-
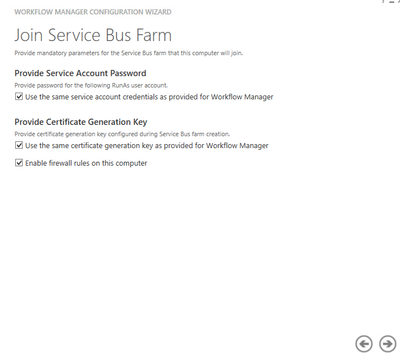
Below are the steps for a 1 Node WFM farm using WFM/SB certificate generation key – resetting expired certificate process:
First, some quick notes:
- NOTE: Ensure you have credentials for WFM Run-As service account and WFM passphrase for generated certificate.
- NOTE: If you have a 3 node WFM farm, then you will need to have WFM2 and WFM3 leave the WFM farm once you have changed the system date and time for all 3 nodes and then run Workflow Manager Configuration Wizard to leave farm.
- NOTE: If the WFM passphrase is not known, step 6 will allow you to change WFM passphrase as long as you are part of the WFM farm
- NOTE: If you are running CA-Cert, you’ll follow the same process to change system date and time, and then follow below article to change to new certificate thumbprints – note new certificate requires to be created prior to expiration date: https://blogs.msdn.microsoft.com/whereismysolution/2017/02/08/changing-my-workflow-manager-farm-certificates/
-
- In order to reset generation key for WFM and SB the following steps needs to be done on the WFM node(s): System date and clock of WFM node must be set back before certificate expiration date (step needs to be done if multiple WFM nodes in farm)
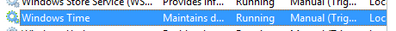
- Stop Windows Time Service

- Change System date and clock to Day before certificate expired (in this example, the cert expired on November 21st, 2024)
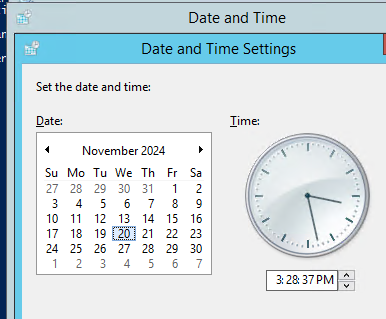
- Steps to follow once System date and time has been set prior to expiration date:
- Output workflow manager PowerShell commands to clipboard and paste to notepad:
TIP: Use “|clip” parameter to output results to clipboard and then paste to notepad
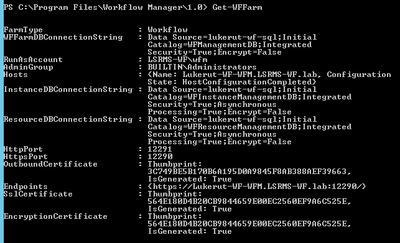
- Get-WFFarm | clip
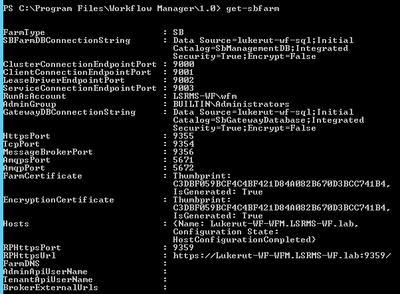
- Get-SBFarm | clip
- Get-SBNamespace |clip
- NOTE: The “Get-SBNamespace” command will list ManageUser accounts – one of those accounts should be the logon credentials used. Account should have the required SQL permissions to reset expired certificates.

- Run below commands (after reverting the date and time, all services should display as “Running” before proceeding to next steps:
- Get-WFFarmStatus

- Get-SBFarmStatus – There are scenarios where Service Bus Message Broker service will get stuck at “Starting”, regardless continue to next step

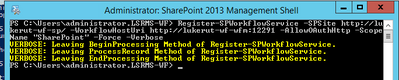
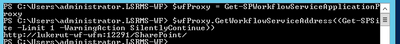
- From Administrative SharePoint Management Shell, run below command to get current WorkflowHostURI used to register WFM to SharePoint:
- $wfProxy = Get-SPWorkflowServiceApplicationProxy
$wfProxy.GetWorkflowServiceAddress((Get-SPSite -Limit 1 -WarningAction SilentlyContinue))
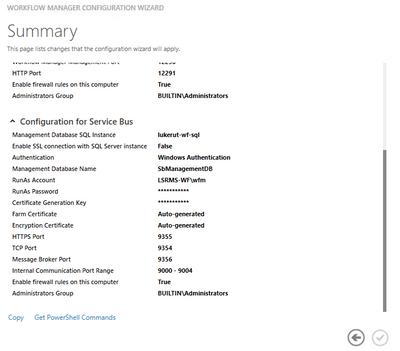
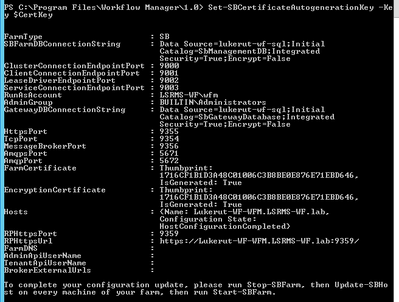
- Run below WFM PowerShell command to change passphrase and thumbprints:
- Run these commands to set the Certificate keys:
- $CertKey=convertto-securestring ‘PASSPHRASE’ -asplaintext -force;
Set-WFCertificateAutoGenerationKey –Key $CertKey
Set-SBCertificateAutogenerationKey –Key $CertKey

- Then run the below commands:
- Stop-SBFarm
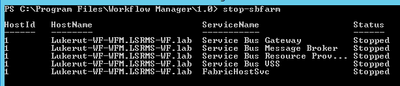
- Update-SBHost

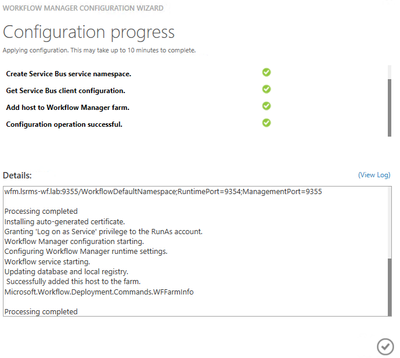
- Run Workflow Manager Configuration Wizard – we’ll leave WFM farm first and then rejoin WFM farm. This step is necessary, as when we rejoin the WFM farm later, it will create the new WFOutboundCertificate for us.
- Enable Windows Time Service – this will automatically change server back to current date and time

- Follow the steps from this article: SharePoint 2016: Step by Step guide to add Workflow Manager Certificate into SharePoint trust (Also install to Trusted Root store)
- Export WFM Client certificate using below command from Workflow Manager Powershell: Get-WFAutoGeneratedCA
- Above command creates “AutoGeneratedCA.cer” file in path where command was executed – default C:Program FilesWorkFlow Manager1.0

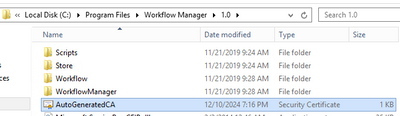
- Copy “AutoGeneratedCA.cer” file to all SP nodes and Web Frontends – install certificate to Trusted Root Certification Authorities certificate store
- Copy the file to the SharePoint server(s)
- Right-click, and select Install Certificate
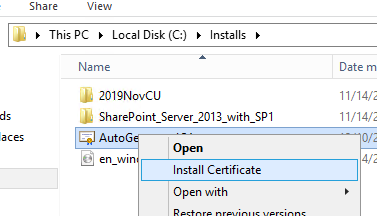
- Select “Local Machine” and click Next

- Select “Place all certificates in the following store”, and then choose “Trusted Root Certification Authorities”, and then choose OK, and NEXT, then FINISH
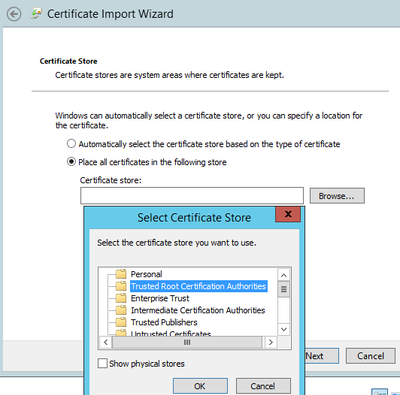
- Choose OK to complete
- Repeat on each SP server
- Repeat same process on each SP server for the certificate that was trusted into SharePoint Manage Trusts earlier during Step 7.
- Reset IIS on all SP WFEs
- Register WFM to SharePoint
- Sample command:
- From SharePoint Central Admin, run daily timer “Refresh Trusted Security Token Services Metadata feed [Farm job – Daily]”
- $tj = Get-SPTimerJob RefreshMetadataFeed
$tj.RunNow()
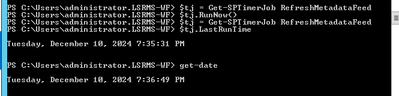
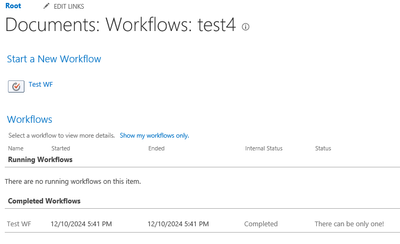
- Test one of your 2013 workflows now, and it should complete successfully
Contents
- What is SSL Offloading
- Configuring SSL Offloading with SharePoint
- Web Applications
- Host Names Site Collections
- SharePoint Apps (App Domain
- Common Issues
- URLs returned to users are incorrect
- List or library Dropdown menu not loading
- After configuring SSL offloading for a web application users receive a 404 or 503
- Additional Information
- Creating IIS bindings for SharePoint Web Applications through PowerShell
What is SSL Offloading?
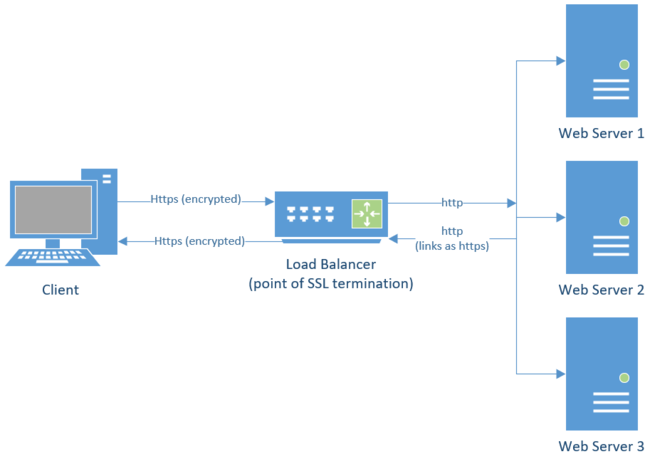
The idea behind SSL offloading is to reduce the load on web servers as well as the administrative overhead of managing SSL certificates across multiple servers. This is accomplished by using a dedicated network device (often times a network load balancer or a proxy server) to terminate SSL as it routes the requests. This removes the burden of decrypting and encrypting https traffic from the web server as well as providing a single location to host the SSL certificate reducing administrative efforts of maintaining and replacing certificates.
What it looks like:
 SharePoint SSL Offloading Request
SharePoint SSL Offloading Request
- The user makes an https request for a webpage that is routed to the load balancer
- The load balancer terminates SSL and sends the unencrypted http request to the web server
- The Web server handles the request and returns an unencrypted http response to the load balancer
- The load balancer encrypts the request and forwards it to the client that made the original request as https
Configuring SSL Offloading with SharePoint
Web Applications
To configure a SharePoint web application to take advantage of SSL offloading the Alternate Access Mappings must be configured in a specific way that allows the request to be accepted as http but have links rendered as https. By using internal URLs we can tell SharePoint to recognize an incoming request to http://sharepoint and handle it as though it were https:/sharepoint. Below illustrates how Alternate Access Mappings should be configured to allow for SSL offloading to occur. Note that the internal URL should match the traffic between the load balancer and SharePoint while the public url should reflect what URL users think they are using.
If you are creating a new web application to be used with SSL offloading use the below settings as a guide to create it.
If you are configuring an existing HTTPS Web Application for SSL offloading add an internal URL using the same hostname over http to the zone they wish to use SSL offloading with. The end result should look like the example below. To add these you will want to go to Central Administration > Application Management > Configure Alternate Access Mappings > Add Internal URLs.
|
Zone
|
Internal Url
|
Public Url
|
|
Default
|
https://sharepoint
|
https://sharepoint
|
|
http://sharepoint
|
https://sharepoint
|
Host Names Site Collections
In path based sites we can utilize a combination of internal and public URLs in the web app’s AAMs to achieve the redirection that we need. While we do have multiple zones for HNSCs we do not have the same functionality that internal and public URLs provide. As such the configuration for HNSCs is different as described below.
Web Application Configuration
- The web application should be configured the same way as seen above except the host header should remain empty
- HNSC should be created using an https URL
Example:
New-SPSite 'https://portal.fabrikam.com' -HostHeaderWebApplication 'https://sharepoint.contoso.com' -Name 'Portal' -OwnerAlias 'contosoadministrator' -Language 1033 -Template 'STS#0'
- Bindings for the backing IIS site should include an http binding with a blank host-header if not already present
Proxy or Load Balancer Configuration
Since we cannot use internal URLs like we would for a path based site collections we must configure the proxy server or load balancer that is serving as the point of SSL/TLS termination to add an additional header to the web requests. The header Front-End-Https tells SharePoint whether the links that it renders for this web request should be rendered as http or https.
|
Front-End-Https
|
|
Value
|
Description
|
|
On
|
The request made by the end user was made over https
Example: Front-End-Https: On
|
|
Off
|
The request made by the end user was made over http
|
Public Content: Use host-named site collections with off-box SSL termination
SharePoint Apps (App Domain)
When attempting to configure SSL offloading for app domains you may see the below error:
03/05/2015 09:13:34.20 w3wp.exe (0x0XXX) 0x0XXX SharePoint Foundation General aiz2a High Request for app scheme does not match the webapp’s scheme for this zone. Request Uri: http://app-XXXXXXXXX.apps.contoso.com…. Zone Response Uri: https://sharepoint.contoso.com Site collection path: /
To allow requests between web applications and app domains to be handled under different protocol schemes (http and https) as you would see when configuring SSL offloading for both web apps and app domains run the below PowerShell to enable support for multiple app domains.
$contentService = [Microsoft.SharePoint.Administration.SPWebService]::ContentService
$contentService.SupportMultipleAppDomains = $true
$contentService.Update()
Public Content: Configure an environment for apps for SharePoint (SharePoint 2013)
Common Issues
URLs returned to users are incorrect
When an environment with SSL offloading is not configured correctly it is not uncommon to see the URL in link rendered by SharePoint such as navigation to be incorrect. I.e. all links are rendered in http instead of https or in some scenarios even a different host name. This is most commonly caused by the configuration of alternate access mappings.
Document the following:
- The address and protocol that the users utilize to access the site.
- The address and protocol that the load balancer (or point of SSL termination) forwards the request as. It is possible that the hostname could differ as well as the protocol.
With the answers to the above ensure that the alternate access mappings for the web application are configured as seen below where the numbers coordinate to the responses from the above:
- Public url matches url that users utilize.
- Internal url matches url of incoming requests from the load balancer, if it is not present click Add Internal URLs on the Configure Alternate Access Mappings page in Central Administration.
List or library Dropdown menu not loading
This can be a problem when the site is accessed via Azure Application Proxy. See https://internal.support.services.microsoft.com/en-us/help/4459184
After configuring SSL offloading for a web application users receive a 404 or 503
This most often is due to the bindings in IIS. Locate the IIS site behind this zone of the web application.
To modify the bindings of an IIS website:
- Open Internet Information Services (IIS) Manager from Start > Administrative Tools
- Expand the server name in the Connections pane
- Expand Sites
- Right click on the site that should be serving the requests for the SharePoint Web Application in question
- Ensure that there is both an https as well as an http binding for the hostname that will be accessed as seen in the image below
Additional Information
Creating IIS bindings for SharePoint Web Applications through PowerShell
While you can add bindings to the SPWebApplication.IisSettings.ServerBindings array through PowerShell do note that this does not propagate to the existing IIS sites. This will however create the bindings when the SharePoint Foundation Web Application service is started on a server. As such any new server added to the farm, or any server where the web application service is started/restarted the bindings added through the below method will be reflected.
Add-PSSnapin Microsoft.SharePoint.PowerShell
$wa = Get-SPWebApplication ‘http://sharepoint.contoso.com’
$binding = New-Object Microsoft.SharePoint.Administration.SPServerBinding
$binding.Port = 80
$binding.HostHeader = “”
#Note the “Default” below references the zone of the web application, if you wish to add a binding to a different zone replace that with the appropriate zone (Default/Intranet/Internet/Extranet/Custom).
$iis = $wa.IisSettings[“Default”]
$iis.ServerBindings.Add($binding)
$wa.Update()
#Call the provision method to push this out to all servers, note that this will overwrite any manual modifications to the web.config or other manual changes within IIS for this web app.
$wa.ProvisionGlobally()
Special thanks to the original author: Ian Ragusa (Microsoft PFE)

In this episode, Vesa and Waldek are joined by Luise Freese – MVP – Microsoft 365 business consultant/Maker. Their inspiring conversation touches on impostering, inclusion, mind mapping, functional drawing, practice, facilitation, less code & more power, and planned chaos. If you’re feeling like an under-qualified topic expert – 1) you are human, 2) you will enjoy this discussion along with the articles.
This episode was recorded on Monday, February 17, 2020

In this episode, Vesa and Waldek are joined by Sébastien “Seb” Levert, Product Lead and MVP managing product strategy at Valo Intranet in Montreal, Canada. The conversation focused on the convergence of portals and collaboration platforms. Teams is becoming the primary work environment through which LOB apps, communications, BOTs, SharePoint, etc., are being accessed. Valo follows a Teams First development approach. The challenge is creating the tailored/personalized landing page in Teams without the same controls that are available in SharePoint. Other trends discussed – clickable BOT actions, Teams left nav, building personal apps using SPFx, enterprise provisioning and “proper snow.”
This episode was recorded on Monday, February 11, 2020


Latest monthly summary of SharePoint Development guidance for SharePoint Online and on-premises is now available from the SharePoint Dev Blog. Check the latest news, samples and other guidance from this summary.
SharePoint in Microsoft 365 is continuously evolving and improving, especially in areas where Microsoft can refine the first-run experience and guide people to the best use and adoption of the technology that supports their day to day.
Today, we expand the in-product help that appears at the top-right of your SharePoint team sites – to make people’s first SharePoint experiences with sites that much easier and actionable. This is especially true for those who help manage sites and train people at scale within your organization. The question is, how do you get the most out of SharePoint and other integrated apps today? How do you ensure a great first-run experience for your people? What is the next step?
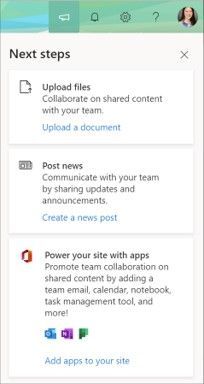
 SharePoint Next steps appear when you click on the megaphone icon in the upper-right of the site.
SharePoint Next steps appear when you click on the megaphone icon in the upper-right of the site.
The answer lies in two options: one “self-service” approach and one “at-scale” method:
- Self-service | people click Next steps and choose from the suggested tips to improve teamwork collaboration.
- At-scale | SharePoint admins perform bulk operations across multiple SharePoint sites at once
No matter which option you choose, your site(s) get improved list and library experiences, an updated home page, and mobile readiness. You, too, can the added benefit from other integrated apps such as Planner and Outlook; this process is often referred to as “groupify” as it begins with adding a new Office 365 Groups membership. Updated sites then present helpful, first-run experiences to guide people through the upload of their first set of files, posting news articles for other team members, and adding others as new members.
And with one additional, sequential step you add a Microsoft Teams team as an additional app for your team members to bring communication alongside content; this is sometimes referred to as “teamify” as you are adding a Microsoft Teams team to your team site; yes, a mouth full, but well worth using beyond saying.
Let’s dive into the details of both options …
Self-service “Next steps” tips improve SharePoint site first-run experiences
We’re expanding the in-product help that appears at the top-right of your SharePoint team sites. More and more, SharePoint in Microsoft 365 helps people get the most value from new sites by providing contextual, actionable help. And today, we’re pleased to announce the expansion and location of the Next steps panel.
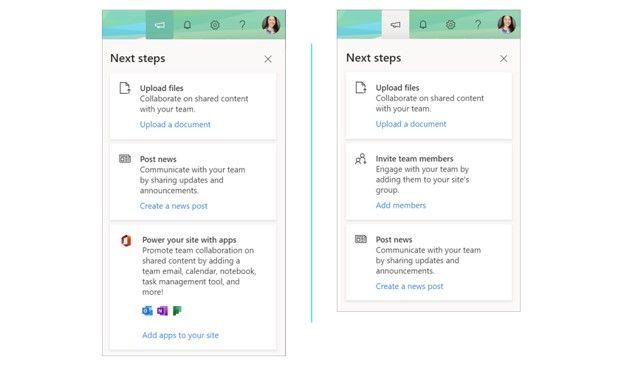 Left-to-right: “Next steps” showing from a classic team site and “Next steps” showing from a group-connected team site. Simply click on the megaphone icon to bring up “Next steps” tips from the Office 365 suite header at the top of the SharePoint site.
Left-to-right: “Next steps” showing from a classic team site and “Next steps” showing from a group-connected team site. Simply click on the megaphone icon to bring up “Next steps” tips from the Office 365 suite header at the top of the SharePoint site.
The SharePoint site “Next steps” panel provides helps for a great first-run experience. All to help you move forward as a team and work out-loud and with confidence and awareness on how everything works in and around your SharePoint site interaction.
Currently there are four tips (cards) site members and owners may see within the Next steps panel:
- Upload files – Collaborate on shared content with your team; encourages people to Upload a document.
- Post news – Communicate with your team by sharing updates and announcements; helps Create a news post the first few times.
- Invite team members – Engage with your team by adding them to your site’s group; makes it easier to see how to Add members.
- Power your site with apps – Promote team collaboration on shared content by adding a team email, calendar, notebook, task management tool, and more; integrates additional capabilities when you Add apps to your site. #groupify
These tips help your users customize and improve their team sites. Tips are useful for anyone learning more about SharePoint or setting up a new team site for the first time.
Note: the “Power your site with apps” card will appear only on classic SharePoint team site that have not yet connected to a new Office 365 Groups group. Once this update has run, that option will no longer appear for that team site and the additional “Invite team members” may then appear.
For clarity, we also wanted to take a moment to highlight the other four top-right icons you will see above and to the right of your site – next to Next Steps:
- Notifications – people will see various alerts from across Microsoft 365 services based on their notification’s preferences.
- Settings – this gives access to deeper level site settings, like Site contents, Site information, Site usage and more.
- Help – this pulls in contextual “how to” information from support.office.com
- Your Office profile – where you can be you and adjust your account settings and Office profile.
Note: “Connect site to a new Office 365 group” may still appear in upper-right gear icon. This is the same as the new “Power your site with apps” Next steps card.
Learn more how to connect your SharePoint team site to a new Office 365 group.
At-scale, SharePoint admins plan and move multiple sites to modern experiences
Beyond individual site owners being able to connect to new Office 365 Groups from either the new Next steps action described above, it’s important to note that SharePoint admins can do this at scale using bulk operations across numerous sites deemed ready for modernization.
You can perform a bulk operation (known as a group-connection) in which you connect an Office 365 group to a series of sites at one time. This option is preferred for enterprise customers because it enables you to control the configuration (public/private, site classification, alias name) – and save time doing it on behalf of people and sites that qualify and request it.
Below are the two main steps to plan and execute the move to the latest SharePoint and Office 365 Groups experiences at scale:
FIRST | Use the Modernization Scanner tool to better understand classic SharePoint sites and the available capabilities to modernize them. The tool provides factual data about optimizing lists and libraries, connecting to Office 365 Groups, rebuilding classic publishing portals, workflow, blogs and more. Using the dashboards generated by the scanner you’ll be able to better assess the readiness of your sites and plan moving forward and any suggested remediation guidance.
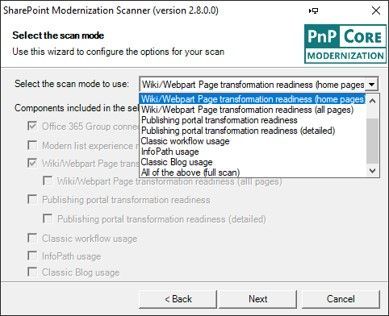 Select the SharePoint Modernization Scanner option you want in the dropdown and then the checkboxes will show which components will be included in the scan. The “Office 365 Group connection readiness” component is the main component that will be included all scan modes.
Select the SharePoint Modernization Scanner option you want in the dropdown and then the checkboxes will show which components will be included in the scan. The “Office 365 Group connection readiness” component is the main component that will be included all scan modes.
Select the SharePoint Modernization Scanner option you want in the dropdown and then the checkboxes will show which components will be included in the scan. The “Office 365 Group connection readiness” component is the main component that will be included all scan modes.
Learn how to get started with the SharePoint modernization scanner. And then download the SharePoint Modernization Scanner and try it today.
SECOND | Programmatically modernize your sites using a CSV files and bulk group-connect PowerShell script. After running the scanner and processing the results, you have identified which sites are ready to group-connect. The next step is to prepare a CSV file to drive the bulk group-connection process.
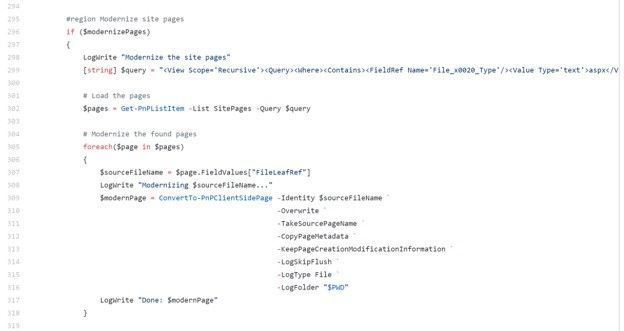 Section of the sample PowerShell script to modernize SharePoint pages.
Section of the sample PowerShell script to modernize SharePoint pages.
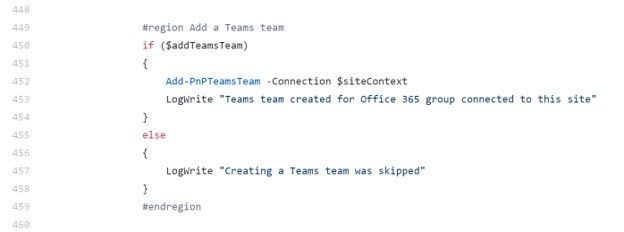 Section of the sample PowerShell script to create a new Microsoft Teams team and associated it to the SharePoint site.
Section of the sample PowerShell script to create a new Microsoft Teams team and associated it to the SharePoint site.
As you move through the options of what you can do, note you’ll be able to:
- Add a Microsoft Teams team to each SharePoint site
- Modernize all the pages within each site
- Clean up site branding
- Apply a tenant theme to each site
Learn how to connect new Office 365 groups to across multiple sites at once (includes sample PowerShell script); this, too contains a best practices guide to managing SharePoint modernization projects.
Wrapping it up…
We recently spoke to Nicole Woon (Twitter | LinkedIn), a program manager at Microsoft. She helped update the above-mentioned “Next Steps” experience for SharePoint sites. In the podcast episode, I interview Nicole about this new feature update and dig into the design, customer use and future action cards that help customers have a great first-run experience with SharePoint sites:
You, too, can learn from the person behind the modernization tool, Bert Jansen (Twitter | LinkedIn), as he shares how to get started transforming classic SharePoint sites to modern experiences using the admin patterns, practices and tools mentioned above:
We hope you enjoy not only the move to more modern experiences, but improved ways to support your growth and engagement throughout your organization.
What is the next step? Click Next steps and see.
Thanks, Mark Kashman – senior product manager – Microsoft
![Microsoft Graph Security API add-on is now available for Splunk Cloud!]()
The Microsoft Graph Security API add-on for Splunk is now supported on Splunk Cloud, in addition to Splunk Enterprise, and includes support for Python 3.0. The support is enabled as an enhancement to the Microsoft Graph Security API add-on for Splunk released last year. Refer to the Microsoft Graph Security API add-on for Splunk announcement blogpost for further details. This add-on enables customers to easily integrate security alerts and insights from their security products, services, and partners in Splunk. The Splunk add-on is built by Microsoft, certified by Splunk, and is available on Splunkbase at no additional cost.
This add-on, powered by the Microsoft Graph Security API, supports streaming of alerts from different Microsoft solutions like Microsoft Defender ATP, Azure Sentinel, Azure Security Center, and more into Splunk using a single add-on and common schema, enabling easier correlation of data across these products.
Note: If you have an earlier version of the Microsoft Graph Security API add-on installed on Splunk Enterprise, and upgrade to this version, please follow the upgrade guidance to reconfigure your inputs.
Getting Started
Choose one of these options depending on your scenario.
Scenario: New Installations on Splunk Cloud or Splunk Enterprise
Follow these steps to install and configure this app as a first-time add-on user. Refer to the documentation for more details.
- Register your application for this Splunk add-on on Azure portal.
- Configure permissions and be sure to add the SecurityEvents.Read.All permission to your application. Get your Azure AD tenant administrator to grant tenant administrator consent to your application. This is a one-time activity unless permissions change for the application.
- Copy and save your registered Application ID and Directory ID from the Overview page. You will need them later to complete the add-on configuration process.
- Generate an application secret by going to Certificates & secrets Save the generated secret as well for add-on configuration purposes.
- In Splunk, click on Find More Apps to browse more apps.
- Search for Microsoft Graph Security as shown below (the picture below is on Splunk Cloud).
 Find the add-on
Find the add-on
- Installation of the add-on
- For Splunk Enterprise – Install Microsoft Graph Security API add-on for Splunk. Restart, if prompted to do so.
- For Splunk Cloud – This add-on requires an Inputs Data Manager (IDM) on Splunk Cloud. Contact Splunk Cloud support per the Splunk Cloud IDM installation guidance.
- Verify that the add-on appears in the list of apps and add-ons as shown in the diagram below.
 Add-on installed
Add-on installed
- Set up a new account in the Account tab in the Configuration page. Then click Add to create an account.
- Enter a unique Account Name, the Application ID and Client Secret registered in abovementioned steps 1 through 4 as shown in the diagram below.
 Add account
Add account
- Configure Microsoft Graph Security data inputs illustrated in the diagram below as per the detailed guidance in the section Configuring Microsoft Graph Security data input. This add-on provides the capability to pre-filter your data by specific alert providers or by alert category or severity, etc. by specifying the OData Filter field as shown in the diagram below.
 Add input
Add input
- Now you can use your Microsoft Graph Security alerts for further processing in Splunk, in dashboards, etc.
If you have Splunk and relevant add-ons running behind a proxy server, follow the additional steps for Splunk behind a Proxy Server in the installation documentation for this add-on. For specific guidance on distributed set up, follow the steps in Where to Install the add-on in the installation documentation for this add-on
Scenario: Upgrade on Splunk Enterprise
If you have an existing version of the add-on installed on Splunk Enterprise that is lower than this version (1.1.0), the best practice recommended is to remove your older version of the Microsoft Graph Security API add-on for Splunk before re-installing version 1.1.0 of the Microsoft Graph Security API add-on for Splunk per abovementioned guidelines.
If you are upgrading on Splunk Enterprise, follow these steps.
- Disable all your inputs before you upgrade the add-on. Otherwise you may see errors in the log files which may result data loss against your already configured inputs.
- On the app list, navigate to the Microsoft Graph Security add-on for Splunk, to see an option to upgrade the app. Click on Update button.
- A new screen appears with the standard Splunk Terms to upgrade an app. Click Accept and Continue.
 Splunk terms
Splunk terms
-
Enter your username and password to log in the app. Click Login and Continue.  Login and continue
Login and continue
- After login, an Overview page appears, and the Update button disappears. Follow the instructions in the Configuring Microsoft Graph Security data inputs section in the installation documentation for this add-on to get alerts from Microsoft Graph Security API using the new configuration experience
Closing
We would love your continued feedback on this add-on. Please share your feedback by filing a GitHub issue.

In this session of SharePoint Dev Weekly, hosts – Vesa Juvonen (Microsoft), Waldek Mastykarz (Rencore), and typically a special guest from the SharePoint PnP Community, discuss the latest news and topics around SharePoint development.
In this episode, Vesa and Waldek are joined by Agnes Molnar, owner of Search Explained based in Budapest, delivering consulting and training services worldwide. In addition to drawing attention to the recent advancements being delivered by the SharePoint Community and Microsoft, Vesa, Waldek and Agnes’ discussion this week centered on why search is again cool.
This episode was recorded on Monday, February 3, 2020.


2020 is officially here and we are ready to help you understand and master all the possibilities that are available in the new modern SharePoint. If you haven’t had a chance to sign up for our hands-on Intelligent Intranet Accelerator Workshop yet, now is your chance.
We have a team of enthusiastic SharePoint, One Drive, Yammer and Stream experts traveling the globe in 2020. From half-day workshops to multiple day shows with breakouts and hands on training, the team is ready! No matter where you are in the world, we will be close by to help you discover the art of the possible with Microsoft and SharePoint technologies. Come see the team at an event near you!
February 2020
February 7 – The Intelligent Intranet Accelerator Workshop- Featured as part of Microsoft Ignite The Tour, Washington DC
As part of Microsoft Ignite The Tour, the Microsoft Intelligent Intranet Accelerator Workshop will bring a deeply technical and immersive hands-on experience where you will build real-world applications to connect, succeed, and engage – faster. You will enjoy a plethora of keynotes, breakout sessions and one-on-one networking opportunities. This free event provides technical training led by Microsoft experts and your community. You’ll learn new ways to build solutions, migrate and manage infrastructure, and connect with local industry leaders and peers.
Register Today!
February 11 – The Intelligent Intranet Accelerator Workshop- Featured as part of Microsoft Ignite The Tour, Dubai
The Microsoft Intelligent Intranet Accelerator Workshop is a hands-on session within Microsoft Ignite The Tour in this location. By registering, you’ll receive instant access to not only the Microsoft Intelligent Intranet Accelerator Workshop, but also the free 2-day Microsoft Ignite The Tour.
Register Today!
February 12 – The Intelligent Intranet Accelerator Workshop – Hosted at the Microsoft Offices in Sydney, Australia
Get inspired with the art of the possible at the FREE Microsoft Intelligent Intranet Accelerator Workshop. Complete the registration today and reserve your spot in your city. By attending the workshop, you’ll walk away with the tools and capabilities necessary to accelerate your time-to-value.
Register today!
February 18 – The Intelligent Intranet Accelerator Workshop- Featured as part of SPTechCon San Francisco 2020
Featured as a part of SPTechCon San Francisco 2020, the Microsoft Intelligent Intranet Accelerator Workshop will bring a deeply technical and immersive hands-on experience where you will build real-world applications to connect, succeed, and engage – faster.
Register today!
February 21 – The Intelligent Intranet Accelerator Workshop- Featured as part of Microsoft Ignite The Tour Singapore
The Microsoft Intelligent Intranet Accelerator Workshop is a hands-on session within Microsoft Ignite The Tour in this location. By registering today, you’ll receive instant access to not only the Microsoft Intelligent Intranet Accelerator Workshop, but also the free 2-day Microsoft Ignite The Tour. You will enjoy a plethora of keynotes, breakout sessions and one-on-one networking opportunities. This free tour provides technical training led by Microsoft experts and your community. You’ll learn new ways to build solutions, migrate and manage infrastructure, and connect with local industry leaders and peers.
Register today!
February 28 – The Intelligent Intranet Accelerator Workshop- Featured as part of Microsoft Ignite The Tour, Copenhagen
As part of Microsoft Ignite The Tour, the Microsoft Intelligent Intranet Accelerator Workshop will bring a deeply technical and immersive hands-on experience where you will build real-world applications to connect, succeed, and engage – faster. You’ll learn new ways to build solutions, migrate and manage infrastructure, and connect with local industry leaders and peers.
Register today!
March 2020
March 10 – The Intelligent Intranet Accelerator Workshop – Hosted at the Microsoft Offices in Amsterdam
Get inspired with the art of the possible at the FREE Microsoft Intelligent Intranet Accelerator Workshop. Complete the registration today and reserve your spot in your city. By attending the workshop, you’ll walk away with the tools and capabilities necessary to accelerate your time-to-value.
Register today!
March 25 – The Intelligent Intranet Accelerator Workshop- Featured as part of Microsoft Ignite The Tour Hong Kong
The Microsoft Intelligent Intranet Accelerator Workshop is a hands-on session within Microsoft Ignite The Tour in this location. By registering below, you’ll receive instant access to not only the Microsoft Intelligent Intranet Accelerator Workshop, but also the free 2-day Microsoft Ignite The Tour.
Register today!
April 2020
April 16 – The Intelligent Intranet Accelerator Workshop- Featured as part of Microsoft Ignite The Tour Chicago
The Microsoft Intelligent Intranet Accelerator Workshop is a hands-on session within Microsoft Ignite The Tour in this location. By registering below, you’ll receive instant access to not only the Microsoft Intelligent Intranet Accelerator Workshop, but also the free 2-day Microsoft Ignite The Tour. You will enjoy a plethora of keynotes, breakout sessions and one-on-one networking opportunities. This free tour provides technical training led by Microsoft experts and your community. You’ll learn new ways to build solutions, migrate and manage infrastructure, and connect with local industry leaders and peers.
Register today!
April 28 – The Intelligent Intranet Accelerator Workshop- Hosted at the Microsoft Offices in Berlin, Germany
Get inspired with the art of the possible at the FREE Microsoft Intelligent Intranet Accelerator Workshop. Complete the registration today and reserve your spot in your city. By attending the workshop, you’ll walk away with the tools and capabilities necessary to accelerate your time-to-value.
Register today!
May 2020
May 5 – The Intelligent Intranet Accelerator Workshop- Featured as part of Microsoft Ignite The Tour Stockholm
As part of Microsoft Ignite The Tour, the Microsoft Intelligent Intranet Accelerator Workshop will bring a deeply technical and immersive hands-on experience where you will build real-world applications to connect, succeed, and engage – faster. You will enjoy a plethora of keynotes, breakout sessions and one-on-one networking opportunities. This free tour provides technical training led by Microsoft experts and your community. You’ll learn new ways to build solutions, migrate and manage infrastructure, and connect with local industry leaders and peers.
Register today!
We hope we will see you on the road!
Register today for a city near you for our Intelligent Intranet Accelerator Workshop!

In this session of SharePoint Dev Weekly, hosts – Vesa Juvonen (Microsoft), Waldek Mastykarz (Rencore), and typically a special guest from the SharePoint PnP Community, discuss the latest news and topics around SharePoint development.
In this episode, Vesa and Waldek are joined by Erwin van Hunen – Lead architect at Valo Intranet. In addition to drawing attention to the recent advancements being delivered by the SharePoint Community and Microsoft, Vesa, Waldek and Erwin’s discussion this week focused on Erwin’s pioneering work on and evolution of PnP Provisioning and PnP PowerShell, the shaping of a tenant templating engine (support for Azure, Teams, OneDrive, SharePoint) – PnP .Net Core SDK, .NET frameworks, and tools – CLI and PowerShell.
This episode was recorded on Monday, January 27, 2020.