of a malicious link, require the display of native links since wrapped links prevent the ability to train users. ‘Native Link Rendering’ lets users see the original link. It is an unique and critical feature serving to empower our customer’s users to become more aware, sophisticated, and proactive at preventing themselves from being compromised by malicious links. Microsoft believes education and awareness is a foundational element for holistic security and Native Link Rendering serves to both educate and raise user awareness on cyberthreats.
 Figure 1. Native Link Rendering Feature showing the original URL in the hover window
Figure 1. Native Link Rendering Feature showing the original URL in the hover window
Enhanced Safe Links Warning Pages
The end user experience is further enhanced with new Safe Links warning pages. The new warning pages provide granular details on why a warning is generated. The pages range from notifying the user that a link is still being scanned, to a generic error warning.
 Figure 2. Summary of New Safe Links Warning Pages
Figure 2. Summary of New Safe Links Warning Pages
With this greater detail, users have better information on why a link was flagged, facilitating user understanding of when and why threats are blocked. Ultimately, a more informed user base can make better decisions and can better protect themselves from threats. We are excited to help your end users heighten their awareness and improve on their knowledge of potential threats.
Send Us Your Feedback
Your valuable feedback enables us to continue improving and adding features that support the goal of making Office 365 more secure. We encourage you to begin a free Office 365 E5 trial today and begin further enhancing your security for Office 365 today.

Investigative Tools to Empower Stronger Threat Protection
We launched Office 365 Threat Intelligence to help organization’s become more secure by enhancing admin capabilities which offer greater visibility, deeper insights, and powerful executable actions (check out the recent webinar overviewing the service). Today we’re excited to announce ‘Threat Trackers’ for Office 365 Threat Intelligence, enabling efficient monitoring and management of threat investigations to help admins quickly remediate and respond to threats. The feature can be found under ‘Threat Management’ in the Security and Compliance Center. Table 1 summarizes the four available ‘Threat tracker’ categories.
 Table 1. The different tracker categories available in Office 365 Threat Intelligence Threat Trackers view
Table 1. The different tracker categories available in Office 365 Threat Intelligence Threat Trackers view
Threat Tracker Categories
Noteworthy campaigns are classified, as well known and important global threats. Office 365 Threat Intelligence pre-builds Noteworthy Campaign monitors, enabling admins to quickly review the impact of these threats, assessing both their volume and frequency. This automated monitoring allows admins speedy remediation from these threats. Noteworthy Campaign monitors update hourly, showing the latest impact of these threats to your organization. Click ‘Explore’ if you want to see the detailed events detected by the filter.
The Trending Campaigns view provides dynamic assessments of email threats impacting your organization’s Office 365 environment. This view shows tenant level malware trends, identifying malware families on the rise, flat, or declining, giving admins greater insight into which threats require further attention. New threats not seen recently in your organization will appear at the top of the page (sorted by trend). Trending Campaigns also offers a comparative view on how a threat impacts your organization versus others. If an organization’s targeting percentage is >10%, it indicates that it is being specifically targeted by the attack. Admins can further investigate targeted and trending attacks in Explorer, where actions such as deleting or moving the malware to junk can be taken. Targeted attacks are typically short-lived, so these types of attacks in the Trending Campaigns view may drop out of the view within a few days.
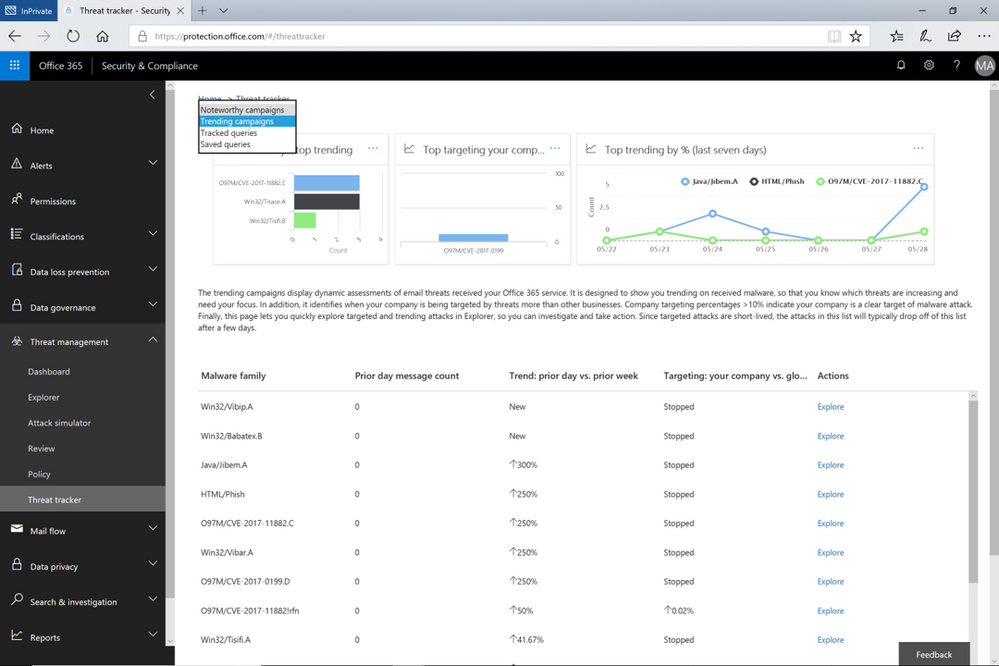 Figure 1. The Trending Campaigns view in Office 365 Threat Intelligence Threat trackers
Figure 1. The Trending Campaigns view in Office 365 Threat Intelligence Threat trackers
While the campaign views enable tracking and quick assessment of threats, queries are powerful investigative views allowing deeper understanding of threats, aiding admins to make data driven security updates. Queries can be accessed from either campaign view by clicking on ‘Explorer’ which displays that tracked threat campaign. Saved Queries provides a view into all Explorer searches saved as queries. Admins can monitor malware and phish events with the scope (number of emails included in an incident) defined and saved from Explorer. Saved queries are useful for checking items frequently. To create more saved queries, go to the Explorer, add filters to view specific sets of events, then select ‘Save query’ (button at top of page).
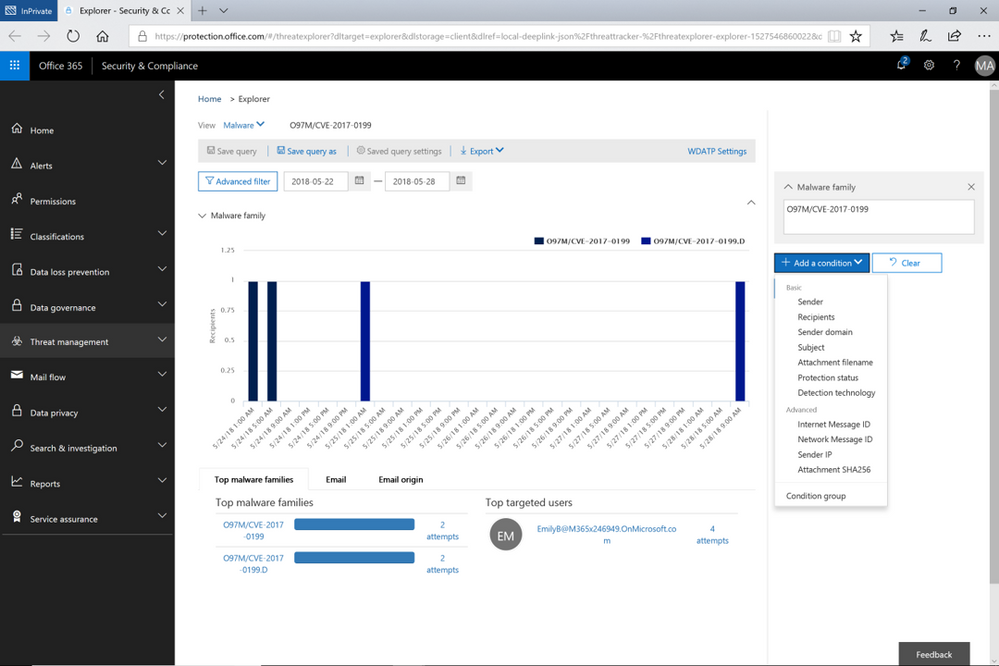 Figure 2. Opened Explorer page on tracked threat campaign. The threat campaign can be saved as query from the Explorer
Figure 2. Opened Explorer page on tracked threat campaign. The threat campaign can be saved as query from the Explorer
Tracked queries provide regular assessments of malware, phish, and other events with the scope defined from Threat Explorer. Tracked queries help monitor items frequently, providing reports, allowing quick and in-depth evaluation of threats or groups. A limited number of tracked queries are available for each organization. Admins can choose to convert saved queries and begin tracking them using the edit option for that query.
These ‘Threat Trackers’ enrich the admin experience, providing a powerful new tool for monitoring and managing, investigations, which ultimately enables quick response to threats. With this added feature, Office 365 Threat Intelligence provides admins to more efficiently and easily secure their organization.
Send Us Your Feedback
Let us know what you think of the new Threat trackers feature by beginning an Office 365 E5 trial today to experience the powerful capabilities of Office 365 Threat Intelligence. Your feedback enables us to make updates and enhancements to provide you with the best protection for Office 365. Please watch our recent webinar on Office 365 Threat Intelligence to learn further details on how the service can help your organization become more secure.

Investigative Tools to Empower Stronger Threat Protection
We launched Office 365 Threat Intelligence to help organization’s become more secure by enhancing admin capabilities which offer greater visibility, deeper insights, and powerful executable actions (check out the recent webinar overviewing the service). Today we’re excited to announce ‘Threat Trackers’ for Office 365 Threat Intelligence, enabling efficient monitoring and management of threat investigations to help admins quickly remediate and respond to threats. The feature can be found under ‘Threat Management’ in the Security and Compliance Center. Table 1 summarizes the four available ‘Threat tracker’ categories.
 Table 1. The different tracker categories available in Office 365 Threat Intelligence Threat Trackers view
Table 1. The different tracker categories available in Office 365 Threat Intelligence Threat Trackers view
Threat Tracker Categories
Noteworthy campaigns are classified, as well known and important global threats. Office 365 Threat Intelligence pre-builds Noteworthy Campaign monitors, enabling admins to quickly review the impact of these threats, assessing both their volume and frequency. This automated monitoring allows admins speedy remediation from these threats. Noteworthy Campaign monitors update hourly, showing the latest impact of these threats to your organization. Click ‘Explore’ if you want to see the detailed events detected by the filter.
The Trending Campaigns view provides dynamic assessments of email threats impacting your organization’s Office 365 environment. This view shows tenant level malware trends, identifying malware families on the rise, flat, or declining, giving admins greater insight into which threats require further attention. New threats not seen recently in your organization will appear at the top of the page (sorted by trend). Trending Campaigns also offers a comparative view on how a threat impacts your organization versus others. If an organization’s targeting percentage is >10%, it indicates that it is being specifically targeted by the attack. Admins can further investigate targeted and trending attacks in Explorer, where actions such as deleting or moving the malware to junk can be taken. Targeted attacks are typically short-lived, so these types of attacks in the Trending Campaigns view may drop out of the view within a few days.
 Figure 1. The Trending Campaigns view in Office 365 Threat Intelligence Threat trackers
Figure 1. The Trending Campaigns view in Office 365 Threat Intelligence Threat trackers
While the campaign views enable tracking and quick assessment of threats, queries are powerful investigative views allowing deeper understanding of threats, aiding admins to make data driven security updates. Queries can be accessed from either campaign view by clicking on ‘Explorer’ which displays that tracked threat campaign. Saved Queries provides a view into all Explorer searches saved as queries. Admins can monitor malware and phish events with the scope (number of emails included in an incident) defined and saved from Explorer. Saved queries are useful for checking items frequently. To create more saved queries, go to the Explorer, add filters to view specific sets of events, then select ‘Save query’ (button at top of page).
 Figure 2. Opened Explorer page on tracked threat campaign. The threat campaign can be saved as query from the Explorer
Figure 2. Opened Explorer page on tracked threat campaign. The threat campaign can be saved as query from the Explorer
Tracked queries provide regular assessments of malware, phish, and other events with the scope defined from Threat Explorer. Tracked queries help monitor items frequently, providing reports, allowing quick and in-depth evaluation of threats or groups. A limited number of tracked queries are available for each organization. Admins can choose to convert saved queries and begin tracking them using the edit option for that query.
These ‘Threat Trackers’ enrich the admin experience, providing a powerful new tool for monitoring and managing, investigations, which ultimately enables quick response to threats. With this added feature, Office 365 Threat Intelligence provides admins to more efficiently and easily secure their organization.
Send Us Your Feedback
Let us know what you think of the new Threat trackers feature by beginning an Office 365 E5 trial today to experience the powerful capabilities of Office 365 Threat Intelligence. Your feedback enables us to make updates and enhancements to provide you with the best protection for Office 365. Please watch our recent webinar on Office 365 Threat Intelligence to learn further details on how the service can help your organization become more secure.

Investigative Tools to Empower Stronger Threat Protection
We launched Office 365 Threat Intelligence to help organization’s become more secure by enhancing admin capabilities which offer greater visibility, deeper insights, and powerful executable actions (check out the recent webinar overviewing the service). Today we’re excited to announce ‘Threat Trackers’ for Office 365 Threat Intelligence, enabling efficient monitoring and management of threat investigations to help admins quickly remediate and respond to threats. The feature can be found under ‘Threat Management’ in the Security and Compliance Center. Table 1 summarizes the four available ‘Threat tracker’ categories.
 Table 1. The different tracker categories available in Office 365 Threat Intelligence Threat Trackers view
Table 1. The different tracker categories available in Office 365 Threat Intelligence Threat Trackers view
Threat Tracker Categories
Noteworthy campaigns are classified, as well known and important global threats. Office 365 Threat Intelligence pre-builds Noteworthy Campaign monitors, enabling admins to quickly review the impact of these threats, assessing both their volume and frequency. This automated monitoring allows admins speedy remediation from these threats. Noteworthy Campaign monitors update hourly, showing the latest impact of these threats to your organization. Click ‘Explore’ if you want to see the detailed events detected by the filter.
The Trending Campaigns view provides dynamic assessments of email threats impacting your organization’s Office 365 environment. This view shows tenant level malware trends, identifying malware families on the rise, flat, or declining, giving admins greater insight into which threats require further attention. New threats not seen recently in your organization will appear at the top of the page (sorted by trend). Trending Campaigns also offers a comparative view on how a threat impacts your organization versus others. If an organization’s targeting percentage is >10%, it indicates that it is being specifically targeted by the attack. Admins can further investigate targeted and trending attacks in Explorer, where actions such as deleting or moving the malware to junk can be taken. Targeted attacks are typically short-lived, so these types of attacks in the Trending Campaigns view may drop out of the view within a few days.
 Figure 1. The Trending Campaigns view in Office 365 Threat Intelligence Threat trackers
Figure 1. The Trending Campaigns view in Office 365 Threat Intelligence Threat trackers
While the campaign views enable tracking and quick assessment of threats, queries are powerful investigative views allowing deeper understanding of threats, aiding admins to make data driven security updates. Queries can be accessed from either campaign view by clicking on ‘Explorer’ which displays that tracked threat campaign. Saved Queries provides a view into all Explorer searches saved as queries. Admins can monitor malware and phish events with the scope (number of emails included in an incident) defined and saved from Explorer. Saved queries are useful for checking items frequently. To create more saved queries, go to the Explorer, add filters to view specific sets of events, then select ‘Save query’ (button at top of page).
 Figure 2. Opened Explorer page on tracked threat campaign. The threat campaign can be saved as query from the Explorer
Figure 2. Opened Explorer page on tracked threat campaign. The threat campaign can be saved as query from the Explorer
Tracked queries provide regular assessments of malware, phish, and other events with the scope defined from Threat Explorer. Tracked queries help monitor items frequently, providing reports, allowing quick and in-depth evaluation of threats or groups. A limited number of tracked queries are available for each organization. Admins can choose to convert saved queries and begin tracking them using the edit option for that query.
These ‘Threat Trackers’ enrich the admin experience, providing a powerful new tool for monitoring and managing, investigations, which ultimately enables quick response to threats. With this added feature, Office 365 Threat Intelligence provides admins to more efficiently and easily secure their organization.
Send Us Your Feedback
Let us know what you think of the new Threat trackers feature by beginning an Office 365 E5 trial today to experience the powerful capabilities of Office 365 Threat Intelligence. Your feedback enables us to make updates and enhancements to provide you with the best protection for Office 365. Please watch our recent webinar on Office 365 Threat Intelligence to learn further details on how the service can help your organization become more secure.

Investigative Tools to Empower Stronger Threat Protection
We launched Office 365 Threat Intelligence to help organization’s become more secure by enhancing admin capabilities which offer greater visibility, deeper insights, and powerful executable actions (check out the recent webinar overviewing the service). Today we’re excited to announce ‘Threat Trackers’ for Office 365 Threat Intelligence, enabling efficient monitoring and management of threat investigations to help admins quickly remediate and respond to threats. The feature can be found under ‘Threat Management’ in the Security and Compliance Center. Table 1 summarizes the four available ‘Threat tracker’ categories.
 Table 1. The different tracker categories available in Office 365 Threat Intelligence Threat Trackers view
Table 1. The different tracker categories available in Office 365 Threat Intelligence Threat Trackers view
Threat Tracker Categories
Noteworthy campaigns are classified, as well known and important global threats. Office 365 Threat Intelligence pre-builds Noteworthy Campaign monitors, enabling admins to quickly review the impact of these threats, assessing both their volume and frequency. This automated monitoring allows admins speedy remediation from these threats. Noteworthy Campaign monitors update hourly, showing the latest impact of these threats to your organization. Click ‘Explore’ if you want to see the detailed events detected by the filter.
The Trending Campaigns view provides dynamic assessments of email threats impacting your organization’s Office 365 environment. This view shows tenant level malware trends, identifying malware families on the rise, flat, or declining, giving admins greater insight into which threats require further attention. New threats not seen recently in your organization will appear at the top of the page (sorted by trend). Trending Campaigns also offers a comparative view on how a threat impacts your organization versus others. If an organization’s targeting percentage is >10%, it indicates that it is being specifically targeted by the attack. Admins can further investigate targeted and trending attacks in Explorer, where actions such as deleting or moving the malware to junk can be taken. Targeted attacks are typically short-lived, so these types of attacks in the Trending Campaigns view may drop out of the view within a few days.
 Figure 1. The Trending Campaigns view in Office 365 Threat Intelligence Threat trackers
Figure 1. The Trending Campaigns view in Office 365 Threat Intelligence Threat trackers
While the campaign views enable tracking and quick assessment of threats, queries are powerful investigative views allowing deeper understanding of threats, aiding admins to make data driven security updates. Queries can be accessed from either campaign view by clicking on ‘Explorer’ which displays that tracked threat campaign. Saved Queries provides a view into all Explorer searches saved as queries. Admins can monitor malware and phish events with the scope (number of emails included in an incident) defined and saved from Explorer. Saved queries are useful for checking items frequently. To create more saved queries, go to the Explorer, add filters to view specific sets of events, then select ‘Save query’ (button at top of page).
 Figure 2. Opened Explorer page on tracked threat campaign. The threat campaign can be saved as query from the Explorer
Figure 2. Opened Explorer page on tracked threat campaign. The threat campaign can be saved as query from the Explorer
Tracked queries provide regular assessments of malware, phish, and other events with the scope defined from Threat Explorer. Tracked queries help monitor items frequently, providing reports, allowing quick and in-depth evaluation of threats or groups. A limited number of tracked queries are available for each organization. Admins can choose to convert saved queries and begin tracking them using the edit option for that query.
These ‘Threat Trackers’ enrich the admin experience, providing a powerful new tool for monitoring and managing, investigations, which ultimately enables quick response to threats. With this added feature, Office 365 Threat Intelligence provides admins to more efficiently and easily secure their organization.
Send Us Your Feedback
Let us know what you think of the new Threat trackers feature by beginning an Office 365 E5 trial today to experience the powerful capabilities of Office 365 Threat Intelligence. Your feedback enables us to make updates and enhancements to provide you with the best protection for Office 365. Please watch our recent webinar on Office 365 Threat Intelligence to learn further details on how the service can help your organization become more secure.
Today is the enforcement date of the EU’s General Data Protection Regulation (GDPR), which establishes an important milestone for individual privacy rights. Microsoft has been a strong supporter of the GDPR since it was first proposed in 2012. The GDPR sets a strong standard for privacy because it puts people in control of their own data.
In this post, we summarize the resources on the Service Trust Portal that can help you with GDPR readiness when using Microsoft Cloud services.
Service Trust Portal – Get in-depth information to help you meet GDPR obligations
The Privacy area on Service Trust Portal provides GDPR resources across Microsoft Cloud services, including Office 365, Azure, Dynamics 365, Windows, and Professional Services. You can find 3 primary topics under the Privacy tab:
- Data Subject Requests (DSRs): get information about how specific Microsoft Cloud services enable you to discover, access, rectify, restrict, delete, and export personal data; connect you to the DSRs tools Microsoft builds to help you respond to DSRs (e.g. Data Log Export for responding to telemetry log DSRs).
- Data breach notification: find information about how Microsoft detects and responds to personal data breaches, and how you can set up your privacy contact to receive breach notifications from Microsoft in the event of personal data breach.
- Data Protection Impact Assessments (DPIAs): learn about Microsoft’s and your responsibilities for DPIA compliance, and get information provided by Microsoft that can support you to create your own DPIAs.
Visit it today at https://aka.ms/GDPRGetStarted and learn more about how to use Service Trust Portal to plan and implement GDPR controls in this video:
Compliance Manager – Assess and improve your GDPR compliance posture
Compliance Manager is a cross-Microsoft-Cloud solution that helps organizations understand and manage the complex compliance landscape with 3 key capabilities:
- Ongoing risk assessment: gain visibility into Microsoft’s internal controls as well as your compliance performance and make better plans with Compliance Score.[1]
- Actionable insights: get guidance on implementing controls to increase your Compliance Score and enhance data protection capabilities.
- Simplified compliance: use the built-in dashboard, control management, and audit-ready reporting functions to assign, track, and record your compliance activities
GDPR assessments are now available in Compliance Manager for Azure, Dynamics 365, Office 365, and Microsoft Professional Services.[2] Check out Compliance Manager today at https://aka.ms/compliancemanager.
Watch this 2-min video, which summarizes the capabilities of Compliance Manager:
More Resources
You can find more resources about Service Trust Portal and Compliance Manager below:
[1] Compliance Manager is a dashboard that provides the Compliance Score and a summary of your data protection and compliance stature as well as recommendations to improve data protection and compliance. This is a recommendation, it is up to you to evaluate and validate the effectiveness of customer controls as per your regulatory environment. Recommendations from Compliance Manager and Compliance Score should not be interpreted as a guarantee of compliance.
[2] Note that Office 365 GCC customers can access Compliance Manager; however, users should evaluate whether to use the document upload feature of Compliance Manager, as the storage for document upload is compliant with Office 365 Tier C only. Compliance Manager is not yet available in sovereign clouds including Office 365 U.S. Government Community High (GCC High), Office 365 Department of Defense (DoD), Office 365 Operated by 21 Vianet, and Office 365 Germany.
Today is the enforcement date of the EU’s General Data Protection Regulation (GDPR), which establishes an important milestone for individual privacy rights. Microsoft has been a strong supporter of the GDPR since it was first proposed in 2012. The GDPR sets a strong standard for privacy because it puts people in control of their own data.
In this post, we summarize the resources on the Service Trust Portal that can help you with GDPR readiness when using Microsoft Cloud services.
Service Trust Portal – Get in-depth information to help you meet GDPR obligations
The Privacy area on Service Trust Portal provides GDPR resources across Microsoft Cloud services, including Office 365, Azure, Dynamics 365, Windows, and Professional Services. You can find 3 primary topics under the Privacy tab:
- Data Subject Requests (DSRs): get information about how specific Microsoft Cloud services enable you to discover, access, rectify, restrict, delete, and export personal data; connect you to the DSRs tools Microsoft builds to help you respond to DSRs (e.g. Data Log Export for responding to telemetry log DSRs).
- Data breach notification: find information about how Microsoft detects and responds to personal data breaches, and how you can set up your privacy contact to receive breach notifications from Microsoft in the event of personal data breach.
- Data Protection Impact Assessments (DPIAs): learn about Microsoft’s and your responsibilities for DPIA compliance, and get information provided by Microsoft that can support you to create your own DPIAs.
Visit it today at https://aka.ms/GDPRGetStarted and learn more about how to use Service Trust Portal to plan and implement GDPR controls in this video:
Compliance Manager – Assess and improve your GDPR compliance posture
Compliance Manager is a cross-Microsoft-Cloud solution that helps organizations understand and manage the complex compliance landscape with 3 key capabilities:
- Ongoing risk assessment: gain visibility into Microsoft’s internal controls as well as your compliance performance and make better plans with Compliance Score.[1]
- Actionable insights: get guidance on implementing controls to increase your Compliance Score and enhance data protection capabilities.
- Simplified compliance: use the built-in dashboard, control management, and audit-ready reporting functions to assign, track, and record your compliance activities
GDPR assessments are now available in Compliance Manager for Azure, Dynamics 365, Office 365, and Microsoft Professional Services.[2] Check out Compliance Manager today at https://aka.ms/compliancemanager.
Watch this 2-min video, which summarizes the capabilities of Compliance Manager:
More Resources
You can find more resources about Service Trust Portal and Compliance Manager below:
[1] Compliance Manager is a dashboard that provides the Compliance Score and a summary of your data protection and compliance stature as well as recommendations to improve data protection and compliance. This is a recommendation, it is up to you to evaluate and validate the effectiveness of customer controls as per your regulatory environment. Recommendations from Compliance Manager and Compliance Score should not be interpreted as a guarantee of compliance.
[2] Note that Office 365 GCC customers can access Compliance Manager; however, users should evaluate whether to use the document upload feature of Compliance Manager, as the storage for document upload is compliant with Office 365 Tier C only. Compliance Manager is not yet available in sovereign clouds including Office 365 U.S. Government Community High (GCC High), Office 365 Department of Defense (DoD), Office 365 Operated by 21 Vianet, and Office 365 Germany.
Today is the enforcement date of the EU’s General Data Protection Regulation (GDPR), which establishes an important milestone for individual privacy rights. Microsoft has been a strong supporter of the GDPR since it was first proposed in 2012. The GDPR sets a strong standard for privacy because it puts people in control of their own data.
In this post, we summarize the resources on the Service Trust Portal that can help you with GDPR readiness when using Microsoft Cloud services.
Service Trust Portal – Get in-depth information to help you meet GDPR obligations
The Privacy area on Service Trust Portal provides GDPR resources across Microsoft Cloud services, including Office 365, Azure, Dynamics 365, Windows, and Professional Services. You can find 3 primary topics under the Privacy tab:
- Data Subject Requests (DSRs): get information about how specific Microsoft Cloud services enable you to discover, access, rectify, restrict, delete, and export personal data; connect you to the DSRs tools Microsoft builds to help you respond to DSRs (e.g. Data Log Export for responding to telemetry log DSRs).
- Data breach notification: find information about how Microsoft detects and responds to personal data breaches, and how you can set up your privacy contact to receive breach notifications from Microsoft in the event of personal data breach.
- Data Protection Impact Assessments (DPIAs): learn about Microsoft’s and your responsibilities for DPIA compliance, and get information provided by Microsoft that can support you to create your own DPIAs.
Visit it today at https://aka.ms/GDPRGetStarted and learn more about how to use Service Trust Portal to plan and implement GDPR controls in this video:
Compliance Manager – Assess and improve your GDPR compliance posture
Compliance Manager is a cross-Microsoft-Cloud solution that helps organizations understand and manage the complex compliance landscape with 3 key capabilities:
- Ongoing risk assessment: gain visibility into Microsoft’s internal controls as well as your compliance performance and make better plans with Compliance Score.[1]
- Actionable insights: get guidance on implementing controls to increase your Compliance Score and enhance data protection capabilities.
- Simplified compliance: use the built-in dashboard, control management, and audit-ready reporting functions to assign, track, and record your compliance activities
GDPR assessments are now available in Compliance Manager for Azure, Dynamics 365, Office 365, and Microsoft Professional Services.[2] Check out Compliance Manager today at https://aka.ms/compliancemanager.
Watch this 2-min video, which summarizes the capabilities of Compliance Manager:
More Resources
You can find more resources about Service Trust Portal and Compliance Manager below:
[1] Compliance Manager is a dashboard that provides the Compliance Score and a summary of your data protection and compliance stature as well as recommendations to improve data protection and compliance. This is a recommendation, it is up to you to evaluate and validate the effectiveness of customer controls as per your regulatory environment. Recommendations from Compliance Manager and Compliance Score should not be interpreted as a guarantee of compliance.
[2] Note that Office 365 GCC customers can access Compliance Manager; however, users should evaluate whether to use the document upload feature of Compliance Manager, as the storage for document upload is compliant with Office 365 Tier C only. Compliance Manager is not yet available in sovereign clouds including Office 365 U.S. Government Community High (GCC High), Office 365 Department of Defense (DoD), Office 365 Operated by 21 Vianet, and Office 365 Germany.
Today is the enforcement date of the EU’s General Data Protection Regulation (GDPR), which establishes an important milestone for individual privacy rights. Microsoft has been a strong supporter of the GDPR since it was first proposed in 2012. The GDPR sets a strong standard for privacy because it puts people in control of their own data.
In this post, we summarize the resources on the Service Trust Portal that can help you with GDPR readiness when using Microsoft Cloud services.
Service Trust Portal – Get in-depth information to help you meet GDPR obligations
The Privacy area on Service Trust Portal provides GDPR resources across Microsoft Cloud services, including Office 365, Azure, Dynamics 365, Windows, and Professional Services. You can find 3 primary topics under the Privacy tab:
- Data Subject Requests (DSRs): get information about how specific Microsoft Cloud services enable you to discover, access, rectify, restrict, delete, and export personal data; connect you to the DSRs tools Microsoft builds to help you respond to DSRs (e.g. Data Log Export for responding to telemetry log DSRs).
- Data breach notification: find information about how Microsoft detects and responds to personal data breaches, and how you can set up your privacy contact to receive breach notifications from Microsoft in the event of personal data breach.
- Data Protection Impact Assessments (DPIAs): learn about Microsoft’s and your responsibilities for DPIA compliance, and get information provided by Microsoft that can support you to create your own DPIAs.
Visit it today at https://aka.ms/GDPRGetStarted and learn more about how to use Service Trust Portal to plan and implement GDPR controls in this video:
Compliance Manager – Assess and improve your GDPR compliance posture
Compliance Manager is a cross-Microsoft-Cloud solution that helps organizations understand and manage the complex compliance landscape with 3 key capabilities:
- Ongoing risk assessment: gain visibility into Microsoft’s internal controls as well as your compliance performance and make better plans with Compliance Score.[1]
- Actionable insights: get guidance on implementing controls to increase your Compliance Score and enhance data protection capabilities.
- Simplified compliance: use the built-in dashboard, control management, and audit-ready reporting functions to assign, track, and record your compliance activities
GDPR assessments are now available in Compliance Manager for Azure, Dynamics 365, Office 365, and Microsoft Professional Services.[2] Check out Compliance Manager today at https://aka.ms/compliancemanager.
Watch this 2-min video, which summarizes the capabilities of Compliance Manager:
More Resources
You can find more resources about Service Trust Portal and Compliance Manager below:
[1] Compliance Manager is a dashboard that provides the Compliance Score and a summary of your data protection and compliance stature as well as recommendations to improve data protection and compliance. This is a recommendation, it is up to you to evaluate and validate the effectiveness of customer controls as per your regulatory environment. Recommendations from Compliance Manager and Compliance Score should not be interpreted as a guarantee of compliance.
[2] Note that Office 365 GCC customers can access Compliance Manager; however, users should evaluate whether to use the document upload feature of Compliance Manager, as the storage for document upload is compliant with Office 365 Tier C only. Compliance Manager is not yet available in sovereign clouds including Office 365 U.S. Government Community High (GCC High), Office 365 Department of Defense (DoD), Office 365 Operated by 21 Vianet, and Office 365 Germany.


























